DCRTR ransomware (Virus Removal Instructions) - updated May 2020
DCRTR virus Removal Guide
What is DCRTR ransomware?
DCRTR ransomware – a file locker that can make important files inaccessible as long as victims won't pay the ransom
DCRTR ransomware is a file-encrypting virus that uses a strong encryption[1] algorithm and appends .dcrtr file extension. When all targeted files are encrypted, malware downloads a ransom note called ReadMe_Decryptor.txt where criminals tell to contact them via decryptor@cock.li email address. DCRTR virus typically spreads as an obfuscated email attachment.[2] Once a victim opens it, the malicious payload is dropped to the system. Malware immediately alters Windows Registry, downloads malicious files, and might affect legit system processes. As soon as it makes a presence on the affected machine, the ransomware virus runs a data encryption procedure. Crypto-malware targets the most popular types of files, such as Microsoft Office documents, images, audio, video files, databases, or archives.
According to researchers, the .dcrtr extension is not the only one that DCRTR ransomware is using. Since 2018 it has been updated several times and currently has WDM-DCRTR, DCRTR-Crypt, Cryptes, Parrot, and Rhino versions behind its back. The latter variant emerged in May 2020 and can be distinguished from the .rhino appendix and double ransom files info.hta and ReadMe_Decryptor.txt.
| Name | DCRTR |
|---|---|
| Type | Ransomware |
| New version | WDM-DCRTR, Parrot, and Rhino |
| Extensions added | [decryptor@cock.li].dcrtr, .crypt, [cryptonationusa@protonmail.com].parrot, [generalchin@countermail.com].rhin, .CRYZP, .COPAN, .COLORIT, .GOLD, .SOS, .STAFS, .LOCK, .cryptes, .java |
| Ransom message | ReadMe_Decryptor.txt, HOW TO DECRYPT FILES.txt, info.hta |
| Email address | decryptor@cock.li, masterdecrypt@openmailbox.org, dekode@qq.com, Sosca@foxmail.com, cryptonationusa@protonmail.com, generalchin@countermail.com, generalchin@countermail.com billy_will_help_you@protonmail.com, btcbrewery@india.combtcbrewery@protonmail.com, corova@qq.com, porasa@qq.com, raceso@qq.com, supdecrypt@foxmail.com, supportdecryption@cock.li |
| Encryption ciphers | A combination of AES, SHA, and RSA algorithms is used |
| Target | The most popular types of files that are locked by the ransomware – images, audios, videos, text files, databases |
| Main distribution source | Spam messages and their rogue attachments |
| Removal process | Perform the elimination as soon as you spot the first symptoms. You can use SpyHunter 5Combo Cleaner to detect all possibly damaged objects in the system |
| vIRUS DAMAGE | Experts recommend fixing virus damage with a repair tool FortectIntego. Otherwise, registry entries, Windows files, and processes that the ransomware might have corrupted may be left malfunctioning |
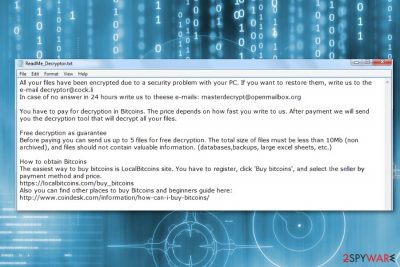
Malware uses a combination of AES, SHA and RSA ciphers to make files on the device inaccessible. The significant feature of the DCRTR is the appended file extension. Typically, it adds [decryptor@cock.li].dcrtr suffix to targeted data. Following the successful encryption, the malware provides a ransom-demanding message to the victims. In the text file, authors of DCRTR malware asks to send an email to decryptor@cock.li. Victims are urged to do it immediately because the size of the ransom depends on the writing speed.
The DCRTR ransom message looks like this:
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail decryptor@cock.li
In case of no answer in 24 hours write us to theese e-mails: masterdecrypt@openmailbox.orgYou have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Crooks also offer to add 5 files for free decryption in order to prove they actually have the DCRTR decryptor. According to the ransom note, victims should receive a response with the number of Bitcoins they have to pay in order to use the criminal’s decryptor. However, if they do not receive a letter in 24 hours, they should send an email again to masterdecrypt@openmailbox.org.
However, paying the ransom is not recommended[3] because crooks might disappear once they receive your transaction. What is worse, they might ask you to pay more money by threatening that your files will be leaked or deleted. We guess that you definitely do not want to face money losses, especially useless ones. You should not get tricked by these threats and remove DCRTR virus from the device.
Unfortunately, DCRTR removal won’t recover your files. However, virus elimination is needed to clean and fix your computer in order to use it safely again. For that, we highly recommend using SpyHunter 5Combo Cleaner or Malwarebytes tols. Once your device is virus-free, you can use data backups or try alternative recovery methods. Find third-party software below this article and choose the most attractive tool for you. Perform each step as shown in the guidelines and you might be able to restore some of your files successfully.

DCRTR ransomware versions
WDM-DCRTR ransomware
At the beginning of November this year, a new version of DCRTR ransomware was released. This file-locking cyber threat is called very similarly – WDM-DCRTR ransomware. The virus operates in the same way as its old variant. Once installed, it uses unique encryption ciphers to lock important documents on the infected computer. Files appear with the .crypt extension and cannot be loaded successfully until they are blocked by the ransomware virus.
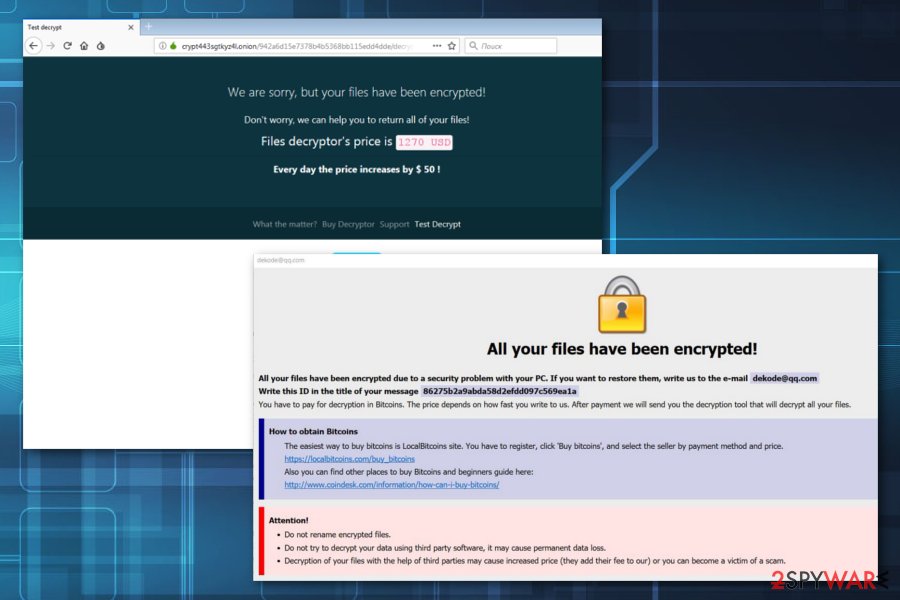
You can recognize WDM-DCRTR virus from this file: FileCryptor.pdb. This sneaky cryptovirus can display various ransom notes. The ransom message can appear as HOW TO DECRYPT FILES.txt. What is even more interesting, WDM-DCRTR ransomware imitates other ransomware viruses. The payment page is designed in the same way as GandCrab-ransomware's, a ransom note's text related to the Rapid ransomware. The content of this message says:
the Hello, dear friend E!
Have your files is the All Been The ENCRYPTED
the Do you really want to the restore your files is?
Our email to the Write – dekode@qq.com
and tell's us your unique ID – ID-XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Nevertheless, WDM-DCRTR uses the Dharma-related Info.hta files to launch one of the ransom notes. So, as we can see, this cryptolocker tries to imitate other viruses by using similar content. This cyber threat also reaches the system via dubious email messages and their attachments. However, you can get easily messed up which ransomware[4] has infected your PC once you see the note.
Parrot ransomware
It seems that DCRTR ransomware is still in an active development phase since its family keeps growing in 2020. Ransomware researchers detected a Parrot ransomware strain in February after people started reporting files encrypted by [cryptonationusa@protonmail.com].parrot.
Likewise its predecessor, Parrot ransomware takes advantage of the mixed AES and RSA cryptography model, which allows criminals to affect all non-system files and render them useless without a unique decryption key. Victims are demanded to write an email to cryptonationusa@protonmail.com and append one locked file, which is less than 500kb for test decryption.
A quick description of the ransowmare fact is outlined in the ReadMe_Decryptor.txt file positioned on the desktop, which stands for a ransom note. The size of the redemption is not specified, although it's stated that the payment is expected in Bitcoin cryptocurrency.
Rhino ransomware
Rhino is yet another DCRTR ransomware family member. Revealed in the middle of April 2020, it is circulating on the internet as a malicious payload attached to email messages. Experts warn that Coronavirus-themed campaigns may be currently used to drive this malware.
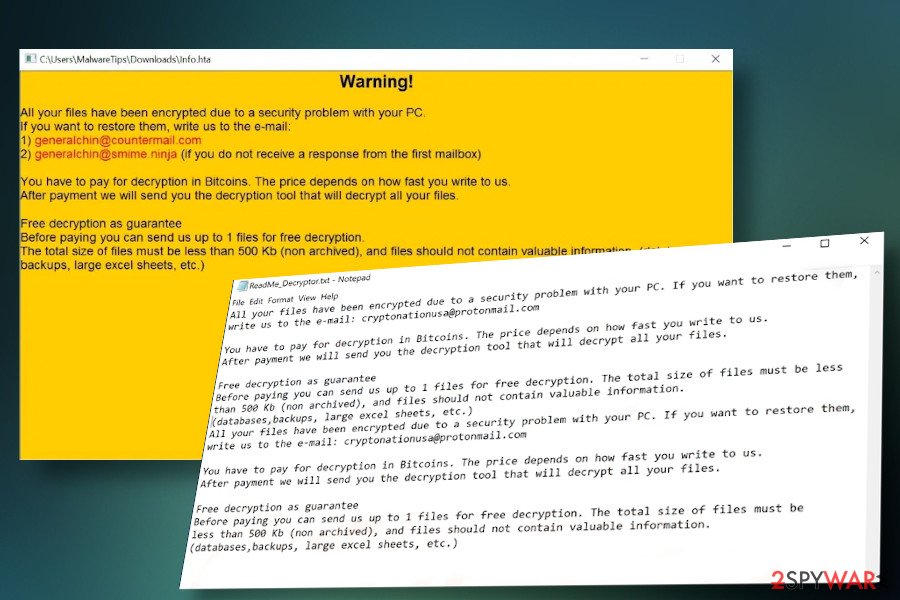
In fact, it's homogenous with the previous Parrot and WDM-DCRTR variants, except that it uses a distinctive file extension, which is [generalchin@countermail.com].rhino. Besides, it shows an unusual trait to drop two ransom notes, one on the desktop and the other in the %APPDATA% directory. Victims can find info.hta and ReadMe_Decryptor.txt ransom notes, which contain the following instructions:
Warning!
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail:
1) generalchin@countermail.com
2) generalchin@smime.ninja (if you do not receive a response from the first mailbox)
You have to pay for decryption in Bitcoins . The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 1 files for free decryption.
The total size of files must be less than 500 Kb (non archived), and files should not contain valuable information. (databases, backups, large excel sheets, etc.)
Unfortunately, none of the DCRTR ransomware versions, including Rhino, can be decrypted for free. The victims are expected to pay a ransom ranging from $500 to $1500 in Bitcoins to get a personal decryption software. However, financial support for criminals is not a good idea, especially having in mind that it may lead to identity theft. Instead of paying, remove Rhino with a tool like SpyHunter 5Combo Cleaner and try to retrieve locked files with a reputable security tool.
Methods used for spreading file-encrypting viruses
The virus might be attached to any spam email that appears in your inbox. Malicious spam emails are the primary ransomware distribution methods. Thus, be careful when opening emails from unknown senders and do not rush opening attached files even though they look safe and legit. If you are not expecting to receive anything important lately, better delete all unrecognizable messages that you receive.
Furthermore, ransomware executable might hide under ads on various websites, presented as a software update or any illegal software that you can download from file-sharing websites. Keep in mind that security programs do not always protect from malware if you download malicious files yourself. Additionally, be careful once browsing on pages that you have never seen before as their links might also have malware-laden content injected.
Security experts from LesVirus.fr[5] also remind to create copies of the most important files and save them in the external storage devices. They will be very helpful if ransomware hits your PC. However, if you decide to purchase a USB flash drive, make sure that you keep it unplugged when it is out of usage.
Get rid of DCRTR virus
DCRTR removal is too complicated to perform manually. Therefore, you should not try to locate and delete any malware-related files. This may lead to irreparable damage to the system. For this reason, you should choose reliable software that will take care of your PC. We recommend using FortectIntego or Malwarebytes to get rid of the cyber threat from your machine. These programs are strong enough to clean your PC from malicious components.
However, after you remove DCRTR virus, you should also reboot the system to Safe Mode with Networking to disable the virus first. In this way, crypto-virus won’t be able to disturb its elimination. After you perform these steps, you can start thinking about the data recovery process. We have provided some methods below this article which we advise trying.
Getting rid of DCRTR virus. Follow these steps
Manual removal using Safe Mode
Rebooting System to Safe Mode with Networking ensures that automatic ransomware elimination is smooth:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove DCRTR using System Restore
System Restore methods might also be helpful to disable the virus:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of DCRTR. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove DCRTR from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Take a look at the below-given methods as some of them might appear to be truly helpful. Make sure you carry out each step exactly as shown in the instructions to reach the best results possible.
If your files are encrypted by DCRTR, you can use several methods to restore them:
Try to recover files with Data Recovery Pro
Data Recovery Pro is NOT a ransomware decryptor. However, this tool might help to recover some of the damaged files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by DCRTR ransomware;
- Restore them.
Access the most important files using Windows Previous Versions feature
This method is helpful to recover important individual files by following the steps below. However, this method requires being enabled System Restore before DCRTR attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try ShadowExplorer for data recovery if possible
ShadowExplorer recovers files from Shadow Volume Copies. So, if ransomware did not delete them, follow these steps to recover your files:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
DCRTR decryptor is not available yet.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from DCRTR and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Margaret Rouse. Encryption. Search Security. Tech Target.
- ^ Swati Khandelwal. Massive Email Campaign Sends Locky Ransomware to Over 23 Million Users. The Hacker News. Online cyber security news and analysis.
- ^ Why You Should Not Pay WannaCry Ransomware. Tripwire. IT news, trends, and insights.
- ^ Ransomware. Wikipedia. The free encyclopedia.
- ^ Les Virus. Les Virus. French cyber security news.





















