Heavypcnetwork.com scam (Chrome, Firefox, IE, Edge) - Free Instructions
Heavypcnetwork.com scam Removal Guide
What is Heavypcnetwork.com scam?
Heavypcnetwork.com is a scam website designed to scare visitors and make them believe system infections
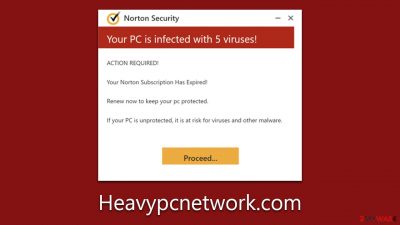
Heavypcnetwork.com stands as a deceptive scam website strategically designed to dupe users into thinking their computers are plagued by malware. When accessed, it immediately displays a message, mimicking the familiar appearance of a McAfee security alert. This message falsely asserts that the user's system has been infiltrated by malicious viruses and harmful websites, invoking immediate alarm.
However, it's crucial to understand that this warning is a complete fabrication, bearing no ties to genuine McAfee products. Such fictitious alerts are tools wielded by scammers seeking monetary gain from advertisements and affiliate marketing through dubious methods.
Furthermore, Heavypcnetwork.com slyly encourages users to activate push notifications. Succumbing to this request can lead to recurrent appearances of these sham virus alerts. It's recommended to steer clear of any engagements with Heavypcnetwork.com and to scan one's system for potential adware. Maintaining awareness and exercising caution is essential in safeguarding one's device against these cunning tactics.
| Name | Heavypcnetwork.com |
| Type | Scam, phishing, redirect |
| Scam content | The scam is based on scaring users into believing that their systems are infected and that they need to remove those infections with promoted software |
| Distribution | Redirects from other malicious websites, adware |
| Risks | Loss of finances due to fake subscriptions; redirects to other malware-laden, scam websites; installation of potentially unwanted or malicious software |
| Removal | Interacting with the scam content is dangerous, as scammers may promote fake versions of antivirus software. Instead, use reputable tools for your system safety |
| Other tips | To prevent third parties from tracking your online activities, we recommend clearing browser caches and other leftover files with FortectIntego |
Accidental access is one of the main ways users reach Heavypcnetwork.com
Users frequently encounter scam websites through two predominant routes: inadvertent interactions on compromised sites or as a consequence of adware and other malware.
The initial scenario involves unsuspecting users accessing otherwise legitimate websites. Sometimes, due to factors like security loopholes or outdated platform versions, hackers manage to exploit these sites. They subtly embed malevolent codes that, when clicked on, redirect visitors to malicious domains. These compromised links can cunningly mimic authentic ones, making detection challenging. Often, users only become aware of the deception when it has already caused damage.
In the alternative situation, a user's device gets infected by adware or similar malware. Defined as software that thrusts unsolicited advertisements, adware can be clandestinely bundled with other online downloads. When this happens, it's common for users to find themselves suddenly redirected to unrequested websites or pestered by pop-ups guiding them toward malicious sites.
Whichever route, the ramifications of being lured into these deceptive websites can be dire, ranging from financial repercussions to identity compromise. It underscores the importance of proactive system defense and cautious online navigation.
Scammers use fake alerts to intimidate people
Scammers capitalize on fear, employing a range of tactics to exploit individuals, especially those unfamiliar with the intricacies of technology. They tap into anxieties, using them as a weapon to manipulate and defraud.
One widespread approach involves conveying alarming malware threats. This is particularly prevalent on malicious websites that rely on advertising networks with lax scrutiny over ad content. As a result, visitors of websites offering unauthorized content—like torrent repositories or unsanctioned video streaming sites—are more susceptible to confronting scam messages or malicious advertisements.
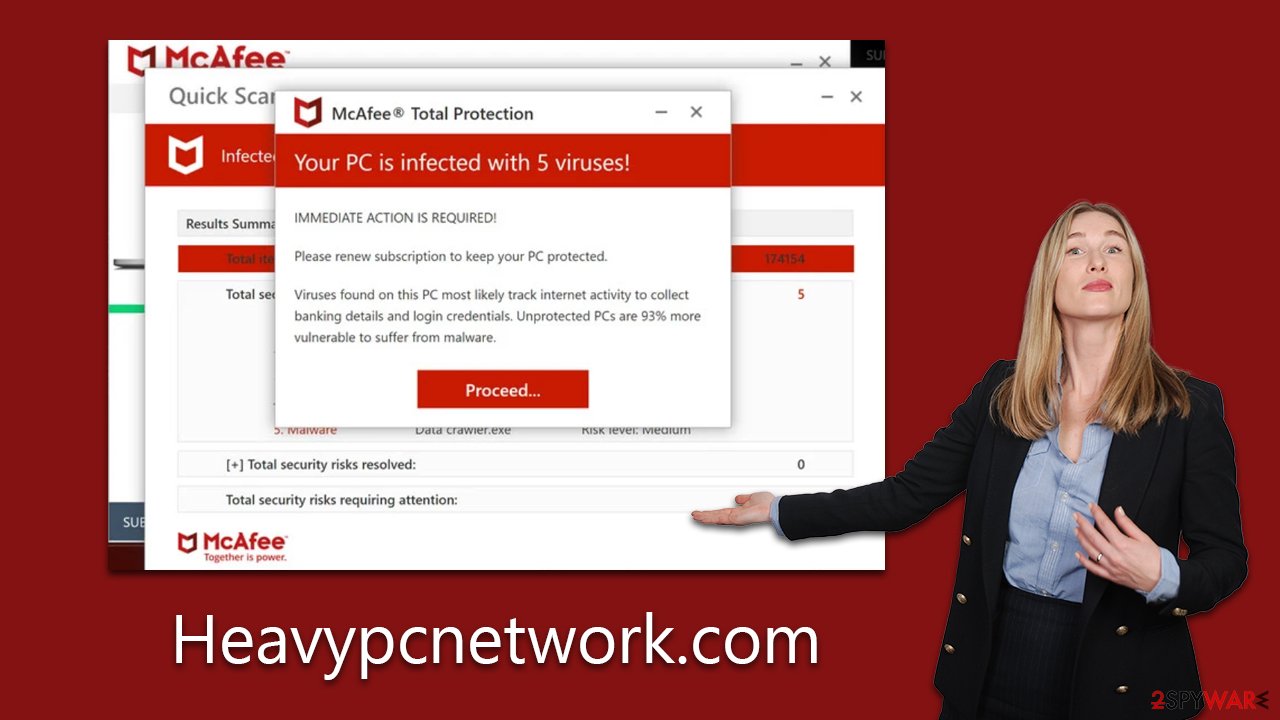
For instance, there's a scam tactic mirrored by sites like Heavypcnetwork.com, where the design and alerts are made to appear akin to established security software interfaces. These alerts might display daunting messages such as:
Your PC is infected with 5 viruses!
IMMEDIATE ACTION REQUIRED!
Your McAfee subscription has expired!
Renew now to keep your PC protected.
Viruses found on this PC most likely track internet activity to collect banking details and login credentials. Unprotected PCs are 93% more vulnerable to suffer from malware.
It's essential to highlight that only legitimate security tools installed on a device can truly identify and neutralize malware threats. The red flags with these scam alerts include their generic nature, presenting the same message to every user, irrespective of their device's security condition. Furthermore, genuine security alerts aren't delivered via browser animations, revealing the superficial nature of such scam warnings.
Checking the system for infections and cleaning browsers
In response to the deceptive tactics of Heavypcnetwork.com, the steps you take for system remediation can differ based on your actions and the current software on your device. If you interacted with the dubious prompts or engaged with compromised links from this site, there's a likelihood that harmful applications found their way onto your computer.
Even if you didn't directly interact with such prompts, maintaining robust system security is paramount. This is because adware, a prevalent culprit, can significantly contribute to the penetration of phishing websites into your system. To ensure your device is thoroughly purged of any potential adware, it's advised to conduct a comprehensive scan using trusted security tools like SpyHunter 5Combo Cleaner or Malwarebytes. These applications swiftly and decisively tackle and remove any malicious entities.
While one might consider manually deleting unwanted programs, the automated process stands out as the more straightforward and safer approach. Erroneously removing essential software can have detrimental effects. After ensuring your system is void of any malevolent programs and intrusive ads, it's crucial to cleanse any cookies or trackers that might be lingering on your browser. Either utilize a specialized cleaner such as FortectIntego or adhere to the following straightforward steps:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Scam sites, such as Heavypcnetwork.com, have expanded their deceptive tactics beyond just direct site interactions. One of their more insidious strategies involves exploiting the push notification system. Push notifications are typically used by legitimate websites to provide timely updates or alerts directly to a user's screen.
However, scam sites abuse this feature by coaxing users, often through misleading prompts or fake alerts, into granting them permission to send notifications. Once granted, these websites can incessantly bombard the user with dubious messages, even when they are not actively browsing the site.
Even after users have diligently removed suspicious programs from their computers, this doesn't always spell the end of intrusive alerts. The reason is that these notifications operate separately from any software installed on the system. They are linked directly to the browser's permissions, meaning that even with the malicious software gone, the push notifications can continue to disrupt the user's experience.
These relentless pop-ups can serve multiple malicious purposes, from phishing attempts to promoting further scam websites. Thankfully, there's a way to combat this nuisance. Instructions to halt these malicious push notifications can be found below.
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the URL's drop-down menu.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
- Click on More actions and select Block.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.








