Ryuk ransomware (Virus Removal Instructions) - Free Guide
Ryuk virus Removal Guide
What is Ryuk ransomware?
Ryuk ransomware is large-scale malware that chooses its targets carefully
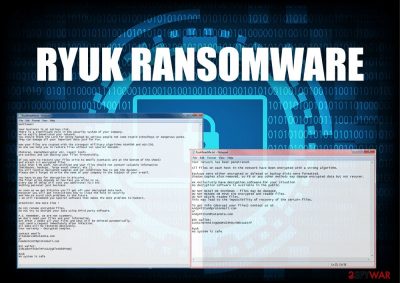
Ryuk is a ransomware virus[1] that, since August 2018, has already attacked and encrypted data from several companies, data centers, and PC users. According to numerous claims, the virus stems from the same family as Hermes ransomware which is attributed by an infamous Lazarus group. It shocked cybersecurity experts after they found out that the malware can misuse the Wake-on-Lan feature to turn the computer on and increase the number of infected devices on the network. It has a copy of Hermes cryptovirus coding and the Bitpaymer ransomware-resembling text in the ransom note but none of these relations were confirmed as genealogy features by researchers.
After ransomware encrypts systematically selected data, it generates a RyukReadMe.txt ransom note with the ransom fee that varies from 15 BTC to 50 BTC, depending on the amount of encrypted data via the provided Bitcoin wallet.[2] Ransomware returned to the headlines after performing several attacks during the Christmas time, including the DataResolution.net cloud hosting provider.[3] This new version has been named RYK ransomware due to the file extension appended. However, note that alternatively it has been called a Cryptor2.0.
Ransom payments averaged around $10,000 in 2018, but Ryuk ransomware made this average come up to $111,605 for the first quarter of 2020 especially due to the fact that this virus is used in 19,6 percent of all ransomware attacks. Even though researchers noticed a slight decrease in attacks involving this malware strain. It is still used against large organizations with at least 1,000 workers. Developers ask for $1,4 million from each victim on average so it becomes the most profitable ransomware of recent years.
| Name | Ryuk |
|---|---|
| Also known as | Cryptor 2.0, RYK ransomware |
| Category | Ransomware/cryptovirus/malware |
| estimated income | Around $3.7 million |
| Encryption algorithms | AES-256; RSA-4096 |
| Ransom notes | RyukReadMe.txt, UNIQUE_ID_DO_NOT_REMOVE.txt, ReadMe.txt |
| Ransom amount | 15 – 50 BTC. A recent analysis showed that the average amount asked from malware victims is $1,4 million |
| Related files | horrible.exe, kIUAm.exe |
| Email addresses used for contact |
|
| Blocked services | Acronis VSS Provider, Sophos-related services, Veeam backup service, MBAM service, McAfeeEngine service, etc. |
| Elimination | Download anti-malware and run a full system scan. After ransomware removal, follow the guide on how to decrypt encrypted files (at the end of the post) |
According to the latest news reports, Ryuk ransomware is still rapidly spreading throughout the Internet sphere and infecting users worldwide. The Federal Bureau of Investigation, also known as FBI, has made a research and found out that this cyber threat has launched dangerous attacks on more than 100 different types of businesses in The United States of America.[4]
Additionally, all of this took place starting from August 2018 until the middle of May 2019. This is a very big number of infected companies throughout such a period of time. Experts think that the reason why this ransomware strain has been so successful is that it also delivers other destructive viruses such as TrickBot and Emotet. The variety of suffered organizations is wide, such as logistics companies, technology-based manufactures, and similar.
Researchers are still working on getting more knowledge about this ransomware distribution means. However, it has been speculated that it is distributed in the form of a phishing email attachment which typically presents itself as an invoice, business report, etc. Additionally, hackers are likely to abuse insufficiently protected RDP[5] configurations to attack targeted companies.
To run on the computer, Ryuk malware needs to gain admin privileges. Therefore, each of the attacks needs to be carefully planned, credentials gathered, network mapped, etc. This led researchers from Check Point to believe[6] that the infection is carefully engineered by sophisticated hackers who are experienced in targeted attacks. According to Check Point experts, the malware has extreme similarities to Hermes 2.1 ransomware which belongs to the infamous Lazarus group who were formerly associated with the North Korean army.

The latest virus version, Cryptor2.0, hits Data Resolution and Tribune Publishing
After staying still for some time, the new version of Ryuk ransomware hit again during the Holiday 2018. Experts encountered the rise of its activity on December 24 and December 27. The first campaign was held on Data Resolution when ransomware gave control of the important data to the attacker. The data center domain was accessible until the company shut down the whole network. According to Data Resolution, no user data was accessed or compromised. The main purpose of this ransomware was to hijack the network not to steal the credentials.
On December 27, 2018, cybercriminals hit Tribune Publishing newsprint organizations and disabled their ability to print papers. The incident was discovered late at night when one editor could not send finished pages to the printing service. The issue was quickly fixed and no more damage discovered on the network.
It is obvious that this ransomware is still active. According to the latest reports, both Data Resolution and Tribune Publishing were affected by Cryptor2.0 which is considered to be the newest variant of the ransomware virus. Once installed, this cyber threat encrypts files and marks them with the .RYK appendix. Additionally, it displays a ransom note explaining all conditions needed to get the decryption tool.
According to the note, victims are given a chance to recover two files for free, however, for the other ones, the users need to be a particular price. All details need to be discussed by email. Moreover, the criminals hiding behind virus threaten users not to reset, shut down the computer, or delete any files because all data will be permanently deleted. 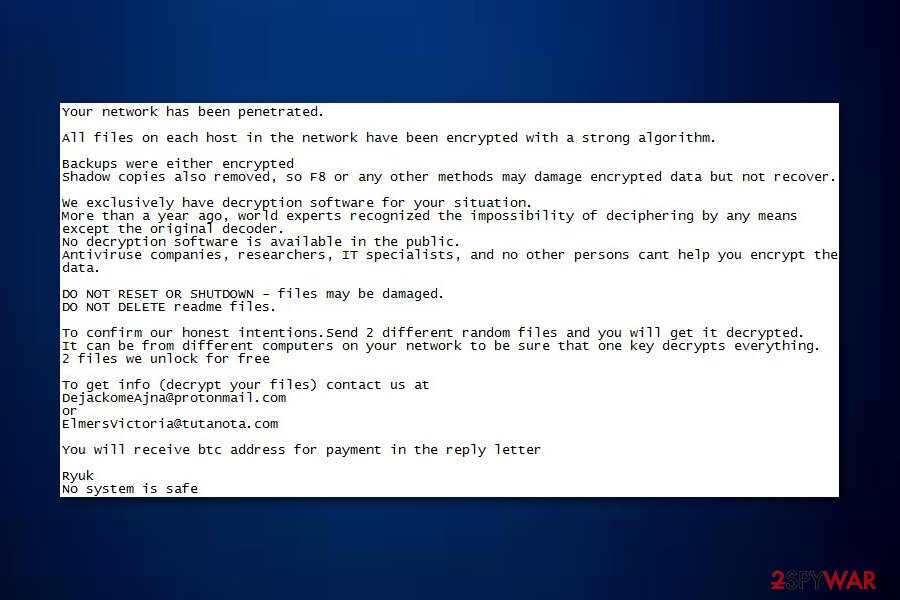
The functionality of malware
Before implementing the necessary changes on the device, ransomware shuts down 180 services and more than 40 processes that are running on the system. The malware executes taskkill and net stop command on a predetermined list of processes and services.
The virus then uses the kIUAm.exe executable file which is launched once the victim reboots the system. Right after that, it encrypts victim’s data, e.g., business documents, reports, photos, videos, databases, and other personal information with the specific file extension using the combination of RSA-4096 and AES-256 encryption algorithms.
Upon successful encryption, the virus generates ransom notes named RyukReadMe.txt and UNIQUE_ID_DO_NOT_REMOVE.txt. They read the following:
All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted or deleted or backup disks were formatted.
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation
No decryption software is available in the public.
DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
This may lead to the impossibility of recovery of the certain files.
To get info (decrypt your files) contact us at
MelisaPeterman@protonmail.com
or
MelisaPeterman@tutanota.com
BTC wallet:
[link]
Ryuk
No system is safe
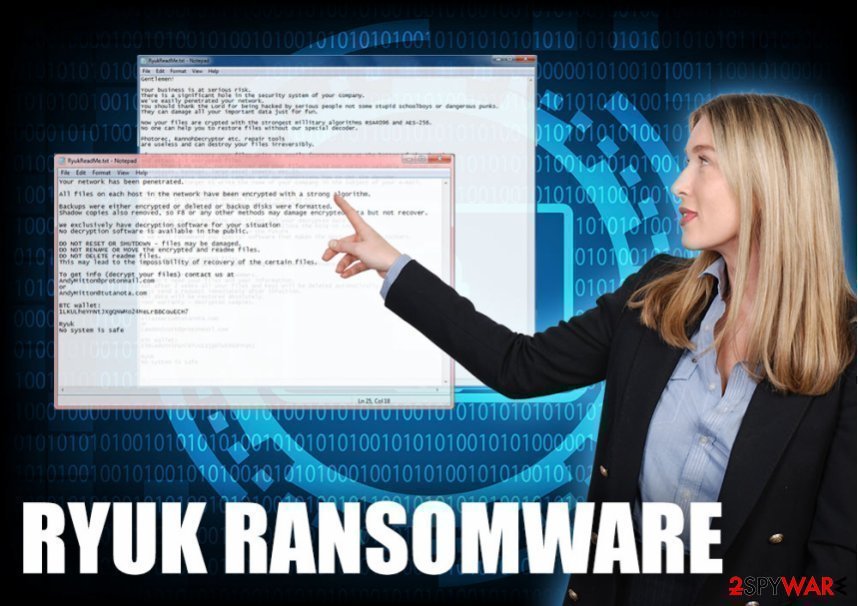
If the virus attacks a company or similar authority, it drops such note:
Gentlemen!
Your business is at serious risk.
There is a significant hole in the security system of your company.
We’ve easily penetrated your network.
You should thank the Lord for being hacked by serious people not some stupid schoolboys or dangerous punks.
They can damage all your important data just for fun.
Now your files are crypted with the strongest millitary algorithms RSA4096 and AES-256.
No one can help you to restore files without our special decoder.
Photorec, RannohDecryptor etc. repair tools are useless and can destroy your files irreversibly.
If you want to restore your files write to emails (contacts are at the bottom of the sheet) and attach 2-3 encrypted files
(Less than 5 Mb each, non-archived and your files should not contain valuable information
(Databases, backups, large excel sheets, etc.)).
You will receive decrypted samples and our conditions how to get the decoder.
Please don’t forget to write the name of your company in the subject of your e-mail.
You have to pay for decryption in Bitcoins.
The final price depends on how fast you write to us.
Every day of delay will cost you additional +0.5 BTC
Nothing personal just business
As soon as we get bitcoins you’ll get all your decrypted data back.
Moreover you will get instructions how to close the hole in security and how to avoid such problems in the future
+ we will recommend you special software that makes the most problems to hackers.
Attention! One more time !
Do not rename encrypted files.
Do not try to decrypt your data using third party software.
P.S. Remember, we are not scammers.
We don’t need your files and your information.
But after 2 weeks all your files and keys will be deleted automatically.
Just send a request immediately after infection.
All data will be restored absolutely.
Your warranty – decrypted samples.
contact emails
eliasmarco@tutanota.com
or
CamdenScott@protonmail.com
BTC wallet:
[link]
No system is safe
While Ryuk ransomware removal will not give users access to the files, it will eliminate the infection itself. We strongly recommend using reputable security software like SpyHunter 5Combo Cleaner or Malwarebytes, capable of destroying all traces of malware. If you later have troubles with system stability or crashes, you could employ FortectIntego to fix virus damage automatically.
While hackers actively try to convince victims that paying the ransom is a great idea (they even go as far as claiming that they will reveal the security hole and show how to fix it), security researchers[7] advise not to. These people are from a high-profile crime organization and can not be trusted. Additionally, despite criminals' warnings, you should remove the ransomware as soon as possible.
Ransomware actors are back after a break
Cybercriminals behind ransomware are usually keeping their attacks consistent, and new victims emerge on a regular basis. However, taking breaks is also not unusual for one reason or another – the threat actors seemed to be doing just that for a long time until a new campaign was spotted in September 2020.
Security researchers at Sophos detailed this new campaign in their security research report, claiming that actors are now back and claiming victims one after the other. The new campaign revolves around sending out targeted phishing emails – it serves as the main attack vector. Experts also claim that the criminal gang has improved and evolved their tools, techniques, and practices.[8]
To begin the attack, malicious actors deployed an array of highly-targeted phishing emails directed to the company's employees. One of the emails read:
From: Alex Collins [spoofed external email address]
To: [targeted individual]
Subject: Re: [target surname] about debit
Please call me back till 2 PM, i will be in [company name] office till 2 PM.
[Target surname], because of [company name]head office request #96-9/23 [linked to remote file], i will process additional 3,582 from your payroll account.
[Target first name], call me back when you will be available to confirm that all is correct.
Here is a copy of your statement in PDF[linked to remote file].
Alex Collins
[Company name] outsource specialist
As soon as the alleged PDF is opened, it redirects users to a Google Doc file, which, once opened, executes a “print_document.exe.” This file is malware loader (known as Buer Loader malware-as-a-service being sold for $350 on the underground forums) – it contacts a remote server and downloads the malicious payload on the target system.
Malicious actors managed to break into domain controllers and obtain critical information needed to proceed with the attack. Just within four hours after the malicious file was launched, several servers were compromised. Within a day, actors attempted to launch the ransomware payload on the targeted network, although this attempt failed – only ransom notes were dropped on the compromised server, and no data encrypted.

Researchers said that the malware itself did not differ much from its previous versions. However, they noted that hackers added additional obfuscation measures to prevent security tools from detecting payload within the system's memory.
Without a doubt, this attack proves that the gang is not going anywhere, and it is ready to employ several break-in tools in order to achieve what they came for – ransom demands.
No longer encrypts systems with certain IPs
A new version of Ryuk ransomware has been first spotted by experts from MalwareHunterTeam.[9] This variant of the ransomware operates by using a newly-discovered technique. Once inserted on the computer, the malware will start searching for IP strings such as 10.30.4, 10.30.5, 10.30.6, and 10.31.32.
If these IPs are found on the targeted computer system, the virus does not perform any encryption on stored files and documents. Nevertheless, this file-locking threat detects the computer name and searches for strings such as “MSK”, “Msk”, “msk”, “SPB”, “Spb”, and “spb”.
If these two components match, the ransomware will not encrypt the computer also. According to the opinions of cybersecurity researchers, hackers use such techniques to prevent encryption of computer systems which are based in Russia. However, such a technique might not seem quite successful if worming activities are performed.
Distribution techniques evolve from spam email to trojan malware
According to PC experts, the virus is using phishing email messages to get into the target PC systems. Usually, a large amount of these messages is sent to businesses to increase the number of encrypted files and earn bigger ransoms. Beware that you need only to click on an infected email attachment to get infected with ransomware. Such messages can also be filled with trustworthy-looking logos, addresses, and similar information pretending to be from Lloyds Bank, HSBC, and similar companies that could increase chances to infect the victim with the ransomware virus.
To avoid the loss of important data, you need to be extremely careful with emails from unknown senders. Make sure you doublecheck every line included and use your mouse to check the trustworthiness of links you have been sent to.
There is a theory that Emotet and TrickBot are used to distribute this ransomware. After gaining the connection to the target network, these viruses bring additional malware to the system in exchange for a certain fee. Often, the Trickbot has been rented only to certain people.
Remove Ryuk ransomware from the system using professional tools
To perform ransomware removal, make sure you do not consider using manual removal techniques. This is a serious virus that travels around with numerous components that can be found only by running a full system scan with anti-spyware. In this case, we recommend using SpyHunter 5Combo Cleaner or Malwarebytes which have been approved to be powerful enough to fight against such complicated malware. Additionally, check the system with FortectIntego for altered registry entries and similar components (does not encrypt files).
Unfortunately, once you remove Ryuk ransomware from the system, your files will still be encrypted. That's because the decryption key needed to recover locked data is saved on the remote servers that belong to the crew of this ransomware. However, don't be desperate and think whether you have extra copies of your encrypted data saved on external devices. If no, use tips provided below to decrypt the compromised files.
Getting rid of Ryuk virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
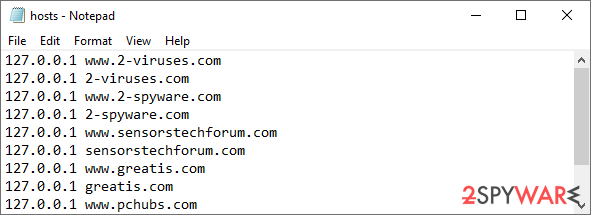
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
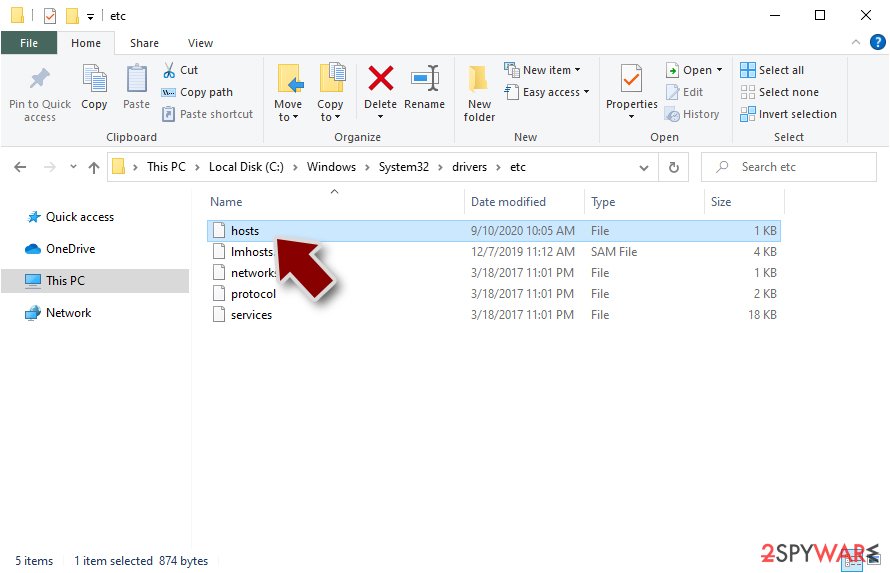
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Ryuk and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ What is Ransomware?. Trend Micro. Security researchers.
- ^ Jake Frankenfield. Bitcoin Wallet. Investopedia. Latest info.
- ^ John Leyden. Ryuk ransomware blamed for attack on cloud provider. Portswigger. Web application security, testing, & scanning.
- ^ David Bisson. More Than 100 US Businesses Affected by Ryuk Ransomware Since August 2018, Finds FBI. Security Intelligence. Daily news.
- ^ Remote desktop protocol (RDP). SearchEnterpriseDesktop. System security management.
- ^ Ryuk Ransomware: A Targeted Campaign Break-Down. Check Point research. Malware experts.
- ^ Virukset. Virukset. Security news and articles.
- ^ They’re back: inside a new Ryuk ransomware attack. Sophos News. Security research blog.
- ^ Malware Hunter Team. Starting to see signed Ryuk ransomware samples.... Twitter. Worldwide network.




























