Android ransomware (Improved Guide) - 2017 update
Android virus Removal Guide
What is Android ransomware?
Android ransomware asks to purchase iTunes gift cards as a ransom

Android ransomware[1] is designed to lock the smartphones and insist on paying the ransom. Usually, the criminals ask to transfer the demanded amount of money to a specific Bitcoin account. However, recently the experts have spotted an new offspring which accepts iTune Gift Cards as a ransom.
Android-based ransomware started spreading around as simple viruses that block the access to the phone with a lock screen ransom note. However, some of them were soon modified to obtain Device Administrator privileges and change the PIN code of the device.[2] Knowing that your phone's or other device's PIN can be changed by hackers is already highly unsettling, but there is much more Android malware can do.
At the end of 2016, security researchers discovered the most surprising news — some smartphone parasites are capable of blocking LG Smart TVs.[3] Fortunately, LG didn't leave their clients to deal with the hijack alone and helped the victim to remove Android virus permanently with TV factory reset.[4] Other versions of this malware can be removed with the help of FortectIntego.
Users who prefer visiting various potentially insecure domains are more exposed to the risk of this file-encrypting malware. You can accidentally infect your phone with this virus by clicking on unreliable links. Such links are usually displayed on high-risk websites (mostly gambling or pornographic content sites).
Additionally, you can become a victim of the ransomware by downloading unreliable apps from shady app stores. For example, adult content related apps such as Porn ‘O’ Mania, Love Beauty, Sexy Hot, Sexy, Lutu and similar apps are known to be spreading mobile ransomware around.[5] You can find these programs in some third-party app stores only.
Unfortunately, we cannot list all of Android ransomware app names. That's why you should always double check apps before installing them on your device. In short, now you should concentrate on Android ransomware removal.
When a user installs such malicious app and runs it, he/she receives an additional pop-up message on the screen, which might look like a regular system message that asks to adjust app settings or to install additional (or recommended) apps.
If the user clicks on this window or agrees to “continue,” he or she unconsciously gives admin rights to the virus. This is exactly what Android malware needs. This indirect method to get user’s agreement is called clickjacking – it forces the user to agree with something that he/she was not aware of.

The peculiarities of ransomware functioning
While there are different types of Android virus, some variants might only perform the screen lock function or be able to encrypt phone's data as well.
The first thing that the malicious program seeks to complete, is to gain Administrative rights of the smartphone. It can trick you to give them by imitating an innocent program or a well-known app.
Then, this mobile virus displays a threatening message, saying that the user has accessed illegal content. It also warns that your personal records, as well as web browsing history, might be sent to all contacts that were found on your phone.
In addition to that, this virus can change your phone passcode and PIN code. The reason update of the malware contributes to the better performance of the threat and makes it more troublesome to remove.
Previously, the malware exploited hard-coded passwords to lock victims devices. Luckily, virus researchers found a workaround – they created a matching code according to the pattern of lock screen original code.
After finding out that their masterpiece was cracked by the “good guys”, hackers came up with the update. Now they switched to pseudorandom codes which are generated in the manner of Math.Random function.
In short, the hackers are able to generate unique 6-digit or 8-digit codes. Moreover, they combined this method with the former peculiarity. Certainly, this technique burdens the termination of the ransomware.
Furthermore, this mobile virus is called a ransomware not without a reason. In the ransom note, the malware demands to transfer the money in order to recover personal files and secure your privacy. It claims:
Country: XXXX
Region: XXXX
City: XXXX
Your location: XXXX
Operating system: XXXXYou are accused of viewing / storage and / or dissemination of banned pornography…you have violated World Declaration of non-proliferation. You are accused of committing the crime envisaged by Article 161 of the United States of America criminal law. Article 161 of the United States or America criminal law provides for the punishment of deprivation of liberty for terms from 5 to 11 years. Also you are suspected of violation of copyright and related rights law (downloading of pirated music, video, warez) and of use and / or of dissemination of copyrighted content.
This alert also claims that you should pay the ransom but you should never do that! This virus can encrypt your files, but reportedly it can permanently delete them all, too. Therefore, there is no logical reason to pay the ransom. It is very unlikely that your files can be recovered, so the only thing you can do now is to remove Android ransomware and protect your device against similar virus attacks in the future.
Updates on new Android virus versions
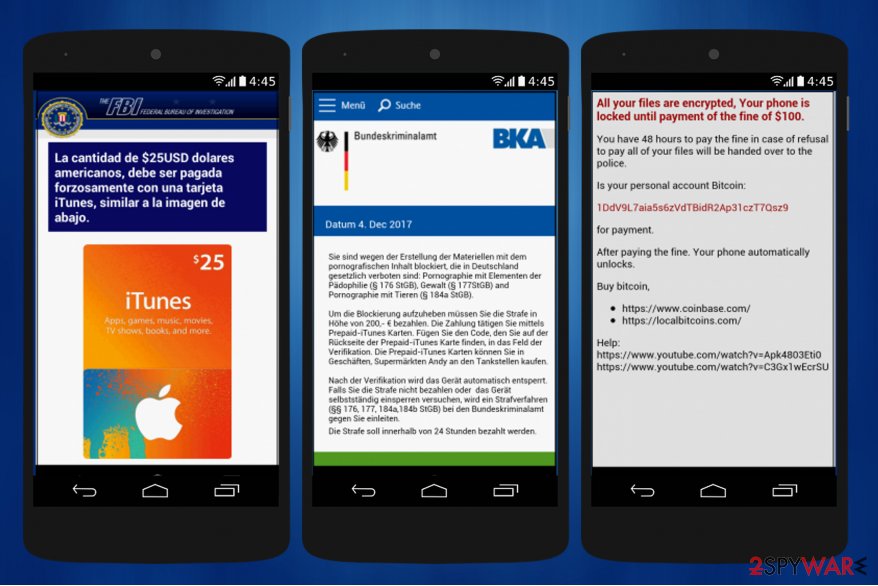
Porn Hub app ransomware. The latest variant of Android ransomware has just showed up on December, 2017. The crooks try to trick to swindle money from gullible people by claiming that they are fined for watching child pornography.
However, now Android ransomware insists on purchasing iTunes Gift Cards worth of $200 as a ransom if the device is connected to the Internet. Else way, the victims see another message which demands to pay $100 in Bitcoins instead.
According to the experts, this ransomware spreads as a fraudulent PornHub app on third-party application stores. Likewise, Android virus is named as Porn Hub app ransomware and comes as com.pornhub_tools package.
Currently, there is no information confirming that the malicious program would perform data encryption rather than simply lock the phone. Since the app does not include the bogus encryption script, you can recover your smartphone's settings using alternative ways and you should not pay the ransom.
Fake DropBox app ransomware. Similarly to the latter Android virus version, this one also demands a ransom of $25 in iTunes Gift Cards. The ransomware tries to trick users by imitating the famous file hosting app — DropBox.
Even though naive people might get confused, note that it is not hard to recognize an imposter. The main difference between the legitimate app and the virus is that the fake DropBox app ransomware asks to give administrative rights shortly after the installation.
If the person agrees to give them, the ransomware locks the device and displays a scam message pretending to be the Federal Bureau of Investigation (FBI). This is not the first time when the criminals try to imitate law enforcement agencies to gain illegal profits. Likewise, people should not get deceived so easily anymore.
The ransom note of the Android ransomware claims that the phone is locked as a punishment for watching child pornography and the user should pay the fine of iTune Card worth of $25 within 72 hours.
Additionally, hackers try to intimidate people once they try to enter a wrong card code by displaying the number of attempts left until the Android is locked permanently. According to the analysis, this only merely a trick to convince people paying the ransom.
Russian variant of Android ransomware. Hackers updating this malicious program have released an offspring which is specifically designed to target Russian-speaking Android users. It locks the smartphone's screen by using the older Google Cloud Messaging system, which is now known as Firebase Cloud Messaging platform.
This facilitates the operation of the hackers’ Command & Control server which is already responsible for around 20 operations that can be carried out on the infected device. The hackers can remotely lock or unlock the smartphone screen, gain access to the saved contacts and create new ones, send SMS and make adjustments to the malware code.
For the unlocking of the phone, hackers demand a huge amount of money (around 9,100 dollars) which usually doubles or triples the actual phone’s worth.
Unfortunately, there are users who are willing to pay the ransom. What they fail to realize, though, is that the money they send to the hackers motivates them to continue creating malicious programs in the future.
If you are ever in such a situation or if your phone is locked at this very moment – do not pay the ransom or enter any sensitive information you might be asked by the hackers. Instead, delete the virus from your device following the instructions we provide at the end of this article.
DoubleLocker ransomware is perhaps the first crypto-malware with exquisite operation mode which appeared in the cyberspace on October 2017. Besides encrypting users' data, the virus is also capable of locking the device and changing a PIN code. The infection makes use of accessibility settings which were designed for users with physical disabilities. The essence of this functionality is to allow certain apps run without users' direct consent.[6]
Furthermore, DoubleLocker virus was created on the basis of Svpeng banking trojan. It might develop into more menacing malware causing high financial losses. Users should also take into account that the malware disguises under fake Flash Player update[7] – a common bait among majority of malware developers.
Fraudulent updates often pop up in random pages. Note that only the notification popping up in Windows Action Center and informing about the latest Flash player update release is genuine. In other cases, treat urgent update messages in the Web as deceptive.
Learn how to protect your smartphone from ransomware infections
Malware researchers note that people who run older versions than Android 5.0 should be extremely cautious of ransomware attacks. New versions of smartphones are far more resistant to infections. Likewise, we care about your security and encourage to take the following precautionary measures:
- Download applications ONLY from verified and secure app stores. You can trust Amazon, Samsung, or Google Play stores.
- Keep your phone software updated.
- You can also install an app that is capable of securing your device from malware infiltration – we recommend BullGuard Mobile Security. It ensures complete Android ransomware removal.
Do not hesitate to remove Android virus
As you may know, there is professional software which could help you to remove Android ransomware automatically. However, you can get help by attentively following the provided instruction which are prepared by the certified IT technicians:
Step 1. Boot Android into Safe Mode:
- Find the power button and then press it for a few seconds until you see a menu. Click Power off.
- Once you receive a dialog window that suggests you to reboot your Android to Safe Mode, select this option and press OK.
- If this did not work for you, just turn off your device and then turn it on. Once it becomes active, try pressing and holding Menu, Volume Down, Volume Up or both these buttons together to see Safe Mode.
Step 2. Uninstall malicious and/or any suspicious and unknown apps:
- When in Safe Mode, go to Settings. Then, click on Apps or Application manager (this may differ depending on your device).
- Here, look for the previously-mentioned suspicious app(s) and uninstall them all.
If you are dealing with Android ransomware on your smart TV, make sure you follow this video guide. Keep in mind that ransomware viruses can attack phones, computers and TVs (!) as well.
This particular virus affects different devices in a similar way – it locks the screen, changes the PIN of device and urges the victim to pay a ransom.
We strongly recommend reading this article about this type of computer viruses – What is ransomware? – to learn more about the prevention of such malware.
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ What is ransomware and how to remove it. 2spyware. Security news and virus removal guides.
- ^ LUKAS STEFANKO. Aggressive Android ransomware spreading in the USA. WeLiveSecurity. News about the latest threats and security trends.
- ^ Catalin Cimpanu. Android Ransomware Infects LG Smart TV. BleepingComputer. News and virus removal guides.
- ^ The infected user posts about Android ransomware on Twitter. Twitter.
- ^ Alistair Charlton. Android ransomware porn app sends internet history to all your contacts unless you pay bribe. International Business Times (IBTimes). A global news publication.
- ^ DoubleLocker Android ransomware explained. WeLiveSecurity. News about the latest threats and security trends.
- ^ Maria Goroshaninova. Svpeng attacks Russia: cybercriminals learnt how to steal with functions for disabled people on smartphones Source : https://realnoevremya.com/articles/1824-svpeng-attacks-russia-cybercriminals-learnt-how-to-steal-with-functions-for-disabled-people-on-sma. Realnoe Vremya. Online newspaper..
