Hachiman ransomware (virus) - Free Instructions
Hachiman virus Removal Guide
What is Hachiman ransomware?
Hachiman ransomware is a malicious program that locks your screen and demands to transfer Bitcoins to a crypto wallet to unlock it
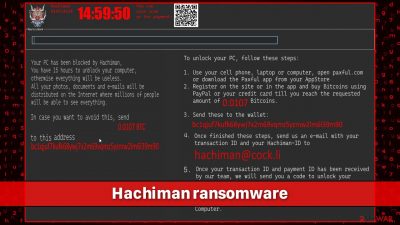
While Hachiman virus is categorized as ransomware, it is not a typical one that locks all personal files individually. Instead, its authors took an approach that was used by cybercriminals over a decade ago – screen locking. This means that, upon infecting the computer, the malware locks the computer screen of the victim and prevents them from accessing any of Windows features, for example, the Task Manager would not show up even by pressing the shortcut that would call it up under normal circumstances.
If you were a victim of Hachiman ransomware, you should not panic, as it not being a file-locker is actually a good thing. What you need to do now is find a way to remove the infection, which would also terminate the screen-locking component from your system. In this article, we will explain how to do just that and how to avoid paying the demanded ransom.
| Name | Hachiman virus |
|---|---|
| Type | Ransomware, screen-locker |
| Encryption method | Screen-locking |
| Cryptowallet | Criminals demand 0.0107 to be sent to bc1qjuf7kufk68ywj7x2m69vqmz5yzmw2lm6l39m90 cryptowallet |
| Contact | hachiman@cock.li |
| PC access block | Enter the unlock key JHA7236-HACHIMAN-37JHAl924-JFHACHI to unblock your computer |
| Malware removal | Perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Detection names
Since the Hachiman virus does not belong to any malware family, little is known about its origins or the cybercriminals behind its creation. The main file that executes the malicious payload is signed by a valid certificate by “Black Line Risk Management Consulting Inc,” which is a legitimate IT assurance and advisory company – crooks usually manage to fake these certificates.
Nonetheless, despite a valid certificate, security software such as SpyHunter 5Combo Cleaner or Malwarebytes can determine that the file would deploy a ransomware attack immediately. Here are the names of the “DomainUtility.exe” file, used in one of the infection samples, is identified by various security vendors:[1]
- Win32:MalwareX-gen [Trj]
- Trojan.GenericKD.48713186
- Trojan:Win32/Tiggre!rfn
- Malware.AI.4292606635
- Trojan.MSIL.LOCKSCREEN.AD
All these names are heuristic, which means that malware was detected by analyzing its malicious properties instead of comparing it to already established malware strains.[2]
The ransom note
Typically, a ransom note is used by ransomware to make sure that the communication between victims and the attackers is established. Under normal circumstances, it is presented as a text file or an HTA file, which would open up automatically after the virus would finish the file encryption[3] process.
Since Hachiman ransomware does not lock the files, the ransom note is displayed as soon as the payload is executed, which is almost immediately after a malicious file is opened. This fine can be downloaded from different sources, including spam emails, torrents or software crack sites, fake updates, and more.
Once executed, malware would alter Windows operating system in various ways in order to ensure it operates the way hackers want it to. Right after that, the ransom note would be shown to users, and Windows would not launch as usual.
According to crooks, victims have 15 hours to unblock their PC, otherwise, all their personal photos, emails, and other information will be leaked on the internet. They demand 0.0107 BTC which is meant to be sent into the crypto wallet bc1qjuf7kufk68ywj7x2m69vqmz5yzmw2lm6l39m90.
Allegedly, once these steps are finished, users should contact hackers via the hachiman@cock.li email with their personal ID and they would send back the code that would allegedly unlock your PC.
However, the unlock key has already been discovered by security researchers, and it works for each of the victims – it is JHA7236-HACHIMAN-37JHAl924-JFHACHI – simply enter this code and your computer will be unlocked. Nonetheless, keep in mind that malware would likely be present on the system, so follow the information in the next section.
Removal instructions
Luckily, screenlockers do not encrypt personal files, which is generally good news. However, they might be a pain to get rid of, especially for users that do not know where to start, as they can't operate their systems at all. As we already mentioned, you can use the code JHA7236-HACHIMAN-37JHAl924-JFHACHI to unlock your device, although this might not always work for all victims – you might also have a different virus version installed on your system.
In such a case, you can bypass malware's functionality by accessing Safe Mode with networking and performing a full system scan with SpyHunter 5Combo Cleaner or another powerful security software:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
![Update & Security Update & Security]()
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
Remediate your system
Upon entering the system, malware can significantly alter its performance and functionality. In this case, as soon as the infection spreads, the boot sequence changes, and, instead of seeing the typical Windows login screen, users would be presented with a ransom note – all the other functions would be disabled in the meantime. Pressing any keyboard combinations that would bring up built-in elements such as command prompt or the task manager would also be disabled.
When the virus performs these changes to the system, it can damage its files, which later might cause instability issues, including crashes, errors, Blue Screen of Death[1] crashes, and much more. Instead of reinstalling the operating system, you could instead rely on a powerful PC repair tool that would get rid of these problems for your automatically:
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
By using this removal guide, you can avoid payments to cybercriminals – it should also help you to get rid of any additional modules or other malicious payloads present on the system. Since this virus does not possess any file-locking functionality, all your data should be intact. However, to avoid future ransomware attack consequences, we recommend you back up your files as we explain below.
Getting rid of Hachiman virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Hachiman and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ DomainUtility.exe. Virus Total. File and URL analysis.
- ^ What is Heuristic Analysis?. Kaspersky. Resource center.
- ^ What is encryption? Data encryption defined. IBM. Security blog.





















