Loplup ransomware (virus) - Free Instructions
Loplup virus Removal Guide
What is Loplup ransomware?
Loplup ransomware is a Windows virus that may result in permanent file loss
Loplup virus is a type of malware that focuses on money extortion and can do significant damage to those affected. It enters users' machines through phishing emails or software installers, or other methods that use some form of phishing[1] techniques. It immediately looks for valuable files, such as documents and pictures, and locks them with encryption algorithms RSA and AES.[2]
Each file is appended with the .loplup.[ID] extension and given blank icons. After the encryption process, users cannot access their personal data on the system. It's worth noting that the data is not lost, however. According to the cybercriminals' ransom note “!!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT,” the only way to restore files is by contacting them via the qTOX app or loplup@cock.li email. Of course, the “favor” is not for free, as crooks would ask to pay a certain amount of bitcoin in return for a decryptor.
We strongly advise against paying Loplup ransomware authors, as you may never see the promised key. Instead, follow this guide and attempt to recover your files using alternative methods. Keep in mind that this process should not be rushed and performed in the correct order, so be careful.
| Name | Loplup ransomware |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Family | Zeppelin |
| File extension | .loplup.[ID] |
| Ransom note | !!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT |
| Contact | qTOX app or loplup@cock.li email |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Perform a full system scan with SpyHunter 5Combo Cleaner or another reputable security software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
The ransom note explained
A ransom note is essential to any cybercriminal activity, as it provides the victim with all the necessary contact information needed to arrange payment. Usually, the note can be found on the desktop or will automatically open once data encryption is complete. Various file types can be used for the note, although the most common one is the basic text (TXT) file which could be opened easily with the default Windows program Notepad.
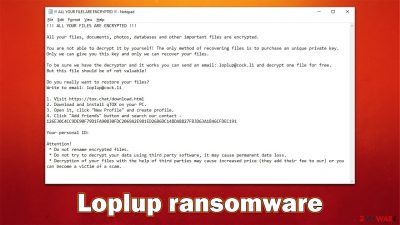
The ransom note of the Loplup virus reads the following:
!!! ALL YOUR FILES ARE ENCRYPTED !!!
All your files, documents, photos, databases and other important files are encrypted.
You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key.
Only we can give you this key and only we can recover your files.To be sure we have the decryptor and it works you can send an email: loplup@cock.li and decrypt one file for free.
But this file should be of not valuable!Do you really want to restore your files?
Write to email: loplup@cock.li1. Visit https://tox.chat/download.html
2. Download and install qTOX on your PC.
3. Open it, click “New Profile” and create profile.
4. Click “Add friends” button and search our contact – 126E30C4CC9DE90F79D1FA90830FDC2069A2E981ED26B6DC148DA8827FB3D63A1B46CFDEC191Your personal ID:
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
It is not uncommon for cybercriminals to offer users a test decryption service. By feigning trustworthiness, they put themselves in a position where the user may be more likely to pay them in hopes of retrieving their data.
However, you should not give in to this proposition, as there are always risks when communicating with attackers. Even if the ransom note might seem friendly, it is not the case at all, as these people are the reason why your files are locked in the first place. Thus, you are risking losing your money as well. You may also get attacked by ransomware again in the future since crooks already know you are willing to pay.[3]
Removal instructions and data recovery steps
Understandably, most users immediately panic when they discover that their files have been locked by ransomware and can no longer be accessed. However, this reaction will not fix anything because the infection has already occurred. In fact, panicking may cause victims to make mistakes which could lead to even more data loss. To avoid additional damage, it is important to follow the correct steps in order.
1. Disconnect from the internet and remove the Loplup ransomware virus
Usually, cybercriminals set up a remote connection with the infected Windows device through what is called a Command & Control server. The communication occurs over the internet, so it's key that the machine is disconnected from any networked connections. Here's how to do just that quickly and easily:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
After your computer can no longer access the internet, it is time to remove the infection from your system, and for that, we recommend using trustworthy security software such as SpyHunter 5Combo Cleaner or Malwarebytes. Security software can locate and remove all the malicious files at once, so you can be sure that your system is clean and ransomware-free.
Keep in mind that some ransomware may self-delete after performing the encryption process, so anti-malware may not find anything. Nonetheless, it is important to make sure that the infection is completely contained and terminated before proceeding with the next steps.
2. Repair system files
You should maintain the health of your system. Malware is a sophisticated program that uses complicated methods to subvert inherent security and modify Windows' behavior. Some system components may be unintentionally destroyed during an infection, which might result in software or the computer crashing or displaying errors. This is especially typical after malware has been removed from the compromised machine since antivirus software can't repair broken system files because of malware.
Thus, we recommend you use an automatic solution that would remediate your system and remove any damage done by ransomware. Follow these steps:
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
3. Restore files
Many users believe that their personal files will go back to normal as soon as they finish scanning their system with security software. However, this is false because anti-malware is not designed to restore ransomware-locked files – its main goal is to delete infected files from the system in order to prevent any future damage.
Finally, there are people who think that data damaged by ransomware is irretrievably ruined, which isn't correct. It's possible to restore it through the use of a unique decryption key (which cybercriminals have) or other methods – waiting for free decryption software to be released is one option. If such a program is ever created, the following links may be useful in locating a decryption tool:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

While it is unlikely to restore all encrypted files using recovery software, it is not impossible. For some users, this option may work very well, while for others – not so much. Before you proceed, make sure you copy the encrypted files to ensure they won't get corrupted during the recovery process:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Loplup ransomware Loplup ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ What is encryption? | Types of encryption. Cloudflare. The Web Performance & Security Company.
- ^ Kevin Townsend. It Doesn't Pay to Pay: Study Finds Eighty Percent of Ransomware Victims Attacked Again. Security Week. Cybersecurity News, Insights and Analysis.












