GonnaCope ransomware (virus) - Recovery Instructions Included
GonnaCope virus Removal Guide
What is GonnaCope ransomware?
GonnaCope is a malicious Windows program that prevents access to personal files
GonnaCope ransomware was first spotted in the wild at the end of April 2022 by security researcher Petrovic.[1] While most malware of this type simply appends the extension to already existing file names, this virus instead renames them in a random numerical pattern and only then appends the .cope extension to each of them. In order cases, ransomware applies the encryption[2] algorithm without appending any extensions to data.
Regardless of this functionality, the result of a ransomware infection is still the same – users are unable to open pictured, documents, databases, videos, and other personal files. Once this process is finished, the GonnaCope virus drops a ransom note ReadMe.txt, which can be opened in any text editing app. In addition, it automatically opens a Command Prompt window which displays the exact same sentence several times – it asks victims to transfer $100-worth of bitcoin to the bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll BTC wallet.
We do not recommend cooperating with the attackers, as there is no guarantee that the data can even be decrypted using their tools (of such exist). Considering that the threat is relatively new, it might be a simple scam. Data recovery might be achieved in other methods we list below, although ransomware removal must be performed before that.
| Name | GonnaCope ransomware |
|---|---|
| File extension | .cope |
| File Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we provide them below |
| Ransom note | ReadMe.txt and Command Prompt window |
| Ransom payment | $100 in Bitcoin to be paid to the bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll BTC wallet |
| ransomware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Ransom note overview
As a general rule, all ransomware developers ensure that a ransom note, usually dropped in the TXT format for ease of access, is delivered right after the data encryption is finished. The note serves the purpose of a quick explanation of what happened to users' computers and files, and that's where ransom demands and contact info are usually located.
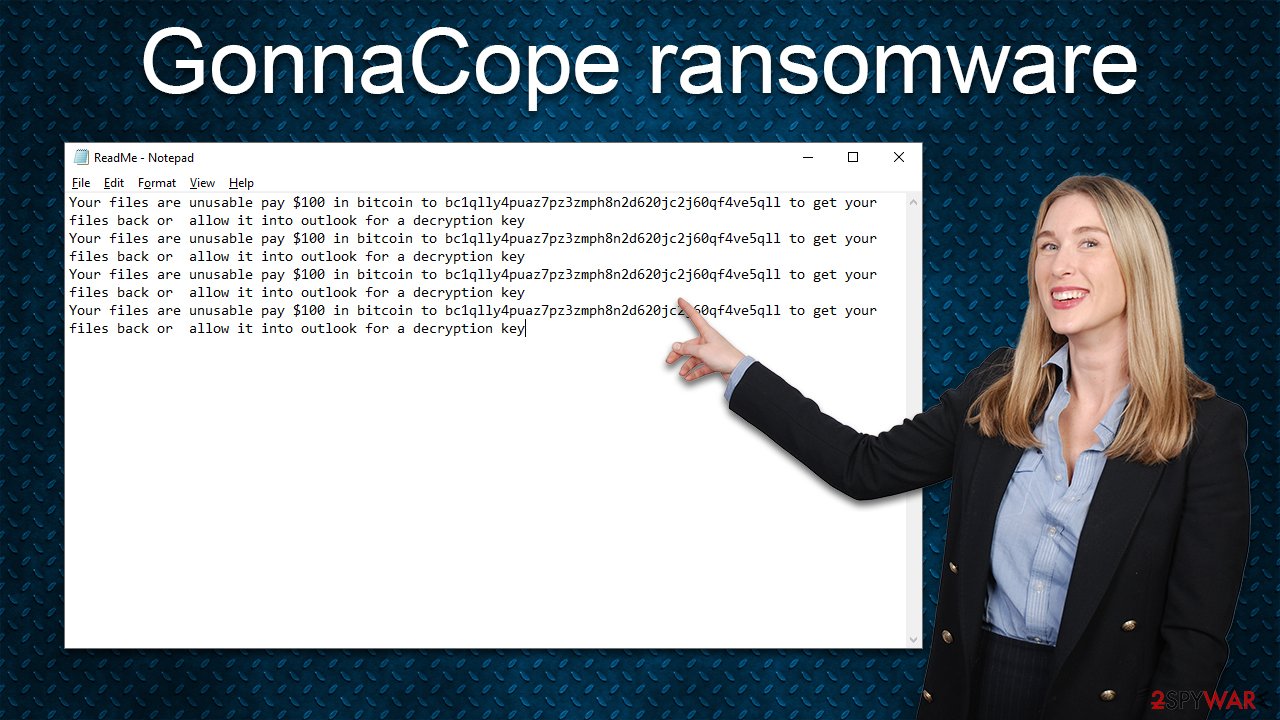
New ransomware strains, such as GonnaCope, might come with poorly made ransom notes, lack certain details, or fail to provide the note in the first place. In this case, malware authors made sure that the note definitely reaches the victims, although it is rather lackluster. The ReadMe.txt and the CMD window show the sentence repeated several times:
Your files are unusable pay $100 in bitcoin to bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll to get your files back or allow it into outlook for a decryption key
Your files are unusable pay $100 in bitcoin to bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll to get your files back or allow it into outlook for a decryption key
Your files are unusable pay $100 in bitcoin to bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll to get your files back or allow it into outlook for a decryption key
Your files are unusable pay $100 in bitcoin to bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll to get your files back or allow it into outlook for a decryption key
As evident, it is lacking the key element here – contact information. Users are simply asked to transfer $100 to a particular BTC wallet, and there's no information about how the decryptor would be sent back to victims. Thus, do not bother paying, and instead, rely on alternative data recovery methods. But first, make sure you remove the virus from your system correctly – simply follow the instructions below.
Step 1. Disconnect your PC from the network
The first task after ransomware infection is to ensure that there's no network and internet connection established on the affected device. For that, you could disconnect the cable from the PC or use the following method if there is more than one machine affected:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Step 2. Remove ransomware
While most ransomware is programmed to self-delete after the encryption process is finished, it is not the case with GonnaCope. As long as the virus is installed on the system, it is not safe to use it, as it may continue corrupting incoming files. Besides, ransomware is commonly spread along with other dangerous malware, so a system scan with security software is mandatory for an affected system.
Once you are sure that your system is disconnected from the network, you should perform a full system scan with powerful antivirus software – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes. It can find all the malicious components at once and remove them automatically for you.
Step 3. Fix your system
Regardless of whether the above methods helped you to restore files or not, you should not neglect your Windows system. After malware infection, it might start malfunctioning – crashing, lagging, failing to launch applications, returning errors, and much more. Thus, we strongly recommend you follow the below instructions to repair your system instead of reinstalling it.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Step 4. Attempt file recovery
It is important to note that file recovery and ransomware infection are two separate occurrences on the affected system. The latter can not be conducted without the former, although data would remain locked even after the virus is removed from the affected machine. In other words, scanning your computer with security software would not restore .cope files.
Since GonnaCope ransomware scrambles the names of the affected files, does not append any extensions to others, and is a relatively new strain, there is a strong chance that malware is still in development or has plenty of bugs. Therefore, counting on crooks' recovery tools shouldn't be an option.
Instead, we recommend relying on applications that are designed for data recovery. Keep in mind that file recovery might not always be possible, but some victims might be able to restore at least some of the locked data.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![GonnaCope ransomware GonnaCope ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors,[3] which allows the keys to be released by the public – this is usually done by reputable security vendors. Here are a few links you might find useful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Petrovic. #Ransomware #gonnacope. Twitter. Social network.
- ^ What is encryption? Data encryption defined. IBM. Security research.
- ^ Europol takes down VPNLab, a service used by ransomware gangs. The Record. Daily breaking news.










