Fast-update.com ads (fake) - Free Guide
Fast-update.com ads Removal Guide
What is Fast-update.com ads?
Fast-update.com is a bogus site using social engineering tactics to trick people

Fast-update.com is a fraudulent website that uses social engineering[1] techniques to trick users into clicking the “Allow” button, which grants permission for push notifications. As a result, users are bombarded with intrusive pop-up advertisements. By potentially utilizing rogue advertising networks[2] that redirect to dangerous websites, the creators of this site demonstrate a disregard for user privacy and security.
Ads that appear on the desktop even when the browser is closed are a clear indication of a suspicious page or adware causing the ads. You may also see pop-ups promoting bogus software or updates, displaying false malware infection alerts, or requesting the installation of cleaning utilities. It is critical not to click on any links contained within these pop-up ads.
Individuals who visit such pages may become victims of deceptive tactics aimed at obtaining personal information, downloading potentially unwanted programs (PUPs),[3] or malware. It is critical to address this issue as soon as possible, especially if the affected machine is accessed by children. It is worth noting that certain push notification spam pages, such as adult and gambling sites, have been known to promote inappropriate content.
| NAME | Fast-update.com |
| TYPE | Push notification spam; adware |
| SYMPTOMS | Intrusive pop-up ads start appearing in the corner of the screen |
| DISTRIBUTION | Shady websites, misleading advertisements, bundled software |
| DANGERS | The website could be using unsafe advertising networks that place ads leading to dangerous pages where people can get tricked into providing their personal information or installing PUPs and malware |
| ELIMINATION | Go to your browser settings and disable push notifications |
| FURTHER STEPS | Use a repair tool FortectIntego to fix any remaining damage and clear your browsers |
Distribution techniques
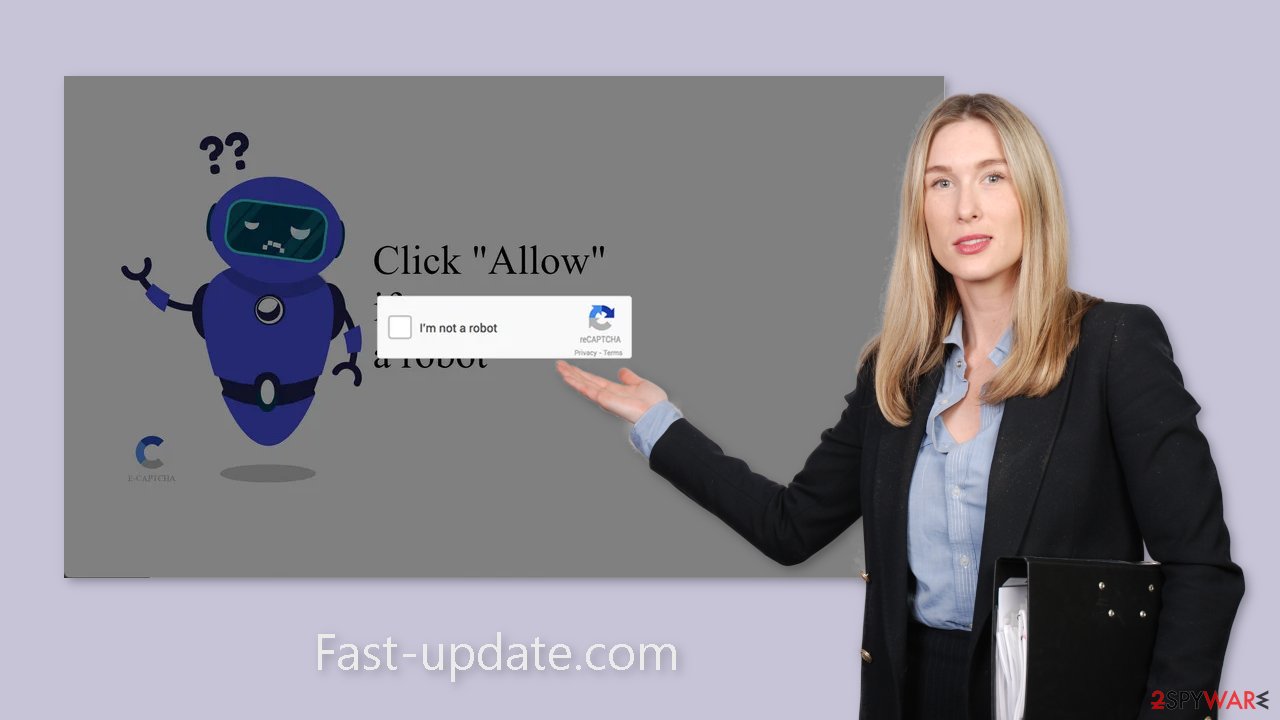
Push notification spam pages, such as Fast-update.com, use deceptive social engineering techniques to deceive users. The appearance of the site may be similar to a captcha verification process, tricking users into confirming that they are not robots. Messages such as these may be encountered:
Type Allow to verify that you are not a robot.
Click Allow to watch the video.
Download is ready. Click Allow to download your file.
Press Allow to verify that you are not a robot.
This scam frequently targets people looking for illegal streaming options for movies or TV shows. Because illegal streaming platforms are unregulated, they are riddled with misleading advertisements and sneaky redirects. Some of these platforms even display bogus “Download” and “Play” buttons that redirect to pages associated with rogue advertising networks.
When possible, it is best to avoid clicking on random links and visiting suspicious websites. Prioritize the security of websites before accessing them. Consider using legitimate streaming platforms such as Netflix or Hulu, which charge a small monthly subscription fee and provide a diverse range of content for users to enjoy.
It is important to note, however, that if the system is infected with adware, such pages may appear without any user interaction. Adware is a type of program that runs in the background and performs malicious tasks without the users' knowledge. Depending on the infection, different methods of removal may be required. A list of potential removal methods is provided below.
Stop push notification spam
If you no longer want to see the annoying pop-ups, you can manually disable Fast-update.com permissions in your browser settings. Keep in mind that if you have an adware infection, this may not work. For the time being, follow these steps:
Google Chrome (desktop):
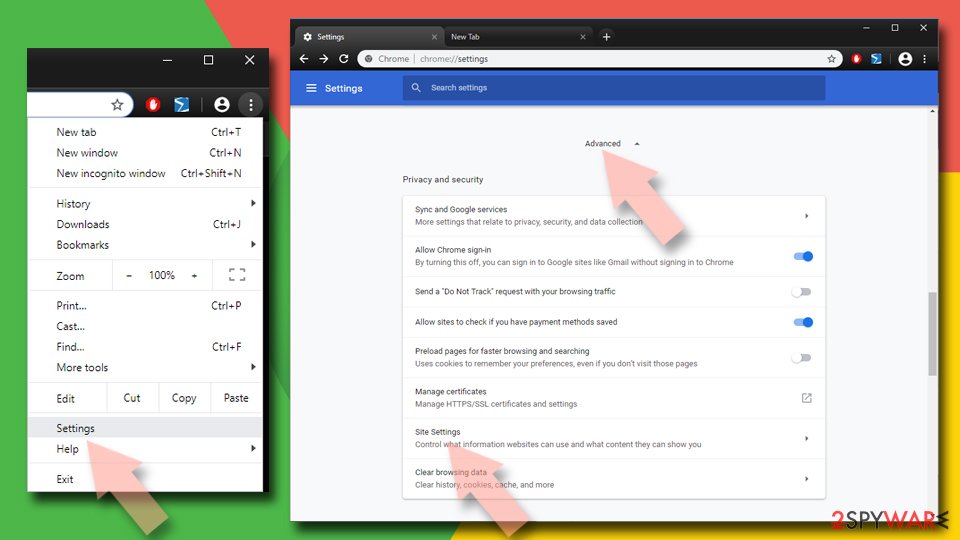
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
![Stop notifications on Chrome PC 1 Stop notifications on Chrome PC 1]()
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android):
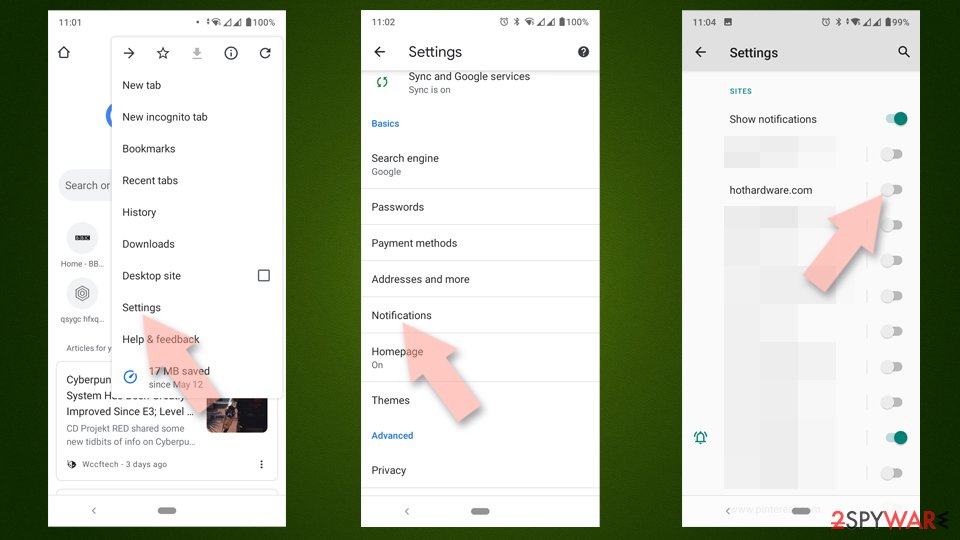
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox:
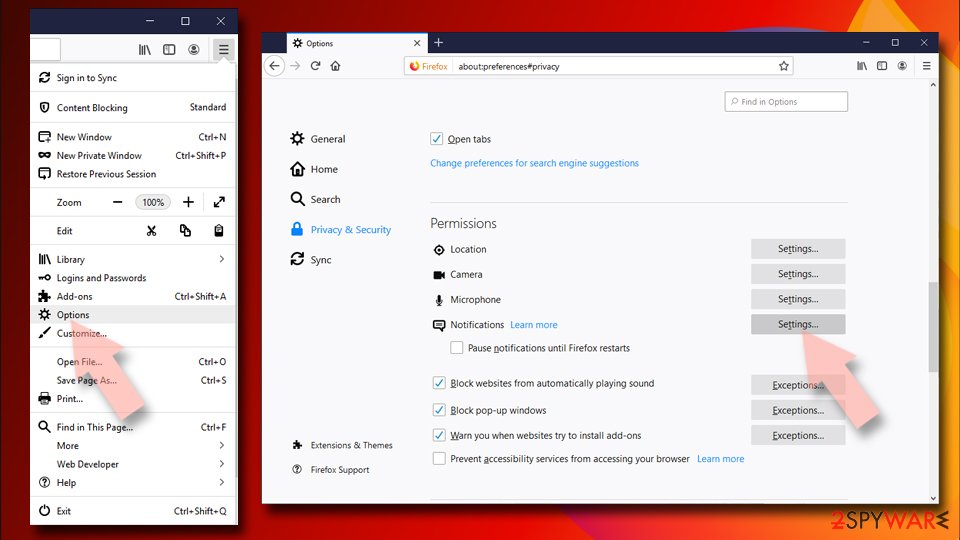
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click Settings button next to it.
![Stop notifications on Mozilla Firefox 1 Stop notifications on Mozilla Firefox 1]()
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari:
- Click on Safari > Preferences…
- Go to Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
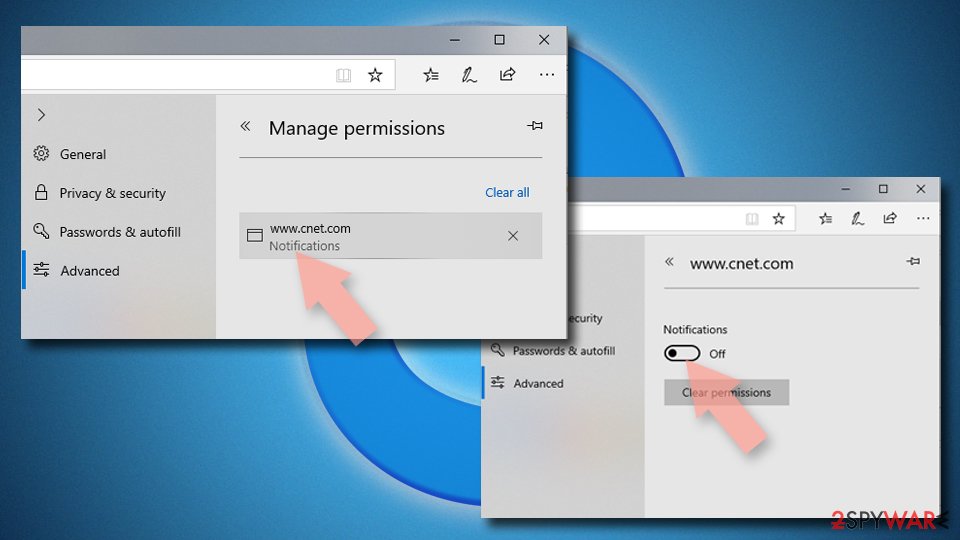
MS Edge:
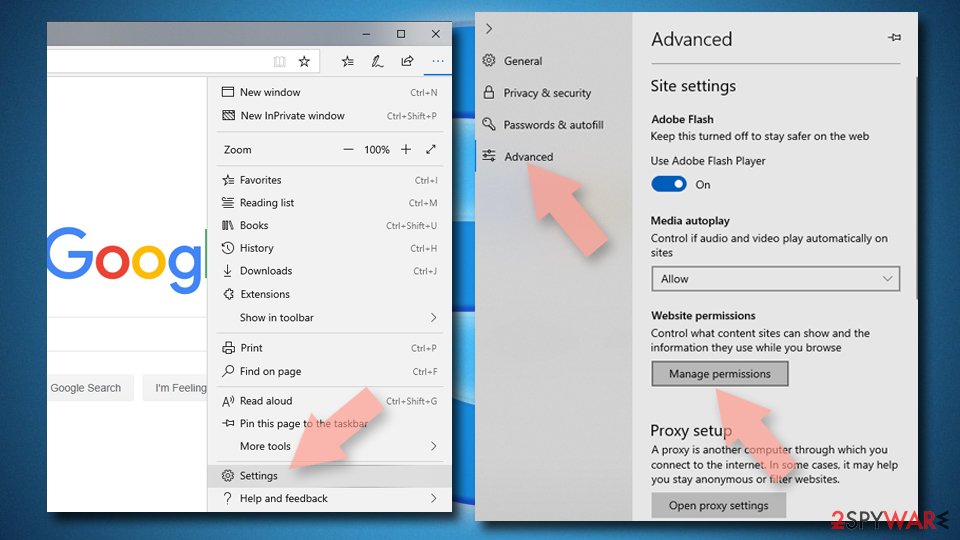
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.
![Stop notifications on Edge 1 Stop notifications on Edge 1]()
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
![Stop notifications on Edge 2 Stop notifications on Edge 2]()
MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Check if you are infected by adware
If the previous method did not resolve the problem and you continue to experience symptoms such as an excess of commercial content, banners, surveys, or redirects, adware may be present in your system. Adware frequently enters the system as part of freeware distributed via various websites.
Adware runs in the background of your computer, generating ads and revenue in the process. To profit from their activities, freeware distribution sites include adware in their installers. They can earn money by using methods such as pay-per-click (PPC), pay-per-view (PPV), and other advertising techniques that are available to anyone.
Manually removing potentially unwanted applications (PUAs) can be difficult, especially if you lack experience. PUAs are frequently disguised as useful tools, such as antivirus software, system optimizers, or media players, by developers. It can be difficult to determine which program is causing the undesirable behavior.
To address this, professional security software SpyHunter 5Combo Cleaner or Malwarebytes that can perform a thorough system scan and automatically remove any PUPs is recommended. These security tools can also help you avoid future infections by alerting you to potentially dangerous downloads. If you'd rather do it yourself, here are step-by-step instructions for Windows and macOS:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
macOS:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
Clear your browsers
After successfully removing the threat, you must take care of your browsers. Shady websites you visit can collect data about your browsing activities using cookies. This includes your IP address, geolocation, websites you visit, links you click on, and online purchases.
Websites and web-based apps typically use them to personalize the user experience, such as by displaying relevant results and suggestions. Fraudsters, on the other hand, can sell them to risky advertising networks and other third parties. Cookies can also be hijacked by threat actors and used for malicious purposes such as data extraction.
Using a maintenance tool like FortectIntego is the simplest way to remove cookies and cache. It can do everything automatically with the click of a button, so you don't have to worry about it. Furthermore, this powerful software can repair a variety of system errors, corrupted files, and registry issues, which is especially useful following a virus infection.
How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Josh Fruhlinger. Social engineering: Definition, examples, and techniques. Csoonline. Phishing.
- ^ Zeljka Zorz. How does a rogue ad network function?. Helpnetsecurity. Cybercriminals and malware.
- ^ Wendy Zamora. What is a PUP? – How to avoid potentially unwanted programs. Malwarebytes. Home security tips and tricks.