News-xofiyu.cc ads (spam) - Free Instructions
News-xofiyu.cc ads Removal Guide
What is News-xofiyu.cc ads?
News-xofiyu.cc is a fake site that is used by crooks to generate revenue from ads
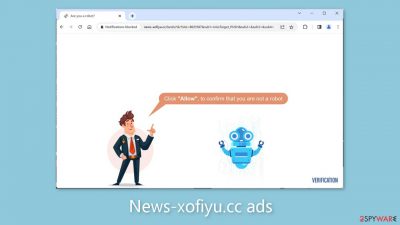
News-xofiyu.cc is a shady website that uses social engineering[1] to trick users into subscribing to push notifications. The website poses as a CAPTCHA verification process, prompting users to click the “Allow” button to confirm their human status. However, once permission is granted, the page bombards users with intrusive pop-up advertisements that persist even after the browser is closed.
These advertisements are most likely generated by rogue advertising networks and may lead users to dangerous websites. As a result, unsuspecting individuals may unknowingly divulge personal information, unknowingly download potentially unwanted programs (PUPs),[2] or inadvertently acquire malware.
| NAME | News-xofiyu.cc |
| TYPE | Push notification spam; adware |
| SYMPTOMS | Annoying pop-up ads start appearing in the corner of the screen after clicking the “Allow” button |
| DISTRIBUTION | Shady websites; deceptive ads; freeware installations |
| DANGERS | Links embedded in the notifications can lead to websites from rogue advertising networks |
| ELIMINATION | Disable push notifications by accessing your browser settings |
| FURTHER STEPS | Use a repair tool like FortectIntego to fix any remaining damage and optimize the machine |
Distribution methods
Rather than being found through search results, people usually come across websites like News-xofiyu.cc while browsing other dubious pages. These pages frequently disguise themselves in platforms involved in illegal activities. Illegal streaming sites, for example, are notorious for displaying deceptive advertisements and clever redirects that can cause the opening of new tabs, leading to websites affiliated with rogue advertising networks.
It is critical to use caution when browsing the internet, and to avoid clicking on random links or visiting unfamiliar websites. The internet is filled with gateway pages that are explicitly designed to redirect users to spam pages that bombard them with push notifications. In addition, the spam site may appear without any user interaction.
This situation can occur if a user's device has been infected with adware, which generates an excessive amount of commercial content such as pop-ups, banners, and redirects. Developers earn money from pay-per-click advertising for each advertisement that is viewed.
Take care of your browsers
Adware's primary goal is to persuade users to click on advertisements, install potentially unwanted applications (PUAs), or install malware. Adware, on the other hand, can collect browsing-related information by using cookies, which are small data files stored on devices. Cookies are not inherently malicious because they allow for the personalization of the user experience on websites and web-based applications.
The problem arises when malicious entities use cookies. Cookies can be used to sell data to third parties and advertising networks. Cookies can be hijacked and exploited for nefarious purposes if the websites you visit or the plugins you use lack robust security measures.
These small data files may contain information such as your IP address, websites visited, links clicked, and online purchase history. It is critical to clear cookies and cache on a regular basis to avoid this information falling into the wrong hands. We recommend using a maintenance utility like FortectIntego to make this process easier. Aside from clearing cookies, such a utility can address various system errors, registry issues, and corrupted files, which is especially useful after a virus infection.
Disable the intrusive pop-ups
According to user reports, News-xofiyu.cc has been displaying deceptive security alerts that masquerade as genuine messages from trusted sources like Norton, Windows, and Google Chrome. These malicious actors employ scare tactics to convince users that their systems are infected with multiple viruses and malware.
What's particularly surprising is that some of these pop-up messages redirect users to the official pages of legitimate security suites, despite the messages themselves being fake. This peculiar behavior might be a result of fraudsters exploiting affiliate programs associated with these security providers.
Push notifications operate on a subscription model, allowing users to manually disable them through their browser settings. To assist you in the smooth removal process, please refer to the step-by-step guide below:
Google Chrome (desktop):
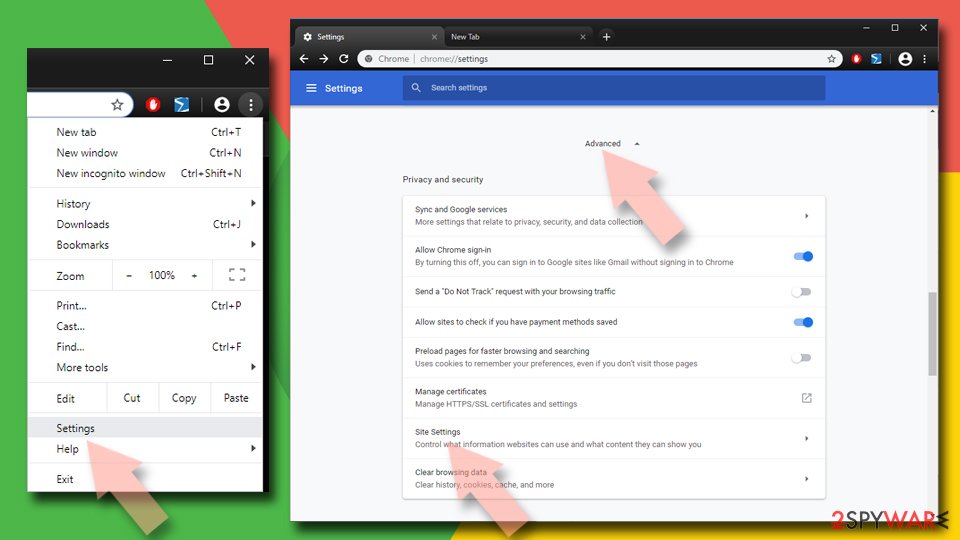
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
![Stop notifications on Chrome PC 1 Stop notifications on Chrome PC 1]()
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android):
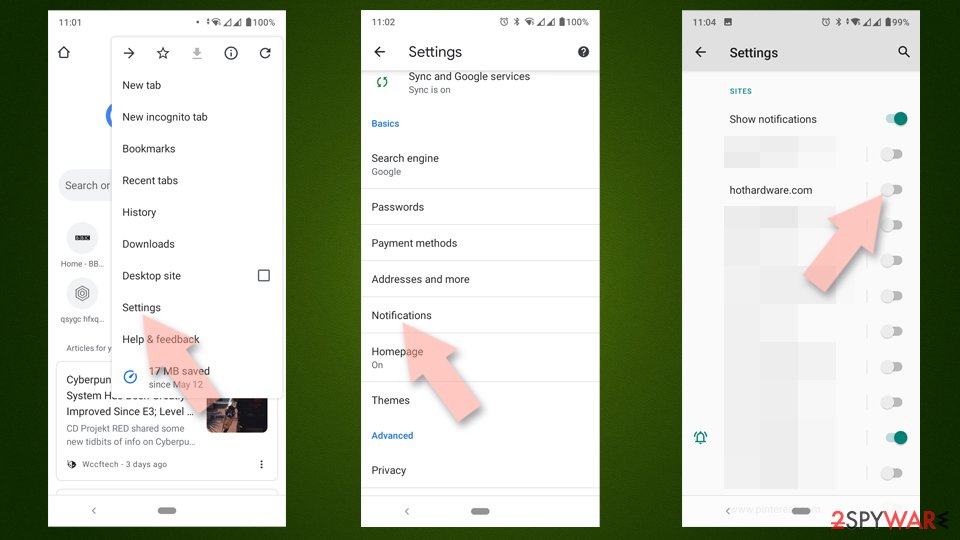
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox:
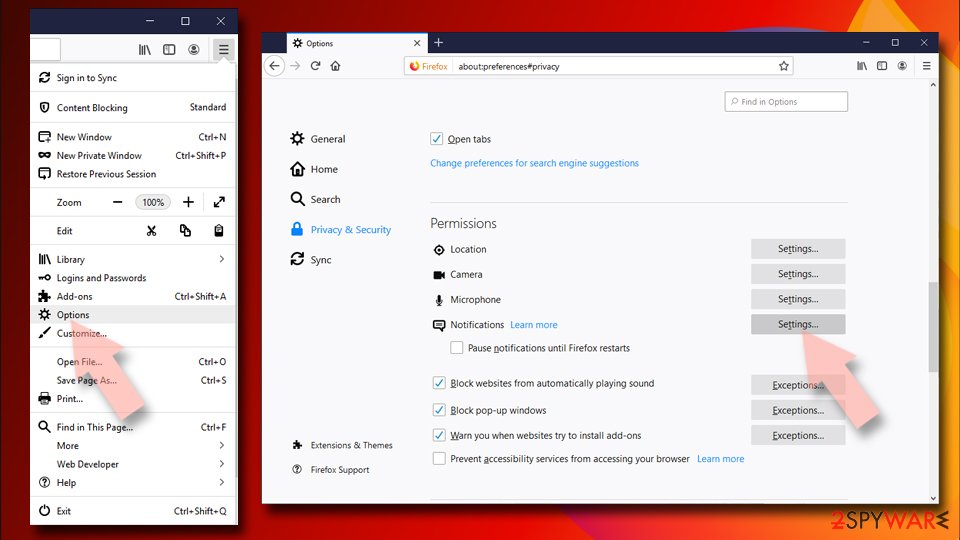
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click Settings button next to it.
![Stop notifications on Mozilla Firefox 1 Stop notifications on Mozilla Firefox 1]()
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari:
- Click on Safari > Preferences…
- Go to Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge:
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
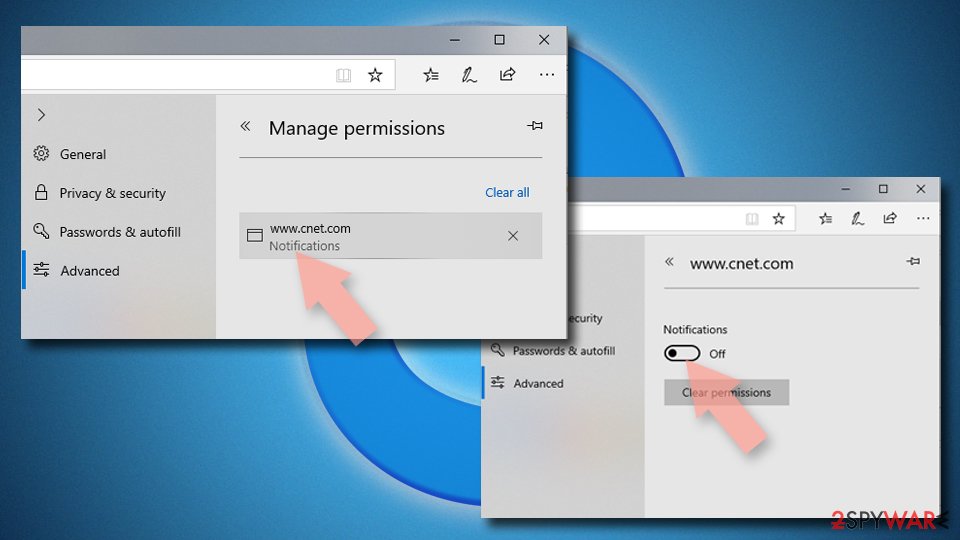
- Under Website permissions, pick Manage permissions and select the URL in question.
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
![Stop notifications on Edge 2 Stop notifications on Edge 2]()
MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Freeware distribution platforms
If you have recently installed programs from freeware distribution sites, peer-to-peer file-sharing platforms, or torrent sites,[3] there is a good chance that they are causing your symptoms. Because they do not make money by giving away software for free, freeware distributors frequently include additional programs in their installers to monetize user activity, such as collecting data about browsing habits and generating ads.
Unfortunately, once these unwanted programs have infiltrated your system, they are difficult to remove. Cybercriminals frequently disguise them as seemingly useful tools to make them more difficult to detect by average users. To reduce risk, it is always best to download and install software from official sources.
Using professional security tools can help ensure that your system is free from intruders. You can utilize SpyHunter 5Combo Cleaner or Malwarebytes to scan your machine, as they will detect any suspicious processes running in the background and remove them completely. Additionally, if you wish to remove recently installed freeware, you can follow our guide for both Windows and Mac machines:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
macOS
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Cynthia Gonzalez. Top 5 Social Engineering Techniques and How to Prevent Them. Exabeam. Information Security.
- ^ Wendy Zamora. What is a PUP? – How to avoid potentially unwanted programs. Malwarebytes. Cybersecurity Tips, Tricks and How-Tos.
- ^ Brad Haddin. 4 risks of using torrents. Creative. Tech Opinions.