News-numefe.cc ads (spam) - Free Instructions
News-numefe.cc ads Removal Guide
What is News-numefe.cc ads?
News-numefe.cc is a fake site set up by crooks to trick visitors into accepting pop-ups

News-numefe.cc is a fraudulent website employing social engineering[1] tactics to deceive individuals into subscribing to push notifications. Users are prompted to click the “Allow” button to confirm that they are not robots. Once authorization is given, visitors are bombarded with obtrusive pop-up advertisements, which continue to show even when the browser is closed.
Moreover, these pop-ups might come from rogue ad networks[2] that send people to dangerous websites. Users may be exposed to fraudulent websites that seek to obtain personal data or trick them into downloading potentially unwanted programs (PUPs)[3] or even harmful software.
Several reports state that advertisements for fake antivirus software, software promotions, giveaways, surveys, and other things are shown. It is imperative to turn off these pop-ups because this vulnerability might result in more serious infections, especially if the impacted device is shared. See our detailed guide for more information.
| NAME | News-numefe.cc |
| TYPE | Push notification spam; adware |
| SYMPTOMS | Pop-up ads start appearing in the corner of the screen unexpectedly, sometimes even when the browser is closed |
| DISTRIBUTION | Shady websites; deceptive ads; freeware installations |
| DANGERS | The pop-ups can contain links leading to websites from rogue advertising networks |
| ELIMINATION | Go to your browser settings to disable website permissions |
| FURTHER STEPS | Use FortectIntego to fix any remaining damage and clear your browsers |
Distribution methods
Sites such as News-numefe.cc are rarely seen in search results; instead, they are usually hidden behind unofficial and questionable websites. An illustrative example is the prevalence of these sites on illegal streaming platforms, where deceptive ads, redirects, and fake “Download” and “Play” buttons are common, leading users to open new tabs with potentially harmful content.
You should only browse websites that you are familiar with and can trust. It is safer to use reputable streaming services like Netflix or Hulu because they don't have any security risks. Avoid clicking on random links and ads, even if they seem to offer legitimate goods or services; it's best to go straight to the source.
Another possible situation is that fraudulent pages appear on their own without any input from the user. This could be caused by adware that is hidden in the user's system and causes an overload of advertisements such as pop-ups, banners, and redirects. Adware often enters computers via installations of freeware.

How to disable push notifications?
Below you will find a manual guide on how to take care of your browser. Because push notifications are subscription-based, you will have to disable them yourself:
Google Chrome (desktop):
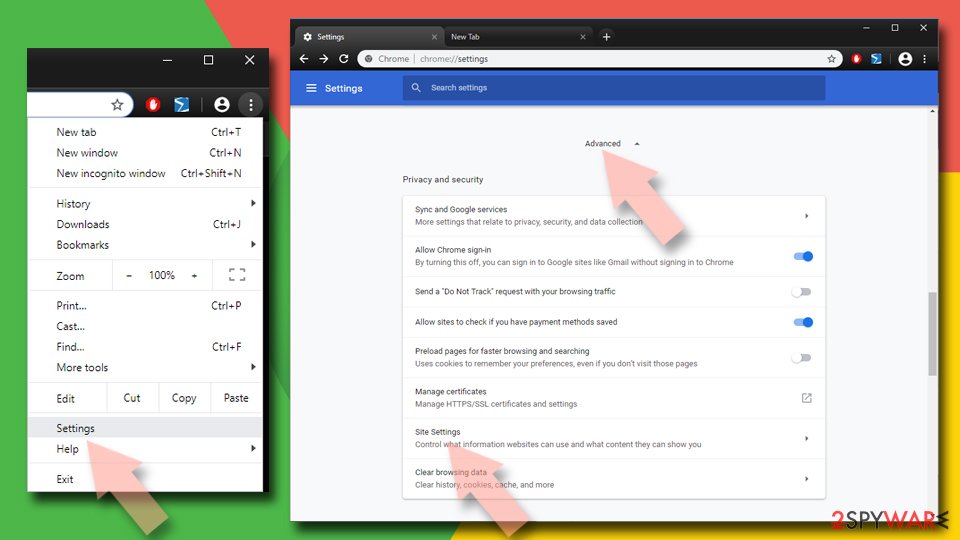
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
![Stop notifications on Chrome PC 1 Stop notifications on Chrome PC 1]()
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android):
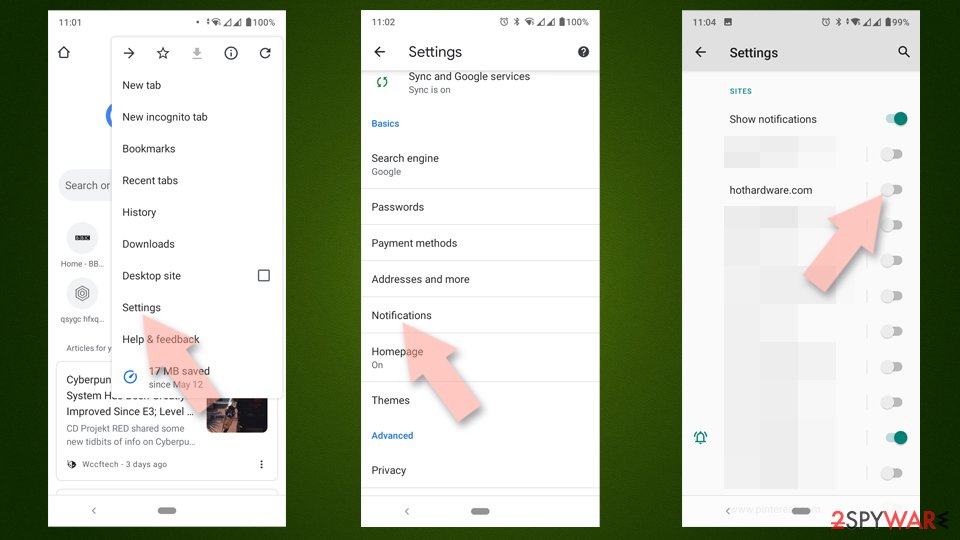
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox:
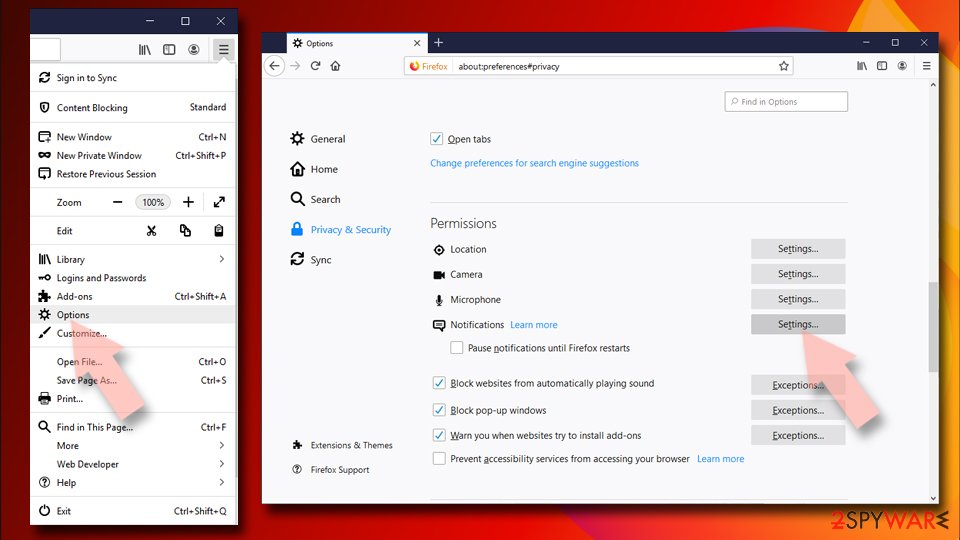
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click Settings button next to it.
![Stop notifications on Mozilla Firefox 1 Stop notifications on Mozilla Firefox 1]()
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari:
- Click on Safari > Preferences…
- Go to Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge:
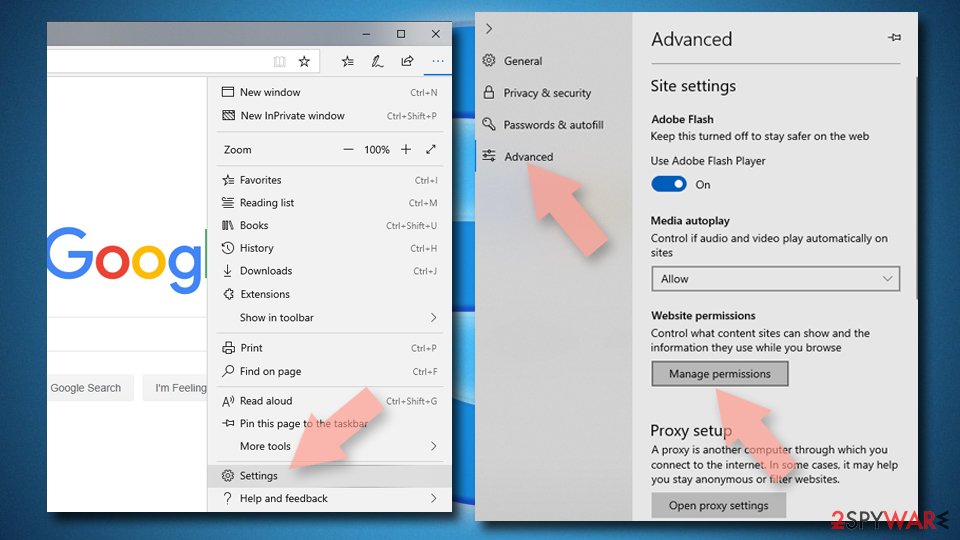
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.
![Stop notifications on Edge 1 Stop notifications on Edge 1]()
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Cookies and cache
If you've been able to effectively block advertisements in your browser's settings, it's time to take care of your browser's health by cleaning the cookies and cache. These techniques are used by almost all websites to track your online activities, saving data such as your IP address, geolocation, websites you visit, and online purchases.
The possibility that advertising networks or other third parties will purchase this accumulated data emphasizes security experts' advice to routinely erase browser data. As an alternative, take into consideration FortectIntego if you're looking for a quick and automated way to get around a tedious manual process. This powerful program helps with registry problems, corrupted files, and system errors in addition to cleaning cookies and cache. It is especially helpful when dealing with issues that arise after a virus infection.
Freeware installations
Adware is often installed on people's computers without their knowledge when they install software from freeware distribution sites. These platforms appear to be “useful” tools by including other programs in the installers. In their hurry, a lot of users often forget about this when installing.
It is imperative that you always select the “Custom” or “Advanced” installation options in order to protect your device. Examine the Terms of Use and Privacy Policy carefully. The crucial stage entails looking over the file list and ticking the boxes next to any programs that aren't linked. When installing software, it is advised to only use official web stores and developer websites for maximum device security.
Remove adware from your system
Examine your system for possible adware infections if you have done the above procedures and you still experience unwanted symptoms like an increase in commercial material, pop-ups, banners, and redirects.
We advise utilizing the SpyHunter 5Combo Cleaner or Malwarebytes anti-malware programs because it could be difficult to pinpoint the exact software that is creating problems. These programs have the ability to automatically scan your computer and remove any risks that are found. The purpose of security software is to alert users before a harmful program may make modifications. Nevertheless, the following instructions are provided for both Windows and macOS computers if you would rather use a manual method:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To entirely remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any suspicious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Social Engineering. Imperva. Learning Center.
- ^ Zeljka Zorz. How does a rogue ad network function?. Helpnetsecurity. Information Security Blog.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. Howtogeek. Technology Magazine.