EventBot (Virus Removal Guide) - Free Instructions
EventBot Removal Guide
What is EventBot?
EventBot – dangerous financial malware designed for Android devices

EventBot is a malicious application that can run on Android-based devices and targets users in the US and Europe. It was first spotted in March 2020, and security researchers from Cybereason Nocturnus were analyzing the malware closely for several weeks before releasing their findings.[1] As it turns out, EventBot is a Trojan that abuses accessibility feature within Android OS in order to steal banking and other information from over 200 different financial apps. Malware is also capable of bypassing two-factor authentication, reading data from crypto-wallets, as well as stealing SMS message contents.
Since EventBot virus is operating in the background, users who are not protecting their devices with security solutions might never know that they are infected in the first place. In the meantime, the malicious app can gather sensitive data and deliver it to cybercriminals. Victims can suffer significant monetary losses, have their credit score corrupted, loans are taken out in their names, and suffer from identity theft. While EventBot is still under active development, it is malware that Android users should be very scared of.
| Name | EventBot |
| Type | Android virus, Financial Trojan |
| Release date | March 2020 |
| Distribution | Like many other malicious apps designed for mobile devices, EventBot is installed via fake applications downloaded from third-party sites (such as P2P) |
| Primary function | Harvest sensitive financial data and device information and send it to a remote server for the attackers to abuse |
| Capabilities |
|
| Versions | Version 0.0.0.1, Version 0.0.0.2, Version 0.3.0.1, Version 0.4.0.1 |
| Elimination | To eliminate malware from Android device a full scan with reputable anti-malware software should be performed |
| Optimization | To clean duplicates and monitor your apps, download and install FortectIntego |
Smartphones are now standalone devices greatly surpassing desktop machines when it comes to volume. According to statistics portals, there are more than 14 billion mobile devices currently in circulation,[2], so there is no doubt that threat actors are willing to benefit from this saturated market.[3]
This can also be noted with an increasing amount of malware that is being produced for portable devices, especially Android OS-based ones. The malware was created to steal from victims and benefit cybercriminals – we will try to explain how to prevent its infiltration and how to remove EventBot virus for good to avoid extensive data compromise.
Just like many other Android virus members, EventBot makes its way to users' devices via applications downloaded from insecure third-party sources. While some apps might be unheard of, it is not uncommon for malware to be disguised as a well-known application. Researchers also managed to trace several legitimate application icons that were used to disguise EventBot malware inside.
Before the installation is complete, EventBot asks for several permissions within the Android device, some of which include:
- install other packages;
- create windows that are shown on top of other apps;
- allow running in the background;
- allow reading SMS contents;
- access information about network;
- allow the app to start with each device launch, etc.
Knowing about EventBot capabilities and purpose, these permissions make much sense. Nonetheless, many users do not pay close attention to permissions and simply allow them all during the installation of the fake app, as they believe it can be trusted (e.g., Adobe Flash Player, MS Word, etc.).
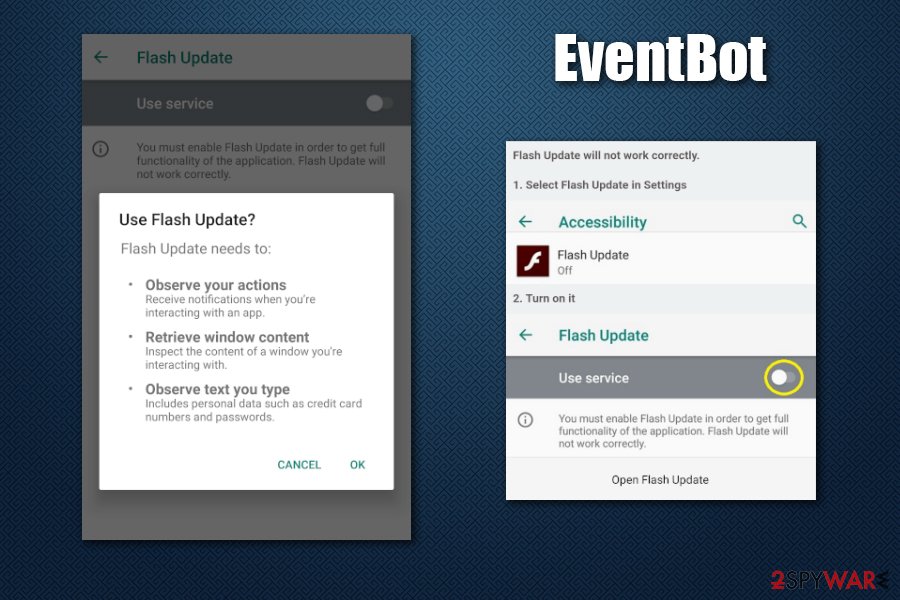
Once established, EventBot Trojan asks for accessibility service access. These are typically used to help users with disabilities to help them perform actions on their mobile devices they would normally not be able to, such as writing, performing gestures, and other functions. With this permission, EventBot will be able to operate as a keylogger, recording all inputs and screen presses from that point.

As soon as it establishes itself, EventBot downloads a configuration file for 200 different financial apps, which include Santander, CapitalOne, HSBC, UniCredit, Revolut, TransferWise, Coinbase, Paypal Business, and many more. This allows the malware to gather sensitive information, such as keystrokes, passwords, transactions, from these apps and send it off to a remote server (data is encrypted with various different ciphers, depending on the version).
When it comes to EventBot removal, only a reputable anti-malware software can help you. When it comes to its detection, you might not notice the malware operating the background, although excessive battery usage is one of the main indicators of the infection. Additionally, we would like to recommend using FortectIntego to optimize and keep your Android device clean.
EventBot versions and improvements
Even though EventBot is a relatively new malware strain, several versions were already identified by security researchers, including:
- Version 0.0.0.1 uses RC4 and Base64 Packet encryption to send out device information and other metadata within a JSON file. The action is repeated until a successful connection to C2 server is made.
- Version 0.0.0.2 loads its main module dynamically, preventing static analysis from outside sources.
- Version 0.3.0.1 includes region-based features to make the app more believable in different countries. This variant also included a function that allows malware to track PIN changes within settings.
- Version 0.4.0.1 incorporated new obfuscation techniques with the help of ProGuard. Additionally, the package name was no longer “com.example.eventbot,” which makes it more difficult to detect.
Based on numerous differences between these variants, security experts quickly concluded that EventBot is still under active development:[1]
EventBot is in constant development, as seen with the botnetID string above, which shows consecutive numbering across versions. This example is from a later version of EventBot, and in other versions the naming convention is very similar, with bot IDs such as word100, word101, word102, and test2005, test2006 etc.
While researchers managed to identify several peculiarities about EventBot malware itself, they could not link it with any cybercriminal gangs, all while monitoring underground forums. This is another strong hint that the virus is not yet fully released, and will be available for sale only later.
Avoid downloading apps from third-parties
Currently, there are over 2.8 million apps on Google Play and, while the IT giant Google does not always manage to keep malicious applications away,[4] it is one of the most secure platforms to use. Of course, security measures are applied in most other websites, although they are nowhere near as extensive as Google's. In most cases, users are keen on downloading apps from unknown sites after they see a link on various platforms, such as Facebook or YouTube.
By default, Android devices are configured not to allow apps from external sources to be installed in the first place. However, many users deliberately switch that function off, exposing their smartphones to potential risks and malware infections. Therefore, turn the security feature back on and avoid third-party sources as much as possible.
Other tips to keep your Android device secure:
- Before installing application, check for permissions it asks for, and ask yourself whether a weather app needs access to read your SMS;
- Always keep your device up to date;
- Install powerful anti-malware software that would detect online treats for you;
- Enable Google Play Protect feature.
Eliminate EventBot malware to protect your finances and privacy
As previously mentioned, EventBot virus might not emit any symptoms, just like many other Trojans do, as they are programmed to operate stealthily. This outlines how important it is to protect mobile devices with security software, and that malware might operate silently in the background for a prolonged time without being noticed. Nonetheless, since the virus actively communicates with a remote server, sends packet information, and performs a variety of other actions, the phone or tablet might suffer from battery drain.
For EventBot removal, employ a powerful anti-malware software and perform a full system scan. Please be aware that not all mobile security tools are effective, as was confirmed by an in depended testing lab AV-Comparatives. Thus, make sure you pick a reliable anti-malware first.
Once you remove EventBot from your system, you should also clear your web browser data and immediately change your passwords for all the apps/accounts. Additionally, you should monitor your online banking to ensure that no illegal transactions are performed. If that is the case, contact your bank immediately and block the account.
How to prevent from getting trojans
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Daniel Frank, Lior Rochberger, Yaron Rimmer and Assaf Dahan. EventBot: A New Mobile Banking Trojan is Born. Cybereason. Endpoint Protection, Detection, and Response.
- ^ Forecast number of mobile devices worldwide from 2019 to 2023 (in billions)*. Statista. Statistics portal.
- ^ One-third of all malware is now mobile. Zimperium. Mobile security company.
- ^ Number of available applications in the Google Play Store from December 2009 to March 2020. Statista. Statistics portal.
