Andromeda Trojan - 2021 update
Andromeda Trojan Removal Guide
What is Andromeda Trojan?
Andromeda is an evasive malware downloader that is capable of stealing information from the infected users

Andromeda virus is a family of Trojans that was first introduced in 2011 and has been active ever since. With dozens of variants released, it serves the purpose of propagating other malicious software (backdoor[1] functionality) and stealing confidential information from the victim. Various criminal gangs behind Andromeda used different attack vectors over the years, including exploit kits,[2] infectious software cracks, spam email campaigns, and others.
| Name | Andromeda |
| Type | Trojan, backdoor |
| Active since | 2011 |
| Related to | Research showed that Andromeda shares multiple source code similarities with Zbot/Zeus |
| Distribution | Malicious actors are known to use several distribution methods, including phishing campaigns, spam email attachments, illegal software downloads, and various exploit kits (Angler, Neutrino, Nuclear, etc,) |
| Encryption used | Various parts of the payload and malware files use RC4 and custom encryption |
| Main process | msiexec.exe |
| Functionality |
|
| Detection and termination | Andromeda and all its variants are particularly evasive, as the authors implement various obfuscation techniques. Nevertheless, most of the reputable security solutions should be able to detect the malicious payload and delete all the malicious files related to the infection (note that in some cases you might have to access Safe Mode – check the instructions on how to do that below) |
| System fix | Since the malware infects various Windows system files, it may corrupt the operation of the OS. To fix the damage done by the virus, scan your computer with FortectIntego |
Researchers from Avast[3] believe that the Andromeda Trojan family stems from ngrBot/DorkBot malware, although they also spotted multiple source code similarities with Zbot, otherwise known as Zeus, which is probably the most prolific malware ever created. Initially, it was used to steal banking credentials from Windows users, although many malicious parties abused the name later in online scam campaigns.
Andromeda is very sophisticated, which it comes to obfuscation and evasion techniques. It uses several uncommon API functions to avoid infecting environments that are used for malware analysis, such as sandboxes and other analysis tools. Distributors also put a lot of effort to prevent AV companies from establishing a malware profile:
Andromeda’s authors put a lot of effort into diversifying their portfolio of infection droppers and to disable, or at least complicate the sample submission and exchange between AV companies and their regular process used to scan and thoroughly analyze files. To achieve this, they update the custom packers daily and as a bonus, they bloat the binaries with more than 70 MB of garbage.
Besides, the virus uses executable compression[4] techniques (PE packers) to prevent Andromeda removal and detection by AV solutions. Nevertheless, the most up-to-date anti-malware tools like SpyHunter 5Combo Cleaner or Malwarebytes should be able to detect and eliminate the malicious files that were populated by the Andromeda virus.
Because malware performs various changes to the system and infects some system-related files (for example, modifies msiexec.exe and creates a new value, “Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run” in the registry), it may also destabilize the Windows, even after the malware is eliminated. Thus, to avoid the OS reinstallation, scan your computer with FortectIntego – it can repair the damage done and revert the damage done to system files.
Interestingly, malware is programmed to detect the language settings of the keyboard. If one of the following languages are identified, Andromeda Trojan will completely eliminate itself from the system:
- Russian
- Ukrainian
- Belorussian
- Kazakh
It is not uncommon for the attackers to exclude countries they are coming from to prevent the interest of local authorities.
Andromeda virus: presence and possible consequences
Andromeda virus is a dangerous Trojan horse, and it can be used for multiple malicious activities. As soon as the malware infiltrates the system, it starts controlling it, so you might notice that your computer is much slower than usual. Of course, Andromeda was not created only for that.
You should also know that this virus can easily infect your machine with additional malware, update it, disable it, remove it, and implement other malicious tasks on your computer. To perform all these tasks, Andromeda connects to its C&C server – all the communications are encrypted with the RC4 algorithm.[5]
The C&C server communication is performed in JSON format, and the following servers are used:
- hxxp://disorderstatus.ru/order.php
- hxxp://differentia.ru/diff.php
Both of these domains are connected to dozens of DNS servers that are located all over the world, including the U.S., Germany, the United Kingdom, etc. Anti-malware solutions detect the malicious domains as URL:Mal, so users with comprehensive online traffic protection software can prevent these communications.
Andromeda Trojan is also known to import various tracking modules and plugins into the system, including the well-known remote control tool TeamViewer. Nevertheless, victims would not be aware of its presence, as it is operated in the background. Besides the remote control, the virus also injects a rootkit,[6] keylogger, and other plugins that help malicious actors to achieve their goals.
In the meantime, users may suffer great losses due to Andromeda virus infection, including monetary loss, sensitive information compromise, and even identity theft/fraud. With the help of malware, hackers can establish a vast botnet, which helps them to harvest data on a mass scale. All the stolen information is typically sold on the Dark Web for large sums of money.
Therefore, remove Andromeda Trojan as soon as your security software flags it, as the consequences may be disastrous for you otherwise. If you had no anti-malware installed, the virus might run on your system for a prolonged time, and you will not know about its existence – this is another reason to keep a powerful security tool installed at all times.
Distribution routine and prevention measures
As previously mentioned, the Andromeda virus uses a variety of techniques to infect users around the world. Just as much other malware, the early campaigns include spam emails – this technique is still prevalent to this day, even though email providers implemented a variety of techniques to prevent such emails from reaching users. Despite that, threat actors always come up with new ways of presenting a phishing email to victims.
These emails include an attachment, typically of a .doc, .xls, .pdf, or .zip format, which, once opened, asks users to allow a macro function to run (i.e., “Enable Content” prompt). If granted, a PowerShell command will contact a remote server and download the malware payload. Thus, it is important not to allow macros to be run on ANY document that is clipped to a suspicious email.
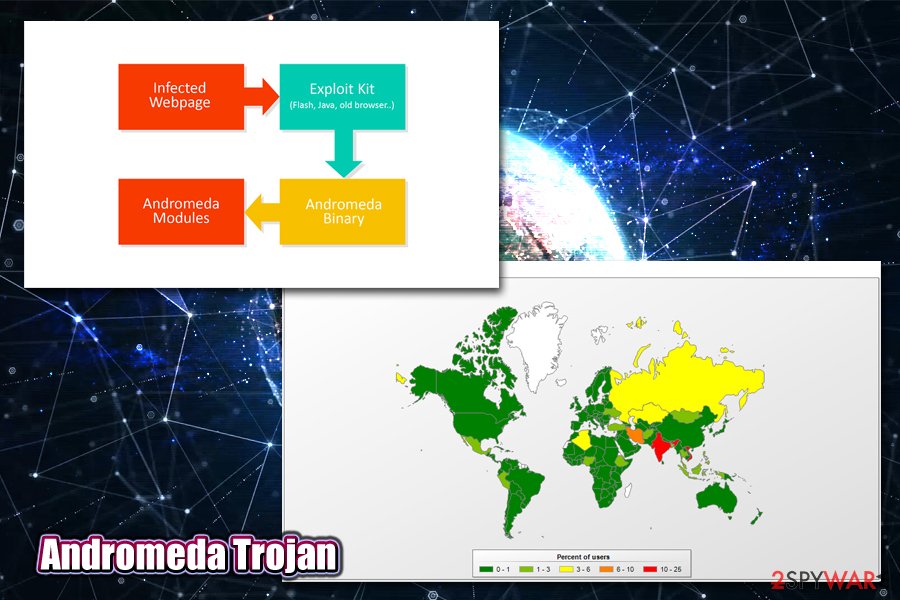
Other techniques used by the criminals include Angler, Neutrino, Nuclear, and other exploit kits, which and be rendered useless by those who use software that is patched by the latest security updates. The infection is triggered automatically as victims who use vulnerable software access a malicious or a hacked site – even a reputable site SourceForge (hosts open-source applications) was compromised by the attackers.
Also, stay away from torrent and warez sites that host illegal software installers and cracks/keygens – these are known to be infested with various types of malware, including ransomware like Djvu.
Andromeda virus removal steps
Andromeda virus is a sophisticated piece of malware, and threat actors use various techniques in order to increase its persistence and ensure that the malware stays on the system as long as possible. This is especially true if no anti-malware is not present on the machine, as it allows the infection to spread without interruptions. Once infected, the computer may remain in the state for weeks or even months, until security software is installed, and a prompt Andromeda removal can be performed.
In some cases, you might not be able to remove Andromeda Trojan immediately, as it may start tampering with your anti-malware software. In such a case, access Safe Mode with Networking, and perform a full system scan from there. To remediate the infected system files, perform a scan with a PC repair tool FortectIntego.
Getting rid of Andromeda Trojan. Follow these steps
Manual removal using Safe Mode
If you are struggling to remove Andromeda Trojan in normal mode, access Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Andromeda Trojan and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Kim Zetter. Hacker Lexicon: What Is a Backdoor?. Wired. American technology magazine.
- ^ Exploit Kits. NJCCIC. NJ Cybersecurity & Communications Integration Cell.
- ^ Andromeda under the microscope. Avast. Security blog.
- ^ Executable compression. Wikipedia. The free encyclopedia.
- ^ RC4. Wikipedia. The free encyclopedia.
- ^ Rootkit. Imperva. Security solutions.
