Swift Searcher browser hijacker (virus) - Free Instructions
Swift Searcher browser hijacker Removal Guide
What is Swift Searcher browser hijacker?
Swift Searcher is a browser-hijacking app that should not be trusted
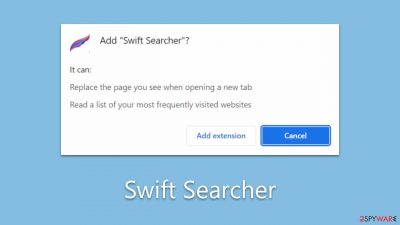
Swift Searcher is a browser hijacker that primarily targets users of Google Chrome and other Chromium-based browsers like Edge. Once installed, it immediately modifies the browser settings without user consent. Specifically, it alters the homepage and new tab preferences, directing users to search.swiftsearcher.com.
A notable distinction arises when users attempt to conduct online searches. Instead of getting unbiased results, all search queries get routed through Bing. However, these aren't the standard Bing search results one might expect. The results from this hijacker are riddled with an increased number of promotional links and intrusive ads, which can be both misleading and disruptive to users.
Additionally, like many browser hijackers, Swift Searcher is suspected of tracking user data, raising potential privacy concerns. If you've inadvertently installed Swift Searcher and wish to remove it from your browser, continue reading this article for detailed steps and guidance.
| Name | Swift Searcher |
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundles, third-party websites, misleading ads |
| Symptoms | A browser extension or an application installed on the device; homepage and new tab address set to search.swiftsearcher.com; ads and sponsored links in search results and elsewhere; promotes other potentially unwanted apps |
| Risks | Installation of additional potentially unwanted software/malware, unauthorized sharing of information with unfamiliar entities, and financial losses |
| Removal | You can remove the browser extension by navigating to your browser's settings. Additionally, it's advisable to perform a scan using robust security software SpyHunter 5Combo Cleaner |
| Other tips | After removing all potentially unwanted applications, we recommend you employ the FortectIntego utility to clean your web browsers and repair any damaged system files |
The spread of Swift Searcher and other browser hijackers
Swift Searcher, like other browser hijackers, poses a potential risk to your computer system. To propagate and establish its presence on devices, its developers employ misleading methods which are frequently associated with potentially unwanted programs.
Software bundling is a primary avenue for the distribution of hijackers like Swift Searcher. Many individuals often inadvertently download malicious or unwanted software when they opt for free applications from unofficial platforms. During the setup of these applications, a hurried or uninformed approach – such as skipping certain steps or breezing through without fully understanding the implications – can inadvertently permit additional unwanted components like Swift Searcher to be installed.
To counteract these stealthy installation tactics, users are advised to exercise caution during the setup phase of any software obtained from non-official sources. Utilizing the Advanced or Custom installation options and diligently unchecking pre-selected boxes can prevent unwanted additions. Additionally, it's essential to be vigilant for deceptive elements—these might include barely noticeable fine print or craftily positioned buttons meant to mislead.
Moreover, indulging in software cracks or visiting websites that provide pirated software amplifies the risk manifold. Not only are such practices illegal, but these platforms can also serve as hubs for more malicious threats like ransomware. To safeguard one's computer, it's always recommended to download software only from trustworthy and legitimate sources.
The hidden dangers of browser hijackers
While Swift Searcher might not directly introduce malware to your system, its effects are far from benign. Its primary mode of disturbance is the persistent display of potentially unwanted applications (PUAs) through ads strategically positioned in the user's browser. Such unsolicited advertisement not only diminishes the browsing experience but also escalates the chances of unintentional downloads of other similar browser hijackers or intrusive adware, thereby intensifying the issue.
What amplifies the threat of Swift Searcher is its capability to monitor user activity. Leveraging tools like tracking cookies or web beacons, this hijacker systematically collects a diverse range of user data. This includes, but isn't limited to, search queries, visited sites, interactions like link clicks, timestamps, device specifics, ISP details, and more.
The depth and breadth of this data acquisition present alarming privacy implications. There's the ever-present danger that this information, once harvested, could be misused or traded with third-party entities, thus amplifying potential hazards.
Another notable aspect of hijackers like Swift Searcher is their tenacity. Once embedded, they institute changes to browser settings that generally persist unless the software is wholly deactivated or purged. Given the myriad risks and absence of any tangible benefits linked to Swift Searcher, it's emphatically recommended to excise it at the earliest. Allowing it or any analogous PUA to operate continuously only augments vulnerabilities and jeopardizes your online security.
Identifying and Preparing for Swift Searcher Removal
Recognizing the intrusion of Swift Searcher is the initial step in regaining control over your browsing experience. Here's what you need to be aware of:
- Symptoms of hijacking: The most overt indicators of a hijacked browser include an unexpected change in your homepage or default search engine. Other signs to watch out for are an influx of unanticipated ads or pop-ups, sluggish browser performance, and new, unfamiliar browser extensions or add-ons that appear without your initiation.
- Initial response: If you encounter any of the aforementioned signs, proceed with caution. Avoid engaging with suspicious or unexpected ads, and do not download or install anything the hijacker suggests or prompts.
- Security software update: Before taking further action, ensure that your antivirus or anti-malware software is current. Tools like SpyHunter 5Combo Cleaner or Malwarebytes can often identify and assist in removing threats like browser hijackers, safeguarding your system from further unwanted changes.
Equipped with this knowledge, you're now better positioned to address the Swift Searcher hijacker and restore your browser's intended functionality.
Swift Searcher removal
While browser hijackers are generally less harmful than malware, they can still disrupt a user's browsing experience and potentially compromise their privacy due to data tracking methods. Such applications should not be overlooked or permitted to run in the background. To remove the unwanted app, you will have to access your browser settings:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
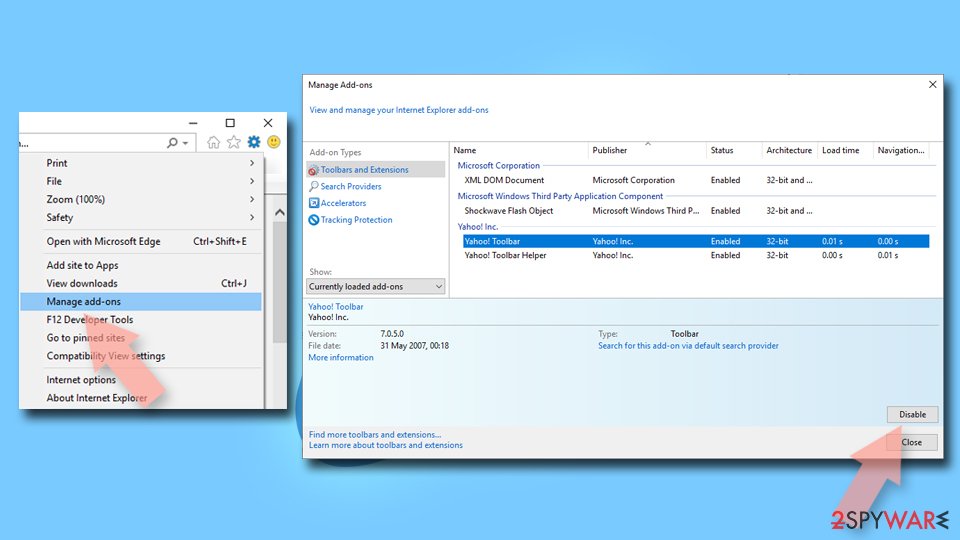
Internet Explorer
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
Clearing your browsers of cookies and other tracking elements is crucial to prevent ongoing tracking by third parties. The most straightforward approach to eliminate residual files is by using a repair and maintenance tool like FortectIntego. However, if you prefer a hands-on approach, you can also manually tackle this by adhering to the following steps:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
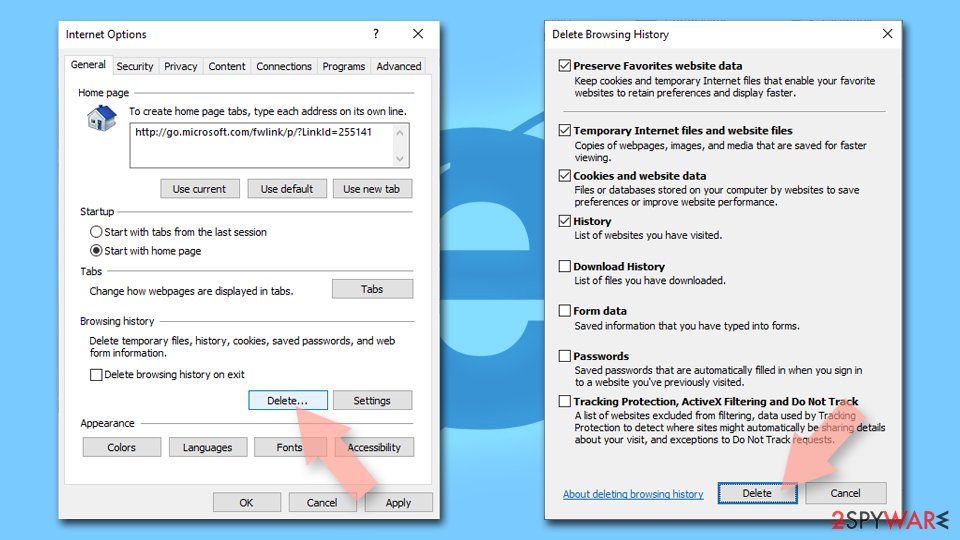
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
![Clear temporary files from Internet Explorer Clear temporary files from Internet Explorer]()
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.