Web Tab Live browser hijacker (virus) - Free Instructions
Web Tab Live browser hijacker Removal Guide
What is Web Tab Live browser hijacker?
Web Tab Live can change the main browser settings and track users' activities online
Web Tab Live is an untrustworthy browser extension that falls under the category of browser hijackers. This add-on, which can be found in the Chrome web store, has few ratings and a small user base. After installation, it immediately modifies important browser settings.
Browser extensions are frequently used to improve the default browsing experience by providing functions like ad-blocking, website protection from dubious sources, and the retrieval of the best discount codes from large databases. There are lots of options. While it is best to only get extensions from legitimate web stores, it is still important to be cautious when choosing additions for your digital environment because certain dangerous extensions may still get past security checks.
This particular application was developed with the intention of making money via data collection and pay-per-click (PPC) advertising.[1] The developers don't appear to care much about providing users with real value. As a result, the search results it produces can point users to misleading or dangerous websites, where they could discover false information, give their personal information to shady parties, download potentially unwanted programs (PUPs), or even make their devices vulnerable to malware.[2]
| NAME | Web Tab Live |
| TYPE | Browser hijacker; potentially unwanted program |
| SYMPTOMS | The homepage and new tab page are changed to webtablive.com |
| DISTRIBUTION | Chrome web store; shady websites; bundled software; deceptive ads |
| DANGERS | The browser plugin can open random links, and redirect users to dangerous websites |
| ELIMINATION | The removal method depends on how the extension was added; you may just have to go to your browser settings or deploy anti-malware tools |
| FURTHER STEPS | Use FortectIntego to optimize your machine and fix any remaining damage |
How browser hijackers are spread online
This extension's platform user base is small, and there are no reviews, so there are questions about its main distribution route. Such programs are frequently distributed through shady websites that engage in illegal activity or through the production of misleading online advertisements. The installation of these extensions is commonly overlooked by users, raising the possibility that they are classified as potentially unwanted programs (PUPs).[3]
PUPs frequently end up on unreliable freeware distribution sites. In order to increase their revenue, the owners of these websites secretly inject extra programs into their installers. They rely on people rushing through the installation procedure and frequently missing the bundled software; sadly, this situation occurs frequently.
It's a good idea to consider the extension's user numbers and any relevant reviews while looking for browser plugins. If reviews are available, it is wise to investigate their veracity. Some people buy bogus evaluations produced by automated bots, which are frequently repeated, lack detailed input, and contain ambiguous words like “Excellent” or “Very happy.”
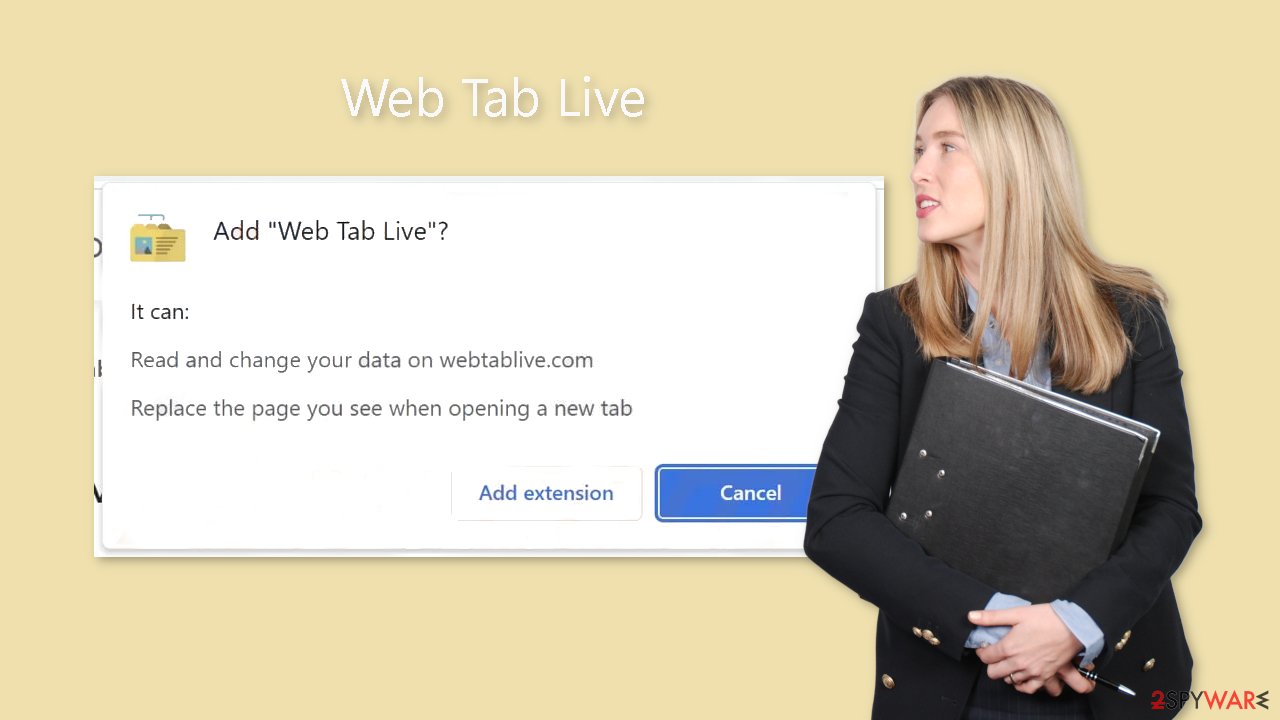
A browser prompt that users get while adding an extension is seen below. It is there to let people know what changes the add-on will make. The notification in this case refers to adjustments to search preferences. However, a lot of users don't read the small print and just start the installation without paying attention.
Safety recommendations
Occasionally, you may also encounter a notification seeking your consent for the use of cookies. These cookies are used to monitor your online activity, including your IP address, the websites you visit, the links you click, and your previous purchases. This data can be misused in a number of different ways. Because of this, we advise having a maintenance program like FortectIntego on your device that can automatically clear your browsers and delete all of this data without a trace.
Installing free software from unreliable sources should be avoided. We are aware that obtaining licenses for software can be expensive, but doing so assures that you can rely on the websites and the software creators to uphold their integrity. For this reason, we recommend incorporating certain habits into your routine to minimize the risk of encountering such issues again:
- Always choose the “Custom” or “Advanced “ installation method
- Read the Terms of Use, Privacy Policy
- The most important part is to check the file list. If you see any additional programs included, untick the boxes next to them
Get rid of the intruder
The first thing you should do is go to your browser's settings and see if the Web Tab Live extension is listed there. It's possible that you unintentionally added the extension, or that you believed it would be helpful after seeing a deceptive advertisement. You can find instructions for the most popular browsers below:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
How to remove PUPs and avoid them in the future
If the previous elimination technique fails, it is very likely that a possibly unwanted program is running on your computer. Simply deleting the addon and changing your settings won't work in this situation. The background intruder won't stop interfering until all of these alterations have been undone.
A Web Tab Live PUA can be difficult to manually remove, especially if it goes by a different name. If you try to do this on your own, you run the danger of unintentionally deleting the wrong programs. Professional security solutions like SpyHunter 5Combo Cleaner or Malwarebytes are excellent at automatically checking your system for suspicious processes and completely removing them together with all associated files. But if you still want to do the removal manually, you may do it by following the detailed steps below, which are provided for both Windows and Mac operating systems.
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ What Is PPC? Learn the Basics of Pay-Per-Click (PPC) Marketing. Wordstream. Advertising Solutions.
- ^ Beware of new malware that steal browser cookies, allow hackers remotely control your web activity. Ciso. From the Economic Times.
- ^ Potentially unwanted program. Wikipedia, the free encyclopedia.










