Encryptedsearch.org (Free Instructions) - Virus Removal Guide
Encryptedsearch.org Removal Guide
What is Encryptedsearch.org?
Encryptedsearch.org – a privacy-offering engine that can easily be replaced by a legitimate search provider such as Google
Encryptedsearch.org is marked as a browser hijacker[1] that offers to browse the web in a safer way. Even though the app claims to encrypt search results and delete browsing history after 30-minute sessions, you can also successfully employ a legitimate web browser such as Google and search privately via the Incognito mode. However, some users quickly get attracted to the offered features and install Encrypted Search extension on their web browsers such as Google Chrome, Mozilla Firefox, Internet Explorer, Microsoft Edge, or Safari.
Encryptedsearch.org is available on the official Google Chrome web store,[2] however, this does not add a better reputation as the product is still mostly bundled with other packages of software from secondary downloading pages such as softonic.com, download.com, and cnet.com. When the PUP ends up on the targeted web browser, it starts modifying the default search provider, homepage, and new tab URL to its own. Afterward, users are forced to use Encrypted Search services unless they get rid of the browser hijacker as soon as they spot that their search engine has turned to https://www.encryptedsearch.org/.
| Name | Encryptedsearch.org |
|---|---|
| Type | Browser hijacker/potentially unwanted program |
| Danger level | Low. Does not act as dangerous malware but still can cause indirect damage by rerouting the user to a potentially malicious website or swindling some money/personal information through ads that include various questionable offers |
| Feature | The developers of this browser hijacker claim to offer a completely private search engine by encrypting search query results and deleting web browsing experience after 30 minutes of online activity. However, this type of feature is provided as a way to attract a bigger number of users |
| Target(s) | You can receive the Encrypted Search extension and experience search engine, homepage, and new tab URL changes on any type of web browser app such as Google Chrome, Mozilla Firefox, Internet Explorer, Safari, and Microsoft Edge |
| Activities | The suspicious app will perform unwanted changes on your web browser's search engine, homepage, and new tab URL. Additionally, you can start receiving intrusive redirects to affiliate domains and start experiencing intense advertising during browser sessions, get your browsing-related information collected, receive other potentially unwanted programs on your PC |
| Spreading | This questionable product can be downloaded from the Google Chrome web store, however, it is the most possible that you will receive such an app through bundled products that come from secondary websites such as cnet.com, download.com, and softonic.com |
| Elimination | If you have been dealing with this browser hijacker lately, you should get rid of it from your computer system and web browsers. For proper elimination, we recommend employing reliable antimalware software or using the manual step-by-step guidelines that have been added to the end of this article |
| Fix software | If you have discovered any compromisation in the computer system after the browser hijacker attack, you can try recovering all of the affected areas with the help of a tool such as FortectIntego |
Encryptedsearch.org virus claims that it does not collect any personally-identifiable information about the user, including the IP address. However, the browser hijacker can still spy on data such as search queries made, hyperlinks and adverts accessed, the most popular offers searched, and so on. The developers might not admit this fact but they can end up sharing the gathered data with other parties. However, the Privacy Policy claims that some information regarding the Encrypted Search extension is stored by the app:
When using a browser extension built by Encrypted Search, we collect the extension version, browser user agent, url referrer, extension platform identifier, and a setting for if remote searches should be encrypted. As part of encryption within the extension, the encryption version date, encryption key, and an expiring encryption search token are stored locally
Encryptedsearch.org can engage in advertising activities also. The app can start loading various sales offers and deals straight on your search page in order to catch your eye. You might also be provided with suggestions to subscribe to some types of monthly services, win non-existing prizes, and participate in surveys. Whatever you do, do not provide complete strangers with your financial information or personal details, including contacts as you can get yourself in big trouble.
If some hackers decide to abuse Encryptedsearch.org and its functionality, your personally-identifiable information can fall in the hands of complete criminals. This way you can get money swindled straight from your bank account, experience identity theft, etc. If you reveal your email address, mobile phone number, or other contact information, you might start receiving unwanted offers and deals straight in your email box or find rogue numbers dialing you constantly.
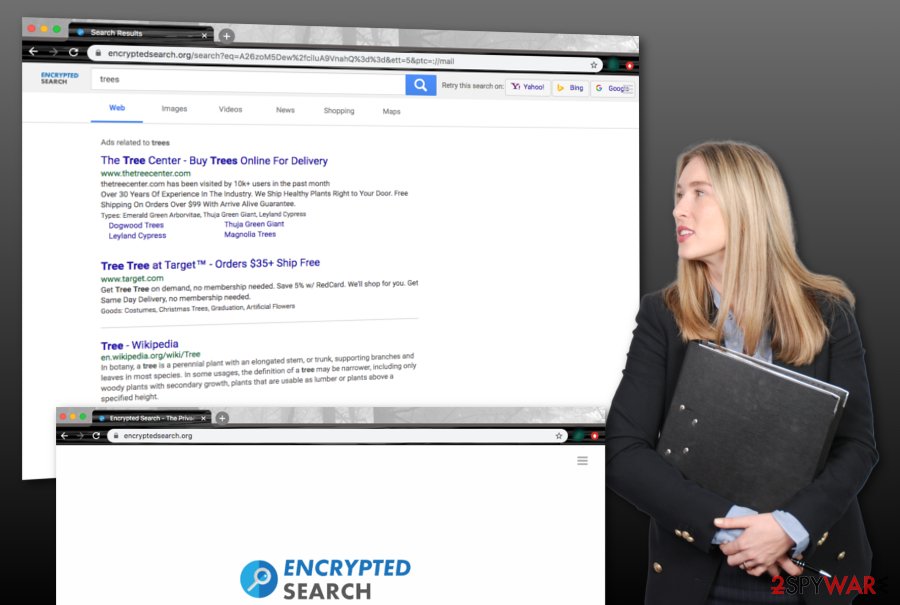
Furthermore, Encrypted Search can initiate redirecting activities to affiliate domains. The browser hijacker can start rerouting you to developer-sponsored places that are filled with more annoying ads. However, here comes a big risk of catching a dangerous malware infection if you land on a potentially malicious website. Your computer system can easily get infected with a ransomware virus, Trojan horse, spyware and suffer from severe unrepairable machine damage.
Even though Encryptedsearch.org is not a dangerous malware form such as ransomware or a Trojan virus, it still can bring indirect damage to the computer system and its components and redirecting is only one way how the browser hijacker does it. Furthermore, some cybercriminals can find PUPs as handy intermediaries when wanting to install a piece of malware to a computer system. This way you can receive a malicious infection completely unexpectedly.
However, browser hijackers can even bring other potentially unwanted programs to the computer system, so you might see more than one suspicious process running in the Windows Task Manager section. If you have been bothered by a lot of intrusive activities lately, you have to remove Encryptedsearch.org together with all of the questionable components that have been causing misunderstandings lately. For compromisation cleaning, try using FortectIntego.
If you want to speed up the Encryptedsearch.org removal and make sure that every suspicious product has been successfully terminated from your computer system, you should get rid of the browser hijacker with the help of antimalware software. However, if you do not mind spending some time reviewing instructions and cleaning both your OS and web browser, you can check out the manual step-by-step guidelines that have been added to the end of this article.
Browser hijackers get delivered by bundled software
Even though a lot of third-party products have their own downloading sources or can even be received from official e-shopping platforms such as Google Chrome web store, AppStore, and similar places, PUPs are most likely to appear on the user's computer system by employing deceptive techniques and taking advantage of the software bundling technique that includes bringing the suspicious product into the computer system as an additional component.
Most of the time, you can download bundled software[3] from third-party downloading websites such as cnet.com, softonic.com, or download.com. The browser hijacker or another type of PUP usually settles on computer systems that have the Recommended or Quick installation settings opted as default. If you also have the same configuration, you have to change it to the Custom or Advanced option that allows deselecting all the unwanted objects to prevent them from downloading on the computer.
However, browser hijackers are capable of distributing by employing other methods also. For example, the potentially unwanted program can come injected into an unsecured hyperlink or advertisement, pretend to be a fake software update, etc. According to Virusai.lt specialists,[4] if the user clicks on such content while browsing the Internet, there is a big chance that he will execute the downloading process of the browser-hijacking application.
If you want to keep yourself protected from such cyber threats, you should avoid entering websites that are marked as deceptive or unsafe to proceed with. Furthermore, if you have been provided with a prompt to update your Flash Player or another program, do not upgrade your software before checking the official update releases. Also, you should purchase a strong antimalware product that includes the safe browsing function.
Accomplish Encryptedsearch.org removal within a few steps
There are two ways in which you can remove Encryptedsearch.org from your Windows or Mac computer system. First of all, you have to measure your own skills and capabilities to know if you are able to remove Encryptedsearch.org on your own. If you find yourself an advanced user, you can definitely continue with the manual elimination option that we have provided at the end of this article and is displayed to help you to clean both your operating system and web browser apps.
However, if you think that you will be struggling with the Encryptedsearch.org removal process, you should employ reliable antimalware software that will help you to get rid of the cyber threat within a few clicks. Download such type of product and save some time by letting it accomplish the task for you. However, do not forget to refresh your web browsers such as Chrome, Firefox, Explorer, Safari, and Edge as they are likely filled with rogue components too.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Encryptedsearch.org. Follow these steps
Uninstall from Windows
To terminate the browser hijacker from your Windows operating system and get rid of all the additional components that were added by the PUP, apply the following guiding steps
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
To diminish all of the suspicious changes that were added to Mozilla Firefox and terminate the browser hijacker itself, try using the below-provided instructions
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
To bring Google Chrome back to its previous state and eliminate the potentially unwanted program, you should apply the following instructing steps
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Encryptedsearch.org registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What are browser hijackers?. Norton. Internet Security.
- ^ Chrome Web Store. Wikipedia. The free encyclopedia.
- ^ Bundled Software. Techopedia. Tech terms and definitions.
- ^ SAUGUMO IR VIRUSŲ NAUJIENOS. Virusai.lt. Security and spyware news.























