Key Board browser hijacker (virus) - Free Guide
Key Board browser hijacker Removal Guide
What is Key Board browser hijacker?
Key Board is a tool that allows crooks to make a profit from your browsing activities
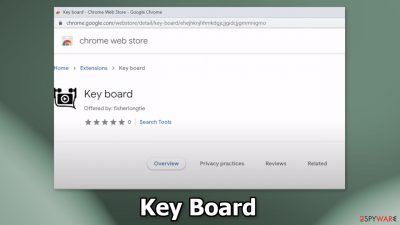
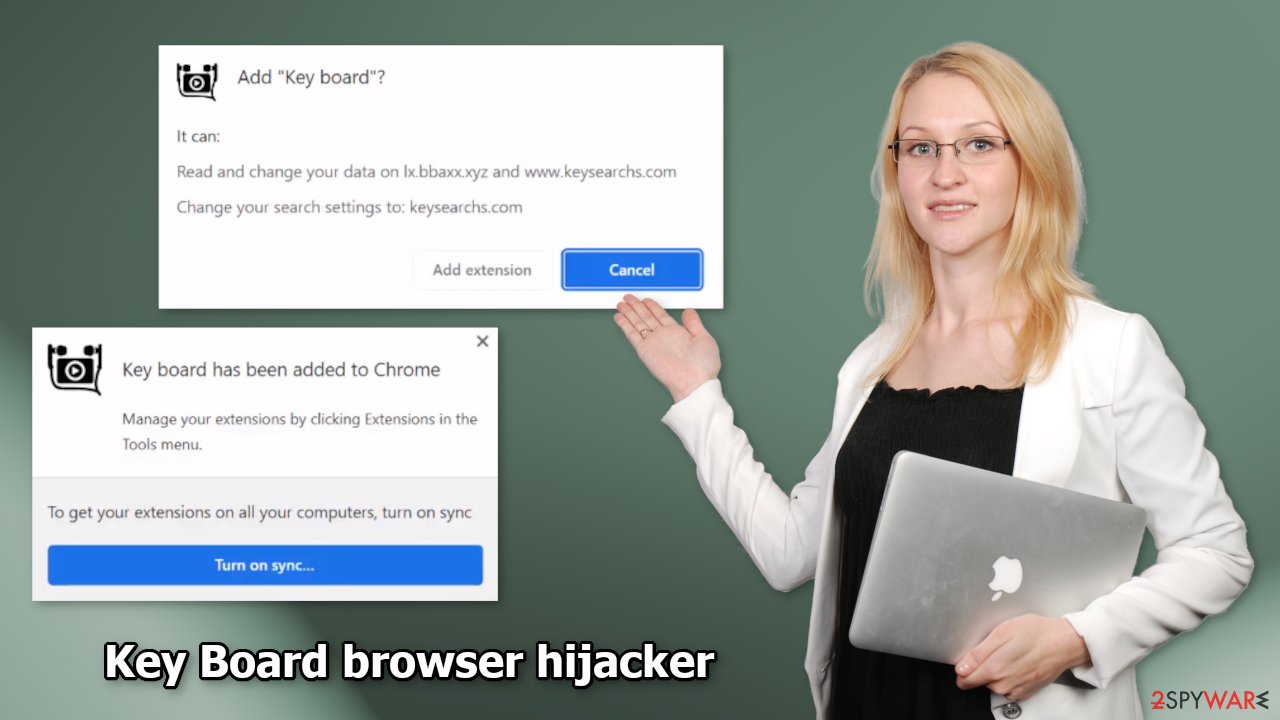
Key Board is classified as a browser hijacker. If you came across this app on a web store you should not install it. If you think it is affecting your browser you should remove it as soon as possible. This plugin can change the main settings of your browser, like the homepage, new tab address, and search engine.
Crooks try to make such applications look like “handy” tools. They often claim that they can block ads, provide secure browsing, and so on. However, none of these claims are true, as such add-ons are created solely for the purpose of generating revenue from pay-per-click advertising[1] and data gathering.
As a result, people can also experience an increased amount of commercial content, pop-ups, banners, and redirects. The creators of browser hijackers do not really care about user privacy or security, so they may use rogue advertising networks that place ads leading to dangerous websites. People can end up on scam pages that try to trick them into providing personal information, downloading PUPs (potentially unwanted programs),[2] or even malware.
| NAME | Key Board |
| TYPE | Browser hijacker; potentially unwanted program |
| SYMPTOMS | The main settings of the browser get changed, like the homepage, new tab address, and search engine |
| DISTRIBUTION | Shady websites, deceptive ads, freeware installations |
| DANGERS | Users might get redirected to shady sites that can trick people into downloading PUPs or even malware |
| ELIMINATION | Remove the extension in your browser settings |
| FURTHER STEPS | Use FortectIntego to fix any remaining damage and optimize the machine |
Distribution methods
Browser hijackers can be spread around the Internet in various ways. Some crooks create separate promotional websites for their plugins and then advertise them on shady pages. That is why you should not trust every ad you see online. Do not click on random links and buttons. Especially avoid sites that engage in illegal activities because they are often full of deceptive ads and sneaky redirects.[3]
Even though we always recommend using only official web stores to download browser extensions, fraudsters have figured out a way to slip through an extensive review process. That is why some browser hijackers, like Key Board, get listed on stores like the Chrome web store.
You should always do your research – read the reviews, look at the ratings, and the number of users a plugin has. It is best to choose those apps that have plenty of feedback and thousands of users. It is also a good idea to read the description – inspect it, and see if there are any grammar or spelling mistakes, they should always raise suspicion.
Key Board removal steps
Browser hijackers are minor infections that are not as malicious as Trojans, ransomware, or other malware. This is why users rarely have trouble removing them. If you follow our step-by-step guide carefully, you should get rid of the intruder easily.
Hijackers usually reside in browsers, which means that the main app that should be removed to eliminate the PUP is an extension embedded in the browser. If you have never dealt with browser add-ons, we provide comprehensive instructions below.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
2. Check your system for PUPs
While Key Board is a browser extension, there could be additional apps installed on your computer that perform unwanted tasks. This is especially true if you are keen on frequently downloading software from third-party websites. Bundles can include several programs and, if you are not careful enough, all of them might slip through during the installation process. Thus, you should check the section of the installed applications on your machine.
PUPs such as adware are often distributed through freeware[4] platforms. We recommend using only official web stores or developer sites if you want to install software. You should also always choose the “Custom” or “Advanced” installation methods, read the Privacy Policy and Terms of Use. The most important step is to check the file list and untick the boxes next to any unrelated apps.
To remove PUAs, you can scan your device with SpyHunter 5Combo Cleaner, Malwarebytes, or another trusted anti-malware software to ensure that there are no malicious programs and processes running in the background. Keep in mind that those who visit dangerous websites are more likely to get infected with malware. Without security software, it is almost impossible for regular computer users to know if it is present on the device, as the operations are usually hidden.
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
3. Clean your browsers
Cookies are small pieces of data that are used to include all sorts of settings. While they cannot be malicious by themselves, they can be stolen by third parties and used for malicious purposes. They can store information such as your IP address, geolocation, websites you visit, links you click on, and things you purchase online.
Therefore, security experts advise cleaning web browsers regularly. You can employ automatic cleaning tools such as FortectIntego, although you can also refer to the manual instructions below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ What Is PPC & How Paid Search Marketing Works. Searchenginejournal. SEO News.
- ^ Adam Kujawa. Encountering the Wild PUP. Malwarebytes. Threat Analysis.
- ^ Nick Altimore. Sneaky Redirects – What You Need To Know. Sirlinksalot. Link Building Services.
- ^ Freeware. Wikipedia, the free encyclopedia.












