Crypt888 ransomware (Removal Instructions) - Nov 2017 update
Crypt888 virus Removal Guide
What is Crypt888 ransomware?
Crypt888 ransomware starts using maya_157_ransom@hotmail.com email address to contact its victims

Crypt888 ransomware is a dangerous program that encrypts files and allows you to decrypt them only after you pay its required ransom. Alternatively, Crypt888 is known as MIRCOP ransomware (also known as MicroCop ransomware) but there is almost no doubt that this ransomware will change its name in the nearest future.
Different variants of Crypt888 use different email addresses to contact their victims. The latest its version uses maya_157_ransom@hotmail.com email address which you should never use to contact hackers and pay the money. If infected, you will be asked 0.8 BTC (584 USD) as a ransom to get a decryption tool.
The newest file extension used by Crypt888 ransomware is called Lock. It is added to every filename of the encrypted data, so for instance, if the file's name is picture.jpg, it will change to Lock.picture.jpg.
The analysis of our experts has revealed that Crypt888 ransomware has already been updated for several times. All these versions look almost identical because crooks do not change the main code drastically. However, each version provides a different user interface and language of communication.[1] For example, while one of these variants addresses its victims in Portuguese[2], the other targets Czech-speaking users.
Taking into account all these changes and the latest version, maya_157_ransom@hotmail.com virus, we are happy to inform you that Crypt888 decryption tool is still effective when you need to recover encrypted files. We assume that cyber criminals are trying to confuse victims and make them search the web for information about Petya ransomware, which cannot be decrypted using any free tools at the moment. Most likely criminals expect to convince victims to pay the ransom by pretending to be a different virus.
Of course, you should NEVER pay the ransom asked by ransomware virus because you can also use an opportunity to recover your encrypted files for free. Scroll down to see Crypt888 removal instructions and find our data recovery guide.
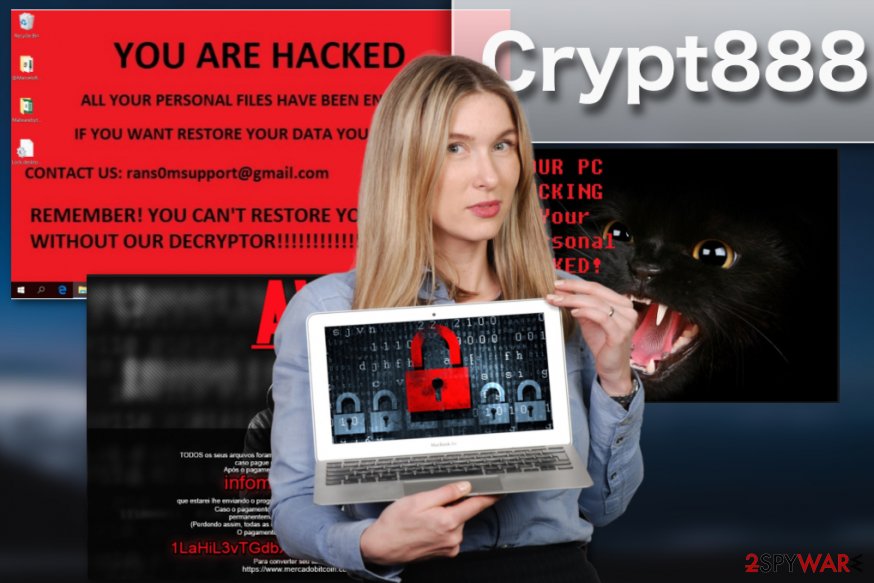
The variants of Crypt888 ransomware
MIRCOP ransomware. The initial version of the discussed ransomware virus used to set a black wallpaper with a picture of the Anonymous mask on it, accompanied by a short note stating the conditions for data recovery. The virus states that the victim “has stolen 48.48 BTC from the wrong people” and now needs to return them, and attempts to threaten the victim with a line “don’t take us for fools, we know more about you than you know about yourself.” You should not believe in such ridiculous threats and remove Crypt888 malware as soon as possible. [3]
Aviso ransomware. Aviso virus is a Brazilian version of this ransomware, which commands victims to contact criminals via informacaoh@gmail.com after paying a ransom worth 2000 Brazilian reals. The virus also adds Lock. prefix to encrypted data, and these files can be recovered for free using Crypt888 decryptor. This version does not differ from the previous ones except of the ransom note it sets as the desktop wallpaper.
The Italian version of Crypt888. Little information is available about the Italian version of this virus, however, according to malware researchers, this virus replaces victim’s desktop wallpaper with an image containing hacker’s manifesto words. The virus does not leave readme.txt (italian version: LEGGIMI.txt) file on the system, therefore, the victim is left without no information on how to restore encrypted data. This version showed up right after a suspicious ransomware variant that used to set “marked graphics” logo on the desktop. Since this particular version provided no decryption instructions or contact address, we assume that it was a test version.
The Portuguese version of the virus which has been spotted by the experts in November, 2016 uses different lock screen but its black and red design it similar to the previous Crypt888 versions. Since most security blogs have already warned the users about the Crypt 888 pretending to be a version of Petya ransomware 2017, the hackers have switched to other ransomware — the Locky virus. The lock screen now states that the user is infected with the “Locky ransomware” and the users have only 36 hours to pay the demanded ransom before their files are permanently destroyed. Please note, that you can still use the Crypt888 decryptor for this variant and fix your computer without paying the ransom or losing your files.
At the end of February 2017, Crypt888 emerges with a version that adds Lock. prefix to encrypted files. This version doesn't provide any information about recovery methods, leaves no contact details, and basically, does not provide any information regarding data recovery. It doesn't even ask for ransom – it simply corrupts files, and that is it. This virus' version changes desktop's wallpaper with a picture of beach view. To recover your files, use the Crypt888 decryptor by Avast.
Zuahahhah ransomware virus. On July 2017, the virus has been updated one more time. The latest version of crypto-malware changes affected computer’s desktop to the message saying that due to the virus infection, passwords, email accounts, and files stored on the computer might be lost. According to the virus analysis, the virus might be capable of deleting files. However, you should not wait for it to happen and just remove Zuahahhah from the device. Once it’s done, you should be able to restore files with Crypt888 decryptor.
Maya_157_ransom@hotmail.com ransomware. The latest version of Crypt888 ransomware uses maya_157_ransom@hotmail.com email address to contact its victims. The ransom note displayed by this virus reads:
YOU ARE HACKED
All your personal files have been encrypted!
If you want restore your data you may have to pay!
Contact us: maya_157_ransom@hotmail.com
Remember! You can't restore your data without our decryptor!!!!!!
Just like previous versions, the virus requires paying 0.8 BTC. However, you can recover your files by removing this Crypt888 ransomware version and using the free decryptor presented by security experts.
Cyber criminals spread ransomware using multiple techniques
Crypt888 scam is mostly spread via malicious ads, email spam, and also with the help of exploit kits [4]. In general, these are the most efficient and popular ransomware dissemination techniques used by almost every ransomware developer.
Distribution of this infection is still based on catchy-looking ads, guileful email letters, and technologies that exploit security vulnerabilities in victim’s computer. If user’s computer is unprotected, there are hardly any chances to survive Crypt888 or similar ransomware attack, especially if the victim tends to click on eye-catching content without estimating the potential danger that lies behind it.
In such case, the only way to save your data is to have a backup. Unfortunately, not many computer users understand the importance of backups [5], so when ransomware infects their computers, in most cases they have no choice but to say goodbye to their personal files.
Wipe out Crypt888 virus from the computer automatically
We suggest using automatic Crypt888 removal tools because it is the safest way to remove malware, infectious files, and unwanted registry keys from the computer system.
It is highly recommended not to try to remove Crypt888 virus manually because, despite its foolish source code, it is still a dangerous program. Leaving one or two files that belong to it can have disastrous consequences later on. Please delete the virus carefully – follow instructions we have prepared for our visitors and get rid of the ransom-demanding virus.
You can decrypt files locked by this virus using a special decryption tool (download link provided below).
Getting rid of Crypt888 virus. Follow these steps
Manual removal using Safe Mode
Delete Crypt888 ransomware by rebooting to Safe Mode with Networking. Then proceed to data recovery guide.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Crypt888 using System Restore
To uninstall this ransomware, you can also use System Restore method. It is explained below:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Crypt888. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Crypt888 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Crypt888, you can use several methods to restore them:
Use Crypt888 decryptor
Good news for victims who have their computers infected with this hideous computer program – you can recover absolutely all files marked with Lock. prefix for free. Simply uninstall the virus and use this decryption tool then.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Crypt888 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Jakub Kroustek. Crypt888 Ransomware Has Facelift as It Seeks Fresh Victims. AVG now. Daily computer security news.
- ^ November 2016: The Month in Ransomware. TripWire IT info site.
- ^ David Bisson. Decryptor Created for MIRCOP Ransomware that Sets $30K Ransom. TripWire IT info site.
- ^ Specific Ransomware Families and Types. The AVIEN Blog. The official blog of the Anti-Virus Information Exchange Network.
- ^ Jake Doe. Why do I need backup and what options do I have for that?. 2-spyware.com online security news site.





















