Clipboard Sync Beta browser extension (Free Instructions)
Clipboard Sync Beta browser extension Removal Guide
What is Clipboard Sync Beta browser extension?
Clipboard Sync Beta is a potentially unwanted application that performs intrusive ad campaigns

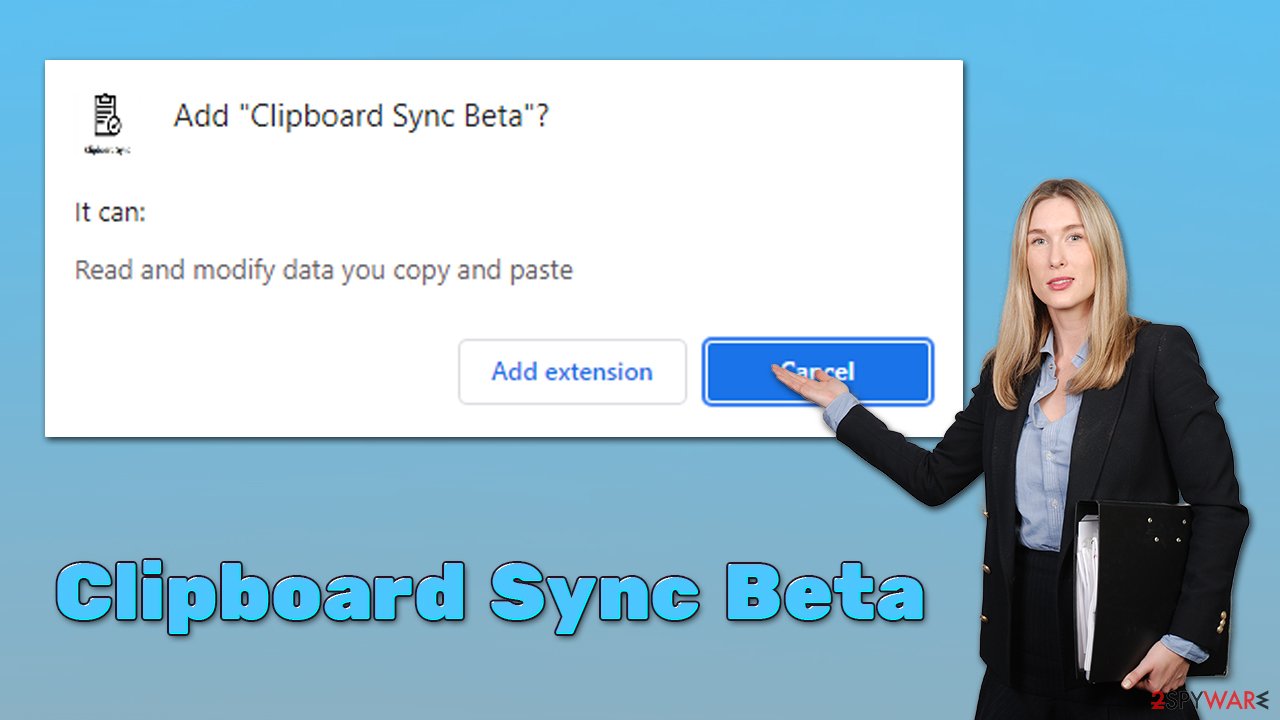
Clipboard Sync Beta is presented as an extension that can “Sync clipboards of two desktop devices,” which some might find useful. However, the app also has a lot of functions that are not immediately apparent, and those who install it might soon suffer from intrusive advertisements while visiting various websites. This is because this extension is a potentially unwanted program that falls into the adware[1] category.
Adware is a type of software that is commonly bundled with other applications that users download from various third parties, hence they might not even notice when or how the entry happened. In other times, people might install Clipboard Sync Beta intentionally thinking that the functionality it offers is beneficial, without knowing about its underlying activities. It was also reported by some users that they got infected after being tricked by a fake online message about Chrome.
Once installed, the virus grants itself the ability to read and modify any data you copy and paste. While it does not change the homepage/new tab web address and the search provider, it undertakes the task of rerouting users to potentially suspicious websites which host phishing, scam, or other malicious content. Users are also commonly exposed to pop-ups, coupons, banners, in-text links, and similar intrusive ads.
The only way to stop this disruptive behavior is to remove the Clipboard Sync Bet extension and then clean the web browser thoroughly. We show all the necessary steps needed to do that properly below.
| Name | Clipboard Sync Beta |
|---|---|
| Type | Adware |
| Alleged functionality | Syncs clipboard data |
| Distribution | Software bundles, deceptive ads, fake updates |
| Symptoms | Installed unknown browser extension or application; intrusive deals, coupons, discounts, offers, and other advertisements; possible homepage and new tab address changes; redirects to ad-filled, scam, phishing, and other dangerous websites |
| risks | Redirects to malicious websites can result in intrusive notifications, personal information disclosure to cybercriminals, financial losses, installation of other potentially unwanted programs/malware |
| uninstall | To delete adware, you can follow our removal guide below. If ads and other intrusive behavior do not stop, you should scan your computer with SpyHunter 5Combo Cleaner anti-malware and delete all threats automatically |
| optional steps | Malware or adware infections can diminish the performance of your computer or cause serious stability issues. Use FortectIntego to remediate your device and ensure that the virus damage is fixed |
How adware is distributed and how to avoid it
People would usually not install applications that would disturb their normal web browsing experience or perform other tasks that are considered disruptive or unwanted. Adware creators are well aware of that, and that is the main reason why they choose less fair software distribution methods. There are several ways that crooks deliver this unwanted software to users – here are a couple of examples:
- Software bundling has been used to deliver PUPs to users behind their backs for many years now. While the practice itself is not malicious in any way, its implementation can make it that way. The distributors are well aware that users commonly install freeware[2] without paying close attention to the process. In order to avoid being tricked, you should always pick Advanced/Custom settings instead of Recommended/Quick ones and always read the installation instructions carefully.
- Fake updates/malicious ads can show up at any time when you browse the web. Quite often, you might be shown a fake update for Flash Player or another well-known software, with a pretense to continue viewing the website or similar. Likewise, you might be shown a fake warning which claims that your system is infected with a virus and you need to remove it using the offered software. Please ignore these prompts and always download software from the official websites instead.
Of course, users might also install adware of their own volition after being tricked by “improves search results” or any other functionality that is promoted. A lot of times, these functions don't even work as promised or have little to no positive impact on the user experience.
Removal of adware
The main goal of adware is to feed advertisements to users, which would provide ad revenue for its creators. While ads are very common on the internet and do an important role in financing many businesses that would otherwise struggle to survive, there are many parties that would abuse ads in order to gain as much money from them as possible. This is why some of the most popular websites are sometimes filled with intrusive ads that change the content of the page or cover it completely – these result in much higher payouts by advertisers.
To make it short, free apps that occasionally show ads are not considered adware. It is several aspects of the programs, like their distribution and deceptive operation that cause them to fall into that category. Clipboard Sync Beta, for example, engages in intrusive ad campaigns that sometimes might put users' security and privacy at risk by showing them links to suspicious websites. They might end up installing malware or providing their details to unknown malicious parties.
This is one of the main reasons why we recommend removing the app and finding an alternative that would provide its function. Those infected with adware are also much more likely to have additional PUPs installed on their devices without permission, so please follow the steps below to check the system properly and remove everything suspicious.
1. Uninstall the browser extension
Browser extensions are a common form of adware, as they are easy enough to provide the functionality of producing ads, tracking data, and more. It is usually not difficult to eliminate the extension from the browser, although if you can't find it in the bar at the top, you might want to go the following way:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
2. Scan the system for infections
While not all potentially unwanted applications can be removed with security software, we strongly recommend scanning the system with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security software. If you found an extension or an app that you did not install yourself, you are at a higher risk of having other PUPs or even malware installed on your device.
Running a security scan would ensure that no malicious processes or files remain on your device, which is very important to your personal security and computer safety. Anti-malware tools are also detrimental in providing protection from incoming malware attacks.
3. Remove leftovers
Adware shows people ads on various websites, and some of these can be very relatable to users they are shown to. This is because the app gathers a lot of information about users – which websites they visit, links they click, search queries they type, and much more. This data is later used to generate ads that are catered to particular users, sometimes making them buy products they otherwise wouldn't.
In order to collect this information, adware uses cookies, web beacons, JavaScript, and other tracking technologies. Bits of information related to this process are stored locally on users' computers, thus security experts[3] highly recommend cleaning web data after the PUP/malware removal and also doing so regularly from time to time.
You can easily do this by employing a powerful maintenance and repair utility FortectIntego – it could also fix any system issues that could have been caused by the infection. Alternatively, follow these instructions:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies, and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Lucian Constantin. What is adware? How it works and how to protect against it. CSO Online. Information on business continuity and data protection.
- ^ Tim Fisher. What Is Freeware?. Lifewire. Tech News, Reviews, Help & How-Tos.
- ^ Novirus. Novirus. Cybersecurity news and malware insights.










