MIRCOP Ransomware virus (Improved Instructions) - Oct 2016 update
MIRCOP Ransomware virus Removal Guide
What is MIRCOP Ransomware virus?
MIRCOP ransomware – the “Anonymous” copycat
While ordinary ransomware viruses focus on attacking ordinary users’ personal information, some of them, such as MIRCOP virus (also known as Microcop or Crypt888 ransomware), act as if the hackers are the victims themselves. However, this does not lessen the destructiveness of this particular virus. It has a few distinctive features which make MIRCOP virus stand out from the majority of recent threats. For example, the virus demands an unbelievably huge ransom. In this article, we will present the vital information about this malware and the ways to remove MIRCOP virus from your computer. Keep in mind that automatic antivirus utilities such as FortectIntego come in handy when eliminating such infections from the infected devices.
The hackers behind Crypt888 ransomware seem to get a liking of the Internet hactivist group called “Anonymous.” Regarding the ransom note, it may seem that the creators of the ransomware belong to this particular organization. Nevertheless, it might as well be that virus owners only impersonate the mentioned group to pose themselves as more respectable, while their real relation to this group is highly questionable. The note goes as follows:
Hello,
You’ve stolen 48.48 BTC from the wrong people, please be so kind to return them and we will return your files.
Don’t take us for fools, we know more about you than you know about yourself.
Pay us back and we won’t take further action, don’t pay and be prepared.
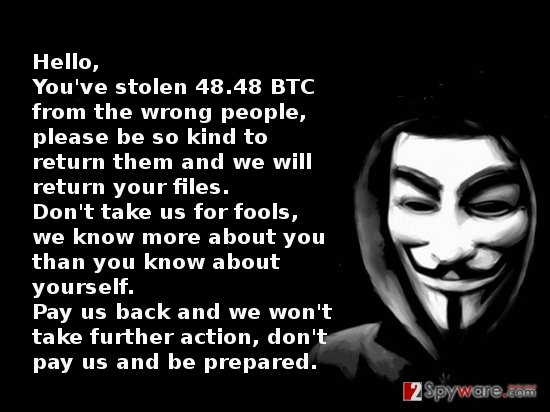
Just below the note, the hackers indicate a Bitcoin address to which the victim is demanded to send 48,48 BTC, i.e., more than 28,00.00 USD! Luckily, no financial transactions have been made to this account so far, but the drama typical to the “Anonymous” messages puts a lot of pressure on the victims. If your company‘s data has been under MIRCOP’s attack, do not consider paying up as there are absolutely no guarantees that the cyber criminals will be kind enough to return the locked data. Instead, you should focus on MIRCOP removal. In addition, you might try data recovery programs, such as PhotoRec, R-studio or go to the end of this article in order to find other data recovery recommendations.
Speaking more about the peculiarities of this ransomware, it seems that the infection is related to another file-locking cyber threat called .Locked, which was launched a couple of months before the MIRCOP. It also used the same “Anonymous” trademark logo – Guy Fawkes’s mask – and appended a similar extension. In this case, the virus attaches the extension “Lock.” in front of the corrupted folder. For example, the files will be encoded as Lock.My Pictures or Lock.My Documents. Lastly, the cyber criminals try to pressure the users to pay the money by blackmailing as if they have stolen some money from unknown “very important” people. MIRCOP threat is surely one of the novelties among recent ransomware.

Another interesting and concerning feature of this virus is that it does not limit itself to the file encryption and steals users login credentials from various browsers and social networking applications such as Skype. Similar techniques have already been used by other ransomware, for instance CryptXXX. This is especially useful if the malware creators decide to a blackmail the users by threatening to expose their private information to the public. Also, some of the collected information may be sensitive enough to be used to break into the victims’ bank accounts and steal money from them directly.
How do hackers plant this ransomware on the victims’ computers?
Reportedly, Crypt888 is distributed via the malicious spam campaign. The targeted users receive a fake Thai customs declaration form. It is a Word document which contains embedded malicious macro settings. If the infected computer’s macro settings are enabled by default, the virus will use the Windows PowerShell to download and set up the virus on the computer. It is now clear that the virus downloads the infectious script from a suspicious hxxp://www[.]blushy[.]nl/u/putty.exe domain, which, interestingly enough, redirects to a Dutch online adult shop.
Later on, the virus downloads three main files which are responsible for the rest of the havoc on the computer: c.exe, responsible for stealing information as well as x.exe and y.exe files, which encode the personal files. It is quite a popular strategy among the ransomware developers to imitate official institutions to convince users into opening the infected attachments. Remain very cautious when opening and downloading attachments of such emails. Always keep in mind that the credentials of official company do not necessarily mean that the email is legitimate. In addition, you should improve the overall protection of the computer by installing a trustworthy anti-spyware program which would not only block the malware but will also decrease the number of received spam emails.
Recommendations for the MIRCOP removal:
What you should first do when you are infected with MIRCOP virus, is to run the system scan with a malware removal application: antivirus, anti-spyware or anti-malware. If one of these programs fails to eliminate the virus, you can another. Eventually, one utility will take care of the threat and remove MIRCOP from your PC. Unfortunately, this method does not help decrypt the locked files. You might try retrieving them with the help of previously mentioned data recovery applications or reconstruct them from a backup copy. If you do not have it, make sure you make one for your future files. It is not difficult to back up the valuable information using the backup function of the operating system. Please note that this must be done only AFTER the MIRCOP removal. If you still cannot run the respective programs or launch some essential OS functions, feel free to use the recovery guidelines presented below and run the system scan once again.
Getting rid of MIRCOP Ransomware virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove MIRCOP Ransomware using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of MIRCOP Ransomware. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove MIRCOP Ransomware from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Though this virus has been a mystery to the virus experts for quite some time, finally, there is a breakthrough in the virus decryption. AVG has released Crypt888 decryptor which can be downloaded from the official AVG website or by clicking the previously indicated link. If, however, your device is infected with some new virus variant and the decryption tool is incapable of recovering your files, you can try out the instructions below to do that.
If your files are encrypted by MIRCOP Ransomware, you can use several methods to restore them:
Data Recovery Pro instructions for MIRCOP data recovery
Data Recovery Pro is one of the data recovery software designed to recover accidentally lost data, but may as well be used to bypass the MIRCOP encryption and retrieve your files. You can try this method out using these instructions below:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by MIRCOP Ransomware ransomware;
- Restore them.
How to use Windows Previous Versions feature for the data recovery after MIRCOP encryption
Windows Previous Versions feature is rather easy to use. All the steps you should take are provided below. However, you should not forget that this feature will only be functional in case System restore function has been enabled pre-infiltration. If it wasn’t you can skip the further instructions and move on to other data recovery methods.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Instructions for data recovery using ShadowExplorer
ShadowExplorer can be a useful feature for restoring data locked by less complex ransomware. Though it may not work for MIRCOP in particular, we still recommend you to try it out and perhaps you will manage to get at least a few of your personal files back.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Crypt888 decryptor method
The best and most guaranteed way of recovering your data is by using the Crypt888 decryptor. Just download the program and follow the further instructions provided by its developers.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from MIRCOP Ransomware and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.







