Can I locate it adware (Free Instructions)
Can I locate it adware Removal Guide
What is Can I locate it adware?
“Can I locate it” is an adware-type browser extension that shows ads whether you want them or not
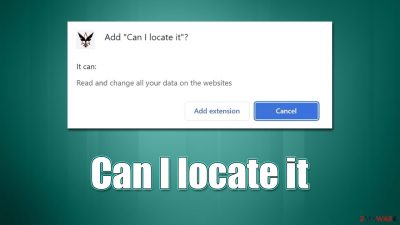
“Can I locate it” is a potentially unwanted browser extension that you may find running on Google Chrome, Mozilla Firefox, MS Edge, or any other used browser. While some users may install it while being tricked into believing it is useful, it is usually spread via fake advertisements and bundles downloaded from freeware[1] distribution websites.
Once on the system, Can I locate it begins its dubious operations. One of the most distinctive traits of the app is that its main goal is not to provide some useful features to users but instead to spam them with unending advertisements which can be monetized by the developers/distributors. These ads could be of questionable nature, which could put users' security and privacy at risk. We recommend removing the app ASAP, especially if it wasn't installed intentionally.
| Name | Can I locate it |
| Type | Adware, potentially unwanted browser extension |
| Distribution | Software bundles, misleading ads, third-party websites |
| Symptoms | Shows intrusive advertisements on various websites |
| Risks | Installation of potentially unwanted software, such as browser hijackers; redirects can also lead to other malicious websites, resulting in monetary loss or personal data disclosure to unknown parties |
| Removal | To remove PUPs manually, you can follow our removal guide below. If the unwanted ads do not stop, you should scan your computer with security software |
| Other steps | To ensure that adware is no longer tracking your data, you should clean your browsers with the FortectIntego repair tool |
Dangers of unwanted programs
Adware is a type of software that is extremely prevalent and can be found in various places. However, its integrity is usually questionable, as the developers of such software put the advertisements and monetization above user experience or even their safety. This is one of the reasons why so many security vendors flag it whenever it's installed on the device.
Adware developers often employ insecure advertising networks, which results in ads of poor quality being shown to users. Not only can they be quite spammy but also malicious. For example, those infected are more likely to encounter various phishing websites, as well as ads that recommend downloading other PUPs, such as browser hijackers.
Besides unwanted and potentially dangerous ads, users are subject to extensive data tracking. Information such as location, ISP, search queries, clicked links, visited websites, and similar can be a huge help when it comes to targeted advertising.[2] The information might also be shared with or sold to various third parties, reducing the protection level of the said data.
Can I locate it adware removal explained
Most people know about computer infection symptoms, so when they start seeing excessive ads everywhere they go, they start looking for the culprit of such behavior. In some cases, it is really easy to determine the root cause of the problem – for example, if you have recently installed an app from a dubious source and immediately after that noticed spam showing up on your system, you can easily get rid of it.
However, in some cases, determining the cause of the unwanted behavior can be quite difficult, especially if the PUP was installed unintentionally. In this case, checking the system is recommended – using manual and automatic methods is the best way to go about this.
1. Delete the browser extension
As evident, “Can I locate it” adware spreads as a browser extension. You can easily remove it by following the steps below. Please remember to check for other unwanted apps as well.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
2. Clean browser caches
After removing the unwanted extension, take your time to clean your browsers, as some components might still remain locally, and continue tracking activities. Likewise, failing to clean your caches at least sometimes might result in increased security risks – for example, cookies[3] might be stolen by criminals and personal accounts accessed. To avoid this, either rest your browser or remove caches, cookies, and other web data from them. You can always employ an automatic solution for this – FortectIntego – or delete caches manually.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
3. Scan with security software
As previously mentioned, it is sometimes difficult to determine was is causing pop-ups, deals, offers, auto-play videos, in-text links, and other intrusive advertisements wherever you go, especially if you visit insecure websites such as torrents or software cracks and download software from there.
Some adware and malware might be quite stealthy – they may not show active windows, perform background connections or even hijack legitimate processes. Therefore, we strongly recommend running a scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware. Not only can it find and remove malware from your system, but it also serves as the best way of protecting yourself from the incoming malware attacks – make sure it is running at all times.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What Is Freeware?. Lifewire. Tech News, Reviews, Help & How-Tos.
- ^ Targeted advertising. Wikipedia. The free encyclopdia.
- ^ Cookies and Web Beacons. NTT. NTT Communications.








