Judy virus (Free Guide) - Tutorial
Judy virus Removal Guide
What is Judy virus?
Judy – Android malware that uses affected devices for generating pay-per-click revenue
Judy is adware program that has been widely distributed on Google Play store. Malware may have affected more than 35 million Android users. The purpose of the adware is to generate advertising-based revenue.
Malware employed a two-stage attack vector that allowed to bypass Google’s security. In this way, 41 applications, such as Jeff Judy: Picnic Lunch Maker, Fashion Judy, Magic Girl Style and Fashion Judy, Masquerade Style, and others, were added in Google Play store without being detected. However, once users installed one of the malicious apps, the malicious payload was downloaded from the another server.
After the installation Judy virus connects to its Command and Control (C&C) server. It responds with malware payload that consists of three main components: JavaScript code, user agent string, and particular URLs. With the help of them, malware connects the affected device to an adware server and starts working as a browser: by opening particular pages it generates advertising-based revenue.
The security firm Check Point detected that malicious applications were created by Kiniwin – the Korean company that develops mobile apps for Android and iOS systems. Meanwhile, on the Google Play shady developers were registered as ENISTUDIO corp. However, several infected apps were developed by other developers. The relationships between creators are unknown.
Surprisingly, malicious applications have been available on Google Play for a while. Some of them were available since 2016. However, recently, they were updated.[1] What is more, they had high rates, and it may have tricked millions of users. However, relying only on user’s evaluation is not enough. Hackers may create dozens of fake reviews in order to make a good image of the app. Therefore, if you have been tricked and installed a malicious program, you should not hesitate and focus on Judy removal.
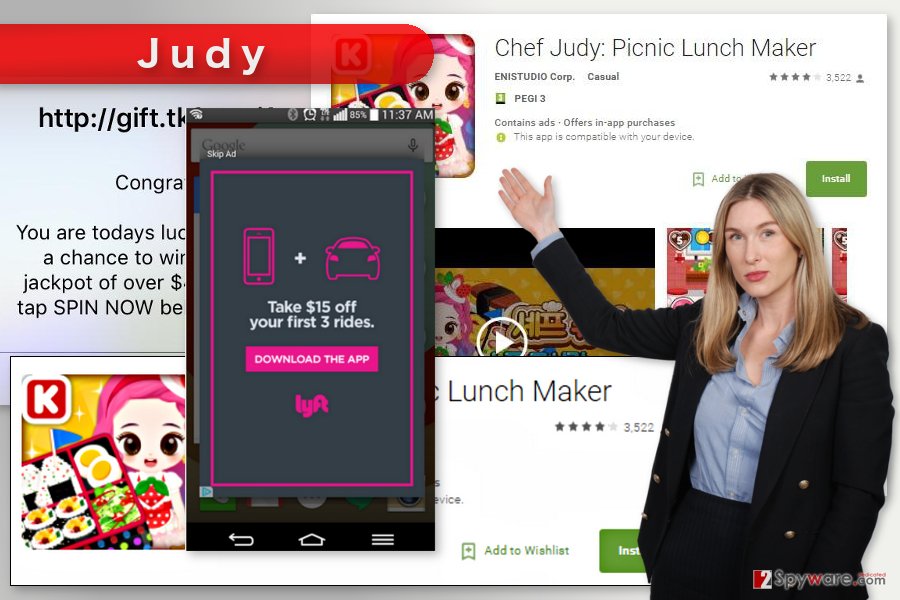
Apart from using affected devices for generating pay-per-click revenue illegally, Judy also displayed tons of aggressive ads. They may have shown up as pop-ups or cover the whole device’s screen. Some of them did not have a close button and forced users to click them in order to use their smartphones normally again.
Google was informed about malicious apps, and they were removed immediately. However, people should check the list of installed programs and make sure that Judy hasn’t been installed on their smartphones or tablets. The full list of applications is disclosed in Check Point’s blog post.[2]
If malware ended up on your device, you should run a full system scan with a mobile-friendly security program, such as FortectIntego. It helps to remove Judy and keep your phone protected from other cyber threats in the future.
Malware has been spreading as an obfuscated app
Judy has been distributed via 41 different application on Google Play App store. Nevertheless, all these applications were detected and eliminated; you should be aware of this sneaky distribution technique in order to avoid similar attacks. Before installing new applications to your phone, always read users review online and learn more about the developer. As you can see, trusting reviews only on Google Play may not be enough.
However, malware might also be distributed on unauthorized sites that offer to download various applications. It goes without saying that you should stay away from these sources. Installing apps from here may lead to even bigger problems than Judy hijack.
Eliminating Judy malware from Android device
In order to remove Judy from the device, you should uninstall a malicious app from your smartphone or tablet. Got to Settings and access Apps (or Application manager) and in the appeared list find malicious apps. Uninstall them just like regular programs.
However, malware may have installed additional components on the device. Thus, we highly recommend opting for automatic Judy removal option. It requires scanning the device with a reputable anti-malware program, such as FortectIntego. Your chosen software not only deletes adware but protects your device from similar threats in the future.
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Daniel Fuller. Judy Malware Has Hidden In Play Store For Over A Year. AndroidHeadlines. The Website Provides Latest Android News.
- ^ The Judy Malware: Possibly the largest malware campaign found on Google Play. Check Point Blog. Check Point Software Blog.
