Corrupt Anti-Spyware
Increasing numbers of potentially dangerous software are being released every day, so the demand for the virus-fighting utilities is very high. Developing reliable and effective antivirus tool is a demanding work and requires constant attention because viruses evolve rapidly, and the antivirus technologies must not fall behind. The computer security specialists have already released numerous antivirus programs helping the users to keep their devices safe. Most of them can do an amazing job. You can read about them in these categories:
However, the cyber criminals have come up with new ways to trick the unsuspecting users by releasing corrupt anti-spyware utilities which convincingly imitate the legitimate ones, but are really designed for extorting their victims. They can look like trustworthy anti-viruses capable of informing you about virus infections and removing them from your computer. Nevertheless, there is one important thing that you need to know before purchasing any of such programs – they are not capable of detecting or removing anything.
What is Corrupt anti-spyware software?
First of all, we should emphasize that these programs should not be confused with scareware. Scareware is usually ad-based and generated by adware viruses, while corrupt antivirus tools are installed on the computer as legitimate applications. The principle of these programs is very similar – they display misleading notifications about the supposedly deteriorating state of the computer’s system. Also known as Rogue anti-spyware, such software usually alerts about malware infections and uses other social engineering tactics to encourage the victims to purchase a full version of the program. In reality, such versions are either non-existent or completely non-functional and created to generate extra profit for the virus creators.
Unfortunately, the users often get hooked and download such programs voluntarily because they are advertised as reputable security tools. These supposed malware removers are usually advertised on the official websites featuring a pleasant-looking design which adds to product’s trustworthy appearance. Of course, if you decide to download such a program on your PC, you are in for a very unpleasant surprise.
How do these fake security utilities work?
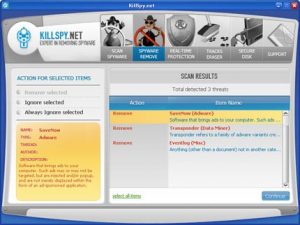
Once the corrupted tools infiltrate the computer’s system they automatically start scanning it for potential threats. Unlike the regular antivirus utilities, these fake ones take significantly less time to display the scan results. A few seconds into the scan, this malware will start displaying notifications about hundreds of threats found on your computer and push you into purchasing a full version of the malware remover to fix these issues. These threatening notifications will not stop until you agree to obtain the suggested software or remove the fake scanner from your computer.
After the payments are made, the newly updated software may report that all the threats have been successfully removed, and your computer is fully protected. In reality, this software is not capable of securing your computer in any way, but merely uses its resources and takes up space. Even more concerning is that the malicious applications may try to interfere with legitimate security software installed on the computer and diminish its functionality. It may even prevent you from installing new trustworthy tools by blocking access to their distribution websites. This way, these potentially unwanted programs take root in the system and significantly aggravate their removal.
2-spyware specialists have analyzed hundreds of reports about rogue anti-spyware programs and have compiled a list of corrupt security software. Every entry on this list provides a software description and introduces its main drawbacks. You can always use the list to check whether the utility you are downloading is legitimate and safe. If you do not find it on our list, do not give it a green light just yet. New rogue software is being released every day, so it is always useful to read through the feedback from other users’ just to make sure the program you are about to download is not some new threat the security experts have not caught up with yet.
How is rogue anti-spyware distributed?
Even though fake malware detectors can be downloaded directly from their developers’ sites, in most cases they infiltrate the computers using a variety of deceptive techniques. Usually, they are installed together with other legitimate software, using the so-called “bundling” technique which allows adding several programs in a single software package and installing them simultaneously. It is not necessarily the legitimate programs these rogue utilities can attach themselves to. They can easily be bundled with other malware increasing the scope of their distribution even more.
Apart from bundling, there are also other ways these malicious security programs can enter the computer. You can inadvertently let them in through fake update installers, email attachments or corrupted advertisements. Briefly said, a rogue anti-spyware may be lurking practically anywhere. Therefore, it is important to keep your system protected with a reliable antivirus software to prevent its installation in the first place. If you do not take action in time, you can already prepare yourself for the long and complex virus removal process.
How can you protect your computer from such malware?
As we have already mentioned, they key of protecting your computer from malicious infections is to check the expert evaluation of the software in question before downloading it on your PC. However, it is naive to rely on security experts to notice all the newest threats that are being released every day. Besides, you might unknowingly or completely accidentally click on some infectious online notifications or links and install rogue anti-spyware on your computer. Thus, it is important to have some extra layer of protection to fend off the primary threats.
Initially, you should equip your device with a powerful firewall. You can use it together with other firewalls from different manufacturers: in case the cyber threat manages to sneak through one of them, the other will definitely stop them. Also, you should obtain a reputable antivirus utility. Just make sure it is reliable and effective. Finally, it is important to be security-minded yourself and avoid visiting obscure websites, downloading suspicious email attachments or clicking on random ads you see while browsing the net. A combination of different security measures should allow you to feel safer and enjoy your browsing without being bombarded with threats from a rogue security tool.
Latest Software Reviews
KillSpy.net scan
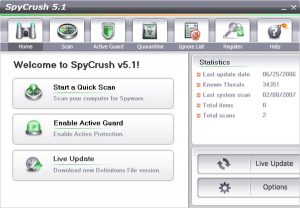
Download SpyCrush for free
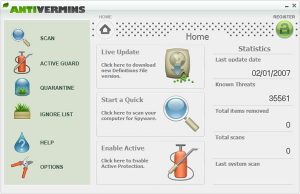
AntiVermeans scanner
Information updated: 2017-05-11