AES-NI ransomware / virus (Removal Guide) - updated Apr 2017
AES-NI virus Removal Guide
What is AES-NI ransomware virus?
AES-NI ransomware virus uses new distribution tricks in 2017
AES-NI virus is a ransomware-type program that is set to encrypt data on a computer using AES and RSA cryptography ciphers. Earlier variants of this virus used to append .aes_ni or file extensions to corrupted records, while the latest version (SPECIAL VERSION: NSA EXPLOIT EDITION) adds .aes_ni_0day file extensions. Following a successful data encryption, the virus creates a text file called !!! READ THIS – IMPORTANT !!! .txt and saves it on the desktop. This file holds a ransom-demanding message and instructions on how to decrypt data locked by the virus. Examination of the virus’ samples revealed that cybercriminals demand a ransom that’s worth 500-1600 US dollars. However, the sum must be paid in Bitcoins (virtual currency). Researchers at 2-Spyware strongly advise victims not to pay the ransom and remove the ransomware instead.
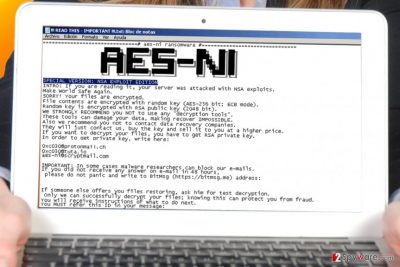
AESNI ransomware is also believed to be an updated variant of AES-256 virus. Just like the new one, the earlier malware version used to attack computers with far-reaching AES-256 algorithm, which searches for .doc, .jpg, .mp4 and other important files, encodes them, and then appends .aes256 file extension [1]. It must be noted that ransomware uses advanced multi-layer encryption tricks to secure victim’s files, therefore it is technically impossible to restore them without knowing the unique key, which the malicious program auto-generates and transmits to criminals’ servers. If you are not specifically familiar with encryption types, it is enough to know that it is AES symmetric encoding technique and RSA asymmetric method. The first one may use 128 or 256-bit cycle of ciphers to encode the files. Naturally, the 256-bit algorithm includes longer cycles and more elaborate cycles of ciphering than 128-bit one. As a result, AESNI virus generates a more exquisite encryption key which is, theoretically, almost uncrackable. However, it does not mean that it is time to fall into despair and grieve over the lost files. Instead, it is advisable to remove AES-NI and use data backups for data recovery.
Cybercriminals know that victims might get attempted to contact the crooks. For that purpose, they provide the following email addresses: aes-ni@protonmail.com and aes-ni@tuta.io. The latest variants of this ransomware provide different addresses – 0xc030@protonmail.ch, 0xc030@tuta.io andaes-ni@scryptmail.com. Even if the amount of ransom does not seem too high for you to pay, keep in mind that you are dealing with cyber criminals. They are not obliged to transfer the decryption key even after receiving the demanded amount of money. Such assumption is more likely taking into account the story of CryptoWall [2]. Therefore, it is unwise to foster hopes and rely on fraudsters‘ sense of conscience. Instead, make AES-NI removal your current priority. For that, experts advise using programs like FortectIntego.

Distribution tendencies and prevention
AES NI ransomware employs traditional malware distribution channels, such as spam messages, malvertising, or infectious torrent files. Although malware researchers repeatedly remind users of the deception techniques that ransomware distributors use (specifically, the hackers‘ tendency to disguise in fake tax reports or invoices), a number of users still fall for the bait. Users should also stay clear of fake emails from the Office of Personnel Management (OPM). Though Locky ransomware prefers hiding in disguising under the name of this institution, due to last year’s data breach, other crooks might take up the habit as well. In general, emails carrying corrupted attachments contain the number of typing and grammar mistakes. They are especially visible in the forged emails of official institutions. The absence of special numeric and PIN codes might alert you as well [3]. In addition, beware of trojans, the harbingers of crypto-malware, and remember that up-to-date security applications serve well as shields against them.
Update April 2016: developer of the virus claims to be distributing it using leaked NSA exploits
The developer of AES-NI now claims that recently leaked NSA exploits (by the Shadow Brokers group) helped him to infect Windows servers with the ransomware on a global scale. The criminal who claims to be the author of this ransomware has been quite active in online forums and Twitter lately. His posts suggest that he has successfully employed ETERNALBLUE exploit that targets SMBv2 protocol. However, this statement remains obscure since the only evidence criminal provided was a screenshot of an ongoing scan of a server for three NSA exploits. However, researchers discovered that the number of infected hosts suddenly increased over the weekend after the exploits were unveiled. However, researchers are not inclined to believe that criminal’s claims are true. Some researchers expressed their opinions[4] saying that the ransomware is transmitted using RDP attacks, not NSA exploits. The alleged author of the ransomware strongly denies it and also blames malware researchers for blocking his email accounts, saying that victims can no longer get an answer from him via email. Researchers never do it because it’s the victim who chooses whether to contact the attacker or not.
Update May 2017: AES-NI developer gives up ransomware decryption master keys
May 2017 marks an important stage in AES-NI ransomware development. The security researcher by the screen name Thyrex has posted AES-NI decryption keys allowing virus victims to recover their data free of charge. The researcher has obtained the 369 unique decryption keys, decryption executable and the user’s manual from the ransomware developer himself via private message on Russian web forum. After a closer analysis of these three components Thyrex found that they really work but are meant to decrypt a specific version of the virus which uses frogobig777@india.com email to communicate with the victims. We insert the download link at the end of the article.
The motifs behind the disclosure of AES-NI keys are quite vague, but according to the software developer, this malware is already outdated, so there is no reason to keep the AES-NI project going. The unknown hacker also talked about the upcoming release of the rest of ransomware keys. If you are infected with the virus version other than frogobig777@india.com, make sure you check back with us later. We will post the recovery tools as soon as they come up.
AES-NI removal methods
The easiest way to remove AES-NI virus is to run a scan with anti-malware software. Programs like FortectIntego or Malwarebytes can banish the virtual threat completely, so our team recommends installing one of those in case you do not have any security programs yet. Note that none of the malware elimination software is capable of decrypting the files. For that reason, you might need an alternative tool or a backup. The latest Windows OS versions have in-built features that helps to easily back up all your files, however, if the ransomware gets administrator access to the system, these backups can be deleted or encrypted as well. Therefore, the only 100% effective backup is the one you created and transferred to a portable data storage device(USB or a hard drive). In general, creating data backups should be an obligatory task taking into account the recent surge of ransomware threats [5]. Even if you do not have additional copies, our further recommendations might be of use. Take care of AES-NI removal and then proceed to the following steps.
Getting rid of AES-NI virus. Follow these steps
Manual removal using Safe Mode
If you are willing to remove the ransomware from your computer, you can find out that it blocks your security software. To overcome this issue, try rebooting your computer to Safe Mode with Networking.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove AES-NI using System Restore
If Safe Mode with networking does not help, you can try System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of AES-NI. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove AES-NI from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by AES-NI, you can use several methods to restore them:
Data Recovery Pro solution while trying to decrypt files encrypted by the ransomware
If you do not possess any backup copies of your encrypted files, try using this application for file recovery. It is a practical application when you cannot find missing files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by AES-NI ransomware;
- Restore them.
Using Previous Windows Versions feature to recover files encrypted by the virus
If System Restore was enabled on your computer before infiltration of the defined ransomware, you can try using the following steps:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
The benefits ShadowExplorer
Rarely, file-encrypting threats access shadow volume copies. In this regard, there is little information whether the discussed ransomware deletes them. The program recreates the corrupted files according to the patterns of shadow volume copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
AES-NI decrypter
A decrypter for AES-NI version that indicates frogobig777@india.com email as means of communication with the criminals have just been released and you can download it by clicking this link. Enter this password to unlock the Zip file: 6bvlWD9yz3yBtQyOhtAqFheg.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from AES-NI and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Doug Lovell. How safe is safe? AES 256 encryption and your data.. CanadianCloudBackup. Serving the global community with a strong focus on growth in Canada.
- ^ Stan Higgins . Report: CryptoWall Creators Earned $325 Million in Bitcoin Ransoms. CoinDesk. Bitcoin News, Prices, Charts, Guides and Analysis.
- ^ How to Spot the Real OPM Data Breach Letter. BBB. Start with Trust.
- ^ Kevin Beaumont. Tweet by Kevin Beaumont. Twitter. Online News and Social Networking Service.
- ^ The Importance of Backup Systems. Practically Networked. An IT Business Edge Site.





















