LeChiffre virus (Removal Guide) - updated Nov 2020
LeChiffre virus Removal Guide
What is LeChiffre virus?
LeChiffre ransomware – file-locking virus that is installed manually after an RDP break-in
LeChiffre ransomware is a relatively old data-locking malware from 2016. Back then, it was known for attacking three banks and a pharma company in Mumbai. Unlike many other viruses of this type, it is not distributed in the regular ways, such as malspam or exploits, but rather installed manually by the attackers. In other words, other ransomware use automatic procedures to reach out and later execute the malicious payload on the targeted machine, while the LeChiffre virus' executable needs to be launched by threat actors manually. Criminals are in search of vulnerable RDPs,[1] crack them, and forcibly enter the login password from a remote server.
As soon as malware is launched, the encryption process with RSA-1024 and AES[2] algorithms is performed, appending .LeChiffre extension in the process. Suchlike documents, pictures, videos, databases, and other files become inaccessible to the victims. In order to recover data, they are asked to email the attackers via the decrypt.my.files@gmail.com email and pay the ransom. Some victims claimed that they were asked for 1 Bitcoin in exchange for a unique key/decryption tool.[3] Paying the ransom is not recommended, however, as there is a fully working, free decrypter available from security company Emsisoft.
Fun fact: LeChiffre is a French word and means “the number,” although the verb version of it also means “encrypting” or “encryption.” While it is easy to assume that the attackers are of French origins, it is simply impossible to tell based on this fact.
| Name | LeChiffre ransomware |
|---|---|
| Type | Ransomware |
| Appearance | This cyber threat was first identified in mid-summer of 2015 |
| Activity | LeChiffre virus attacked three banking companies and one pharma firm in India, Mumbai, in 2016 |
| Appendix | Locked files are renamed after the encryption process. The .LeChiffre appendix is added to each filename |
| Cipher(s) | According to the ransom message, criminals employ the RSA-1024 and AES algorithms for successful data encryption |
| Ransom note | All information regarding the encryption process and ransom conditions is provided in the _How to decrypt LeChiffre files.html message |
| Payment demands | Users have reported that the malware demands for 1 BTC (approximately, $400-$450 at the time) to be transferred in exchange for the decryption software |
| Special offer | Hackers try to gather as many ransom payments as possible and try to give the users a look that they are reliable people. Regarding this purpose, the crooks claim that they will provide a free decryption key after 6 months post encryption if the victim does not want to pay |
| Crook's email | The hackers provide the decrypt.my.files@gmail.com email address as a way for users to contact them |
| Distribution | It is known that the ransomware virus is mainly distributed through hacked RDPs and then injected manually in the computer system by the cybercriminals |
| Malware elimination | Scan your system with SpyHunter 5Combo Cleaner or another reputable security application |
| Damage fix | Once you have uninstalled LeChiffre ransomware from your computer, try using FortectIntego to remediate Windows system and prevent future crashes, lag, errors, or another stability issues |
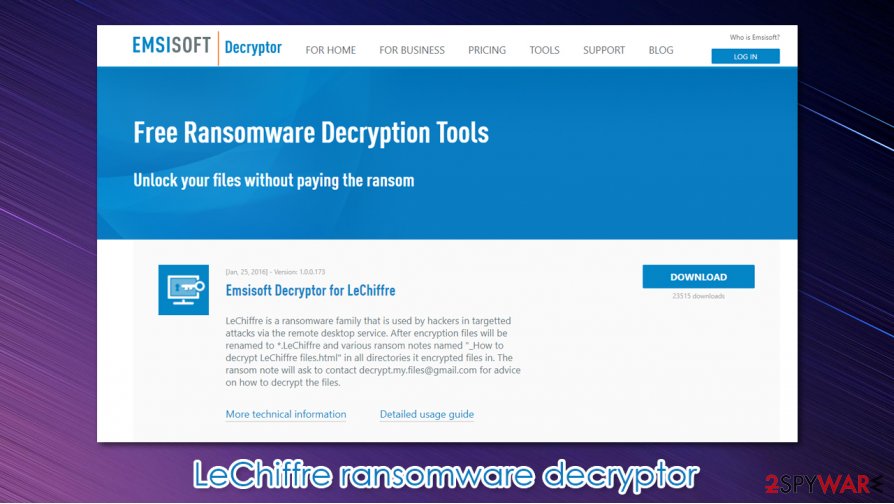
| Data recovery | Download Emsisoft's decryption tool or scroll down to the article to see other file restoring alternatives |
LeChiffre ransomware provides a non-typical ransom note through which criminals try to convince the victims that they are not scammers. As evidence, they offer to send them 1-2 encrypted files that contain less than 5 MB of space but no relevant information. Additionally, the crooks offer to send the victims a free decryption tool after six months if the users do not want to transfer any money. However, there is no need to pay a ransom or wait as the free decryption software has already been released by Emsisoft researchers.
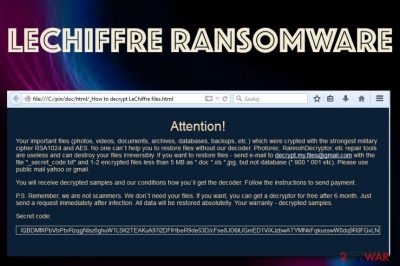
The encryption is made by encrypting the first and last 8192 bytes of the file and then attaching the malicious key to the file as a 32-byte blob. Continuously, LeChiffre ransomware developers might use remote servers to store both encryption and decryption keys so that the secret codes would be accessible only for the criminals themselves. After the encryption process is finished, LeChiffre ransomware leaves a note on the infected computer in the format of a .html or .txt file that usually looks like this:
Your important files (photos, videos, documents, archives, databases, dackups, etc.) which were crypted with the strongest military cipher RSA1024 and AES. No one can't help you to restore files without our decoder. Photorec, RannohDecryptor, etc repair tools are useless and can destroy your files irreversibly. If you want to restore files – send e-mail to decrypt.my.files @ gmail.com with the file “_secret_code.txt” and 1-2 encrypted files less than 5MB as *.doc *xls *jpg but not database (*.900 *.001 etc). Please use public mail yahoo or gmail.
You will receive decrypted samples and our conditions how you'll get the decoder. Follow the instructions to send payment.
P.S. Remember, we are not scammers. We don't need your files. If you want, you can get a decryptor for free after 6 month. Just send a request immediately after infection. Al data will be restored absolutelly. Your warranty decrypted samples.
Secret code:
%secret_code%
Continuously, LeChiffre virus is delivered through payload that looks like a usual executable file and ends up with a copy of itself (in the format of a .jpg component) in the Trash section. After that, the hackers can choose what type of files to encrypt no matter if it is all of them or just a specific number of data. Besides, the ransomware can lock all active data-storing sources not only the ones that are placed on the computer system directly.

Nevertheless, LeChiffre ransomware replaces the sethc.exe executable in the C:\Windows/system32\sethc.exe with cmd.exe to open a backdoor on the infected machine system. The original sethc.exe file can be executed by the user clicking the SHIFT key on his keyboard for 5 times in a row when the criminals can call the placed cmd.exe file and launch specific commands automatically by gaining remote access to the machine with no login data required.
Another interesting thing about LeChiffre ransomware is that the malware records relevant data about the machine's geographic locations and provides the country code number on the left of the graphical user interface. Additionally, criminals initiate remote communication by using an HTTP protocol and deliver important information through a Command & Control server.
The name “LeChiffre” might have different relations. Cybersecurity specialists claim that the word is French and translated means “the number”, however, if we emphasize the word as a verb or noun “chiffer”/”chiffrement”, it means encrypting/encryption. Another theory says that LeChiffre ransomware was named after the name of the villain called “LeChiffre,” meaning “the Cypher”, featured in the first James Bond movie.[4] The latter franchise inspired many cybercriminals.
If you see the ransom note or files encrypted with the .LeChiffre appendix added to each filename, it is actual proof that LeChiffre ransomware has attacked your computer. We do not recommend paying the ransom[5]. You cannot trust the cybercriminals – there’s no guarantee that they will put any efforts to help you get the files back. Plus, a decryptor for this ransomware has been created already.
However, you can also restore your files in case you have backup copies of them[6]. If you have such copies of your files, all you need to do is to remove the LeChiffre ransomware from your computer. Keep in mind that you should store backups on an EXTERNAL backup drive, because some viruses can reach your online data cloud storage and infect files that are stored there, too. Also, after you force the virus to vanish, you can try to fix the damage that has been left by the malware by employing a tool such as FortectIntego.
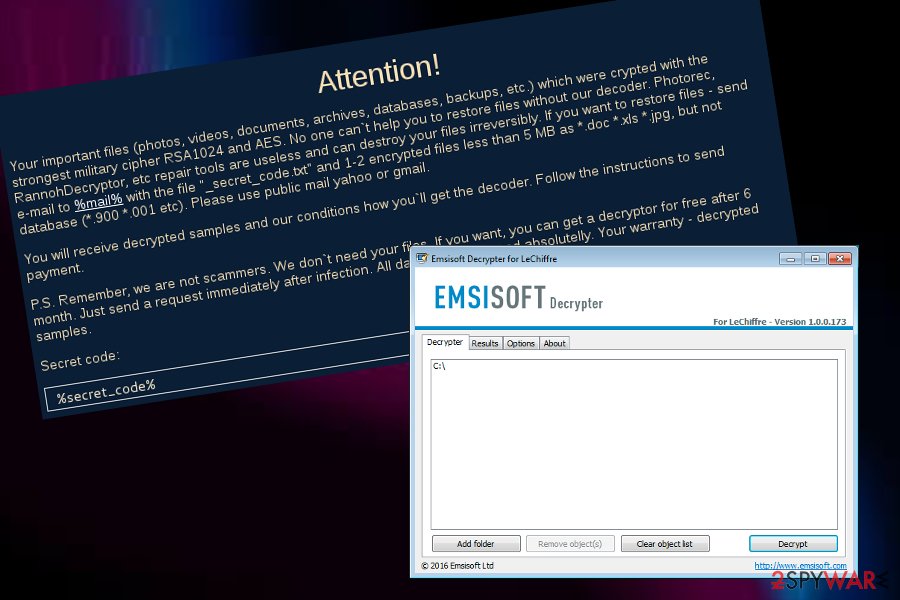
LeChiffre ransomware attacked banks and a pharma company in Mumbai. The newer version uses a password-guessing technique
Since the appearance of the ransomware in mid-summer 2015, the authors have not departed the ransomware market. Unfortunately, the virus has been continuously developed. Small business with a wider network of servers happens to be the preference of LeChiffre malware.
Additionally, news reports regarding LeChiffre virus activities have been flooding the cybersphere back in 2016 when the malware aimed to attack the Indian banks and a pharma company.[7] The criminals have demanded a ransom of 1 BTC on every infected machine which could have related in huge monetary losses (up to millions of dollars) if the ransom demands would have been taken seriously.
It has been also known that the newer version of LeChiffre ransomware utilizes a password-guessing technique. In other words, if you have been using a standard and a weak code such as “password123″[8], the cyber villains easily hack into the server remotely and then download the main payload of the ransomware. Therefore, netizens are advised to use long passwords comprised of characters and numbers. Password managers may also be a solution.
Distribution techniques for ransomware viruses
Security experts from Virusai.lt[9] claim that ransomware viruses spread through different channels. Some cybercriminals find ways how to distribute the malware via Remote Desktop Ports that do not have password protection or include weak passwords that are very easy to guess.
Crooks also prefer disguising their threats in spam emails. Users are deceived with the fake notifications supposedly sent from delivery companies such as FedEx/DHL, banking companies, or even law enforcement institutions. Once a suspicious message with the intention to infect users is received, people are encouraged to click on an infectious link or open a questionable attachment, mostly, an executable or word document.
Continuously, ransomware can be distributed through exploit kits, various outdated services, and products, other malicious threats such as trojans, or on p2p networks such as The Pirate Bay that provide various software cracks and have very low protection.
Avoid clicking on suspicious hyperlinks, downloading bogus products from the Internet, opening unknown emails and you will have a great chance of avoiding ransomware viruses. Besides, get an antivirus program that will ensure full system protection during your computing work.
Remove LeChiffre ransomware and restore files
According to the note of .LeChiffre file extension virus, you can get your files back for free after 6 months. This is unlikely to happen. There is no guarantee that the crooks will return the undamaged or all files after this period. Do not waste time and initiate automatic LeChiffre ransomware removal. Install and update your security applications, e.g. SpyHunter 5Combo Cleaner or Malwarebytes. Don't forget that your system might need an extra repair with FortectIntego or similar software to restore damaged Windows system files.
Only when the full elimination is completed, you can proceed to file recovery steps. In case, you encounter any problems and cannot remove LeChiffre ransomware, the below instructions will help you regain access. You can boot your machine in Safe Mode with Networking or activate System Restore to disable malicious changes.
Once LeChiffre is completely gone, you can start thinking about data recovery possibilities. Below you will find a few methods that might help you to restore your files back to their primary states. Additionally, we have added the original decryption tool released by Emsisoft at the end of this article that you might want to give a try to.
Getting rid of LeChiffre virus. Follow these steps
Manual removal using Safe Mode
To disable all malicious processes on your Windows computer system, complete the following guidelines.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove LeChiffre using System Restore
To boot your machine via System Restore and reverse the system back to its primary state, follow these steps.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of LeChiffre. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove LeChiffre from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by LeChiffre, you can use several methods to restore them:
Run Data Recovery Pro to restore some documents
If you did not have the back-up copies, this program, which locates missing and damaged files, might help you find the solution with the file restoring process.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by LeChiffre ransomware;
- Restore them.
Use Windows Previous Versions feature for data restore
If you have enabled the System Restore function in the past, you should give this method a try. Follow all instructions carefully to reach the best results possible.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Employ Shadow Explorer to unlock some individual files
The key advantage of the software is that it may recover the files according to the patterns of shadow volume copies. They are automatically created by every operating system. However, if the ransomware virus erased the copies of your encrypted data, this method might not be work.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Gladly, cybersecurity specialists have released an official decryptor for .LeChiffre files. You can find the tool released by Emsisoft here.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from LeChiffre and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Remote Desktop Protocol (RDP). Techopedia. Tech terms and definitions.
- ^ Cassius Puodzius. How encryption molded crypto-ransomware. WeLiveSecurity.News, views, and insight from the ESET security community.
- ^ Pit4. Virus LeChiffre. Avast Forum. Topics.
- ^ Hasherezade. LeChiffre, Ransomware Ran Manually. Malwarebytes Labs. Security Blog.
- ^ Carl Straumsheim. Your Data or Your Money. Inside Higher ED. Higher Education News, Career Advice, Jobs.
- ^ Eric Geier. How to back up your computer and files. My Dayton Daily News. Dayton in-depth, Investigative News.
- ^ LeChiffre Ransomware Hits Indian Banks, Pharma Company. Security Week. Relevant news articles.
- ^ Rob Price. The world's most popular password is depressingly easy to guess. Business Insider. Business and Tech News.
- ^ Virusai.lt. Virusai. Security and spyware news.





















