Locdoor ransomware (Removal Guide) - Decryption Steps Included
Locdoor virus Removal Guide
What is Locdoor ransomware?
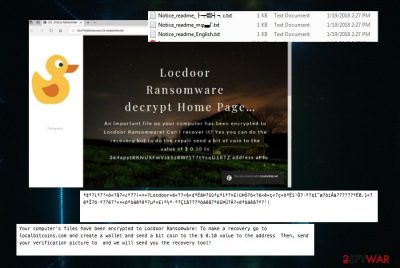
Locdoor ransomware is a cryptovirus that demands $0.10 for encrypted files
| Name | Locdoor/ DryCry |
|---|---|
| Type | Ransomware |
| Sub-type | Cryptovirus |
| Ransom note | Notice_readme_English.txt; Help!_How |
| Contact email | sealocker@daum.net |
| Also displays | HTML window “DryCry Ransomware Decrypt Page” |
| Distribution | Spam email attachments, other malware |
| Elimination | Use FortectIntego for the Locdoor ransomware removal |
Locdoor ransomware is not encrypting your files, as typical ransomware, so there are numerous speculations claiming that the program is still in development. However, this virus replaces some of the file extensions with the appendix .door. The ransom note claims that this infection locks your data and you need to pay the ransom in cryptocurrency worth $0.10. The virus developers demand you to pay in Bitcoin at the address localbotcoins.com and send a photo to sealocker@daum.net.
However, researchers[2] do not advise victims of this cyber threat to contact its developers in any way. Besides, paying the ransom is not useful since there is no encryption procedure initiated by the virus. Developers are seeking just to lure people with the small ransom, but there is no doubt that people behind the threat are not trustworthy in any way.
Locdoor/DryCry ransomware displays the following ransom note:
Your computer's files have been encrypted to Locdoor Ransomware! To make a recovery go to localbitcoins.com and create a wallet and send a bit coin to the $ 0.10 value to the address Then, send your verification picture to and we will send you the recovery tool!
The other version of the ransom note:
Bit coin is only allowed on localbitcoins.com! Send a bit coin of $ 0.1 value to at localbitcoins and send it to sealocker@daum.net with a certified photo! We will then email the recovery tool! Thank you! to Buy Recovery Tools.txt
You need to remove Locdoor ransomware, no matter its declared encryption is not real. keep in mind that this program was developed by crypto-extortionists, and you should get rid of this threat as soon as possible. It is important if you want to avoid any significant damage caused by this threat in the future. Keep in mind that ransomware can access important data and change system settings on your device immediately after the infiltration. Because of this fact, we do not recommend initiating Locdoor/DryCry ransomware removal manually.
You cannot be sure that this virus is not working in the background of your device. Perform Locdoor ransomware removal and then use FortectIntego to fix damage caused by this malware. This is a full procedure required for a full recovery after the infiltration of ransomware infection.
A malicious script is spread via spam emails
Silent infections can be spread in various ways. The most common for ransomware is spam email attachments. The malicious script of the ransomware can spread on your system from an insecure email that you open unknowingly. A payload dropper can be designed to install the direct malware script when you download and open a file attachment from an email. This malicious intruder can be this ransomware.
There is an opportunity to get various other malware like Trojans[3] which are designed to open backdoors or spread the ransomware directly on the device. You are downloading the file and installing malicious programs on the device at the same time. This is a silent infection you have no idea about this background process.
You can avoid these cyber infections if you pay more attention to processes happening on the device. If you are not waiting for an email, be aware that not every one of them is safe. Do not download suspicious attachments and try to scan those files before opening them on the computer.
Eliminate Locdoor ransomware from your device
To remove Locdoor ransomware once and for all, and get rid of its damage, you need to use reliable anti-malware tools like FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. This method ensures that all ransomware related files will be detected in no time and deleted from the system.
After a successful Locdoor ransomware removal, double-check if the system is clear. You can use the same anti-malware tools or virus termination tips provided by our experts. However, each of these methods should be implemented carefully, so make sure you follow every step in exact order.
Getting rid of Locdoor virus. Follow these steps
Manual removal using Safe Mode
You can try rebooting your device in Safe Mode with Networking to disable ransomware:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Locdoor using System Restore
System restore feature can also help if you are dealing with the dangerous Locdoor/DryCry ransomware:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Locdoor. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Locdoor and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Danny Palmer. Ransomware: Not dead, just getting a lot sneakier. ZDNet. Technology news.
- ^ Avirus. Avirus. Spyware news.
- ^ Margaret Rouse. Trojan horse. Techtarget. Search security.





















