Kyc.bartus.live ads (scam) - Free Instructions
Kyc.bartus.live ads Removal Guide
What is Kyc.bartus.live ads?
Kyc.bartus.live ads are fake: scammers attempt to manipulate you into downloading software
Kyc.bartus.live is a scam website created to trick users in various ways. Its operation is rather simple: it attempts to convince people that their systems have been infected with dangerous malware and it needs to be removed as soon as possible. As typical, it is then offering to follow the link where a purchase of security software can be made.
In order to make the scheme more convincing, Kyc.bartus.live uses several tricks. First of all, it attempts to imitate a full system scan usually performed by anti-malware software. It also uses a well-known cybersecurity vendor Norton – it usually redirects to a security app purchase page of the official website.
However, the whole scheme is operated by scammers who want to profit from affiliate marketing. Each user who spends money on this converts into a commission fee paid to scammers. Also, it is not a secret that scam messages often advertise potentially unwanted applications to be installed, which can actually harm the computer instead of protecting or fixing it. Thus, we do not recommend interacting with the promoted links and instead, following the instructions below to ensure that the system is not affected by adware[1] or other malware.
| Name | Kyc.bartus.live |
| Type | Scam, ads, fraud, redirect |
| Infiltration | Compromised websites, pop-up ads, potentially unwanted applications |
| Scam content | Claims that the subscription for security software has expired and that it needs to be renewed immediately. Asks to download malicious software and enable push notifications |
| Dangers | Installation of other potentially unwanted software or malware, personal information disclosure to cybercriminals, financial losses due to scams, etc. |
| Removal | Do not interact with links or other content of a scam site. Instead, check your system with SpyHunter 5Combo Cleaner security software |
| Other tips | Cleaning web browsers is one of the secondary things you should do after PUP/malware removal to secure your privacy. You can use FortectIntego to do it quicker |
Numerous websites promote the same scam
The main reason for the creation of fake messages online is to profit from ads, software downloads, or subscriptions to various services. While selling software or services is a totally legitimate practice used by many parties, it becomes the opposite when highly misleading messages are used to promote it.
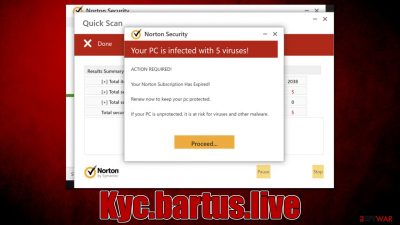
Upon entering Kyc.bartus.live, users are shown a fake anti-malware scan, which immediately comes back with the following fake result:
Your PC is infected with 5 viruses!
ACTION REQUIRED
Your Norton Subscription Has Expired!
Renew now to keep your PC protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Frightened users are more likely to fall for the scam, as they are scared about their personal information and computer security. This is one of the main pointers when it comes to social engineering, and crooks use them well. They mislead people thanks to fake logos, fake warnings, and fake virus scan results.
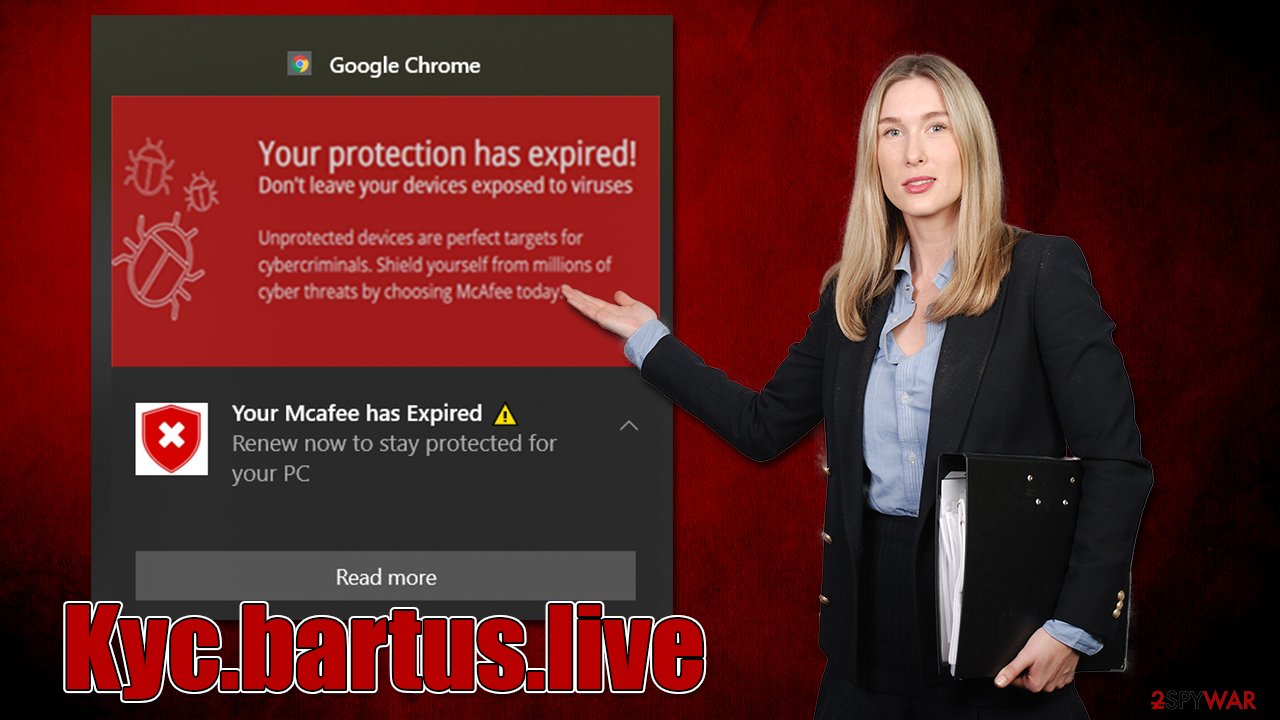
It is easy to tell when the page is showing you phishing[2] content, however. First of all, you should look at the web address displaying the message – Kyc.bartus.live has nothing to do with Norton or any other reputable company.
Second of all, you should generally never trust messages which claim that something is missing, needs to be updated, or that malware has been found on your device. All of these, without exception, are fake. If you need to install updates, always visit legitimate websites of various vendors and completely disregard redirects.
Encountered Kyc.bartus.live ads? Here's what to do next
The most important thing when dealing with dubious messages online is not to panic and assess the situation correctly. Scammers might claim that your PC is locked or that you shouldn't/can't close the tab – always check if this is true. Obviously, the best way to go about this is not to interact with any scam page components – links, buttons, etc.
Regardless of whether you have done so or not, we still recommend checking the below instructions to ensure your system integrity and security, as adware could be secretly running on your device.
Check your system for infections
The first step to a better and safer computing environment is a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. Anti-malware tools are diverse, and they serve an important purpose – protecting users from infections. If the virus is already inside, its removal should be performed using them.
You could check the installed extensions on your browser and also go through the list of the installed applications on the system level. However, this is not necessary if you scan your device with security software.
Take care of your privacy
Once you are sure that your device is not infected with anything malicious, it is time to clean your web browsers. Cookies, web beacons,[3] and other tracking technologies are used to track various user data by third parties. These items are stored locally and might remain there for years if not deleted. The easiest way to get rid of them is by using FortectIntego, although a manual method is also available:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
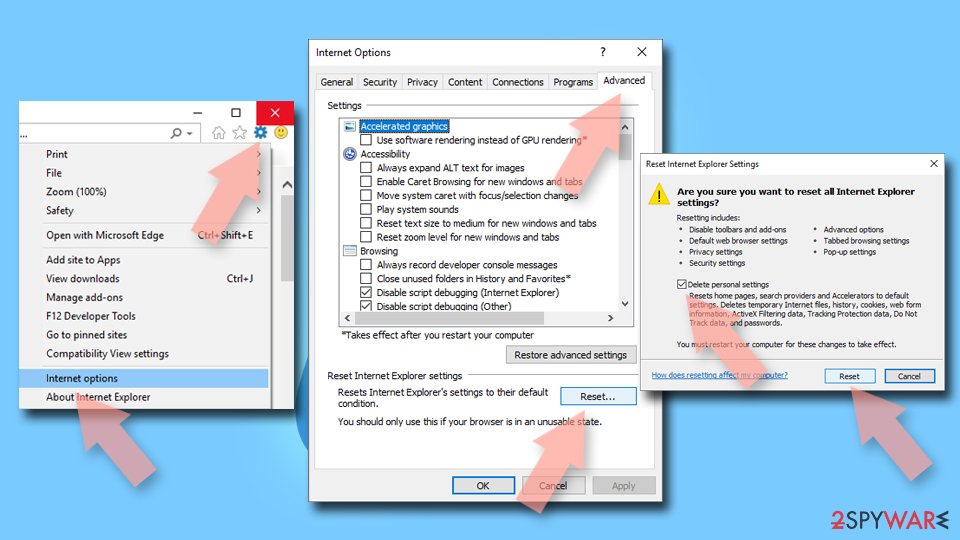
Internet Explorer
- Click on Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
![Reset Internet Explorer Reset Internet Explorer]()
Remove push notifications
A push notification prompt is always shown upon entering the Kyc.bartus.live site. Even if you don't accept this request intentionally, this can happen by accidentally clicking the “Allow” button within the prompt.
Those who agree to this request would allow the website to send information to users' desktops at any time without any restrictions. Push notifications would show all kinds of dangerous ads and links to malicious websites. Do not interact with the promoted material, or you could put your privacy and computer security in danger. Instead, follow these steps:
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
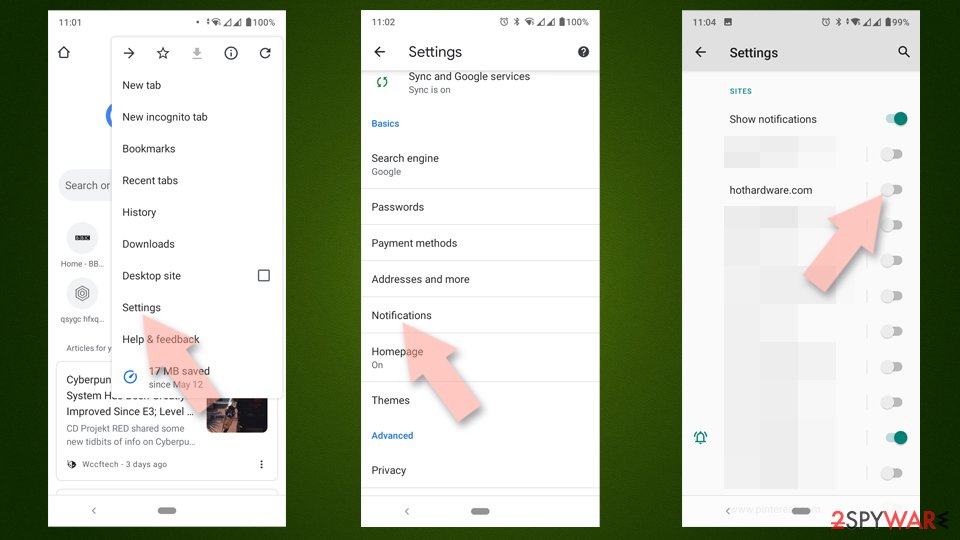
Google Chrome (Android)
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off position).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
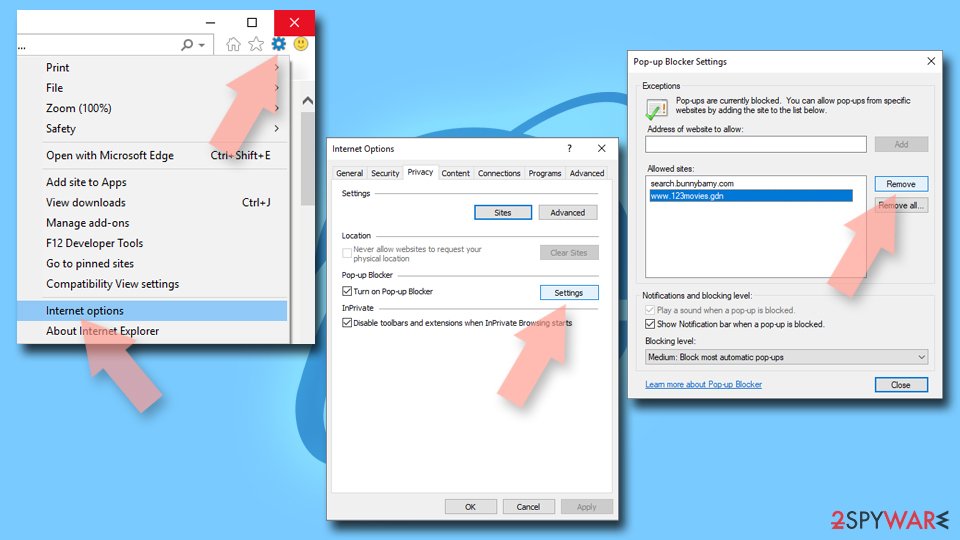
Internet Explorer
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
![Stop notifications on Internet Explorer Stop notifications on Internet Explorer]()
- Locate the web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Adware. Investopedia. Source of financial content on the web.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ Cookies and Web Beacons. NTT. NTT Communications.