Leex ransomware (virus) - Decryption Methods Included
Leex virus Removal Guide
What is Leex ransomware?
Leex ransomware – a file virus that leaves victim data inaccessible until proper decryption software is used
Leex ransomware can infect any device that runs on Windows operating system. Since its demanded ransom amount is relatively low ($980) and it's spread primarily through file-sharing platforms, such as torrent websites, this cryptovirus is aimed at everyday computer users.
When this file-locker is downloaded, camouflaged as the latest game crack, pirated software, etc., and executed, it immediately starts its bidding. All non-system files (documents, databases, pictures, etc.) are encrypted with an army-grade coding algorithm and renamed by adding the .leex extension to original filenames.
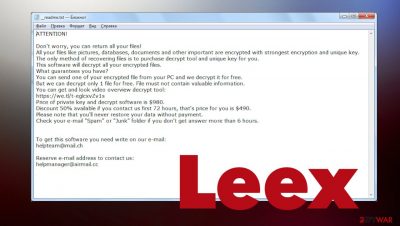
Please rest assured that file contents aren't modified. Thus after using a suitable decryption tool, you will be able to use them like nothing ever happened. Threat actors spreading this ransomware try to convince you into paying the ransom by using various persuasion techniques, which are seen on the _readme.txt ransom note found on the desktop:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-9CYW99VhUR
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpteam@mail.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
Don't believe a word written in this message as you could recover .leex files using alternative software. We're helping various cyber victims to get out of sticky situations for over 20 years. So we've compiled a lot of knowledge. This article will show you how to remove the ransomware, repair corrupted system sectors, and present the most plausible data recovery options.
As you can see from the ransom note, the criminals are bending over backward to push you into making rash decisions. They even offer a 50% discount on the ransom amount for victims that contact them by provided emails (helpmanager@airmail.cc or helpteam@mail.ch) within 3 days of the incident.

Succumbing to the demands of Leex file virus developers would finance their attacks and development of new, more advanced cyber threats and means to distribute them. We can't reiterate this enough – do not forward any money to the cyberthieves.
Instead, use our free, easy-to-use, illustrated instructions to remove the cryptovirus belonging to one of the most proliferate ransomware families – Djvu. It spews out new variations of their vile creations very frequently. This week it's the third one already. The prior variants were the Neer file virus and the Ddsg file virus.
| name | Leex file virus |
|---|---|
| Type | Ransomware, file-locker, cryptovirus |
| Family | Djvu/STOP |
| Infection symptoms | Personal files are locked and can't be opened; can't launch anti-malware software; ransom note appears on the desktop and in affected folders |
| Ransom note | _readme.txt |
| Spreading methods | This family is known for distributing threats via pirating services and during game cracking |
| Ransom amount | $980/$490 |
| Data recovery | Use our guides posted below to decrypt or recover your data |
| Virus elimination | To remove the ransomware, you must scan your device with a trustworthy anti-malware tool. Recommendations are displayed below |
| System health check | System files and settings are heavily modified when an infection starts encrypting files. These changes can be undone by using the time-tested FortectIntego all-in-one system repair software |
Leex ransomware removal and system repair guides
Before we begin the removal process, you need to extract all encrypted files from your device to a removable, offline storage device. That must be done, as there's a possibility that anti-malware software would flag those files as malicious and suggest you delete them.
Afterward, download the Malwarebytes security software, update it, and perform a full system scan. Its AV engine will detect all files and entries related to Leex file virus, isolate them, and suggest removing them. Please stick to what the security software recommends to delete.
Djvu family ransomware can sometimes block access to security-related pages, preventing you from downloading any necessary removal software and even disable such tools. In this case, you would have to download the recommended program and scan your device's system with it in Safe Mode with Networking. If you require help accessing it, follow these guidelines if you're using Windows 10/8:
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
Once you reboot your infected device in the Safe Mode with Networking, launch SpyHunter 5Combo Cleaner or another reputable antivirus, update it with the latest malware definitions and perform a full system scan to remove Leex virus and all its malicious components completely.
Anti-malware software is a must for all computer users that value their safety, privacy, and money. Making a habit of scanning your device at least a couple of times per week and updating its virus database could save you from similar perils in the future.
Once the threat is removed, you'll have to use another tool to fix all system irregularities caused by the ransomware when it's establishing persistence on your device. It causes various havoc – changes Registry values/keys, modifies host files, deletes Shadow Volume Copies,[1] disables certain software, etc.
There are tons of various system optimizers on the market, but many users praise the FortectIntego PC repair tool as one of the best and most versatile. It automatically repairs all system-related issues and even deletes tracking cookies stored by deceptive websites.
Therefore, cybersecurity specialists,[2] including us, highly recommend using it on a daily basis. It's free to try it out, so give it a go:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Once you remove Leex ransomware and fix all the problems regarding your PC's system, you can safely restore your data from backups as there's no chance for the infection to renew itself. If you haven't kept backups of your essential files, then proceed to the next step.
File decryption using free Emsisoft application
We've already mentioned that Djvu family ransomware is the most popular as it infects more devices than all other ransomware strains combined.[3] That's why Emsisoft is helping victims of these attacks to get out of this sticky situation without losing a dime.
They've developed a free decryption software meant to decypher files locked by Djvu ransomware. This tool is your best shot at regaining access to your data for free. There's no guarantee that it will work with Leex ransomware, but you should download it and try it out; maybe you'll be lucky:
- Download the app from the official Emsisoft website.
- After pressing the Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe, should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Leex ransomware Leex ransomware]()
- Press Decrypt.
![Leex ransomware Leex ransomware]()
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
We hope that this tool helped you to recover .leex files and that you can reaccess them. Suppose it didn't; please stay optimistic as there are other data recovery options. We've compiled the best of them and included them in our free instructions section right below this paragraph. If you have any questions, please feel free to contact our staff at any moment.
Getting rid of Leex virus. Follow these steps
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Leex and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Shadow Copy. Wikipedia. The free encyclopedia.
- ^ Dieviren. Dieviren. Spyware news and security.
- ^ Ransomware statistics for 2021: Q1 report. Emsisoft. Security blog.












