Update-mac.com ads (fake) - Chrome, Firefox, IE, Edge
Update-mac.com ads Removal Guide
What is Update-mac.com ads?
Update-mac.com ads might show up on your desktop one day – do not click them
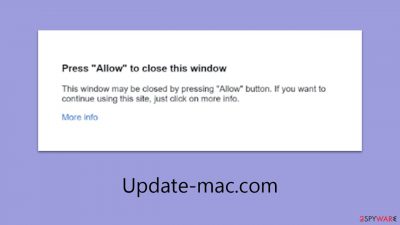
Update-mac.com is an illegitimate website devised by cybercriminals to mislead internet users. The main tactic of these scammers is to convince individuals that accepting push notifications is a normal verification step, urging them to click the “Allow” button in a prompt. They employ sophisticated phishing strategies that might not be immediately apparent to the victims.
Users typically encounter Update-mac.com through intrusive pop-ups that appear over other applications, not just within the browser. This not only causes annoyance but also poses a significant risk if the links or messages are interacted with. Clicking on these can redirect users to harmful sites, leading to potential financial scams, downloading of dangerous software, or sharing personal information with nefarious parties.
We strongly advise against engaging with these pop-ups. Instead, users should disable Update-mac.com notifications through their web browser's settings. This article provides a guide for this process. It's crucial to be vigilant as those who encounter these pop-ups are susceptible to phishing and other online threats. Additionally, it's wise to inspect the device for any signs of adware or malware infections.
| Name | Update-mac.com |
| Type | Push notifications, ads, pop-ups, scam |
| Distribution | Users allow push notifications after they click the “Allow” button within the prompt |
| Symptoms | You may start seeing intrusive pop-ups on your desktop at varying times |
| Risks | Notifications sent by the site could potentially lead you to unsafe websites, which may, in turn, cause malware infections, monetary losses, or exposure of your personal information to harmful entities |
| Removal | To block the intrusive pop-ups, you need to access your browser's settings section. Also, perform a scan with SpyHunter 5Combo Cleaner anti-virus to check for infections |
| Other tips | It is important to clean your browsers after removing potentially unwanted programs from your system – use FortectIntego for quick and reliable results |
Push notifications and pop-up ads might look similar, but they are not the same
It's easy to mix up pop-up ads with push notifications due to their similar appearance. Both emerge in separate windows, showcasing advertisements and have a comparable look. While their ultimate goal is the same – to generate advertising revenue – their mechanisms differ significantly.
Generally, pop-up ads are activated when a user visits a website that displays them. Users have the option to avoid these sites to sidestep intrusive pop-ups and other bothersome ads. In contrast, Update-mac.com ads utilize a different approach by leveraging the browser's push notification API (Application Programming Interface).
This means that push notifications from Update-mac.com persist, regardless of the user's current website, and can even appear when the browser isn't actively in use. For instance, users might be interrupted and pulled out of full-screen mode during video playback or gaming sessions if they have a web browser operating in the background.
The scam techniques used by scammers
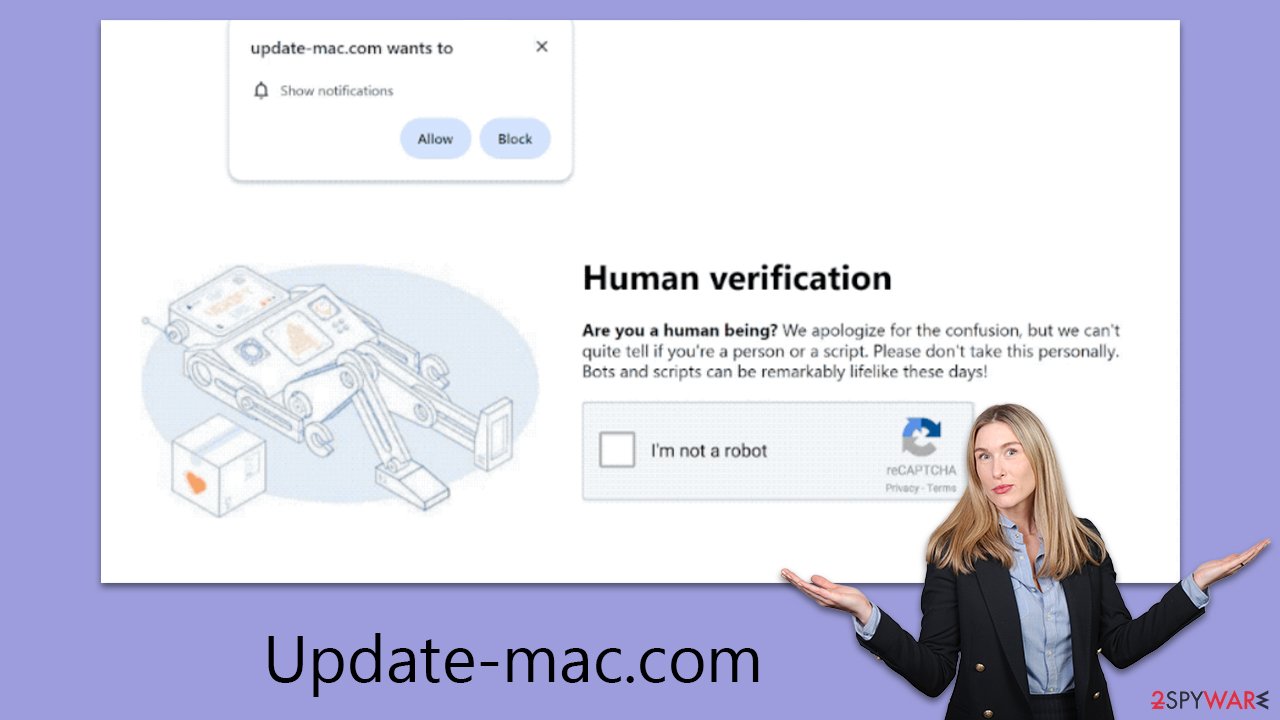
Scammers are increasingly using push notifications as part of sophisticated schemes to trick internet users, often imitating common online practices. The ruse usually starts with an innocuous message prompting the user to enable notifications.
These messages are cleverly crafted to exploit users' trust and their familiarity with standard internet interactions. Some of the most frequently used messages include:
- “Click Allow to confirm you're not a robot.” This message takes advantage of users' familiarity with human verification methods like captchas, lending the scam an air of legitimacy.
- “If you are 18+, click Allow.” This acts as a bogus age verification step. Since many authentic websites use age verification, this seems trustworthy to many users.
- “Click 'Allow' to win a prize and pick it up from our store!” This deceptive lure of a nonexistent giveaway and promised rewards is entirely false, with no real prizes or winners.
- “Click Allow to watch the video.” This often features a fake video GIF about to play or mimics the format of a YouTube video, further deceiving the user.
Awareness of these deceptive techniques is crucial for maintaining online safety and avoiding falling prey to these push notification scams. It is vital for users to be educated and vigilant, recognizing that such scams are not merely nuisances, but can lead to more severe consequences like privacy breaches and financial losses.
Users should be skeptical of prompts that appear too good to be true or out of context, especially on unfamiliar websites. It's also important to regularly update browser settings to block unwanted notifications and to use reliable antivirus software to detect potential threats.
Ultimately, a proactive approach to internet safety, including a critical assessment of online requests and regular updates on cybersecurity trends, is the best defense against these sophisticated push notification scams.
Removal of unwanted ads and adware
While receiving numerous push notifications from sites like Update-mac.com is bothersome, it's important to note that it doesn't necessarily mean your system is infected. However, the possibility of adware or other malicious software shouldn't be dismissed. Adware is known for redirecting users to harmful websites and embedding dangerous links, so conducting a thorough system check is a wise precaution.
Employing powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes can be effective in identifying and eliminating potential threats. These tools excel in scanning your system, detecting, and removing a variety of threats, ranging from adware to more serious malware, thereby ensuring a more secure online environment.
After removing any threats, it's advisable to clear cookies and other web data to completely remove any remnants of the infection. Tools designed for this purpose are particularly useful. They not only help clean your digital environment but also repair any damage caused by malware, restoring your system to its best condition.
To stop unwanted push notifications, you need to unsubscribe from them in your browser settings. The steps for this vary slightly among different browsers but usually involve accessing the site settings and revoking the site's permission to send notifications.
Detailed instructions for this process, specific to various browsers, are included in the provided removal guide. Following these steps can effectively eliminate unwanted push notifications and help you regain control of your online experience.
Google Chrome
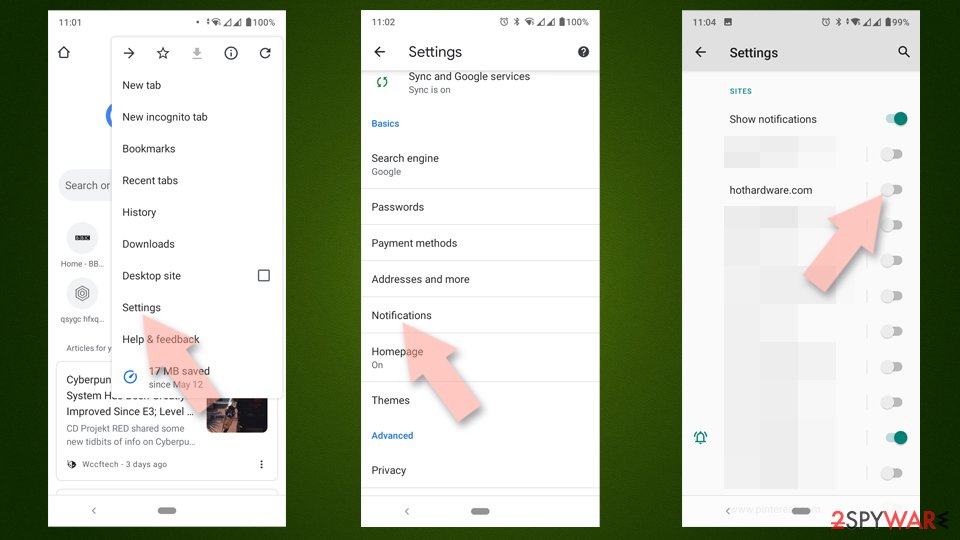
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android)
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off position).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Internet Explorer
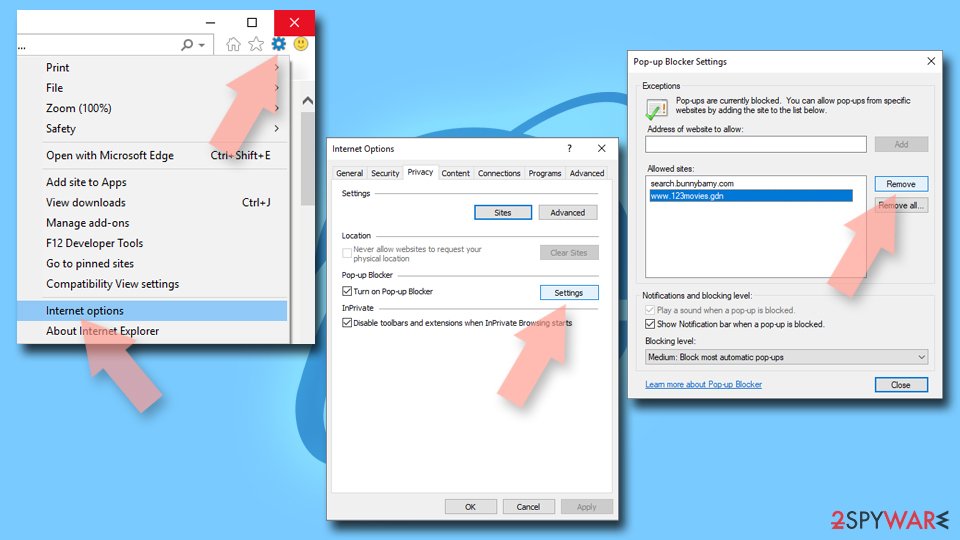
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
![Stop notifications on Internet Explorer Stop notifications on Internet Explorer]()
- Locate the web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.