2021 Guide. URL:Mal alerts explained
URL:Mal Removal Guide
What is URL:Mal?
URL:Mal is a threat warning message, although adware authors can use such alerts to redirect online traffic
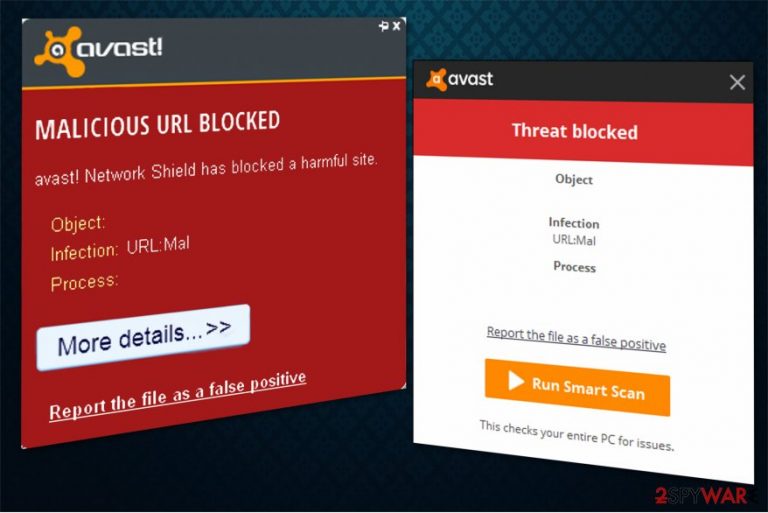
URL:Mal is a heuristic name of a possible threat that shows up on AVG and Avast scans or directly before accessing the suspicious site. This is a warning message that is displayed by various anti-virus engines but can indicate different issues. Typically, it pops up whenever users are about to visit a malicious website, and the security software blocks the entry. This is normal behavior, and users should not ignore it.
However, cybercriminals managed to utilize this alert and display it as a fake message in order to trick users into installing bogus software, redirecting their traffic to ad-supported sites, or retrieving personal information. The questionable rundll32.exe also is associated with this alert warning. This fact only raises more questions even though the executable is mainly reported as safe and legitimate. If you want to know more about what is URL:Mal and what causes those suspicious alerts, keep on reading this article.
| Name | URL:Mal |
| Type | Adware |
| Purpose | To make users install fake software or expose their personal data |
| Main dangers | Malware infiltration, identity theft, stolen money from a bank account |
| Symptoms | Fake messages, redirects, pop-up ads, etc. |
| Distribution | Software bundling, dubious websites |
| Elimination | You can get rid of URL:Mal by using FortectIntego or by checking our manual guide below |
URL:Mal warnings started to spark suspicions when users noticed the alert is popping up whenever they visit a website which is entirely legitimate, like Amazon.com or Wikipedia.com – these sites do not display advertisement content, and neither they are harmful.
The malicious URL:Mal virus looks identical to the original alert message. In most cases, it starts showing up after the user falls for installing a malicious add-on, plugin or extension on his/her computer. It can also block you from entering your favorite websites, so there is a high risk that you can fall into believing that the pop-up message is real.
Similar alerts about errors or even threats appear on the browser due to the corruption of a file associated to URL:Mal – rundll32.exe, so these messages may be fake and the issue is this executable file. The best tip to know what is the reason for this behavior is to disable third-party antivirus tools and other applications and scan the system with one powerful anti-malware program that should indicate all possible threats and diagnose the corrupted executables.
The URL:Mal alert shows up with a similar warning:
We have safely aborted the [link] connection because it was infected by URL:Mal
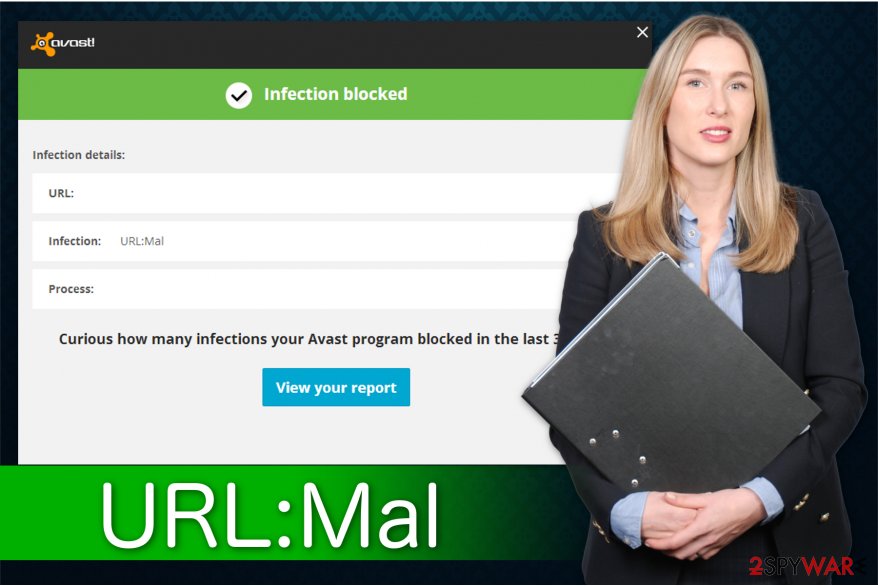
In most of the cases, URL:Mal fake alert is used to swindle the money away from unsuspecting users.[1] However, it can also trick them into installing other PUPs, redirect to other suspicious websites or show fake surveys that are used for personal data harvesting.
Finally, the fake URL:Mal message can lead victims to domains that advise downloading and installing questionable software (usually scareware or bloatware). If you have any doubts about the legitimacy of URL:Mal warning message, make sure you ignore suggestions to download/install programs or their upgrades offered to you by them.
The particular URL:Mal alerts show up on many people' computers and browsers, as we can find on various forums and discussions online.[2] These messages cause frustration because of many things:
- pop-ups appear continuously;
- alerts come up while visiting certain sites;
- there is no particular threat that can be removed;
- warnings show up on social media, Wikipedia, other safe and commonly visited pages.
Additionally, you should complete URL:Mal removal as soon as possible since these types of viruses could stealthily infiltrate other high-risk computer infections such as Trojan Horses, spyware, etc. According to the Virusi.hr[3] experts, you should not try to eliminate these cyber threats by yourself. 
Malware alerts indicating threats or messages appearing out of nowhere?
Generally, seeing such pop-up alerts means that your antivirus blocked a suspicious domain from opening on your browser. It may be caused by malicious page, ad-supported website or PUP-filled site.
However, this alert can also be caused by two different AV programs interacting with each other and causing such alerts to show up. It usually appears people have a few anti-malware or security tools and they cannot work properly due to the existence of the other one, so blocks various safe sites instead.
Another thing that may be the issue causing such messages about URL:Mal threat is potentially unwanted programs. This alert can be used by a cyber threat developer that attempts to trick users into accessing their sites, sponsor domains or even purchase promoted applications.
Besides the fake message, PUP is capable of the following:
- installing additional software without users' knowledge;
- modifying certain system settings to avoid elimination;
- slowing down the computer;
- disturbing web browsing activities by covering up contents with annoying ads.
If you think that you are infected with such adware, you can remove URL:Mal by scanning your computer with FortectIntego. It will detect all potentially unwanted programs which cause false positive detection and eliminate the adware from your computer.
Unfortunately, there is no particular program that we could offer to remove and the associated file has a low detection rate[4], but you should disable all your AV tools, choose one of many reliable anti-malware programs and then scan the machine fully. This way, your computer gets thoroughly checked and cleaned, so all the malicious programs get removed entirely.
Potentially unwanted programs distributed in software bundles
The most common way of how the potentially unwanted program enters your system is software-bundling. Usually, people are unaware that once they download a free application, it can secretly install the additional one. This marketing strategy is widely used by the developers of PUPs[5].
However, you can easily avoid adware programs if you pay attention during the download/installation procedure. Firstly, you should opt for Advanced or Custom settings during the process. They will reveal the previously selected checkmarks which allow installing the potentially unwanted program. Do not forget to de-select them.
Also, we recommend you to stay away from online ads. Once clicked, they might even help to infiltrate the adware or other high-risk computer infections. Therefore, use a robust anti-spyware software to protect your computer and valuable information stored on it.
The best way for URL:Mal removal – professional anti-malware tools
Since it might be hard to determine whether Avast URL:Mal warning is real, you should double-check your system using a professional security software. Scan your computer and make sure that the adware is not present on your PC. If it is compromising your computer, the antivirus tool will eliminate it.
Additionally, keep in mind that adware programs do not travel alone — its components might also damage your system. Therefore, it is vital to not only remove URL:Mal but its elements as well. For that, use one of the anti-malware tools from the list below.
If you want to complete URL:Mal removal manually, make sure to check the instructions below. They will help you to detect adware-related components and eliminate the hidden hazard.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of URL:Mal. Follow these steps
Uninstall from Windows
If you continuously are provided with URL:Mal pop-up, you have to clean your Windows following the given guide:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Fix Chrome from URL:Mal pop-up by deleting all adware-related components.
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of URL:Mal registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Lee Brandt. The Dangers Of Adware And Spyware. Poindexter Solutions. Tech Support website.
- ^ Url:mal virus is getting detected again and again.. Techguy. Tech support forum.
- ^ Virusi. Virusi. Security and Spyware News.
- ^ Sample AV detection rate. Virustotal. Online malware scanner.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. How-To Geek. We Explain Technology.
