LeakerLocker ransomware / virus (Virus Removal Instructions) - Tutorial
LeakerLocker virus Removal Guide
What is LeakerLocker ransomware virus?
LeakerLocker – Android malware that was spotted spreading in Google Play
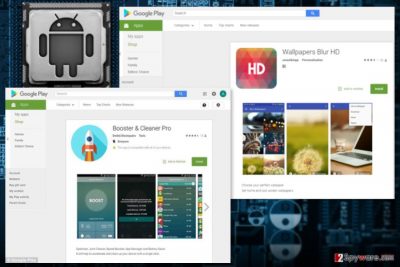
LeakerLocker is a new variant of Android ransomware that has been spotted spreading via two apps in Google Play store – “Wallpapers Blur HD” and “Booster & Cleaner Pro.“ This mobile malware[1] cannot encrypt files but threatens to leak sensitive victim’s information if she or he does not pay a ransom of $50 in 72 hours.
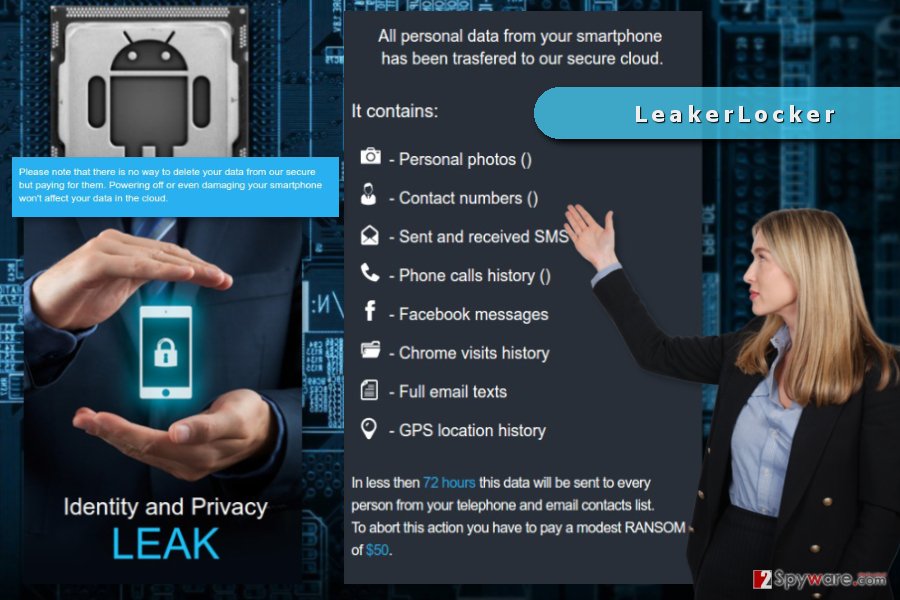
LeakerLocker virus locks device’s screen and delivers a pop-up window as soon as the user downloads one of the infected apps. It says that malware contains this information that will be sent to each phone and email contact if criminals won’t receive a “modest ransom” within the deadline:
- Personal photos;
- Contact numbers;
- Send and received SMS;
- Phone calls history;
- Facebook messages;
- Chrome visits history;
- Full email texts;
- GPS location history.
Crooks claim that all the personal data was transferred to their secure cloud. Thus, deletion of the LeakerLocker ransomware won’t protect personal files and data. However, these words might be just a threatening tactic used by cyber criminals in order to get as many ransoms as possible. Therefore, you should not rush click “Procceed” button and make the transaction.
No one knows if crooks copied your files, if they can publish this data or if they keep their words once they receive the ransom. The research has shown that malware can access particular data by communicating with its Command and Control (C&C) server. However, the situation does not seem as crooks want to make you believe.
What is more, even if you pay the ransom, they might ask for more money later. Therefore, demanded $50 might be just the beginning of swindling your money. Thus, it’s better to remove LeakerLocker from the Android device and hope for the best.
LeakerLocker removal requires not only uninstalling malicious apps but checking the system for other suspicious components. This task might be complicated, so we suggest automatic elimination option using mobile-friendly security software, for instance FortectIntego.
Two malicious apps were available on Google Play store
This version of Android virus spread via two apps in the official store:
- Wallpapers Blur HD;
- Booster & Cleaner Pro.
Researchers announced about these apps and Google removed them. However, they might spread in unofficial download websites or stores. Since McAfee research team discovered LeakerLocker,[2] these malicious apps were already downloaded thousands of times.
According to the analysis, “Wallpapers Blur HD” was downloaded 5,000 – 10,000 times. Meanwhile, the installation rate of “Booster & Cleaner Pro” is smaller. This malicious app was downloaded only from 1,000 to 5,000 times. The latter app has a pretty high rate. But judging from user’s reviews, it’s clear that they are fake.
However, “Wallpapers Blur HD” users note that the application requires access to irrelevant data, for instance, access to contacts, call logs or SMS. We want to point out that it’s important to read authorization agreements before installing the app.
If you chosen application seems to ask for lots of information that is not necessary for the operation, you should not give the access to such data. In this case, it’s obvious that wallpaper app does not need to get access to your contacts in order to operate.
It’s unknown what countries have suffered the most from this mobile malware. According to the primary data, the United States, Canada, and the United Kingdom[3] might be at the top of the list.
Uninstall LeakerLocker from your Android smartphone
Undoubtedly, LeakerLocker removal requires uninstalling “Wallpapers Blur HD” and “Booster & Cleaner Pro” from the phone. However, we also highly recommend scanning the system with security software and eliminate all malware-related components entirely.
However, malware can block FortectIntego or another your preferred security software. In this case, you may need to restart your Android to the Safe Mode by following these steps:
- Press the power button and press it until you see a menu. Click on the Power off option.
- You will receive a dialog window that asks to reboot the device to Safe Mode. Thus, click OK.
If you cannot reboot your device or remove LeakerLocker manually, please check manual Android removal instructions here.
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Mobile Malware. Techopedia. Technology dictionary.
- ^ Fernando Ruiz, ZePeng Chen . LeakerLocker: Mobile Ransomware Acts Without Encryption. McAfee Blogs. The blog about online security and recent cyber threats.
- ^ NoVirus. NoVirus. British website about malware and its removal.
