Brick ransomware (Decryption Methods Included) - Free Guide
Brick virus Removal Guide
What is Brick ransomware?
Brick ransomware is the cryptovirus that runs on Windows devices and uses the AES encryption algorithm to lock files as the reason for a ransom demand
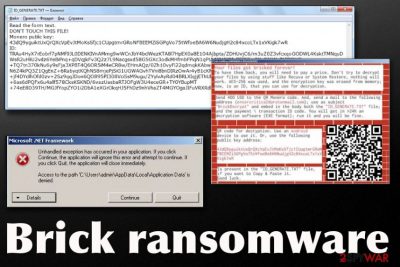
As long as Brick ransomware virus is on the computer, it can affect many parts of the device and run in the background until you fully get rid of it. When you see that your files got locked and marked using .brick appendix, you can already know that there is malware on the machine. When you receive the ID_GENERATE.txt and additional pop-ups with messages from virus developers, you should react as soon as possible, because time is not in your favor when it comes to ransomware threats. Paying is not the best option because there is no guarantee that virus creators will send you the alleged BrickDecrypt tool. Even contacting them via the provided entercritical@prolonmail.com email address is not advisable because criminals can be unpredictable and spread more malware for their victims or ask for bigger amounts than the initial $400.
| Name | Brick ransomware |
|---|---|
| Symptoms | File get locked and marked with the particular appendix, pop-up windows get opened on the screen with particular messages stating that your machine got encrypted and locked, so you should pay up to get those files recovered |
| File marker | .brick is the extension that gets on the end of encoded files alongside the random chain of characters for particular victims' ID indication |
| Ransom note | The lock screen pop-up or program windows deliver instructions and additional information about the encryption and payment options. These windows get named with the same ransom numbers and letters indicating the particular ID of the unique victim. Also, the text file ID_GENERATE.txt appears on the desktop and in additional folders on the machine with your unique victims' ID and a Monero wallet address that is needed for the money transfers |
| Contacts | entercritical@prolonmail.com |
| Ransom amount | $400 in Monero cryptocurrency |
| Encryption methods | AES-256[1] |
| Distribution | Developers of the threat use common methods like infected files sent via safe-looking emails and, hacking through insecure RDPs and other malware like exploits,[2] botnets or trojans for the cryptovirus distribution |
| Elimination | Brick ransomware removal is the process that should be taken seriously, especially when other malware and malicious processes can be involved in delivering and activating this malicious threat. Get an anti-malware program and run the tool on the system for a thorough check that reveals all the possible intruders and can remove them |
| Repair | You should follow the virus termination with a PC repair procedure using something like FortectIntego. System optimizers or cleaners can find and fix affected files, entries and other parts of the OS that malware managed to damage |
Brick ransomware is the threat focused on file-locking and encryption process, so it starts the attack with finding particular documents, photos, images, archives, and even databases that can get encrypted and potentially create a good reason for the ransom demand.
The message that directly asks for the payment appears once the file-locking is done. Brick ransomware developers can inform their victims about the processes and consequences or give instructions for further actions. The initial ransom note gets shown in the program window that locks your screen to deliver the information about the encryption process that has happened.
Brick ransomware generates the pop-up and names the window with random characters, possibly related to victims' ID and other identifications that help to differentiate between all the victims. The additional text file named ID_GENERATE.txt also gets placed on the desktop and in other folders that contain encrypted files.
Brick ransomware ransom-demanding message states the following :
Your files got bricked forever!
To have them back, you will need to pay a price. Don't try to decrypt your files by using stuff like Recuva or System Restore, nothing will work. AES-256 was used, and the encryption key was erased from memory; now, is an ID, that you can use for decryption.
Send 400 USD to the QR Monero code. And, send a mail to the following address ( entercritical@prolonmail.com ); use as subject ” BrickDecrypt ” and embed in the body both the “ID_GENERATE.TXT” file; and the payment \ transaction ID code. You will get in> 24h an decryption software (EXE format); run it and you will be fine.
QR code for decryption. Use an Android device to use it. Or, use the following public key address:
43dQ9yguiktUxQrQXcVpEvJtMoKsSfjc1CUpgtmrGRoNFBEEMZiSGPgVo75tWfoeBA6W6NudjgH2c84xcoLTx1xVKigk7wR
Is present in the File.ItX.TX if youTOP.IDT.TX.It presentToFile
Good luck.
Brick ransomware aims at English-speaking users, and the initial file of the ransomware was created back in summer 2019, but the sample was discovered in February 2020. This fact can mean that malware was perfected and released without any flaws. It makes the threat even more dangerous because of this because developers made sure that there are no issues with the code that may be used by researchers for termination or decryption tool generation.
That said, the sooner you decide to remove Brick ransomware the better because you can avoid further damage on the machine while the virus is freshly dropped on the machine. If you don't remove all parts of the virus and load files on the machine, your data can get encrypted again or permanently damaged. If you decide to pay and files remain locked, you lose your money and files at the same time. 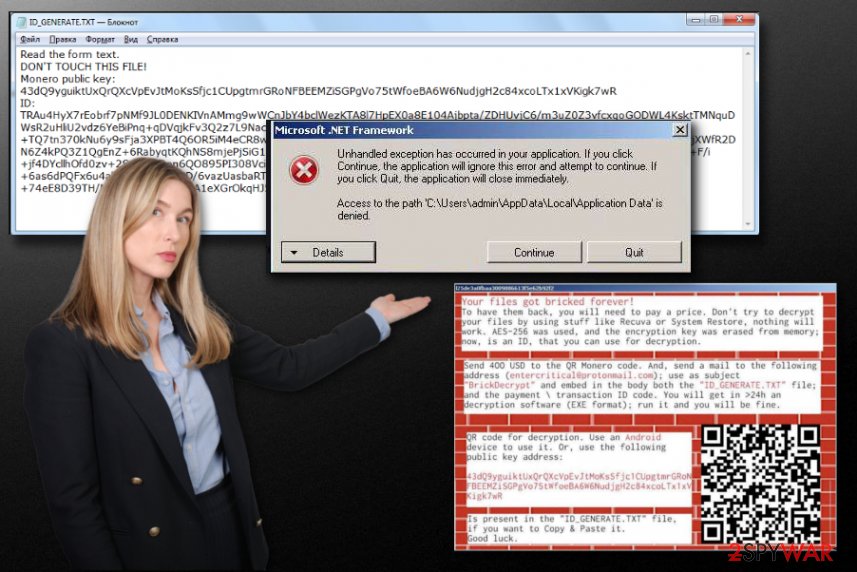
Criminals created Brick ransomware to lock files and demand a ransom of $400 that should get paid via QR Monero. Such transfers of cryptocurrency are almost impossible to track, so ransomware creators, in most cases, choose such payment methods instead of real dollar transfers.
Experts[3] strongly discourage people to stay away from any cybercriminals, especially people like these Brick ransomware virus developers. You cannot trust them because the initial aim and goal of these people is gaining money from victims.
The better option is to terminate Brick ransomware by running an anti-malware tool that can check and detect these viruses running in the machine. Antivirus programs are the best for this because the malicious purpose of files and programs can be indicated for you.[4] These detection names differ and show the particular payload dropper that caused the infection.
Focus on the cleaning and then rely on a program like FortectIntego that can find and fix virus damage. Since the threat affects processes and other features that can help to fight Brick ransomware, you need to repair them and fix the affected parts before adding files on the machine. Traces of the virus or affected functions can interfere with recovery or affect recovered data. For some additional restoring tips – check below. 
Malicious files attached to spam emails and pirated software packages
Ransomware is one of many more stealthily threats that rely on silent techniques that allow the infiltration to happen in the background. The received malicious file can trigger the ransomware attack pretty quickly and you cannot notice neither the payload drop nor the file locking.
Spam emails that have malicious macro-filled documents can pose as legitimate notifications from companies like DHL, eBay, Amazon or different online shopping platforms. These types are chosen because order information, invoices, and other files related to financial details are commonly sent by such companies.
However, these files and data send out during pirated program installations can trigger the infiltration of direct cryptovirus or the malware that is designed to drop the ransomware executable file. Take this into consideration, stay away from pirating or torrent sites and delete any suspicious emails once you receive them.
Brick ransomware elimination requires attention and help from the proper system tools
Since Brick ransomware virus is a serious infection, you need professional anti-malware tools to fight the malware fully. The automatic method involving anti-malware programs saves you time because the tool during a full system scan finds all possibly associated and malicious files, programs, and potential intruders.
You need to go for this method of Brick ransomware removal because tools like SpyHunter 5Combo Cleaner or Malwarebytes can find security issues and cyber threats, intruders that affect your time on the computer. You can enter the Safe Mode with Networking before scanning the machine with an AV tool to ensure the best results too. Below is the guide that shows how to do that.
When you remove Brick ransomware, you should be sure that there is no traces of malware before you go for file recovery. Anything left that is related to the virus can affect the performance and even trigger secondary encryption. You need to repair virus damage immediately after the termination. Use FortectIntego or a PC repair tool and make sure to check for damaged registry entries and system files.
Getting rid of Brick virus. Follow these steps
Manual removal using Safe Mode
Get rid of Brick ransomware virus by rebooting the machine in Safe Mode with Networking and then run the AV tool
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Brick using System Restore
Using System Restore can help because this feature allows recovering the machine in a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Brick. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Brick from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Brick, you can use several methods to restore them:
Data Recovery Pro is the program that manages to recover files after virus encryption processes or direct deletion
Try Data Recovery Pro for encrypted data after the Brick ransomware infection
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Brick ransomware;
- Restore them.
Windows Previous Versions feature for the rescue after encryption
The Windows Previous Versions can be useful when System Restore gets enabled in advance
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer restores data that Brick ransomware manages to damage
However, when Brick ransomware deletes Shadow Volume Copies, the feature is not helpful
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Brick ransomware decryption tool is not released yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Brick and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ How strong is 256-bit Encryption?. Thesslsstore. Cyber security blog.
- ^ Exploit kit. Wikipedia. The free encyclopedia.
- ^ Virusai. Virusai. Spyware related news.
- ^ Brick virus detection rate. VirusTotal. Online malware scanner.





















