LockBit 2.0 ransomware (Decryption Steps Included)
LockBit 2.0 virus Removal Guide
What is LockBit 2.0 ransomware?
LockBit 2.0 ransomware is a file-locking parasite that demands Bitcoins from its victims
LockBit 2.0 ransomware is a powerful computer virus that encrypts all non-system files on an infected device and then demands a ransom to be paid in Bitcoins. Some users agree to pay cybercriminals because they promise to give a decryption key – the only way to recover files. But actually communicating with attackers or sending them money is a bad idea and security professionals don’t recommend doing something like this.
By paying a ransom, victims encourage cybercriminals to continue such illegal activities. Moreover, there is no guarantee that hackers will actually send a decryption key to a victim. By doing what attackers demand, users only support their actions and risk being left without important files and money.
This is why if your computer is infected by this virus, you should simply remove the ransomware. And then, when the system will be completely clean, you can try to recover the locked files.
But let's start from the beginning. What is LockBit 2.0 ransomware[1] and how did it get into the system? This file-locking virus originates from MegaCortex and LockerGoga's notorious malware family. The first version appeared on the internet in September 2019. Cybercriminals behind it have improved ransomware[2] over the years by implementing new features and providing support to their affiliates. The new virus version encrypts Windows domains by using Active Directory group policies. It is important to note that this is the first ransomware that automates this process.
Authors even created their own leak site to promote the latest variant. They openly advertised the LockBit 2.0 affiliate program, offering hackers to make millions of dollars.[3] The leak site also provides important information about the features of the new version. One of the most interesting features is the capability to use group policy update to encrypt a Window domain.
| name | LockBit 2.0 ransomware |
|---|---|
| Type | Ransomware, file-locking parasite |
| Infection symptoms | Documents, pictures, videos, archives, and other personal files are renamed and locked; a ransom note appears on the desktop and in affected folders; can't open security-related websites |
| Appended file extension | Non-system data is renamed by appending the .Lockbit extension to original filenames |
| Ransom note | RESTORE_MY_FILES.txt |
| Distribution | Downloads from file-sharing platforms, fake Flash Player updates |
| Data recovery | A possible decryption method is described in the article |
| Elimination | Instead of paying the cybercriminals, remove the virus and use alternative data recovery options |
| System health check | Use the FortectIntego PC repair tool to fix all system irregularities that the infection might have caused |
This means that when hackers enter the target network and compromise the domain controller, the ransomware can spread on the domain. The infection creates new group policies on the domain controller that migrates to all devices in the Windows domain. The policies disable security features, such as Microsoft Defender and alerts, and prevent the system from providing samples to Microsoft to avoid detection. So, this ransomware is more advanced than before.
Of course, this infection is still similar to other ransomware – it locks all personal files on the infected computer. Once the virus completes the encryption process, the victim can no longer open affected files. All non-systemic data is locked: photos, videos, documents, etc. In addition, all encrypted files receive a new extension – .Lockbit.
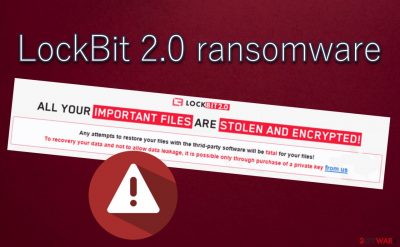
The virus then automatically drops the ransom note on the desktop and into the affected folders. Cybercriminals try to convince the victims that the only way to recover locked files is to pay a ransom. Here's the whole text from the ransom note:
LockBit 2.0
All your important files are stolen and encrypted!
Any attempts to restore your files with the third-party software will be fatal to your files!
To recover your data and not to allow data leakage, it is possible only through purchase of a private key from us.
Attention!
Decoding.at may be blocked. We recommend using a Tor browser (or Brave) to access the TOR site.
Do not rename encrypted files. Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to ours).
All you stolen important data will be loaded into our blog if you do not pay ransom…
Of course, as we've already mentioned, you shouldn't rely on hackers. The best solution would be to remove the ransomware and then try to recover the files in other ways. If your computer is infected with this virus or other ransomware, just keep reading and use our tips to successfully fix the device.
How to remove LockBit 2.0 ransomware and recover affected files
To resolve this issue, you should get rid of the virus first. Manually eliminating such a serious threat is not recommended. You should use SpyHunter 5Combo Cleaner, Malwarebytes, or a similar antivirus program that will scan the entire system easily and quickly. After a system scan, security software will automatically remove the ransomware and other viruses that it may find on your computer.
After that, you should make sure that the device is completely clean and that there are no suspicious files or system changes left on it. Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is.
It's usually hard to spot all the changes, but if you don't remove them, you might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required. We recommend using FortectIntego – a useful tool that will fix the registry files, various errors, and other system problems.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
If your computer is completely clean, you can start the .Lockbit file recovery process. Unfortunately, if you do not have proper data backups, it can be difficult to recover files. You might lose access to important data permanently. But paying cybercriminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool. So, it is not worth sending them Bitcoins.
Although this situation sounds terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![LockBit 2.0 ransomware LockBit 2.0 ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Charlie Osborne. A deep dive into the operations of the LockBit ransomware group. ZDNet. Technology news.
- ^ Josh Fruhlinger. Ransomware explained: How it works and how to remove it. CSO. Security news.
- ^ MalwareHunterTeam. LockBit 2.0 ransomware says:. Twitter. Microblogging and social networking service.










