Gero ransomware (Free Guide) - updated Sep 2019
Gero virus Removal Guide
What is Gero ransomware?
Gero cryptovirus is the ransomware that belongs to a DJVU virus family but has the updated encryption method
The only solution for this threat – total virus termination since this Djvu ransomware strain cannot be eliminated using other methods. Then, you can try to employ other tools and features that your device has, or rely on paid services offered by cybersecurity researchers. Unfortunately, this is a pricy pleasure, so keep those encrypted files and wait for the newer version of decryption tool that could work for Gero files virus.
When Gero ransomware virus infects the system, it starts the encryption and file marking process immediately. Once that is done, files get .gero file markers and cannot be opened anymore. As _readme.txt – a ransom note states, the victim needs to pay as soon as possible to get at least an opportunity to get their data back. However, we never recommend paying since it can lead to more damage than positive results.[1] You should check the article to find a more reliable method of decryption or data recovery.
| Name | Gero ransomware |
|---|---|
| Type | Cryptovirus that encrypts files with the aim to get profit from people |
| File extension | .gero is the appendix that marks every encrypted document, photo, video file or archive |
| contact Email addresses | gorentos@bitmessage.ch, gerentoshelp@firemail.cc |
| Family | DJVU/STOP virus |
| Additional danger | Virus leaves behind a software module that steal personal data, installs direct AZORult malware payload, modifies host files and can steal data stored on the machine or web browser |
| Ransom amount | $980 is the initial demand, but criminals offer to lower the price to $490. This is the method that should fake the trust between virus developers and victims |
| Ransom note | _readme.txt is the file that delivers ransom demanding message with all the payment instructions and contact details |
| Alters files in directories |
|
| Decryptable? | This version came out with different encryption method and cannot be decrypted with STOP decrypter. However, there are some other options for the particular version that uses offline keys for encoding. (Direct link to decryptor additional instructions can be found here) |
| Elimination | Install anti-malware and remove Gero ransomware. You need a professional anti-malware program to get rid of the malware, as manual termination is hardly possible for regular users |
| recovery | If you suffer from system slowdowns, crashes and other unwanted behaviors after malware infection, use FortectIntego to repair it |
Gero ransomware is the threat that affects your photos, videos, documents, and even archives because it alters common types of data found on the machine. This encryption process starts immediately after the initial system infiltration because the virus is developed to scan the device quickly.
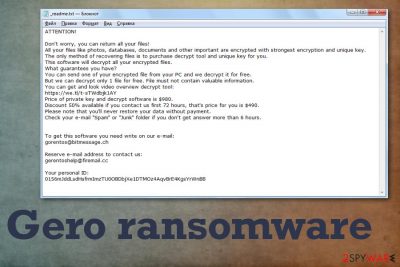
Gero ransomware delivers the following message for each victim, where criminals explain all the possibilities for the person affected:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-o7ClqIH7RS
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gorentos2@firemail.ccOur Telegram account:
@datarestore
Mark Data RestoreYour personal ID:
The typical ransom demand message is not changed since the beginning of Djvu ransomware attacks, so the message is the same for other variants on the same family as Gero ransomware. The principle of this threat is the same – encrypting personal files and offer to decrypt data for a hefty payment in cryptocurrency.
Although the message from Gero ransomware developers seem calm and may create trust, you need to remember that malicious actors who create such treats are self-centered criminals and have no mercy form their victims. Sometimes cryptovirus may be designed to restrain from third-world countries. This is the only merciful behavior you can expect from malicious threat creators. 
A deeper look into Gero ransomware decryption options
Gero file-locking virus is 156th version in the family that started its malicious attacks back in November 2018. However, up until this .gero version, all the files were decryptable with STOP virus decryption tool. In this case, you need to get rid of all the parts of the virus and then rely on data recovery tools or file backups on external devices.
The encryption method got altered and never variants rely on a proper asymmetric algorithm that is not relying on offline keys that got used before. However, when offline keys are used, other decryption possibilities can work. When personal IDs end in t1 it is possible to recover files using the tool listed here.
However, you still need to get your files back even though decryption is not possible. You cannot attempt any data restoring until you perform Gero ransomware removal on the machine. Get anti-malware tool and then run the full system scan to eliminate all components of the ransomware. We also recommend running a scan with FortectIntego to eliminate virus damage.
DR.Web researcher team also offers the service called Rescue Pack that can decrypt various file formats. However, not all of them get recovered and this service costs 150 euro per victim. You should consider trying this if you are desperate to get encrypted files back.
Since Gero ransomware decryption is a sensitive topic, you should save those encoded files and wait for the particular software capable of recovering those files. Try to check for tools here from time to time:
- https://www.nomoreransom.org/en/decryption-tools.html
- https://www.emsisoft.com/ransomware-decryption-tools/
- https://noransom.kaspersky.com/
- https://www.avast.com/ransomware-decryption-tools
- https://www.quickheal.com/free-ransomware-decryption-tool/
- https://www.mcafee.com/enterprise/en-us/downloads/free-tools/ransomware-decryption.html
- https://success.trendmicro.com/solution/1114221-downloading-and-using-the-trend-micro-ransomware-file-decryptor
This is STOP/Djvu ransomware version, but the more recent versions .gero and .hese came out not decryptable. So you need to remove Gero ransomware and then attempt to restore encrypted files using data backups. Do not contact the criminals yourself, as they may attempt to take advantage of you or continue to extort you.
Djvu cryptovirus family is known as the one that installs the Azorult trojan besides the encryption process.[2] This malware allows stealing passwords from the victim. So it is crucial to change all passwords, as experts[3] note you need to do so for your computer and online services. However, do so when your computer is clean, and Gero ransomware is not running in the background. 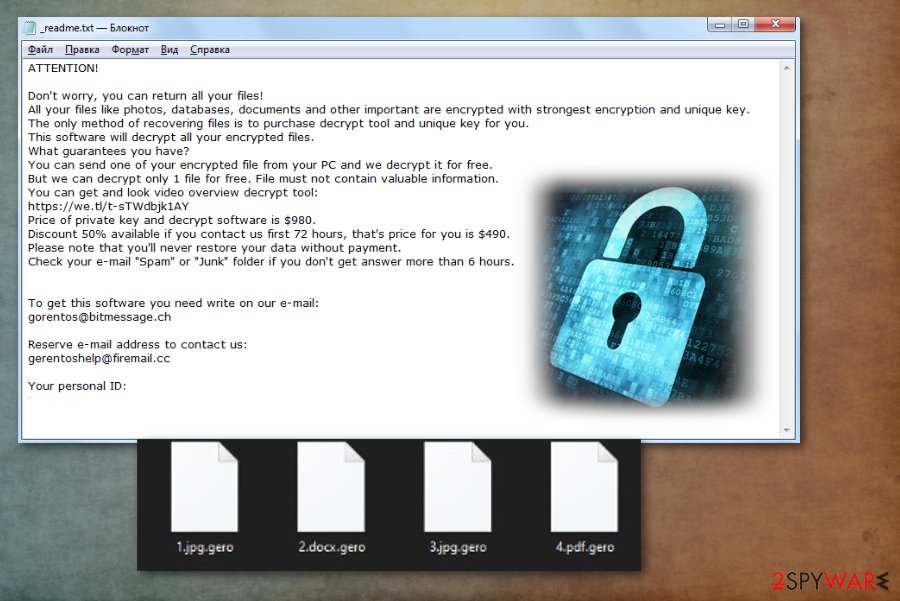
Infected files deliver the direct malicious script
Ransomware is one of the many threats that distributes with the help of other malware and also can spread threats during its own infiltration. This threat can come alongside trojans, worms, or malware, but the main spreading technique for all of these cyber intruders remain the same – infected email attachments filled with macro viruses.
Criminals spam out emails with forged subject lines, sender information and trick people into believing that the notification is delivered from the legitimate company like FedEx, DHL, and so on. Unfortunately, people fell for such tricks and opens those emails. File attachments when opened delivers malicious scripts and leads to ransomware infections.
Avoid infections by:
- deleting received emails if not expected;
- pay close attention to the spam email box and its contents;
- avoid downloading and opening files attached to emails;
- check for typos and hyperlinks before opening anything from the email.
Additional facts about the particular virus family include certain methods of spreading. When the newest versions got released, many users complained about the infection online, searching for particular decryption options. Also, those victims revealed that main vector used by criminals includes software cracks and details like serial game numbers, licensed keys for legitimate OSs and other cheats. Avoid such illegal activities, since these are also used to deliver malware.
Eliminate Gero ransomware virus with robust anti-malware tools
You need to rely on professional tools that are required for Gero ransomware removal because this threat is more than dangerous when it can install AZORult malware and other info-stealers on the machine. The encryption becomes less of a damaging process when users data becomes affected, stole, or even leaked. Since the virus loads other files and modifies crucial places of the machine, locate to C:\Windows\System32\drivers\etc\ and find modified host file to delete it completely.
You should remove Gero ransomware, and then clean the virus damage with FortectIntego. If you have reliable backups, you can use those to replace encoded files, or get a data restoring software. Also, you may have an advantage in all these processes if you go for the methods listed below.
Getting rid of Gero virus. Follow these steps
Manual removal using Safe Mode
Reboot your machine in the Safe Mode with Networking, so all the needed security functions can work properly
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Gero using System Restore
You may benefit from System Restore feature when dealing with Gero ransomware
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Gero. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Gero from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Gero, you can use several methods to restore them:
Data Recovery Pro can be one of the many options suitable for the file restoring after the ransomware attack
You may need an alternate method for file restoring when backups are not up to date. Data Recovery Pro is the program for that
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Gero ransomware;
- Restore them.
Gero ransomware encrypts files, try to recover them with Windows Previous Versions
When System Restore feature gets enabled, you can try Windows Previous Versions for data recovery
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is capable of restoring files after Gero ransomware attack
ShadowExplorer works when ransomware leaves Shadow Volume Copies untouched
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption is not possible for Gero ransomware affected files
However, many researchers work on creating such tools, so check occassionaly
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Gero and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Larry Dignan. Ransomware attacks: Why and when it makes sense to pay the ransom. ZDNet. Technology news and reviews.
- ^ New version of AZORult stealer improves loading features, spreads alongside ransomware in new campaign. Proofpoint. Threat insight.
- ^ Virusi. Virusi. Spyware related news.





















