GandCrab ransomware (Free Instructions) - 2021 update
GandCrab virus Removal Guide
What is GandCrab ransomware?
GandCrab ransomware is one of the most prolific ransomware viruses worldwide, but most of its versions can be decrypted now
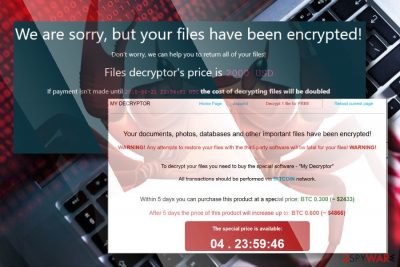
GandCrab ransomware is an infamous family of cryptoviruses that was first introduced in early 2018. Within a year, it has earned a name as one of the most destructive cyber infections in the world. The family consists of numerous variants, such as GDCB, KRAB, CRAB virus, etc. All these versions are using RSA 2048 and AES 256 algorithms to encode data and are appending a random and unique file extension to mark doomed victim's data. At the moment of writing, the most aggressive versions are 5.0.4 and 5.1.
The ransomware has been using an array of various distribution methods, including RIG, GradSoft, Magnitude, and Fallout exploit kits,[1] cracks, keygens, and fake updates. While the malware is one of the most devastating threats currently, Bitdefender research team, while working with Europol and Romanian police, managed to create the 3rd decryptor that works for versions 1, 4, 5.0.1 through 5.1.[2]
| Name | GandCrab |
|---|---|
| Type of malware | Ransomware |
| Discovered | January 30, 2018 |
| Systems affected | Windows |
| The extension added to infected files | .gdcb, .crab, .krab, .KRAB, .lock, .[random_characters] |
| Ransom note | GDCB-DECRYPT.txt; KRAB-DECRYPT.txt; krab-decrypt.txt, [randomly_generated_extension]-DECRYPT.html, [victim's ID]-DECRYPT.txt, [victim's ID]-DECRYPT.html |
| TOR ID used | ransomware@sj.ms |
| Amount of ransom | Might vary depending on a version |
| Decryptable? | Yes. Download a decryptor from Bitdefender here. Additionally, you can also try an alternative tool. |
| Elimination | Use SpyHunter 5Combo Cleaner for ransomware removal |
| System fix | After you get rid of ransomware using security program, fix damaged system components with FortectIntego |
In the beginning, after two months of active distribution, the first versions of ransomware were defeated by the Romanian police, experts from Bitdefender, and Europol. After revealing the flaw in the ransomware code, authorities hacked cybercriminals, and Bitdefender created a free decryptor available on the NoMoreRansom project.[3]
However, it seems that virus developers are not likely to give up. During the first months of 2019, they presented several new versions demanding the 2000 USD ransom in Dash or Bitcoin in exchange for the decryption key. The improved versions 5.0.4 and 5.1 haven't been decrypted because hackers patched the critical flaw within 24 hours after the Bitdefender decryptor was released.
At the moment, the virus is appending .[random characters] file extension. Additionally, the victim is given a Tor address to buy the so-called Gandcrab Decryptor from virus creators. However, you should be careful when dealing with hackers because making a payment does not guarantee that you will get the key that you need. The quote from one of the latest victims reveals that you can be left with nothing:
Our outsourced IT, Protek Support, received a ransomware on their master server affecting all their 80 clients including us yesterday morning. They’ve paid the ransom this morning about 7 am, but we are still waiting to get our files decrypted and it’s already 4:45 pm.
If you have even the slightest suspicion that you can be infected, make sure you take care of GandCrab removal by using tools like SpyHunter 5Combo Cleaner. Additionally, try free decrypters given in the table above. If none of them help, delete the virus to prevent additional data loss. Then, keep your files somewhere in a safe location until the decryptor for your version is released.
Actions proceeded by ransomware after infecting the system
Following the infiltration, ransomware starts collecting information about its victim, including user name, PC name, OS, and similar data. Additionally, the virus creates a unique ransom ID and starts encrypting files stored on the system. As a result, the user is no longer able to access encrypted files without a key that is saved in C&C servers and can't be obtained without a ransom.
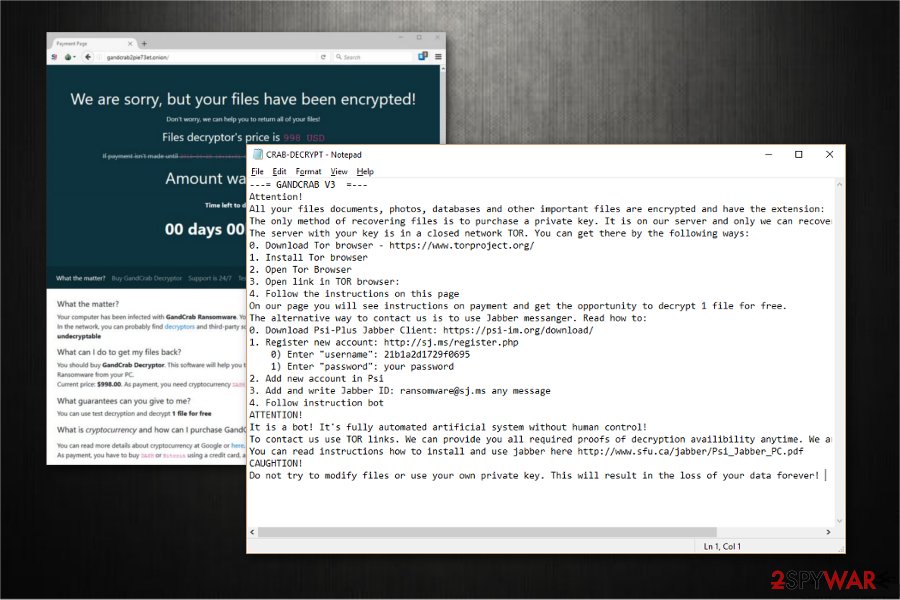
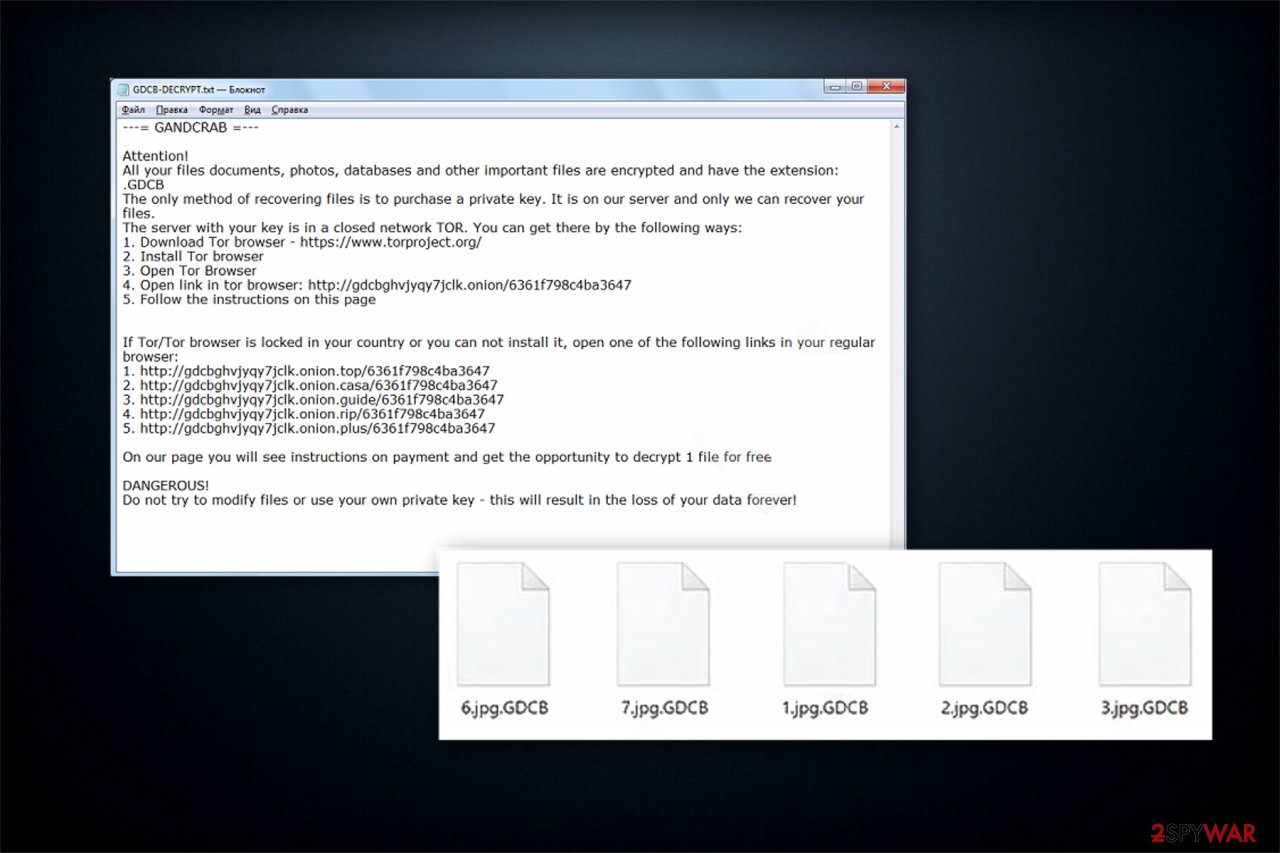
The entire situation, explaining what happened and what has to be done to recover files, is described in the ransom note, saved in every folder with the encrypted data. The file can be named GDCB-DECRYPT.txt, KRAB-DECRYPT.txt, or [victim's ID]-DECRYPT.txt and should never be deleted if you are willing to buy a decryptor. That's because it should be uploaded to a specially-crafted TOR site.
The first versions were using such message:
—= GANDCRAB =—
Attention!
All your files documents, photos, databases and other important files are encrypted and have the extension: .
The only method of recovering files is to purchase a private key. It is on our server and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
1. Download Tor browser – https://www.torproject.org/
2. Install Tor browser
3. Open Tor Browser
4. Open link in tor browser: http://gdcbghvjyqy7jclk.onion/[id]
5. Follow the instructions on this pageOn our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
DANGEROUS!
Do not try to modify files or use your own private key – this will result in the loss of your data forever!
Newer variants as displaying the following message to their victims. As you can see, you can't :
—= GANDCRAB V5.1 =—
***********************UNDER NO CIRCUMSTANCES DO NOT DELETE THIS FILE, UNTIL ALL YOUR DATA IS RECOVERED***********************
*****FAILING TO DO SO, WILL RESULT IN YOUR SYSTEM CORRUPTION, IF THERE ARE DECRYPTION ERRORS*****
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension:
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————-
| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor browser
| 2. Open Tor Browser
| 3. Open link in TOR browser: [link]
| 4. Follow the instructions on this page—————————————————————————————-
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
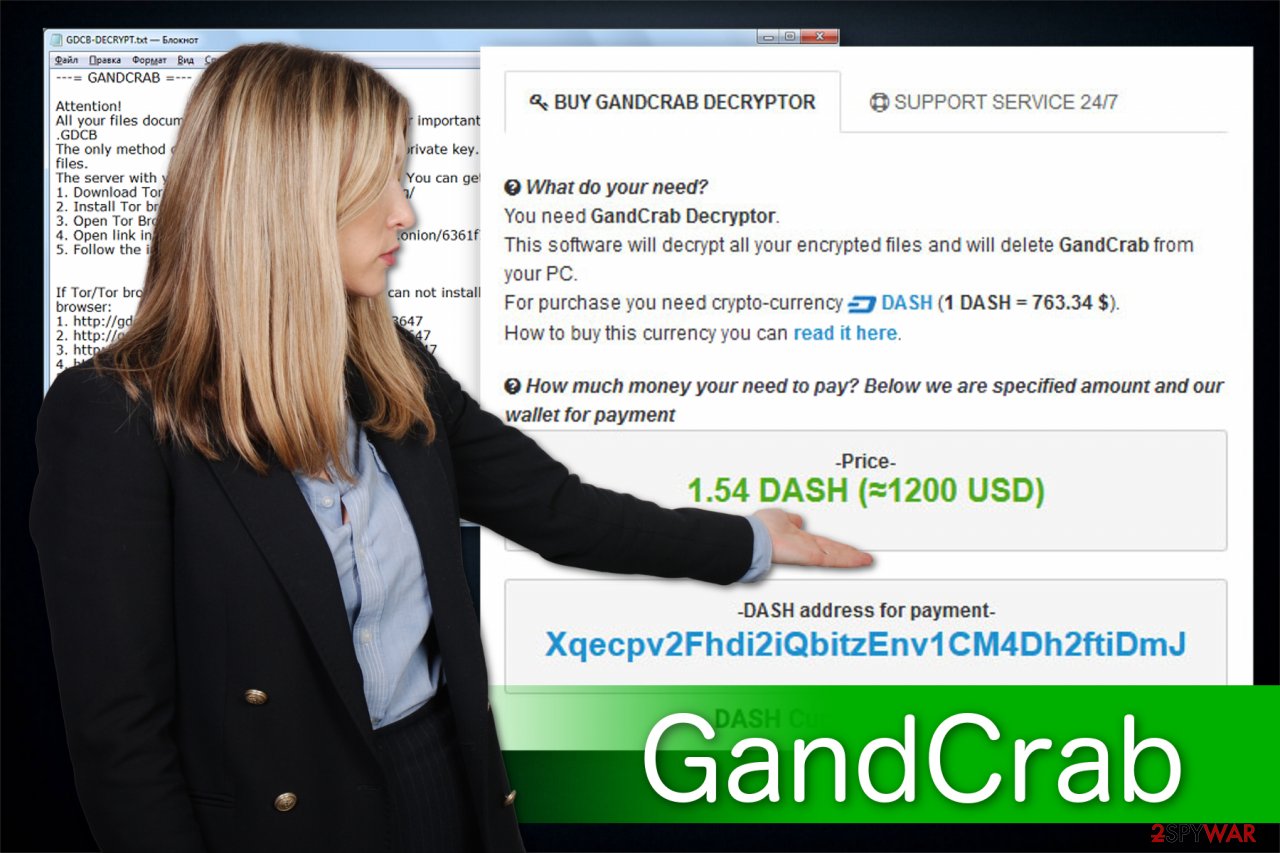
Once the victim downloads the Tor browser and clicks the link provided in the ransom note, he/she is led to the attacker's website selling the decryptor. Here, the popup titled “GandCrab authentication” shows up, which starts the procedure by requesting to upload the ransom note at first. That's why cybercriminals are claiming in their ransom note: “Under no circumstances do not delete this file.”
Additionally, the official site is “unlocked” and presents payment instructions, the amount of the ransom (approximately $1200), services that can be used to exchange the money to bitcoin or DASH cryptocurrency, the address where the money should be sent to and a possibility to upload one file for free decryption. According to hackers, postponing the payment can double the ransom amount.
We should add that the site is well-designed and unique, filled with cartoons and such features as chat support. However, it seems that you can be banned from the assistance for using harsh language.
It is worth mentioning that ransomware identifies a specific period that should be obeyed to make the transaction, or the amount of the payment will double. However, this is merely an attempt to intimidate the victims and force them to pay the ransom without evaluating other options.
Therefore, we strongly advise you not to follow the rules of the criminals since there are alternative ways to get back access to your files or use the decryptor developed by the experts. For that, you must remove ransomware first.
Experts from NoVirus.uk[4] have already warned affected users that this is a highly dangerous computer virus and should be eliminated with the help of a professional or using a robust antivirus. You can find detailed instructions on how to start the elimination procedure at the end of this article.
Additionally, do NOT try to get rid of the virus by yourself. Such complex ransomware-type infections are designed to hide their presence and disguise as legitimate computer processes. Terminating crucial system files might lead to permanent computer damage and re-appearance of the crypto-malware. Thus, we recommend using the elimination guide below.
Exploit kits have been actively used in virus distribution
Hackers have employed numerous tactics to infiltrate computers with ransomware. However, exploit kits are considered the most sophisticated ones as they can successfully detect and identify system vulnerabilities and then misuse these holes for the attack. Experts note that this ransomware strain has been distributed via the following exploit kits[5]:
- Rig EK;
- GrandSoft EK;
- Magnitude EK;[6]
- Fallout EK.
The Magnitude Exploit Kit, previously used to spread Magniber ransomware, has mainly been used to spread GandCrab ransomware version 2. The EK renders a fileless technique used to execute the virus, which is encoded using VBScript.Encode/JScript.Encode scrip and injected into memory. When the payload is being executed, the ransomware roots into the explorer.exe file and forces the PC to reboot. After that, it enables the encryptor and locks files with the unique file extension.
Ransomware has also been distributed via a malvertising[7] campaign known as Seamless. With its help, victims are lead to yet another exploit kit called RIG EK. After detecting system vulnerabilities, it exploits them to infect the targeted system with a file-encrypting virus or another dangerous computer virus.
Additionally, the Fallout exploit kit has been used to distribute the Vidar data stealer, which additionally drops the 5.0.4 payload via its command and control server. This function can be configured by the administrator when configuring the malware initially. Upon further inspection, it seems that malware is distributed via malvertising campaigns and even sold as a product online.
Finally, the virus has also been distributed as a Ransomware-as-a-Service (Raas) on the Russian black web. According to the Check Point, hackers have already collected more than 600,000 USD ransom due to the innovative Affiliate Program. Ransomware developers have been paying the participants from 60% to 70% of ransomware revenue in exchange for 24/7 tech support.
According to researchers, this crypto-malware has almost 100 active affiliates; 80 of these participants have successfully dispersed 700 different samples of the malware. More than 70% of infected PCs are located in the UK and US, so it's dedicated to English-speaking PC users. However, the recent version provides several languages to choose from, including German, Italian, French or Japanese languages.
Other methods used for infecting systems with Ransomware
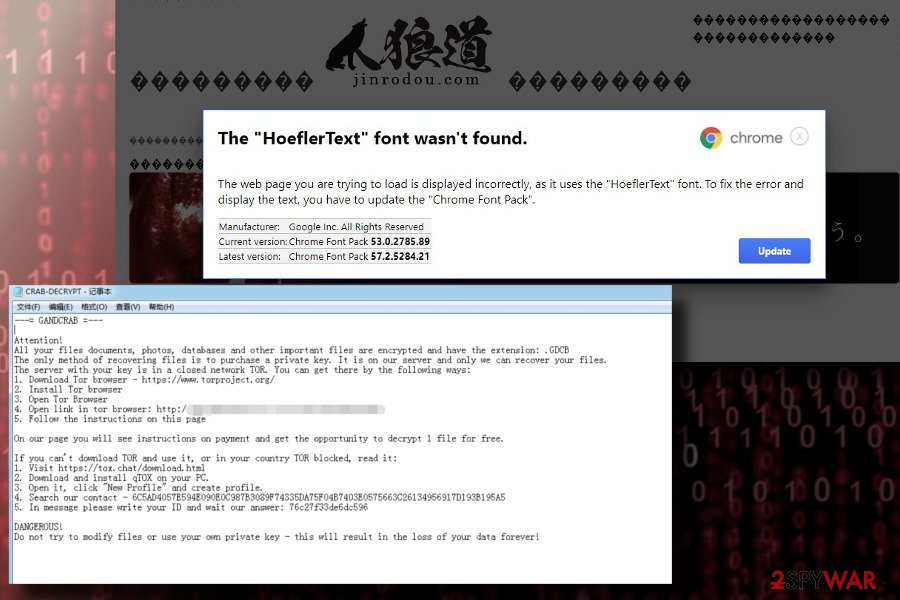
It is worth knowing that exploit kits are not the only way how ransomware is distributed. Criminals might take advantage of credulous people and use deceptive spam emails with malicious attachments. Usually, these emails disguise themselves as shopping receipts, invoices, or similar documents from well-known brands and companies. Likewise, naive users open the infected attachments and let the cyber threat in.
The first campaigns relied on the “Receipt Feb-21310 [random numbers]” attachment, using the @cdkconstruction.org suffix. This spam email does not have much information, except points out that “DOC attached,” which should never be downloaded to the system. Otherwise, the .doc file subsequently runs a PowerShell script and creates an exploit file (sct5.txt), which currently affects a 64-bit system. As pointed out by various crypto-malware researchers, the sct5.txt file does not run the ultimate payload of the virus but executes an exploit and runs as a medium for malware to get inside.
The latest Gandcrab 5.1 virus has been actively relying on emergenсy exit maр spam, which reads and includes an attachment named “Emergencyexitmap.doc:”
Hi All,
Please find bеlow the Uр tо date еmеrgency exit maр.Please see Emergency exit map in the attachment..
Thаnks,
Rоsie L. Ashton,
Еstаtе Mаnаgemеnt
If you happen to receive such an email, the most important thing is not to enable macros that are typically disabled by software makers. Make sure that the Protected view is enabled and ignore emails from unknown senders.
In January 2019, a new malspam campaign “Love You”[8] was noticed by security researchers that targeted users in Japan. It includes the name of a popular Japanese show business star, along with an emoji presented in the subject line. The phishing email contains an attachment PICo-[9 digit number]2019-jpg.zip that administers the payload. In addition to 5.1 version, the “Love You” campaign also distributes various other payloads, including XMRig mining malware and Phorpiex worm.
New variants are detected almost every month. Find your version
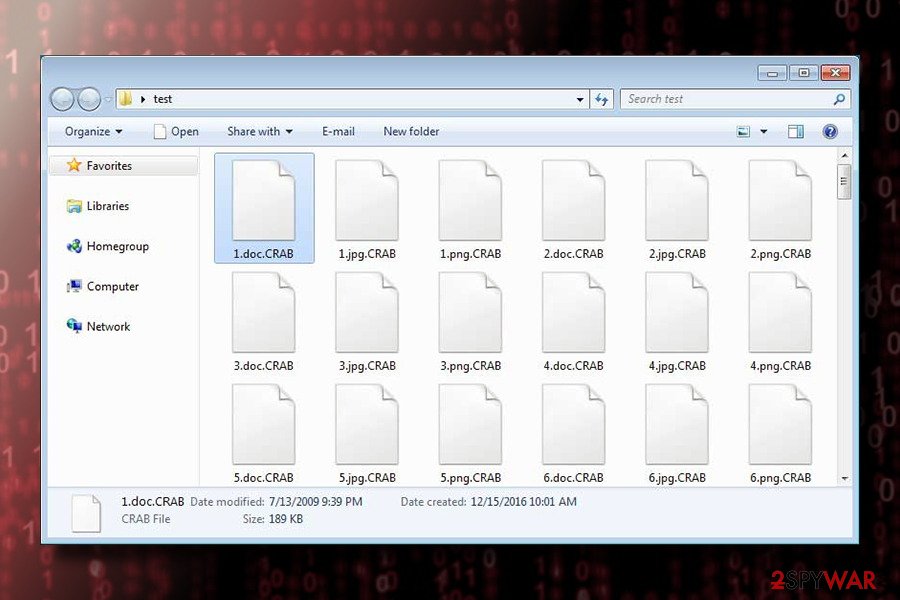
GDCB file extension virus
GDCB file extension virus is one of the first versions of the virus was detected in January 2018. It showed up a couple of weeks after the release of the original version. Just like its predecessor, it spreads via infected spam email attachments and runs a payload once the attachment is opened. The virus has been targeting the most popular files, including but not limited to .doc, .txt, .jpg, .png, .audio, .video, etc. and appending .GDCB file extension to each of them. It creates a GDCB-DECRYPT.txt file on the victim's desktop, which urges to download Tor browser and transmit 1.54 DASH ransom. The amount of the ransom increases if the victim is late to pay it.
Get GandCrab decryptor for free
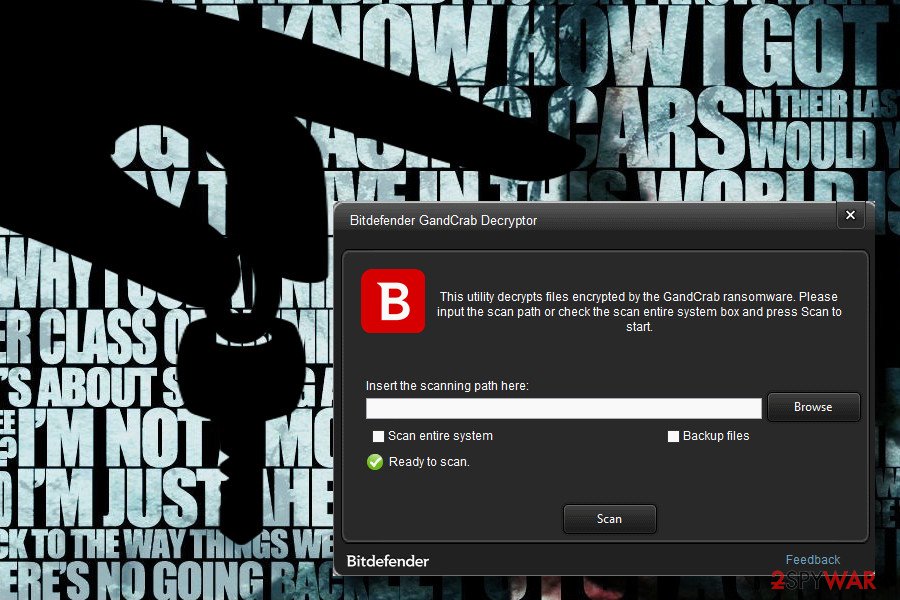
Cybersecurity experts at NoMoreRansom.org have already presented a decryptor for v1, v4, and v5. People who got infected with this cyber threat and find the following extensions can install a free tool to recover their encrypted files without paying the ransom: .GDCB, .CRAB, .KRAB, .UKCZA, .YIAQDG, .CQXGPMKNR, .HHFEHIOL. You can download it by clicking this link. Additionally, you can download the tool from Raj Samani security expert. However, having in mind that this virus family has numerous versions, sometimes these decryptors can fail to recover your files.
Before you rush with this procedure, note that the experts recommend installing and using the decryption tool only after getting rid of ransomware first. Otherwise, the ransomware will continue to encrypt data on the victimized computer over and over again. Use only professional security tools to delete ransomware from the system. We strongly advise you use the ones which are provided at the end of this article.
If you are unable to regain access to the compromised information with the official decryption tool, there are alternative methods that might help. For example, only some of the virus versions are designed to delete Shadow Volume Copies, so you can use ShadowExplorer or similar third-party tools to recover at least some of the files. Additionally, you can fully recover files without paying the ransom by using backups. If you do not have them, you should check our prepared alternative data recovery methods at the end of the article and try the decryptor as well.
Also, note that version 4.1.2 and version 5.1 have two different vaccine apps that can trick the virus into thinking it already has encrypted files on the computer. These apps typically create the special file in advance and, this way, make the ransomware to think it has already encrypted this data.
To protect yourself from GandCrab 4.1.2, get this tool here. However, the virus hasn't been active during the latest period. At the moment of writing, the most active virus is 5.1 which has been relying on numerous techniques to get into the system. To protect yourself from this threat, download the vaccine created by Valthek. (direct link)
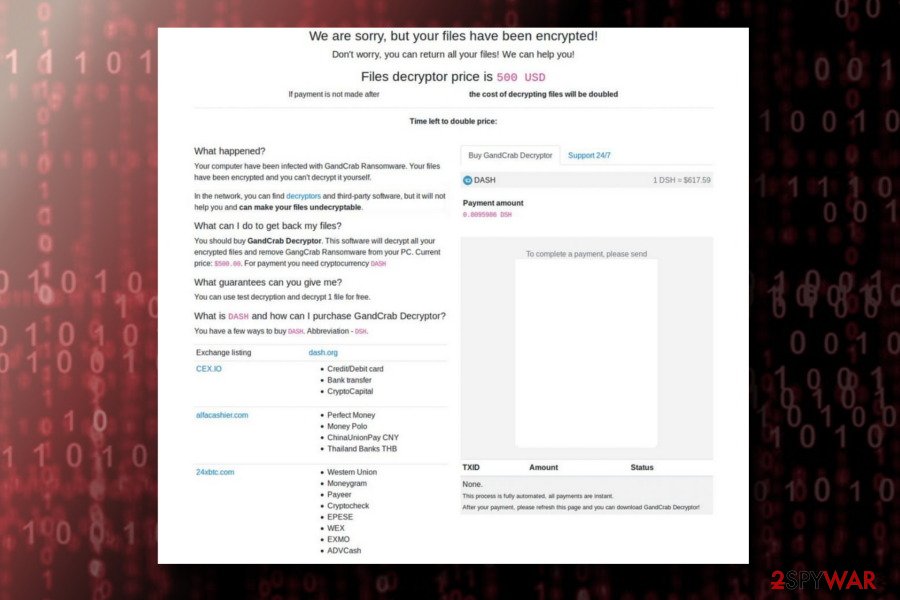
Before you proceed to data recovery, get rid of GandCrab ransomware
If you want to recover compromised files, you must remove GandCrab ransomware first. Unfortunately, there are not many options on how you can do that. In fact, only one — you must download a professional malware removal software and let it scan your PC files thoroughly.
To fix the system, download professional security software as soon as you notice encrypted files on your computer. We recommend using [d12] or SpyHunter 5Combo Cleaner for removal, which has been used while testing the virus. After installing one of these apps, run a full system scan and let it terminate this file-encrypting virus. FortectIntego can also be used to fix virus damage done to the Windows system automatically. Unfortunately, these programs have nothing to do with the decryption of encrypted files.
Note that you might not be able to install the malware removal tool at first. For that, you must reboot your computer into Safe Mode with Networking or rely on System Restore. You can find a step-by-step guide on how to do that and get rid of this ransomware at the end of this article. Additionally, our experts have prepared alternative methods to help you disable this malware and recover files encrypted by ransomware.
Getting rid of GandCrab virus. Follow these steps
Manual removal using Safe Mode
Rebooting your computer to Safe Mode with Networking is the first step in ransomware elimination procedure.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove GandCrab using System Restore
To get rid of this ransomware with the help of System Restore, follow these steps:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of GandCrab. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove GandCrab from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by GandCrab, you can use several methods to restore them:
Data Recovery Pro can help you get back the compromised data
This is a great tool for data recovery since it does not require any additional functions enabled on the system. Note that is is also useful if you have lost your files due to a system crash.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by GandCrab ransomware;
- Restore them.
Windows Previous Versions Feature helps to recover encrypted files
You can travel back in time with Windows Previous Versions if you have System Restore function enabled before ransomware attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use the available decryption tool
Experts have designed a unique decryption software for GandCrab ransomware. You can get it here. In case it doesn't decrypt specific malware versions, feel free to try alternative recovery methods above.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from GandCrab and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ New Exploit Kit Fallout Delivering Gandcrab Ransomware. Trend Micro. Malware researchers.
- ^ Catalin Cimpanu. Bitdefender releases third GandCrab ransomware free decrypter in the past year. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ Bogdad Botezatu. GandCrab Ransomware decryption tool. Labs Bitdefender..
- ^ NoVirus. NoVirus. Security and Spyware News.
- ^ Exploit Kits. F-Secure. Cyber Security Solutions for your Home and Business.
- ^ Jerome Segura. Magnitude exploit kit switches to GandCrab ransomware. Malwarebytes Labs.
- ^ Dilan Samarasinghe. Malvertising. CIS. Center for Internet Security.
- ^ Juraj Jánošík. “Love you” malspam gets a makeover for massive Japan-targeted campaign. WeLiveSecurity. ESET official blog.





















