Magniber ransomware / virus (Removal Guide) - updated Aug 2018
Magniber virus Removal Guide
What is Magniber ransomware virus?
Magniber – a dangerous ransomware virus which returns with the stronger version to infect Korean PC users

Magniber is dangerous crypto-virus that first showed up in October 2017. Its name originates from two words: Magnitude (ransomware was spread using Magnitude exploit kit) and Cerber. Malware uses AES-128 to lock up data and ads file extension consisting of 5 to 9 letters. It then demands a ransom of 0.2 BTC, which later doubles to 0.4 BTC. Although South Korean cybersecurity researchers managed to create a decryptor for most variants of Magniber virus, it came back stronger in July 2018 with updated obfuscation techniques. While it was targeting Korean users exclusively, its spectrum has been expanded with the ability to encrypt files of Chinese and Malaysian victims. The ransomware adds .dyaaghemy file extension and, at the time of the writing, is not decryptable.
| SUMMARY | |
| Name | Magniber ransowmare |
|---|---|
| Type | Crypto-virus |
| Associated with | Cerber virus |
| Exploit used | Magnitude exploit kit |
| Demanded ransom | 0.2 BTC; 0.4BTC in five days |
| Extensions used |
.fprgbk; .ihsdj; .kgpvwnr; .vbdrj; .skvtb; .vpgvlkb; .dlenggrl; .dxjay; .fbuvkngy; .xhspythxn; .demffue; .mftzmxqo; .qmdjtc; .wmfxdqz; .ndpyhss, .dyaaghemy |
| Symtoms | Encrypted files |
| Distribution | CVE-2016-0189 vulnerability in Internet Explorer |
| Elimination | Download and install FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. Reboot PC in safe mode |
| Decryption | Available here (newest versions)and here |
Magniber cyber threat was noticed spreading via Magnitude exploit kit. This exploit kit has been used by Cerber virus. However, it’s not the only similarity to the infamous ransomware.[1].
Originally, the crypto-virus targeted South Korean computer users only. However, it is now been spotted in other Asian countries – China and Malaysia. Interestingly, the malware terminates itself (by deleting its ping.exe[2] executable file) if it detects other than the Korean, Chinese or Malaysian language.

The malware is using AES cipher. Before the end of March 2018, it was almost impossible to decrypt files without AES key. However, South Korean cybersecurity experts managed to crack the code for most of the Magniber ransomware versions.
This fact sparks suspicion that North Korean hackers might have created the malware. Such an assumption is not baseless taking into account the cyber capabilities of this country[3] However, this theory still needs evidence.
Magniber ransomware is designed to encrypt files and demand to pay the ransom. Malware has been updated several times and the latest updates were spotted in June 2018.[4] This version adds .ndpyhss file extension and drops a ransom note README.txt.
Each of the new variant appends different file extension. Currently, malware locks files with these suffixes:
- .fprgbk;
- .ihsdj;
- .kgpvwnr;
- .vbdrj[5];
- .skvtb;
- .vpgvlkb;
- .dlenggrl;
- .dxjay;
- .fbuvkngy;
- .xhspythxn;
- .demffue;
- .mftzmxqo;
- .qmdjtc;
- .wmfxdqz;
- .ndpyhss
After data encryption, malware offers to buy My Decryptor to restore corrupted files. At the moment, it costs 0.2 bitcoins ($1140). It will double to 0.4 after five days. Do not remit the payment as the malware is decryptable. Instead, concentrate on Magniber removal. FortectIntego or Malwarebytes is a reliable security software that can help in a quick malware elimination.
Previous attempts to crack the malicious code
Simone “evilsocket” Margaritelli, the researcher for mobile security company Zimperium, managed to create a decryption tool that might help to restore files after the Magniber attack. However, in order to use it, victims have to know the AES key.
According to the researcher, the decryptor should work if victims were infected from a non-Korean IP address or they cannot connect to Command & Control (C&C) server. These people should know the hardcoded key and IV which should be included in the ransomware’s code.
A South Korea-based security expert team released new decryptors
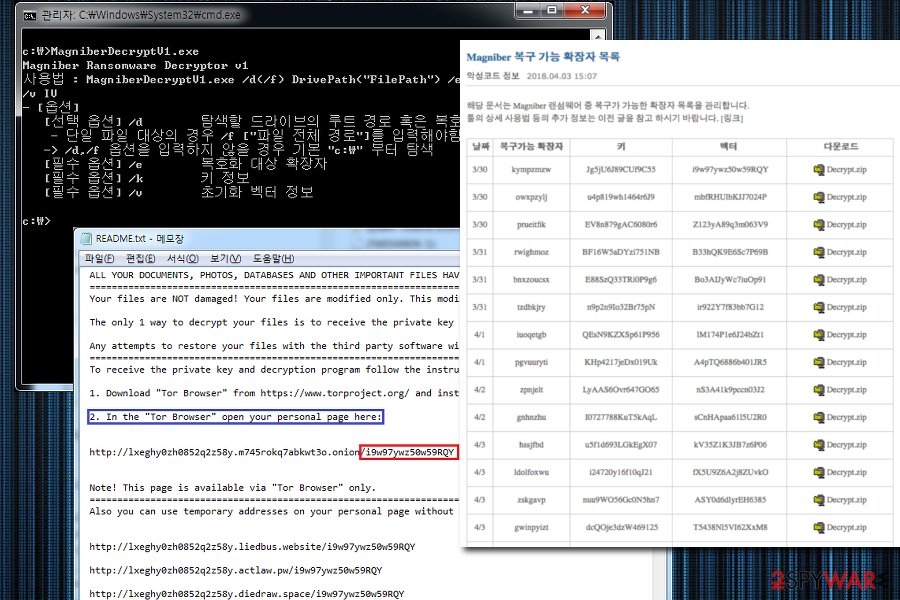
At the end of March 2018, security researchers from AhnLab released multiple decryptors for different types of Magniber virus. The recovery tool functions based on an encryption bug that was left out by hackers.
Below you can see the table showing which versions of Magniber ransomware can be now decrypted:
| Decrypter release date | Recoverable file extension | Victim Key | Magniber payment site vector | Download Link |
| 3/30 | kympzmzw | Jg5jU6J89CUf9C55 | i9w97ywz50w59RQY | MagniberDecrypt.zip |
| 3/30 | owxpzylj | u4p819wh1464r6J9 | mbfRHUlbKJJ7024P | MagniberDecrypt.zip |
| 3/30 | prueitfik | EV8n879gAC6080r6 | Z123yA89q3m063V9 | MagniberDecrypt.zip |
| 3/31 | rwighmoz | BF16W5aDYzi751NB | B33hQK9E6Sc7P69B | MagniberDecrypt.zip |
| 3/31 | bnxzoucsx | E88SzQ33TRi0P9g6 | Bo3AIJyWc7iuOp91 | MagniberDecrypt.zip |
| 3/31 | tzdbkjry | n9p2n9Io32Br75pN | ir922Y7f83bb7G12 | MagniberDecrypt.zip |
| 4/1 | iuoqetgb | QEsN9KZXSp61P956 | lM174P1e6J24bZt1 | MagniberDecrypt.zip |
| 4/1 | pgvuuryti | KHp4217jeDx019Uk | A4pTQ6886b401JR5 | MagniberDecrypt.zip |
| 4/2 | zpnjelt | LyAAS6Ovr647GO65 | nS3A41k9pccn03J2 | MagniberDecrypt.zip |
| 4/2 | gnhnzhu | I0727788KuT5kAqL | sCnHApaa61l5U2R0 | MagniberDecrypt.zip |
| 4/3 | hssjfbd | u5f1d693LGkEgX07 | kV35Z1K3JB7z6P06 | MagniberDecrypt.zip |
| 4/3 | ldolfoxwu | i24720y16f10qJ21 | fX5U9Z6A2j8ZUvkO | MagniberDecrypt.zip |
| 4/3 | zskgavp | nuu9WO56Gc0N5hn7 | ASY0d6dlyrEH6385 | MagniberDecrypt.zip |
| 4/3 | gwinpyizt | dcQOje3dzW469125 | T5438Nl5VI62XxM8 | MagniberDecrypt.zip |
Security experts seem to release new versions in short intervals. Thus, this information might be outdated really soon. To check for the latest releases, check AhnLab's website.
Cerber and Magniber analogies
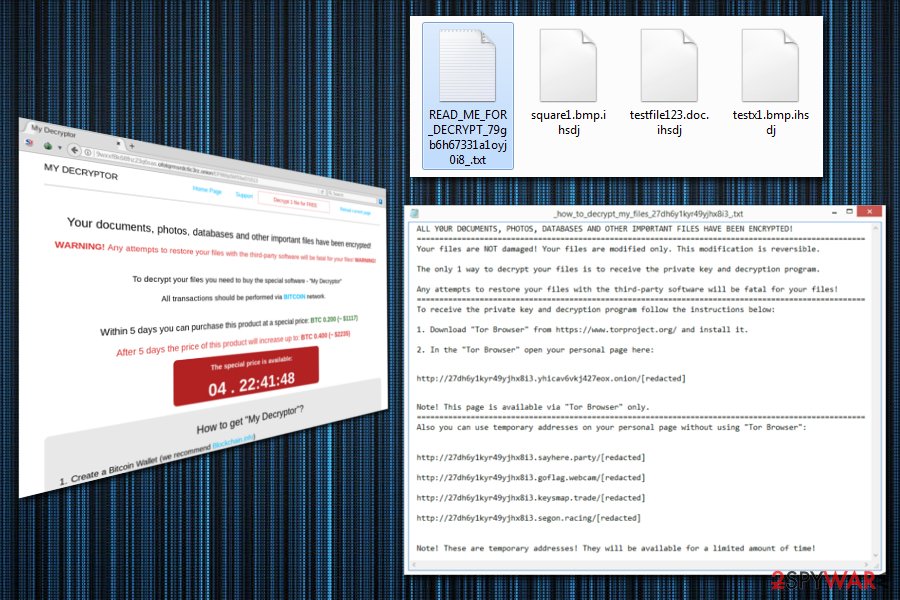
Though it uses the same payment site, its source code seems to be much less elaborate than Cerber‘s. Therefore, it gives hope that the virus can be decrypted[6]. After infiltrating the system, the malware encodes data and appends either .ihsdj or .kgpvwnr extension. Furthermore, it will open the ransom file called as READ_ME_FOR_DECRYPT_[id].txt file.
It contains the typical text explaining that all documents, photos, and databases have been encrypted. The very manner of the written text slightly differs, though, in contrast to the original Cerber’s note.
Furthermore, Magniber virus manifests a peculiar feature. Usually, ransomware threats assign the infected devices user’s ID. Furthermore, affected users have to enter the code into an indicated Tor website in order to proceed with data decryption.
On the other hand, Magniber crypto-malware directs users to a subdomain, containing the victim’s ID, of the payment site. It is divided into four sections: Homepage, Support, Decrypt 1 file for FREE and Reload content page.
The crypto-virus also evades certain directories when looking for encryptable files. As common for ransomware, it skips Program Files, Recycle Bin, local settings, and certain AppData subfolders. Furthermore, the malware has the ability to change payment bitcoin address if it identifies an URL with a different victim’s ID.
Magniber ransomware came back stronger in July 2018
Security researchers from Malwarebytes Labs published[7] a detailed technical report of a new sample of Magniber virus. According to experts, the ransomware has undergone some tremendous changes during the past year and came back even more powerful.
The first significant change in the code of the virus is the capabilities of the infection. The new Magniber now targets users outside of South Korea, i.e., the virus deploys its payload whenever it detects South Korean, Chinese (Macau, China, Singapore) or Malay (Malaysia, Brunei) keyboard languages. Thus, researchers speculate that it will expand even more, and users around the world could be affected by this threat.
The new Magniber version is utilizing Magnitude exploit kit makes use of Internet Explorer zero-day vulnerability (CVE-2018-8174), which was first discovered in April this year, and patched next month. Therefore, users who are updating their browsers on time should be safe from the new Magniber virus attack. Furthermore, the virus is rather unsuccessful when it comes to other modern day browsers, such as Google Chrome or Mozilla Firefox.
Magniber ransomware no longer relies on the Command & Control server or the hardcoded key, as well as uses improved obfuscation methods. The enhanced version of the virus encrypts files by adding .dyaaghemy appendix, and as of now, this variant of Magniber is not decryptable.

Magnitude exploit kit was used to spread crypto-virus
As previously mentioned, at the moment, the malware is spread with the assistance of Magnitude exploit kit. It targets a particular CVE-2016-0189 vulnerability in Internet Explorer[8]. This flaw has been fixed already. Thus, if you are using the browser, make sure it is updated.
If the exploit kit detects the vulnerability in a user’s browser, the kit directs them to a fraudulent website which is customized according to a victim geolocation. Such sites are likely to include a link. Activating it would download the malware and begin Magniber hijack.
At the moment, the malware only targets South Korea, but soon it may extend its activities in other East Asian countries, for instance, Japanese[9] sites. Thus, make a rush to remove Magniber.
Eliminate Magniber virus and then proceed with the file recovery
Though the malware tries to persuade that it is the latest Cerber version, differences in the operation mode and source code trigger speculations whether the developers are the same. Though security experts state that the malware is Cerber in fact, less elaborate source code contradicts such statement.
In any case, the malware elimination should be your top priority. Do not waste time on meddling with the virus manually. Install a security tool, for instance, FortectIntego or SpyHunter 5Combo Cleaner, to remove Magniber virus. The virus might prevent you from starting security software. In that case, boot the system in Safe Mode and launch the program. Below instructions display further instructions on how to do it. Only when Magniber removal is complete, proceed to data recovery.
Getting rid of Magniber virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Magniber using System Restore
If, by any chance, you cannot boot the device into Safe Mode, perform System Restore. It should grant you access to the security tool. Likewise, you will be able to remove Magniber virus.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Magniber. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Magniber from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.The official Magniber decryptor can help to restore file if you know the AES key. Otherwise, you will not be able to take advantage of this tool. However, you can try alternative recovery methods.
If your files are encrypted by Magniber, you can use several methods to restore them:
Data Recovery Pro method
Note that backing your files is crucial especially at times of ransomware infiltration. If you did not create them, try this program. It might help you recover some files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Magniber ransomware;
- Restore them.
The usefulness of Shadow Explorer
This utility creates the copies of original files based on shadow volume copies, which are automatically generated by the operating system. There is no information whether Magniber crypto-malware deletes them in advance. However, regarding Cerber's feature to delete them, the former virus might do so in the future as well.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Magniber decryptors
As we already mentioned, the South Korean security team managed to create several decryptors for Magniber virus. You can find the full list above, or download them from the official website.
In case decryptors created by AhnLab do not work for you, you can try the older version, but it only helps to decrypt files encoded by the hardcoded version of the ransomware. It means you have to know the key and IV that are necessary in order to use the decryption software. You can download a decryptor here.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Magniber and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Kafeine. Goodbye Cerber Ransomware ? Last known (to me) infection vector (Magnitude) for Cerber switched to Magniber . Twitter. Online source for news and communication.
- ^ Magniber ransomware: exclusively for South Koreans. MalwareBytesLabs. The Security Blog from Malwarebytes.
- ^ SamKIm. How North Korea Built An Army of Hackers: Q&A. Bloomberg. Technology section .
- ^ Michael Gillespie. Magniber ransomware. Twitter. Social network.
- ^ Michael Gillespie. Seeing some fresh domains + exts ".vbdrj" + ".fprgbk". Twitter. Online source for communications and news.
- ^ Lawrence Abrams. Goodbye Cerber? Hello Magniber Ransomware!. BleepingComputer. News, reviews, and tech support.
- ^ Magniber ransomware improves, expands within Asia . Malwarebytes Labs. Cybersecurity researchers.
- ^ Joseph C Chen. Magnitude Exploit Kit Now Targeting South Korea With Magniber Ransomware. TrendMicro. Security News Direct from Threat Defense Experts .
- ^ Eliminate computer threats. Uirusu. Security news in Japanese.







