Rapid ransomware (Removal Guide) - Feb 2020 update
Rapid virus Removal Guide
What is Rapid ransomware?
Rapid ransomware — a dangerous cryptovirus that targets users from USA and Europe by using fake IRS emails
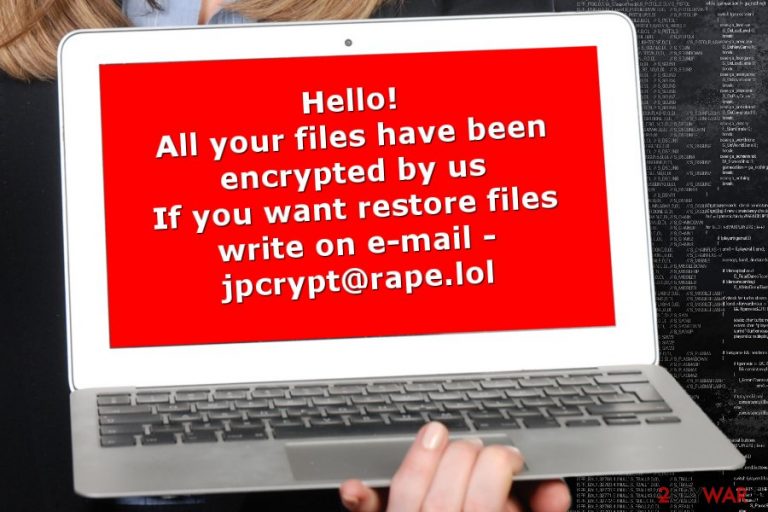
Rapid ransomware is a malicious crypto-virus circulating on the Internet since January 2018. During the seven months of its existence, malware has changed four times. The virus encrypts files using AES encryption algorithm and appends .Rapid file extension to each locked file. The latest version hailing from this family – RPD ransomware. It attaches .RPD file extension and drops How Recovery File.txt ransom note instructing the victim on how to contact criminals and send them the requested amount of money. The amount of ransom varies and is mostly selected depending on how many files are encrypted and how soon the victim reaches virus developers.
| Name | Rapid |
|---|---|
| Classification | Ransomware |
| Versions | |
| Danger level | High. Compromises core system's settings and encrypts personal files |
| File extension | .Rapid; .RPD; .EZYMN |
| Contact email | rapid@rape.lol; airkey@rape.lol; asgard2018@cock.li; supp1decr@cock.li; supp2decr@cock.li; demonslay335@rape.lol; anonimus852@tutanota.com, anonimus852@cock.li. |
| Related files | How Recovery Files.txt and !!! txt the README; How Recovery File.txt |
| Distribution | “Please Note – IRS Urgent Message-164” spam email, fake software updates |
| Countries targeted | Spain, France, USA |
| Decryptor | None |
| Termination | Get rid of ransomware and all its malicious files by scanning your PC with reputable anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | Repair Windows system damage after malware termination with FortectIntego |
.Rapid ransomware was noticed for the first time at the end of January. Currently, the virus is still active and keeps bothering people from Spain, France, USA, and other world's countries. Thus, we suggest you being extra cautious because, after infiltrating the system, this malware encrypts files and makes them inaccessible. The main difference between this virus and similar file-encrypting viruses is that it remains silent on the system and keeps encrypting new documents created by the user.
Rapid ransomware, most likely, infiltrates the system with the help of social engineering and malicious spam emails. At the moment the virus spread the first time, Internal Revenue Service (IRS)[1] name was used as a disguise in email letters.
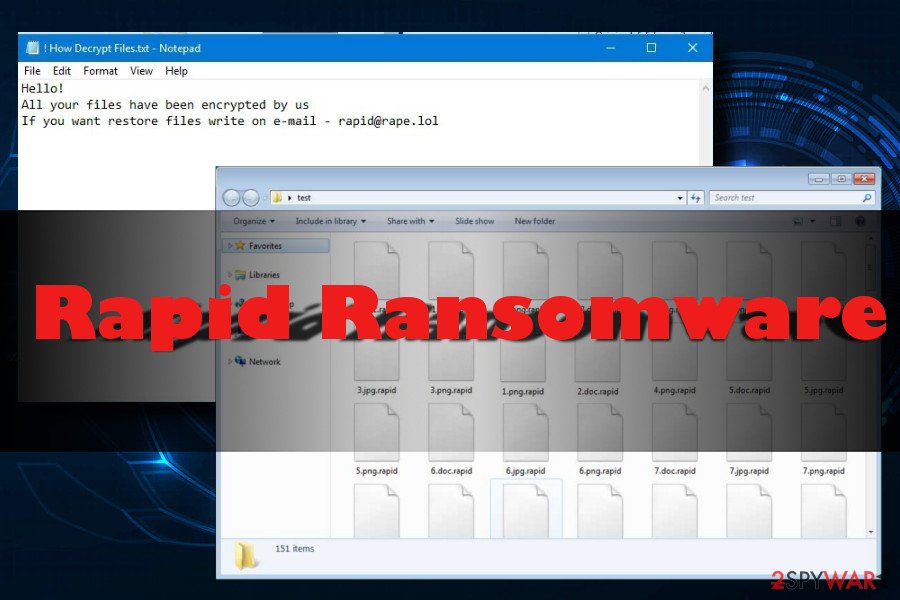
Once inside, it makes system changes and starts scanning the device for the targeted file extensions. Following the successful encryption procedure, the crypto-malware also drops a ransom note called How Recovery Files.txt or !!! txt the README. Both of them contain identical instructions saying:
Hello,
All your files have been encrypted by us
If you want to restore files write on e-mail rapid@rape.lol or airkey@rape.lol.
- rapid@rape.lol;
- jpcrypt@rape.lol;
- fileskey@qq.com;
- fileskey@cock.li;
- frenkmoddy@tuta.io;
- unlockforyou@india.com;
- support@fbamasters.com;
- airkey@rape.lol;
- help@wizrac.com
- decrfile@protonmail.com
- file.wtf@protonmail.com
Despite the fact that Rapid ransomware drops a ransom note, it's informative. It’s clear, though, that criminals will ask to transfer a particular sum of money. The payment might be set based on the number of encrypted files or how fast a victim sends an email. However, security specialists do not recommend[2] contacting authors of the Rapid virus.
The problem is that no one can assure that crooks have working Rapid ransomware decryptor or they let you use it even if you pay the ransom. Thus, you might increase your loss. Apart from encrypted files, you might lose your money as well.
Thus, if you found your files encrypted by .Rapid file extension, you should focus on cleaning your computer. Ransomware may have injected malicious code into system processes. As a result, your device became sluggish, and programs started crashing. Additionally, malware makes the system vulnerable, and it might open the back doors for other cyber threats. Thus, to avoid possible damage, you’d better remove Rapid ransomware.
Please, do not try to locate and terminate malicious components yourself. It’s a difficult task. For Rapid ransomware removal, you should use reputable security software. If you have problems with virus elimination, please check the instructions below. After that, we suggest using FortectIntego to repair Windows registry and corrupted system files.

Rapid ransomware versions
Rapid 2.0 came out in March 2018. This variant excludes Russian-speaking countries from the targeted regions and does not encrypt files of people living in here. Additionally, the virus is adding eight random numbers to encrypted files' extensions and typically uses SHA-256 chipper to encrypt them. The ransom message of this virus displayed in DECRYPT.[5-random-characters].txt file, people are suggested to contact developers via supp1decr@cock.li or supp2decr@cock.li email addresses. Please, do NOT use them to contact hackers who are hiding behind ransomware. You should run a full system scan with updated anti-spyware first and then rely on our data recovery options.
Rapid 3.0 was discovered in May 2018. This one is targeting English-speaking users in the USA and Europe. An alternative name of the virus – Rapid ransomware v3. Once it finishes modification of target files, ransomware appends [random_numbers].EZYMN file extension. This time, ransom amount was set to 0.7 BTC. The victim is given this email address to contact virus developers: demonslay335@rape.lol.
RPD ransomware is the newest variant that showed up in June 2018. It carries .RPD file extension and provides victims with two contact emails: anonimus852@tutanota.com, anonimus852@cock.li. This ransomware creates the unique identification key for each of its victims and drops the How Recovery File.txt file to require the spacial amount of ransom in bitcoin.
The ransom note of the RPD ransomware reads the following:
Hello, dear friend!
All your files have been ENCRYPTED
Do you really want to restore your files?
Write to our email – file.wtf@protonmail.com
and tell us your unique ID
Cybercriminals use fake Internal Revenue Service emails to spread .Rapid virus
Recently, cybercriminals who are working behind Rapid virus have started sending emails which claim to be from IRS. The Internal Revenue Service is a tax collection agency from the USA. Most emails come with a subject “Please Note – IRS Urgent Message-164” or similar.
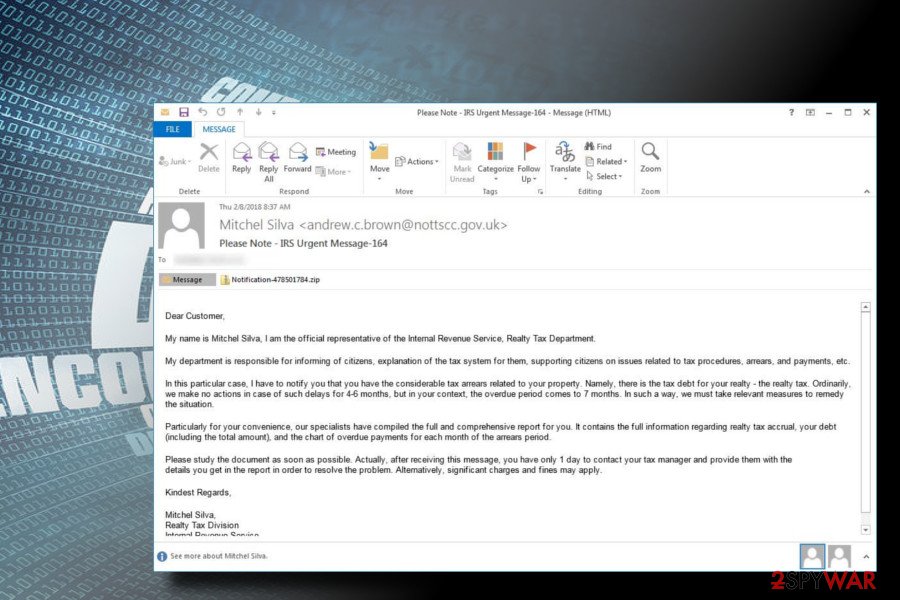
The fake email claims that the victim has not paid the correct amount of tax to the government and had to compensate for. It then encourages the user to open the attachment with “other useful information. Additionally, the person in the email states that the taxpayer only has one day to contact the tax manager; otherwise, fines might be issued.
Thus, cybercrooks are still using social engineering to scare their victims into thinking that there is an extreme urgency to contact the supposed authorities. As soon as the user unzips the attachment, he/she finds a malicious word document where a victim needs to enable macros to proceed with the installation. As soon as that is implemented, Rapid ransomware executes its malicious code.
Fortunately, it is relatively easy to recognize the scam used to spread Rapid ransomware. First of all, IRS does not contact users by email or text messages. Additionally, we must note that the Internal Revenue Service is a US body, the email address comes from the UK, and the file executable is displayed in German. Therefore, watch out for these danger signs.
Insecure emails are commonly used in spreading ransomware
Criminals often spend much time while trying to develop techniques which would allow them to infect computers easily. So far, the crooks have highly beloved malspam campaigns that have been actively targeting health[3] and other sectors. They send fraudulent emails letters with malicious attachments inside. This way people are tricked to install ransomware by themselves.
However, spam emails are not the only way how hackers distribute high-risk computer infections. According to malware analysts from LesVirus.fr,[4] malware might enter the system when users:
- download illegal content;
- install fake programs or updates;
- click on malware-laden ads.
Thus, you have to be careful with the content you download from the Internet. Additionally, keep all your software and operating system updated. It prevents malware from using security flaws to launch the attack.[5]
Installing a reputable antivirus is also a good tip for ransomware prevention. However, you should not forget that even the most reliable security program cannot fully protect you from cyber threats if you do not be responsible online.
Remove Rapid ransomware using reputable security software
To remove Rapid ransomware, you should use tools that can be trusted. Only this can ensure that you are avoiding other improved versions of the same virus. In fact, file-encrypting viruses can easily install additional malicious programs and complicate the elimination process. These type of programs are similar, but only IT professionals can get rid of Rapid ransomware manually.
Automatic Rapid ransomware removal requires you to employ an antivirus. You can use SpyHunter 5Combo Cleaner or Malwarebytes to make the elimination procedure even easier. However, dangerous computer threats tend to block users from downloading professional malware removal tools or performing a scan on the device. Therefore, you can use a few tools to double check. Also, do not forget to fully clean your system and only then attempt to decrypt data.
Unfortunately, Rapid ransomware decryptor is still unavailable because of the extensive encryption algorithm used by the virus. However, you should definitely try the methods provided below that involve third-party software.
Getting rid of Rapid virus. Follow these steps
Manual removal using Safe Mode
If your anti-virus is blocked by a .rapid virus, you must reboot your computer in Safe Mode with Networking. This procedure will prepare your system for ransomware removal.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Rapid using System Restore
If Safe Mode fails to work for you while trying to get rid of ransomware, try using System Restore method to launch antivirus:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Rapid. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Rapid from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.To recover encrypted .rapid files, use the following guide. It provides several tips that can be used to unlock locked files and start using them again.
If your files are encrypted by Rapid, you can use several methods to restore them:
Get help from Data Recovery Pro
In case you do not store backups, feel free to use this professional recovery tool.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Rapid ransomware;
- Restore them.
ShadowExplorer might be useful
If Rapid ransomware failed to delete Shadow Volume Copies, you might take advantage of ShadowExplorer software and recover encrypted data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Experts are currently working on Rapid ransomware decryptor.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Rapid and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ The official IRS website. The Internal Revenue Service. Tax collection agency of the USA.
- ^ Kacy Zurkus. Why you shouldn't pay the ransomware fee. CSO Online. Latest information and best practices on business continuity, data protection, and cyber security.
- ^ Nicholas Leider. Hostage crisis? Ransomware is a threat that demands disaster planning. Clinical Innovation + Technology.
- ^ Les Virus. Les Virus. Cyber security news.
- ^ Richard Smith. How to protect your business from ransomware cyber attacks. Dynamic business. The premier destination for SMEs and startups.







