WannaCash ransomware (Decryption Methods Included) - updated Oct 2020
WannaCash virus Removal Guide
What is WannaCash ransomware?
WannaCash is a cryptovirus which encodes data and demands to transfer the ransom to the Yandex wallet
However, our security researchers note that there are alternative ways how you can recover files encrypted by WannaCash virus without paying the ransom. The text file как расшифровать файлы.txt contains various scary claims, so it may seem that the best option is paying. However, we cannot stress enough how dangerous can Russian hackers get. Especially, when this threat has already released a few major versions. The most recent one, WANNACASH NCOV ransomware was released into the wild in March 2020, almost two years after the initial release of the original version.
It now uses double the encryption because relies on AES and RSA method mix and delivers the same Как расшифровать файлы.txt file as the money-demanding ransom note. This variant uses the pattern of extensions and renames files with Файл зашифрован. Пиши. Почта clubnika@elude.in [number].WANNACASH NCOV v310320 marker, according to the report from virus researcher.[2] Even though, this family uses the Russian language, there is still a possibility that malware occurs on devices in various countries all over the world.
| Name | WannaCash |
|---|---|
| Type | Ransomware |
| Cryptography | AES 256 and RSA-1024 |
| ransom note | как расшифровать файлы.txt – file contains contact information and instructions, scary allegations, and encouragement to pay the ransom |
| File markers | WannaCash compresses files and adds файл зашифрован to their names. These tactics change and malware also adds prefixes, renames files entirely. Some of the marker versions include .wannacash; .punisher; File encrypted [original_name].zip; .happy new year; Файл зашифрован. Пиши. Почта clubnika@elude.in[number].WANNACASH NCOV v310320 |
| Amount of the ransom | 4999 RUB and the amount may get changed per each victim |
| Payment platform used | Yandex.Money |
| Targets | People located in Russia or Russian-speakers |
| rELATED FILES | lock.exe; keys.exe; key.txt; Decrypt files.txt; chrome.zip; |
| Distribution | Might come hidden inside the malicious attachment via spam emails and get triggered when the user enables the macro malware added to the document or executable file, hyperlink included in the notification itself |
| Elimination | You should get rid of WannaCash virus and other similar sophisticated infections with professional tools, like anti-malware programs and security software |
| repair | You can remove WannaCash ransomware damage with PC repair tools like FortectIntego or optimization software that is designed to keep the system okay |
Usually, infections like WannaCash ransomware reach the targeted systems via email. They might come hidden inside the letters as innocent attachments that are hard to identify. Once WannaCash virus settles on the system, it starts encrypting the most widely used files on the computer, including the following ones:
- .doc; .docx; .xls; .xlsx; .xlst; .ppt; .pptx; .rtf; .pub; .pps; .ppsm; .pot; .pages;
- .indd; .odt; .ods; .pdf; .zip; .rar; .7z; .jpg; .png;
- .mp4; .mov; .avi; .mpeg; .flv; .psd; .psb;
The ransom note by WannaCash virus is dropped after a successful data encryption[3]. People are asked to pay 4999 RUB for WannaCash decryption software. Additionally, they are urged to do so as the criminals claim that there is not much time left. Otherwise, random data will be deleted after every 10 minutes. However, people should not fall for these deceptive promises. 
All files of the following extensions were encrypted:
.doc .docx .xls .xlsx .xlst .ppt .pptx .accdb .rtf .pub .epub .pps .ppsm .pot .pages .odf .odt .ods .pdf. djvu .html .txt .tib .iso .dat .zip .rar .7z .gzip .gz .jpg .png .mp4 .mov .avi .mpeg .flv .gif .psd .psb .veg
——- ————————————————– ————
We guarantee that you can safely and easily recover all your files.
Contact us.
mail: wannacash@rape.lol
spare mail: help73@tutanota.com (use only if the first does not respond within 24 hours)
Indicate your identifier in the letter
————————————————– ——————-
Your identifier: D061-7E **
———————– ———————————————-
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third-party programs, this can lead to permanent data loss.
WannaCash ransomware similar to other cyber threats is designed to generate illegal profits. People are tricked to obey the rules of the attackers which might lead to financial losses rather than effective WannaCash decryptor. Thus, our experts do not recommend you to agree to pay the ransom.
Instead, you should remove WannaCash ransomware from your system to avoid further damage. For that, only professional tools can help you as there are numerous components related to this virus that can be hidden inside your PC. You must get rid of them all if you want to protect your computer successfully. Get FortectIntego for any file recovery needed in the system folders.
You need to rely on professional tools to avoid any additional damage, so get an anti-malware tool for cryptovirus termination. After the antivirus programs complete WannaCash ransomware removal, you will be able to start thinking about data recovery. We have prepared multiple methods that can help you retrieve all or even individual files encrypted by WannaCash ransomware. The list of effective data recovery tools is presented at the end of this article. 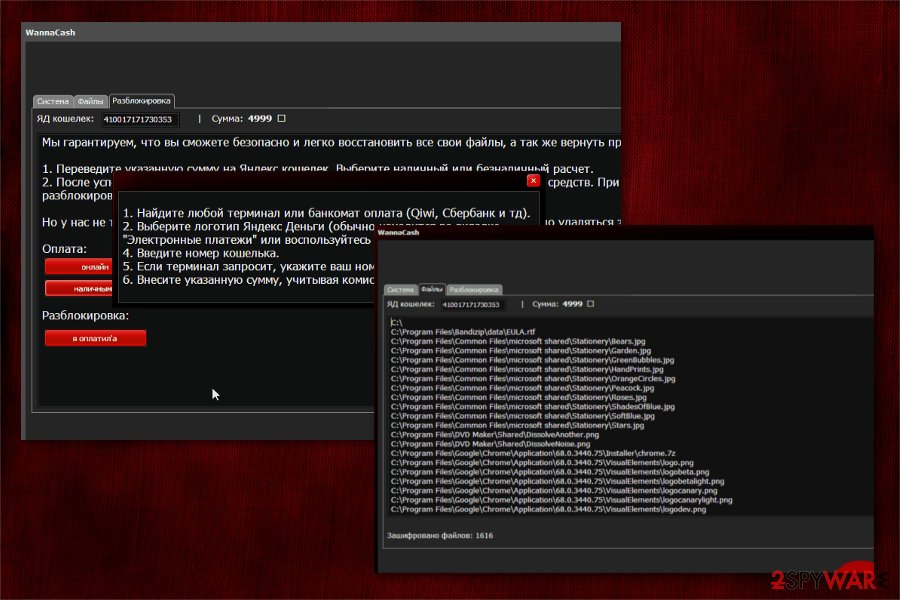
WannaCash ransomware virus comes back in 2020
WANNACASH NCOV ransomware virus came out in March 2020, when the world was paralyzed and in lockdown due to the Coronavirus pandemic, but many people try to take advantage of such a situation, especially malicious actors. This is not the first version after the initial WannaCash, but other variants only carried the initial code and were released back in 2018, mainly.
Throughout those years ransom note evolved to a normal text file with a message about encryption, but all the other features remained the same. What comes different with WANNACASH NCOV ransomware?
First, WANNACASH NCOV ransomware adds a lengthy file marker to encrypted files and runs destructive processes in the background to avoid detections and quick virus removal. As for encryption, it is still the main purpose of the virus, but this particular version relies on AES and RSA encryption algorithm mix that ensures complete changes in the original coding of your common files.
However, all these changes affect the WANNACASH NCOV ransomware removal as well. As always, ransomware creators prefer emails for contacting them, but writing via clubnika@elude.in, clubnika@cock.li is never recommended. There are too many incidents when paying victims are left with unrecovered and damaged files. You better remove malware with AV tools.[4] 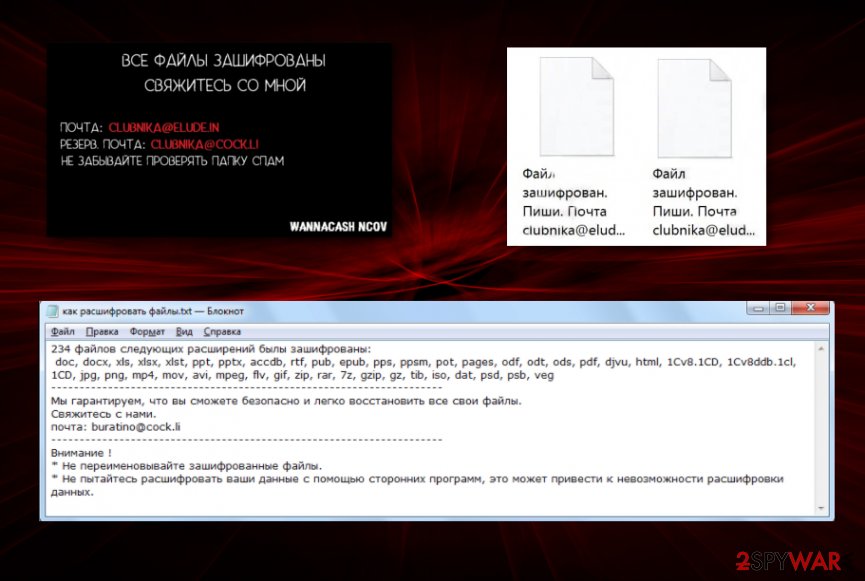
Все значимые файлы на ВАШЕМ компьютере были заархивированы и зашифрованы при использованием AES-256-CBC + RSA 1024bit шифрования.
———-
Я гарантирую, что ВЫ сможете безопасно и легко восстановить все свои файлы.
Чтобы подтвердить мои честные намерения, отправьте мне на почту 2 любых файла, и ВЫ получите их расшифровку.
почта: clubnika@elude.in
резеврная почта: clubnika@cock.li – Если не отвечаю в течении суток, пишите на резервную почту.
не забывайте проверять папку спам !
———-
У ВАС есть ровно 7 дней на связь со мной. 09.04.2020 числа в расшифровке ВАМ будет отказано,а ВАШ ключ дешифровки в автоматическом порядке удален. Я предупредил.
———-
* Не пытайтесь расшифровать ваши данные с помощью сторонних программ, это может привести к повреждению или другим неприятным для ВАС последствиям.
* Крайне не рекомендую обращаться за помощью на форумы антивирусных компаний. Только лишь потеряете время на ожидание отрицательного ответа.
__________
WANNACASH NCOV v310320
1705
66,01 сек.
Spam email attachments might hide the payload of ransomware
Even though the inbox might seem like a safe place, criminals distribute infected emails to spread cyber threats. Usually, the malware comes as an attachment which might mimic innocent documents, such as invoices or shopping receipts. Users who fail to identify an infection and open the attachment infiltrate a file-encrypting virus on their systems.
Likewise, it is vital to monitor your inbox. Always be cautious that cybercriminals disguise as well-known companies or brands to trick novice PC users. Never open any suspicious attachments and if you have any doubts about the legitimacy of the letter, contact the company directly and ask for confirmation.
Look out for any red flags and make sure to delete any emails that:
- state about financial information;
- include files attached or hyperlinks in the notification itself;
- are send from unknown senders;
- contains grammar mistakes or typos;
- ask for additional content agreements or offers to enable macros.
Terminating WannaCash ransomware virus safely
Virusi.bg[5] team warns that since ransomware-type infections are highly advanced, they are programmed to stay persistent. It is not only hard to remove WannaCash ransomware by yourself but also might be dangerous. You can either damage your system or the malware might reappear in the future.
Thus, only the automatic WannaCash ransomware removal process is safe. For that, you should install reliable security tools, such as SpyHunter 5Combo Cleaner, or Malwarebytes. They will help you detect and uninstall all ransomware-related components and clean the system from other cyber threats.
For any damage caused by WannaCash ransomware virus in system folders or alterations made to your programs and OS functions, rely on FortectIntego because such PC repair tools can check and even fix corrupted files or affected data on the computer. This is the program that helps to improve the performance of the affected machine. Then you can go further and focus on data recovery options. Some of them are listed below.
Getting rid of WannaCash virus. Follow these steps
Manual removal using Safe Mode
Booting your system into Safe Mode can help you disable the virus.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove WannaCash using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of WannaCash. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove WannaCash from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by WannaCash, you can use several methods to restore them:
Retrieve corrupted files with Data Recovery Pro
This professional software was primarily developed to recover deleted or damaged data after the system crash. However, experts note that it might be useful in case of ransomware as well.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by WannaCash ransomware;
- Restore them.
Get back data with Windows Previous Versions Feature
The first thing to do before using this option is to check whether the System Restore function was enabled before.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Using ShadowExplorer to recover encrypted files
ShadowExplorer software is an excellent method to recover compromised data if the ransomware hasn't deleted Shadow Volume Copies from the system.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Professional WannaCash decryptor is still in development.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from WannaCash and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Yandex.Money. Wikipedia. The Free Encyclopedia.
- ^ Alex Svirid. New variant WannaCash Ransomware. Twitter. Social media platform.
- ^ Margaret Rouse. Encryption. TechTarget. Computer Glossary, Computer Terms.
- ^ Malicious file analysis. VirusTotal. Online malware scanner.
- ^ Virusi. Virusi. Security and Spyware News.





















