Uazq ransomware (virus) - Free Guide
Uazq virus Removal Guide
What is Uazq ransomware?
Uazq ransomware – a dangerous Windows virus that might lock your files forever
Uazq ransomware is a variant of the notorious Djvu family, renowned for its destructive capabilities. This version continues the trend of infiltrating computer systems, often through the use of software cracks and unauthorized installers, to encrypt critical files and demand a ransom for their release.
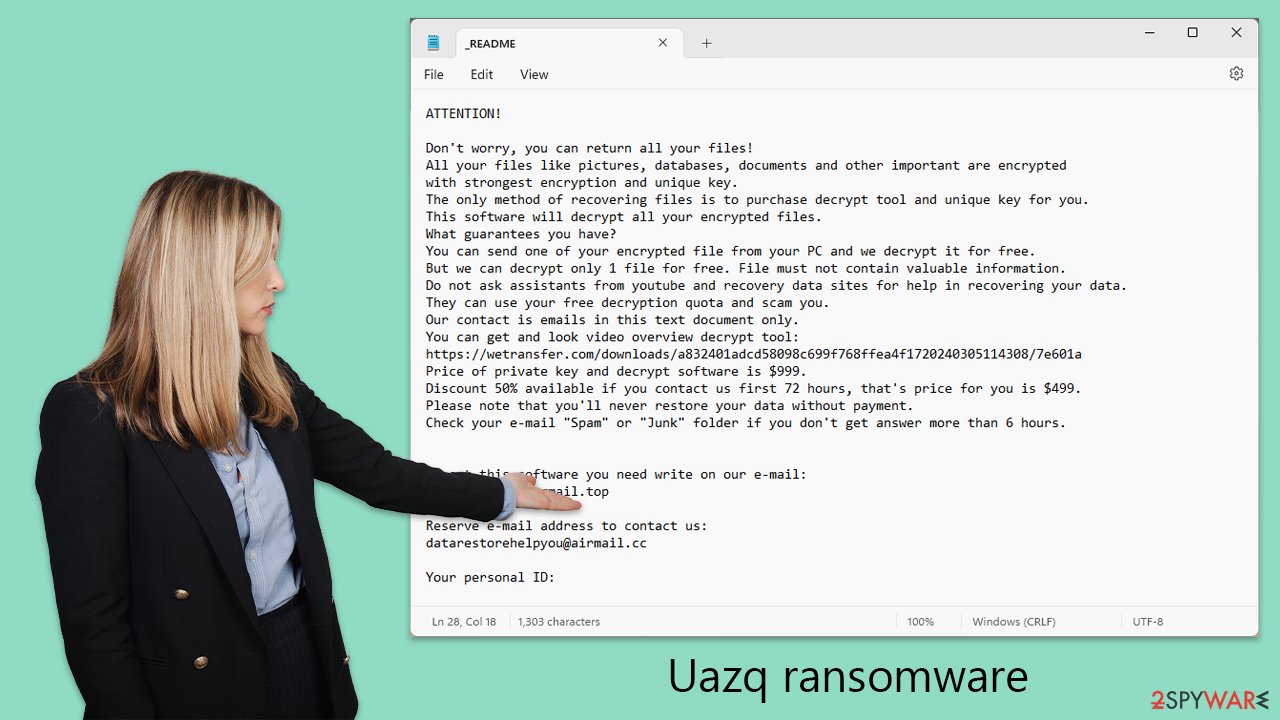
Upon entry, Uazq ransomware zeroes in on documents, images, videos, and other valuable files for encryption. It employs the RSA encryption algorithm, a complex method that renders files inaccessible without a unique decryption key. Once the encryption process is complete, affected files are appended with the “.uazq” extension, and victims are presented with a ransom note named “_readme.txt,” which demands a payment of $999/$499 for the decryption key.
Immediate action is essential upon detecting the Uazq ransomware. Victims should disconnect their systems from any networks and deploy advanced antivirus software for a thorough system scan. To mitigate the impact of ransomware attacks, maintaining regular backups and implementing strong security protocols are indispensable strategies.
| Name | Uazq virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .uazq extension appended to all personal files, rendering them useless |
| Family | Djvu |
| Ransom note | _readme.txt dropped at every location where encrypted files are located |
| Contact | support@freshingmail.top and datarestorehelpyou@airmail.cc |
| File Recovery | There is no guaranteed way to recover locked files without backups. Other options include paying cybercriminals (not recommended, might also lose the paid money), using Emisoft's decryptor (works for a limited number of victims), or using third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security app |
| System fix | Upon installation, malware can cause severe damage to system files, resulting in instability issues such as crashes and errors. However, FortectIntego PC repair can automatically fix any such damage |
How ransomware is distributed
The spread of Uazq ransomware, a member of the Djvu family, predominantly occurs through a method called bundling. This technique tricks users into downloading infected software or cracked versions of legitimate programs, which appear to offer an easy way to access paid applications for free.
Within these compromised installers, the ransomware lies hidden, activating silently when the unsuspecting user installs the supposed software. Once active, Uazq embarks on its mission to encrypt data and then demands a ransom in exchange for the possibility of data recovery.
To protect against such ransomware threats, a combination of safe browsing practices and solid security measures is crucial. Avoiding the temptation of pirated software or unauthorized downloads is the first step; these are common traps set by cybercriminals to distribute malware. Always opt for downloads from reputable sources, such as official software vendor sites or verified platforms.
Keeping your security software up to date is another critical defense strategy. Regular updates provide the latest protections against both known and new threats, with automatic updates ensuring continuous protection without manual intervention.
Moreover, the practice of regularly backing up valuable data cannot be overstated. Although backups do not prevent ransomware infections, they can significantly mitigate their impact by preserving copies of important files. Backups should be stored on separate devices or cloud services, isolated from your primary network, to protect them from ransomware attacks. This approach ensures that, in the event of an infection, you retain access to your essential data without succumbing to ransom demands.
Attackers demand money in exchange for the encrypted files
Within the landscape of cyber threats, particularly ransomware, the delivery of a ransom note is a critical step for attackers. This document serves as the attackers' primary method of communication, detailing the attack specifics and the conditions for decryption. It's their way of presenting demands and guiding victims on how to proceed.
Victims of Uazq ransomware encounter a message that outlines the encryption of their files with advanced techniques and a unique key, stressing that recovery is only possible through the purchase of a decryption tool and key exclusive to them. The message attempts to establish a semblance of assurance by offering to decrypt one file for free, as a demonstration of their ability to reverse the encryption. However, this offer is laden with conditions, such as the exclusion of files containing valuable information and warnings against seeking external assistance, which could purportedly risk the free decryption quota or result in scams.
The ransom note includes contact information and a deadline for a discounted payment rate, pressuring victims to act swiftly to reduce their financial burden. Despite the tone of assurance and the promise of a solution, engaging with the attackers is fraught with risks. There is no certainty of regaining access to encrypted files even after payment, and many victims report further demands, unfulfilled promises, or continued inaccessibility to their data.
Paying the ransom further emboldens cybercriminals by funding their activities, potentially leading to the development of more sophisticated attacks. It's a direct contribution to the cycle of cybercrime, encouraging perpetrators to persist in their illicit endeavors. Before considering payment, victims are advised to exhaust all other alternatives and seek professional guidance. Complying with ransom demands not only lacks guarantees but also supports the continuation of these cyber threats.
The ransomware reads as follows:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
Do not ask assistants from youtube and recovery data sites for help in recovering your data.
They can use your free decryption quota and scam you.
Our contact is emails in this text document only.
You can get and look video overview decrypt tool:Price of private key and decrypt software is $999.
Discount 50% available if you contact us first 72 hours, that's price for you is $499.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshingmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
Recover after a ransomware attack
Responding to a ransomware attack like Uazq with careful actions is essential. Immediately disconnecting the infected device from the internet prevents further spread and communication with the attackers' servers.
Perform a detailed scan with updated antivirus software such as SpyHunter 5Combo Cleaner or Malwarebytes to remove the ransomware. If you have backups, use them to restore your data. Without backups, consider decryption tools or data recovery software, following specific instructions for these methods – we provide all the details below.
After removing the ransomware, a system repair tool FortectIntego can fix any lingering issues. Reinstalling the operating system is an alternative, though it poses a risk of data loss.
Prevent future attacks by maintaining regular backups, staying aware of cybersecurity threats, securing compromised accounts, and reporting the incident to law enforcement. This approach minimizes damage and strengthens defenses against future intrusions, promoting a swift recovery and enhanced digital security.
Data recovery
Navigating the recovery of files encrypted by Uazq ransomware without yielding to cybercriminals' demands marks a pivotal stage in addressing this cybersecurity predicament. Contrary to common misconceptions, neither a basic antivirus scan suffices to decrypt files, nor is file recovery necessarily futile post-encryption.
Exploring data recovery options is crucial:
- Backup Restoration: Leveraging recent backups is the most dependable method, emphasizing the importance of frequent and up-to-date backups.
- File Recovery Software: Certain tools are designed to search the hard drive for recoverable files, including those affected by ransomware encryption.
- Decryption Tools: While not always applicable, tools like Emsisoft's, tailored for Djvu ransomware victims, can sometimes decrypt files affected by specific ransomware families.
Initiating recovery with a tool such as Emsisoft's, obtained from their official website, is recommended. Follow the instructions provided by the tool to attempt file decryption. Success varies based on the specific ransomware variant and the corresponding decryption keys' availability.
Should decryption attempts not yield success, consider advanced data recovery software. Install the software, perform a deep scan, and follow the prompts to recover your data.
It's worth noting that decryption solutions sometimes emerge following legal actions against ransomware operators, leading to the release of decryption keys. Stay informed about new tools and updates, as they can offer additional recovery avenues for those impacted by Uazq ransomware.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you need more detailed instructions on the mentioned recovery methods, please check out the information below.
Getting rid of Uazq virus. Follow these steps
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
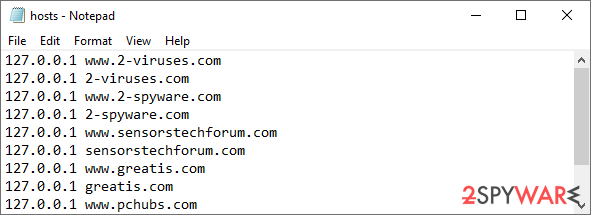
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

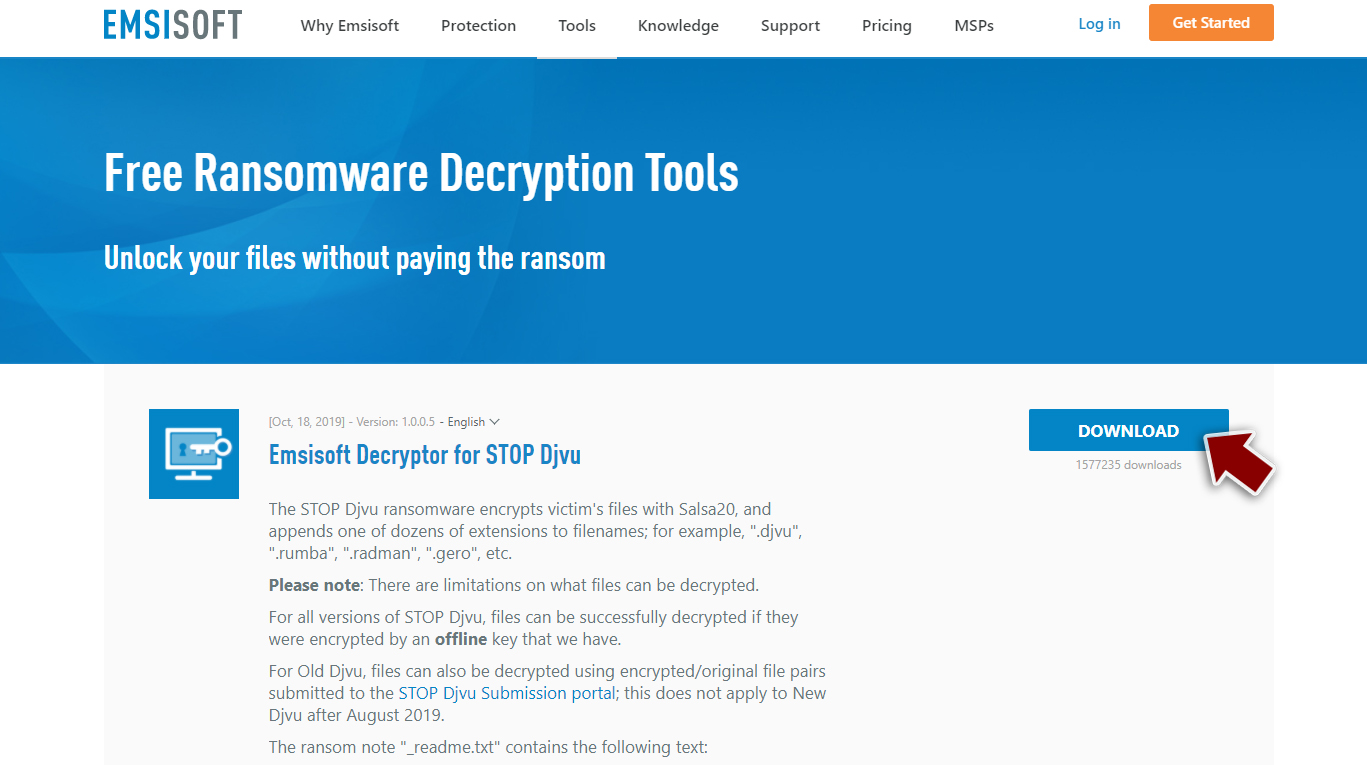
Use Emsisoft decrytor for Djvu/STOP
If your computer got infected with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.

- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
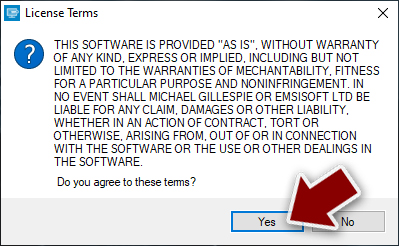
- Agree to License Terms by pressing Yes.

- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.