Nbwr ransomware (virus) - Free Instructions
Nbwr virus Removal Guide
What is Nbwr ransomware?
Nbwr is a ransomware-type virus that can make you lose access to your files permanently
Nbwr ransomware represents a formidable threat, emerging from the notorious Djvu ransomware family known for its aggressive impact on digital assets. This malware typically infiltrates computer systems unauthorized, often through illicit software downloads and fake software activation tools.
Upon entry, Nbwr ransomware rapidly launches a thorough file encryption process. It particularly targets vital files including documents, multimedia, and other crucial data. Employing the complex RSA encryption algorithm, it effectively locks users out of their files. Without a specific decryption key, these files become inaccessible.
Subsequently, affected files are appended with a “.nbwr” extension. Concurrently, a ransom note, typically named “_readme.txt,” appears, demanding payment of either $980 or $490, depending on how fast victims pay, in exchange for file access. For communication purposes, hackers provide two contact emails:
- support@freshmail.top
- datarestorehelpyou@airmail.cc.
Immediate action is paramount when dealing with the Nbwr virus. The infected device should be quickly isolated from any networks and subjected to a detailed system analysis using advanced security software. Below you will find all the details needed to deal with this threatening PC infection.
| Name | Nbwr virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | Malware appends .Nbwr extension to all affected files |
| Family | Djvu |
| Ransom note | _readme.txt dropped at every location where encrypted files are located |
| Contact | support@freshmail.top, datarestorehelpyou@airmail.cc |
| File Recovery | There is no guaranteed way to recover locked files without backups. Other options include paying cybercriminals (not recommended, might also lose the paid money), using Emisoft's decryptor (works for a limited number of victims), or using third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security program |
| System fix | As soon as it is installed, malware has the potential to severely harm some system files, causing instability problems, including crashes and errors. Any such damage can be automatically repaired by using FortectIntego PC repair |
Ransom note encourages victims to pay sooner rather than later by offering discounts
In the case of Nbwr ransomware attacks, the primary mode of communication between the cybercriminals and their victims is through a ransom note. This note is intended to instruct victims on the process and amount necessary to pay the ransom in Bitcoin to retrieve their encrypted data.
The ransom note is characteristically straightforward, outlining the steps and amount required for payment. The attackers behind Nbwr ransomware adopt a professional tone in their communication, lending a deceptive air of legitimacy to their demands.
This ransom message is typically displayed on the victim's device immediately after Nbwr completes the file encryption. It can manifest as a text file, an image, or a webpage, and it clearly details the steps for making the ransom payment and the process for regaining access to the encrypted files.
The note often reads like a blend of reassurance and threat, stating:
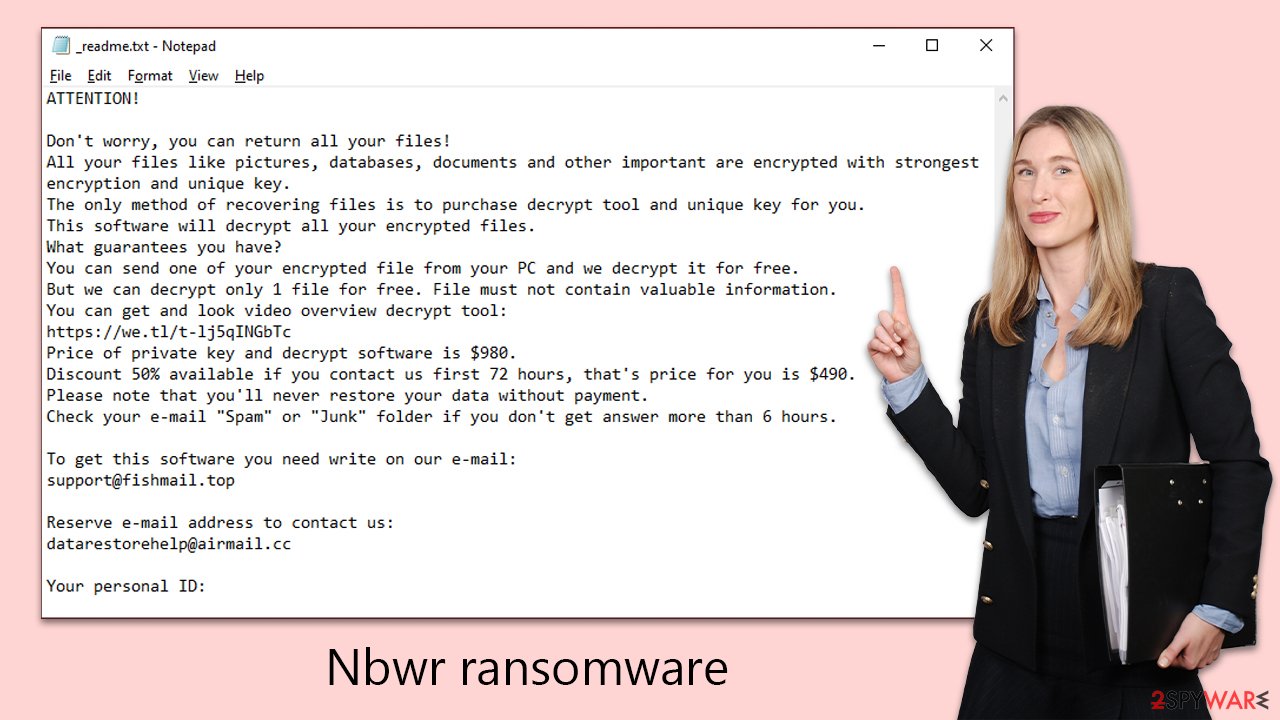
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-rmxjMZAZBJ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
The ransom typically stands at $980, with a 50% discount offered if contact is made within the first 72 hours, reducing the cost to $490. It stresses the futility of other recovery methods without payment and provides contact emails for communication.
Cybersecurity experts and law enforcement agencies strongly discourage paying the ransom. Such actions fund criminal activities and there's no assurance that the decryption key provided will be effective. The tactics used, such as offering discounts and free decryption of a single file, are designed to pressure victims into paying quickly, but compliance with these demands only perpetuates the cycle of ransomware attacks.
The first step is to remove the Nbwr virus effectively
Addressing an Nbwr ransomware infection requires a thorough understanding that the malware might not be completely eliminated from the system after encrypting data. It can leave behind residual components that pose ongoing risks. Additionally, ransomware often comes bundled with other malicious software, adding complexity to the infection.
To commence malware removal, the first step is to disconnect the infected system from the internet. This prevents further spread or damage. Following this, a comprehensive system scan should be performed using reliable security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. These programs are designed with advanced capabilities to detect and eradicate various forms of malware, including ransomware and Trojans.
Furthermore, users are advised to go to:
C:\Windows\System32\drivers\etc
In this directory, the “hosts” file should be located and deleted. Ransomware frequently alters this file to block access to websites that provide malware removal assistance or data recovery solutions. Running a scan with a robust PC repair tool FortectIntego is also recommended. This tool can repair damaged Windows files, ensuring the system's optimal functionality and preventing crashes or instability.
Only after confirming that all aspects of the malware and associated threats have been thoroughly removed should users proceed to data recovery. It's crucial to ensure the system is completely free of ransomware traces before starting recovery to avoid additional data loss or re-encryption. The next section will delve deeper into data recovery methods. Adopting this two-step approach – first removing the malware and then focusing on data recovery – provides the safest route to recovering your digital assets.
.Nbwr files recovery possibilities
Navigating the complexities of ransomware, like Nbwr, reveals that commonly held beliefs about data encryption and malware functionality are often misplaced. Many victims mistakenly think that simply running a system scan with security tools will fix their encrypted files, or that manual efforts like renaming files can reverse the encryption. But the reality is more complex.
Nbwr ransomware's encryption is based on advanced algorithms, creating secure cryptographic sequences that are extremely difficult to crack. Simply removing the malware does not unlock the encrypted files; they remain inaccessible without the specific decryption key held by the cybercriminals.
This ransomware encrypts data and assigns each file a unique identifier and complex encryption key, which the attackers use to demand a ransom. Their goal is clear: to monetize the victim's desperation, making ransomware a lucrative venture for cybercriminal groups.
While paying the ransom may seem tempting, we recommend exploring other options. Before attempting any recovery methods, ensure you have a backup of the affected data to prevent further loss.
One potential starting point for recovery is the Emsisoft decryption utility, but its success depends on the specific ransomware strain and other factors. It's crucial to approach recovery with a clear understanding of these limitations.
- Download the app from the official Emsisoft website.
![Nbwr ransomware Nbwr ransomware]()
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
![Nbwr ransomware Nbwr ransomware]()
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Nbwr ransomware Nbwr ransomware]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Nbwr ransomware Nbwr ransomware]()
- Press Decrypt.
![Nbwr ransomware Nbwr ransomware]()
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If your data was encrypted with an online ID, Emsisoft's tool won't work. In such a case, we recommend trying specialized data recovery software instead.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Nbwr ransomware Nbwr ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.