DoubleLocker ransomware / virus (Free Guide) - Virus Removal Instructions
DoubleLocker virus Removal Guide
What is DoubleLocker ransomware virus?
DoubleLocker – a new Android virus that locks device’s screen and demands to pay the ransom

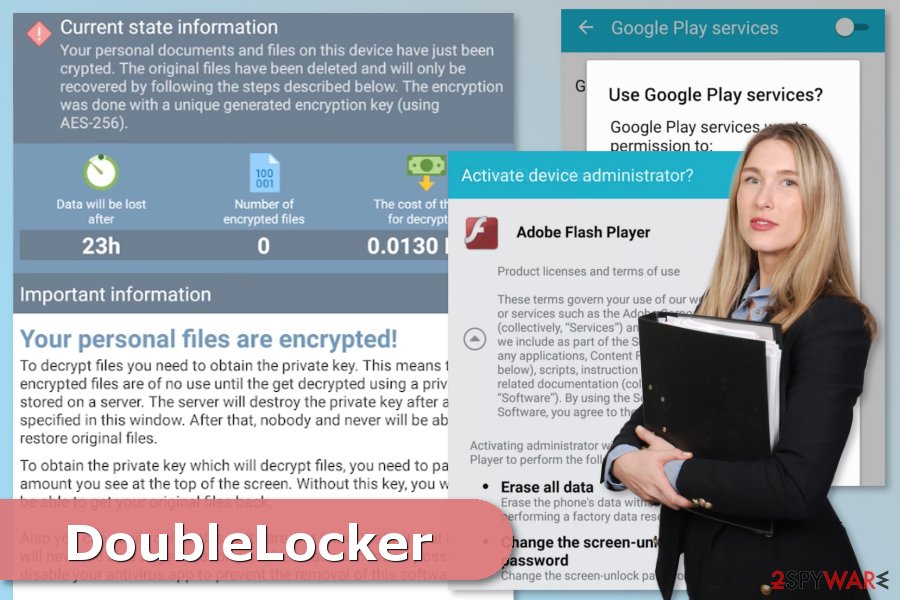
DoubleLocker is a ransomware-type mobile virus that aims at the Android operating system. This variant of Android virus spreads as a fake Adobe Flash update.[1] After the infiltration, it encrypts files and changes PIN lock. Then malware tries to hack victim’s bank account and demands to pay 0.0130 Bitcoins.
The significant feature of the DoubleLocker ransomware is that it is a “two-stage” malware. The first task it performs on the targeted device is hacking victim’s PayPal or bank account. Then it starts data encryption, locks the mobile and demands to pay the ransom. Therefore, it has features of the banking trojan[2] and file-encrypting virus.
According to cyber researchers, it’s a first mobile ransomware that misuses Android accessibility in this way. However, the virus is expected to be upgraded and used only for swindling the money from online banking accounts. Thus, in case of the attack, victims are advised to remove DoubleLocker immediately with FortectIntego or another mobile-friendly malware removal tool.
Once DoubleLocker gets inside the Android device, it requests “Google Play Services” accessibility feature. If users give this permission, malware gets administrative rights of the phone. Then it sets itself as a default home application, or in other words, launcher.
Users who installed fake Adobe Flash update does not know about this malicious activity. However, when a victim clicks the home button, he or she activates crypto-malware. Thus, the device gets locked. The problem is that DoubleLocker changes the PIN. However, victims lose access to their mobile phones.
Meanwhile, ransomware encrypts all the information stored there and demands to pay the ransom in 24 hours. Once attackers receive the money, the device is unlocked and files decrypted automatically. However, trusting attackers is not a wise decision.
It’s better to focus on DoubleLocker removal and restore files from backups. Hopefully, your device creates backups automatically and stores in the cloud. There’s no information that malware can encrypt files in cloud storage. Thus, get rid of malware and do not risk losing your money.
Do not install updates from unauthorized sources to avoid the attack
As we have mentioned this Android ransomware spreads as a fake Adobe Flash update on the compromised websites. Thus, you should stick to Google Play Store if you need to install some programs. Also, don’t forget that malware might bypass the security and act like a legit app. However, you should always download software from the verified developers.
Additionally, available app updates might pop up as a notification, or you can find them in the Google Play Store as well. Thus, install them only from there. Other sources distribute various types of malware.
Security experts from Sweden[3] also remind that you should be careful with other clickable content to protect from mobile malware attacks. Thus, do not click on suspicious links and ads. Moreover, do not download unknown apps or security tools promoted in pop-ups.
Tips for DoubleLocker elimination
DoubleLocker removal might be complicated if you have a non-rooted Android device. Victims can only unlock the phone by resetting the phone to factory state. Then, it’s possible to wipe out the virus with security software, such as FortectIntego.
If malware attacked rooted an Android phone that has enabled debugging model can take advantage of Android Debug Bridge (ADB) tool. Thus, they do not need to factory-reset phone to unlock it and remove DoubleLocker. Once the phone’s PIN is reset, victims can uninstall ransomware with a mobile-friendly security program.
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Swati Khandelwal. New Ransomware Not Just Encrypts Your Android But Also Changes PIN Lock. The Hacker News. Cyber Security and hacking news.
- ^ Roman Unuchek. A new era in mobile banking Trojans. Securelist. Information about viruses, hackers and spam.
- ^ UtanVirus. UtanVirus. Swedish cyber security news.
