DevilsTongue malware (Free Guide)
DevilsTongue malware Removal Guide
What is DevilsTongue malware?
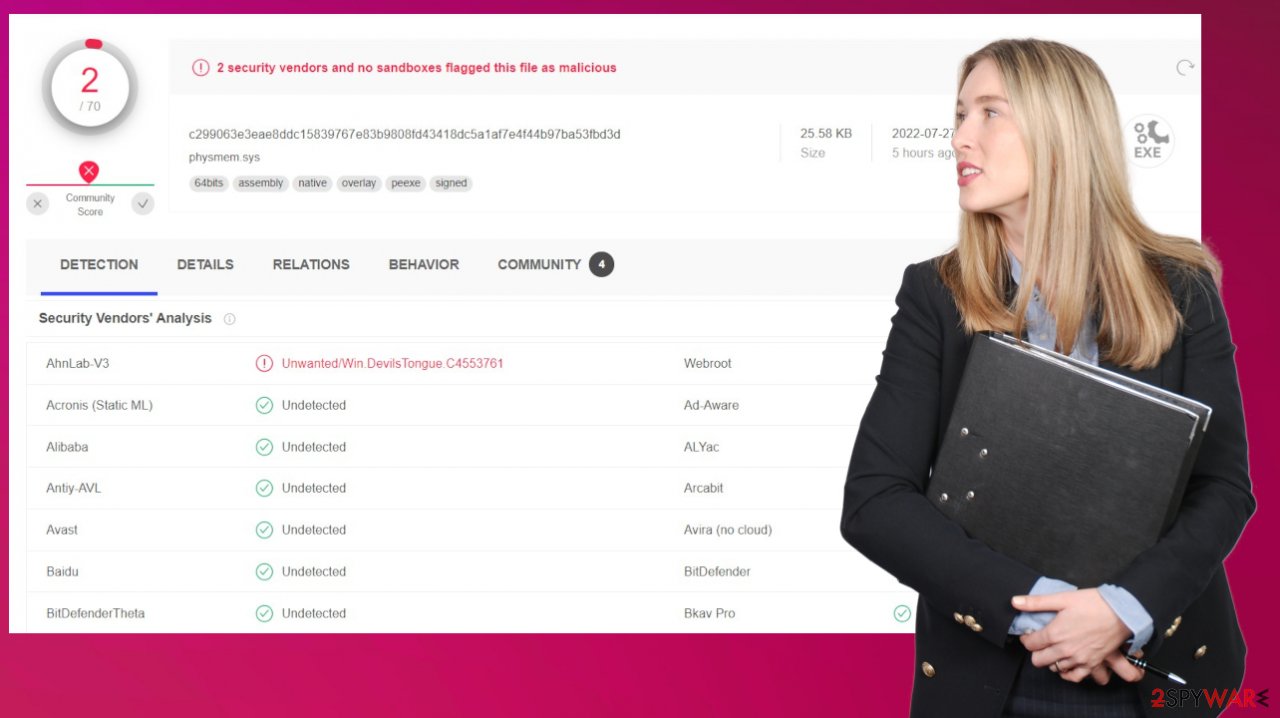
DevilsTongue malware is a virus that is written in C and C++ programming languages

DevilsTongue malware was discovered by researchers, and it is reported as a cyber threat that has been targeting various victims online related to politics and activism. The threat is used by malicious actors that rely on selling malware and hacking tools for the purpose of cyber warfare.[1] This is the piece used by the cybercriminals group SOURGUM, which is based in Israel and targets politicians, embassy workers, academics, human rights activists, journalists, and political dissidents.
The malware is a complex piece that is capable of evading anti-malware detections and has various codes helping with anti-analysis techniques. The threat is using various exploits to abuse known system flaws like CVE-2021-31979 and CVE-2021-33771, which helps to spread the DevilsTongue malware further.
The infection is altering the Windows registry and other parts of the machine to carry out other attacks and run commands, so the infection can download various files from the affected machine and exfiltrate any valuable details or data. The threat can gather internet cookies and use them later on, to browse the web as the user and gather more personal details from social networking sites and email services. DevilsTongue malware focuses on data from Facebook, Twitter, Gmail, Mail.ru, and Yahoo.
Summary
The infection can perform various attacks since it has been known for a while, and these newer releases are improved. The trojan can access various data that gets collected and shared with the malicious actor. Devils Tongue virus can even be involved in highly confidential information exfiltration, so it can create major consequences.
| Name | DevilsTongue virus |
|---|---|
| Type | Information stealer malware, spyware |
| Category | Trojans |
| Damage | Stolen data like passwords or banking details can be used for identity theft |
| Distribution | Files with the payload can be provided via infected email attachments, malicious online sits, social engineering |
| Symptoms | Trojans show little to no symptoms while running on the machine, and these threats can run various processes while the infection is gathering data or infiltrating the machine with other infections |
| Elimination | Try to remove the infection with tools like antivirus apps or system security tools |
| Repair | Data gets seriously damaged, so you need to recover issues with tools like FortectIntego |
DevilsTongue malware gathers users' credentials from web browsers and downloads conversations from SIgnal messaging applications, so the threat creates major privacy issues, financial losses, and identity theft. The malware is designed for these sophisticated cyberattacks, and criminals behind it can be geopolitically motivated.
The spreading of these trojans is a silent issue
These threats need to be properly removed from the machine because prolonged existence of the infection can lead to major issues with the machine. DevilsTongue malware relies on zero-day flaw exploitation and other silent infiltration methods. Experts[2] always warn that the stability and security of the machine is crucial for cyber attack prevention.
These trojans and malware, viruses that run on the machine, can spread around using other malware as vectors or act as the deployment tools for ransomware themselves. It is common to get trojans or malware installed on the machine when there are infections on sites you visit without knowing.
Not paying attention to details can lead to these infections and infiltrations of the DevilsTongue malware. These criminals behind the infection can use phishing and social engineering methods to spread the cyber threat and target particular people or companies. A malicious app can be spread as an email attachment too.
Infections can be avoided if you make sure to ignore any shady messages. Emails can be convincing and disguised as important alerts or common messages, so people do not think twice about opening the infected file attachment. However, the data from those notifications and emails can have DevilsTongue trojan payloads that get launched immediately after the download.
Removing the infection is crucial
DevilsTongue malware can damage the machine further than gathering details about the user. Infection creators can easily infiltrate the system with other infections, and these trojans often act as vectors for the ransomware virus deployment. The threat is a major infection, and it needs to be removed properly.
Trojans are designed to infiltrate machines and remain silent, so you cannot point to a particular time when the infection found its way to the computer. However, you can remove the threat as soon as possible. That is helpful with anti-malware tools since DevilsTongue malware can be detected using those.
You need to eliminate all possible malware infections, and scanning the machine with legitimate antivirus tools can provide the best results. The threat is targeting particular devices that belong to people involved in political or academic, humanitarian work, so these machines might not be protected properly.
So AV tools are crucial in the DevilsTongue malware termination procedure. Since the infection can evade detection and remain not found by these tools even, Safe Mode and other programs on the machine can help with the terminations. You need to follow the guide below that shows how you can recover the machine after the infiltration.
SpyHunter 5Combo Cleaner or Malwarebytes can detect[3] and eliminate all virus-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the DevilsTongue malware removal process.
Getting rid of DevilsTongue malware. Follow these steps
Access Safe Mode to remove malware from Windows
If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions, and perform a full system scan to eradicate malware and all its malicious components.
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Identify ransomware affecting your PC
Modern-day ransomware had its roots in the early 2010s when cybercriminals began to understand the potential it has for money extortion. Over the years, thousands of new ransomware strains have been developed and spread all over the world, infecting regular consumers, small businesses, and high-profile organizations.
Because of the lucrative nature of ransomware, cybercriminals are creating new ransomware versions in the hopes of establishing themselves in this illegal business. Ransomware often uses different extensions, ransom notes, and other attributes that it can be identified by. However, quite often, this information can overlap or simply not be available, so identifying the threat might be difficult.
In order to deal with ransomware infection effectively, you must first identify it. Here are a few examples of how to determine the precise ransomware you are dealing with:
File extension
Almost all modern ransomware viruses are using extensions that are appended at the end of the original filenames. However, this is not a rule, and in some cases, cybercriminals change the name by replacing it with randomly generated characters, add the marker before the file name, or do not visually change the name of the file at all.
Here you can see an example of a unique extension .hhmgzyl that belongs to the Snatch ransomware family:
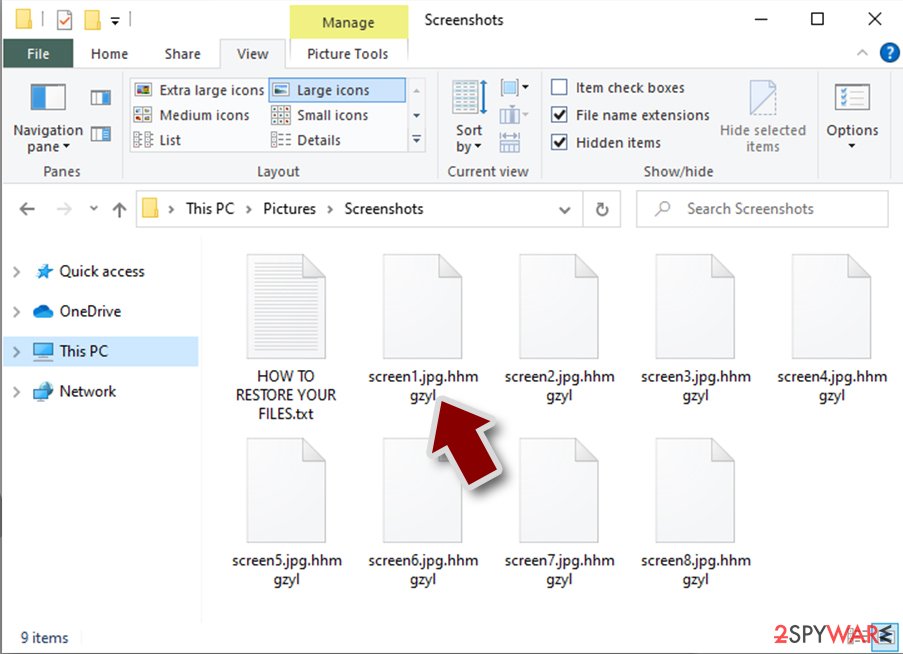
If your files are appended with .exe, .locked, .encrypted, or other broadly-used extensions that are difficult to identify, proceed with the next step.
Ransom note
Ransomware family might sometimes be identified by the ransom note it uses. In most cases, cybercriminals create a simple .txt file and place it on users' desktops or other places that are easily reachable (typically, where the encrypted data is located). Other times, a pop-up window can also be used, which is launched as soon as the encryption is complete. In some cases, threat actors name the ransomware within this note:
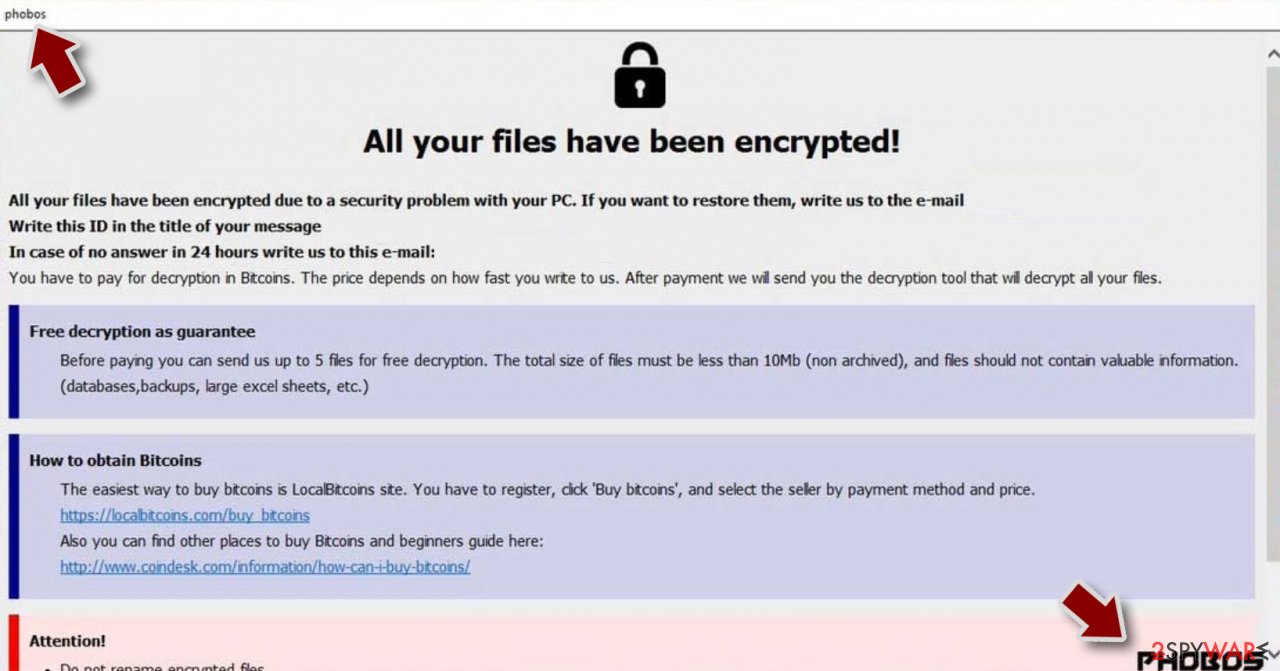
In some cases, it is possible to identify ransomware by its ransom note name, but they are typically very generic (e.g., FILES ENCRYPTED.txt, _readme.txt) and used by different cybercriminals groups.
Free ID Ransomware service
ID Ransomware is a free service that can easily let users identify the precise malware they are dealing with. All you have to do is upload the ransom note that can be found on the desktop and within folders where encrypted files are located and the sample of an encrypted file.
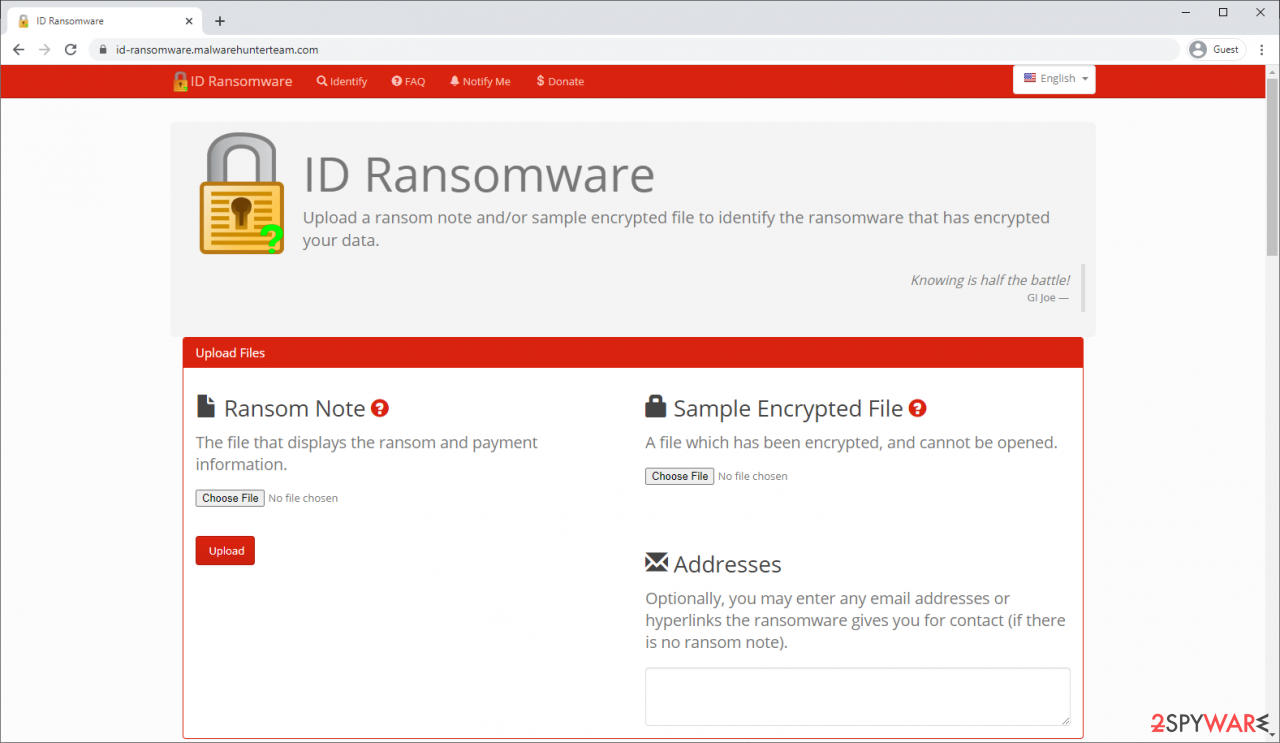
Soon after uploading the required files, you will be provided with all the relevant information, including what family ransomware belongs to and whether or not it is possible to decrypt files.
If none of the above helped you to identify which ransomware you are dealing with, you should use keywords (extension, contact email, ransom note contents, crypto-wallet address, etc.) to find the information on the internet.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

How to prevent from getting trojans
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Cyberwarfare. Wikipedia. The free encyclopedia.
- ^ AVirus. Avirus. Virus removal guides.
- ^ Virus detection rates. VirusTotal. Online malware scanner.

















