Bhacks ransomware (Decryption Methods Included) - Free Guide
Bhacks virus Removal Guide
What is Bhacks ransomware?
Bhacks ransomware is the threat that adds two different extensions to files and folders it encrypts and locks
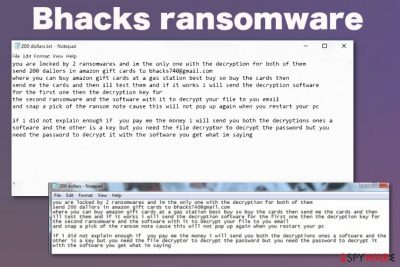
The ransom type and the encryption methods are both non-typical for other threats falling into the same category[1] as this Bhacks ransomware virus. Criminals behind this threat demand 200 dollars in Amazon Gift Cards instead of cryptocurrency payments. The latter is typical for ransomware, hence the name of the cryptovirus category. The payment demand message is named 200 dollars and is a Notepad file. In the same message criminals provide the email address and a few common places where you can buy gift cards.
However, there is little to no possibility that Bhacks virus developers are going to send you the promised decryption software and decryption keys after you contact them via bhacks740@gmail.com email address. Communicating with such malicious actors can lead to more malware infiltrations instead of recovered files on your device, so ignore these demands and make sure to clear all the threats from the system with a proper AV tool, since this is the threat that can be detected by many anti-malware engines.[2]
| Name | Bhacks file-locking virus |
|---|---|
| Category | Ransomware |
| File markers | .bhacks for individual files and Lock. prefix for folders |
| Tactics | Makes data inaccessible by encrypting and locking files, folders. Then criminals try to get profit from victims by demanding the payment for the alleged decryption software that may not even exist or work |
| Specific feature | Threat locks files and folders and demands for dollars in the form of Amazon gift cards instead of cryptocurrency like typical ransomware |
| Ransom amount | 200 dollars in Amazon Gift cards |
| Ransom note | A text file named 200 dollars.txt contains a message about further actions you can take and informs about possible places where you can get those gift cards that criminals ask for. Also, it delivers the contact email that gives the opportunity to reach extortionists |
| Contact email | bhacks740@gmail.com |
| Distribution | Malware spreads its payload via infected email attachments that get injected with malicious macros. documents and other types of data get attached to legitimate-looking emails claiming to have important information and users trigger the drop of the malicious code without noticing when they enable the additional content |
| Damage | Ransomware is dangerous because it involves blackmailing and money extortion, there is a possibility that you may lose your data permanently when the threat affects those files and folders. This virus also goes through system folders and settings, changing them or adding programs, files. Such changes can damage the machine itself and create issues with the performance |
| Elimination | Bhacks ransomware removal requires professional anti-malware tools because any files or programs related to the virus can affect files again and damage your device permanently. The sooner you clean it off of the machine, the better |
| Repair | Besides affecting files and folders directly, ransomware interferes with system settings and functions, so you need a proper system tool like FortectIntego that can find and repair damage in such essential system places |
Bhacks ransomware is the program that falls into the category of ransomware due to extortion and blackmail functionalities. This is the file-locker virus, even though it is not demanding cryptocurrency as other threats in the category typically do. There is a huge possibility that your data may get damaged or permanently locked, even when you pay the amount asked by criminals.
So there is no need to fall for those claims and believe every word the ransom note says. Criminals that release such infections like Bhacks ransomware and other extortion-based threats care for your money and data, in most cases, files affected in these attacks will not get recovered. Researchers, in rare cases, can develop decryption tools, but crypto-malware became more and more powerful and dangerous.
This is why other experts[3] and we always recommend cleaning the machine from malware first and then remove Bhacks ransomware with anti-malware tools, repair damage that the virus has caused on the PC. Only when the machine is virus-free and clear of any affected files and system folders, you can safely restore files encrypted and locked by the malware.
When all of those files get compromised the wallpaper of the desktop is changed to the disturbing photo and a statement that you need to pay 200 dollars in Amazon Gift cards and the direct ransom message in a text file gets added in multiple folders that contain encoded data. Bhacks virus ransom note delivers the following text:
you are locked by 2 ransomwares and im the only one with the decryption for both of them
send 200 dallors in amazon gift cards to bhacks740@gmail.com
where you can buy amazon gift cards at a gas station best buy so buy the cards then
send me the cards and then ill test them and if it works i will send the decryption software
for the first one then the decryption key for
the second ransomware and the software with it to decrypt your file to you email
and snap a pick of the ransom note cause this will not pop up again when you restart your pcif i did not explain enough if you pay me the money i will send you both the decryptions ones a
software and the other is a key but you need the file decryptor to decrypt the password but you
need the password to decrypt it with the software you get what im saying
Bhacks ransomware removal can get difficult because this is the threat that has two functions: locking files and folders separately. It relies on encryption for the process of making files useless and inaccessible so army-grade algorithms allow criminals to change the original code of photo, video, audio files or documents, databases. So rely on cleaning processes and focus on the system and security before worrying about affected data. 
It is not a good idea to go out and purchase those gift cards wort of hundreds of US dollars and contact Bhacks ransomware virus creators in the first place. You cannot ensure that people behind the malware are worthy of your trust. Instead of receiving the decryption key or more information, criminals may send you malicious files, other payloads of malware and expose you to the dangerous material online.
Bhacks ransomware creators can claim to offer test decryption and discounts or try to fake the legitimacy, so people are more eager to pay up. Your day can remain worthless and encrypted after the payment, so this is not a reliable method. You should avoid financial losses as much as possible and go to the virus removal instead.
Get a proper anti-malware tool and get rid of the Bhacks ransomware by running a full system scan. During such a process software checks various places on the machine where malware-related files get hidden and terminate these processes end the activities related to cryptovirus.
Follow the steps and suggestions that the AV tool displays before you. However, Bhacks ransomware termination is not the process that restores files or fixes damage, decrypts affected data. You need particular system tools like FortectIntego that can find and repair system damage and proper data backups that can replace damaged files with safe, unaffected copies. You can find a few alternate data recovery methods below the virus removal guide below. 
Spam emails from unknown sources deliver malware
There are many methods used by such malicious actors that develop and spread threats like ransomware around the globe. All of them involve fraudulent techniques and precise techniques that allow hackers to infect the payload directly on the targeted system. Most of them involve malicious files:
- pirating sites and torrent services;
- malicious website hosting services;
- spam email campaigns.
In most cases, when you get the email from an unknown sender or the company you don't normally use or rely on, you don't pay enough attention. Such behavior leads to cyber infections because attention to details may keep the system virus-free when you take all the suspicions more seriously. Get rid of the email notification immediately if it states about financial information or other sensitive information that is not related to your previous activities.
Such email attachments hide malicious macros and once you open the downloaded Microsoft file on the machine and allow the additional content malicious macros get enabled and trigger the payload drop of the trojan designed to install a virus or the ransomware infection itself. Be cautious.
Terminate Bhacks virus and avoid financial losses
To prevent further Bhacks ransomware virus infections, you need to get rid of the virus from the machine completely. Any traces left on the operating system can trigger and launch a secondary encryption process. After double encryption, your data is damaged permanently and there is no other option than to replace affected files using safe copies from the cloud or external storage.
Bhacks ransomware removal is the quickest and the most successful when you select the right tool for this job – antivirus detection tool. Programs like SpyHunter 5Combo Cleaner, Malwarebytes can detect malicious behavior-based intruders and terminate the dangerous process. This automatic method is needed because other files and programs that get added on the machine can interfere with crucial functions needed for file recovery.
However, when you remove Bhacks ransomware, you should note about the alterations directly in system folders, changes made to settings and programs that get disabled to ensure that malware is more persistent. Unfortunately, such changes can cause damage to the security functions and such parts of the device like registry entries. To check for virus damage and possibly repair damaged parts, rely on FortectIntego system program.
Getting rid of Bhacks virus. Follow these steps
Manual removal using Safe Mode
Reboot the system in Safe Mode with Networking before scanning the machine using the AV tool and removing Bhacks ransomware
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Bhacks using System Restore
Try System Restore feature that allows recovering the device in a previous state before the virus
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Bhacks. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Bhacks from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Bhacks, you can use several methods to restore them:
Data Recovery Pro is the method for restoring encrypted or damaged data
You can rely on Data Recovery Pro when Bhacks ransomware encrypted files or when you accidentally deleted them yourself
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Bhacks ransomware;
- Restore them.
Windows Previous Versions is the data restoring feature
If you enabled System Restore, you can use Windows Previous Versions and restore files affected by Bhacks ransomware virus individualy
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the alternate method for file recovery when you don't have needed backups
When Shadow Volume Copies are left untouched, you can rely on ShadowExplorer
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
There are no options for Bhacks ransomware decryption
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Bhacks and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Ransomware attacks grow. NYTimes. Global media news source.
- ^ Ransomware detection rate. VirusTotal. Online malware scanner.
- ^ Virusai. Virusai. Spyware related news.





















