Mew767 ransomware (Removal Guide) - Improved Instructions
Mew767 virus Removal Guide
What is Mew767 ransomware?
Mew767 ransomware – an aggressive infection that has been attacking users already for a month
Mew767 ransomware appears to be the first version of Go ransomware that employs a graphical user interface in the executable file that is responsible for data encryption. According to cybersecurity researchers from Malware Hunter Team,[1] this malicious string has been active for about a month and has been targetting both regular users and business organizations. Even though it appears that Mew767 ransomware is still like any other of its kind and does not have a more complex module than a usual ransomware virus, it still can be really dangerous and force users to face big monetary losses.
Malicious actors provide a short text message that announces the recent encryption. These people encourage victims to write them via the given email address as this is claimed to be the only way to return files. Mew767 ransomware developers try to scare users that they will permanently damage the encrypted files if they try to restore them independently.
The encryption process is activated by launching a specific executable and targetting all files and documents that are discovered on the infected Windows computer. Afterward, some type of extension gets appended to each filename and marks the components that were touched by Mew767 virus. The files can be reversed only by activating the decryption tool that has been created specifically for them.
| Name | Mew767 ransomware |
|---|---|
| Type | Ransomware/malware |
| Family | This malicious string is a variant of the Go ransomware family |
| Founder | MalwareHunterTeam has announced their findings on the Twitter social platform |
| Target | The ransomware virus has been targetting English-speaking users, according to the ransom note. Cybersecurity experts discovered that the malware has already hit not only regular users but also various businesses and has been active for around a month |
| Encryption | Malicious actors employ unique encryption ciphers such as AES, RSA, and SHA for locking up all the files and documents that are found on the infected Windows computer system. The ransomware virus launches a specific executable for the encryption process |
| Distribution | Most of the time, ransomware infections are distributed through email spam campaigns and malicious email attachments. However, these parasites can also get delivered through infectious hyperlinks, adverts, software cracks, and hacked RDPs such as the TCP port 3389 |
| Removal | If you have discovered Mew767 virus on your Windows computer system, you should get rid of the malware as soon as possible. Use reliable antimalware software for completing the process |
| Recovery | Try restoring your locked files by employing alternative software that we have added to the end of this article |
| Fix | If you have encountered any damaged areas on your computer system, you can try repairing them with a tool such as FortectIntego |
Mew767 ransomware is a malicious parasite that affects different areas of the Windows computer. When entering the system through infectious attachments or other products such as cracked software, the malware alters Windows Registry keys and adds malicious processes into the Windows Task Manager directory. Some of these tasks aim to carry out the encryption process by targetting different types of files and documents that are discovered on the machine.
Mew767 ransomware is capable of capturing all kinds of components such as images, audios, videos, word documents, executables, powerpoints, databases, etc. The encryption process proceeds by launching a specific cipher such as AES,[2] RSA, or SHA. Afterward, all the filenames receive a specific appendix marking that the components have been locked for good. This means that you are not able to reverse your files without a proper decryption key.
Mew767 ransomware developers store both encryption and decryption keys on remote servers where they are unreachable for other people. This way crooks can ensure that they are the only ones that hold the software and this gives a chance to manipulate the victims by demanding ransom payments. Even though the ransom message does not include any particular information about monetary demands, they can vary anywhere from $100 to $1000 or more.
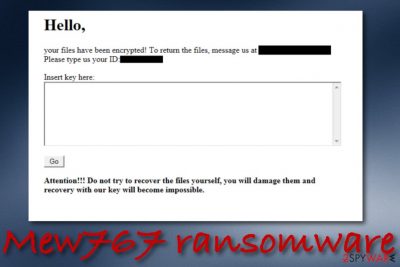
Nevertheless, cybercriminals are orientated toward receiving cryptocurrency transfers. These people often urge for Bitcoin, Monero, Ethereum, or another type of digital currency that allows the entire payment process to stay safe and untrackable. Some even add particular wallets to which the price should be transferred. Even though Mew767 ransomware does not provide any ransom demands in the note, it urges to write the criminals if wanting to return the locked files:
Hello,
your files have been encrypted! To return the files, message us at
Please type us your ID:
Insert key here:
Attention!!! Do not try to recover the files yourself, you will damage them and recovery with our key will become impossible.
Furthermore, Mew767 ransomware might try to harden the file recovery process for the users by eliminating the Shadow Volume Copies of encrypted files by running PowerShell commands. Nevertheless, the malware might be programmed to permanently damage the Windows hosts file. This way the users will be prevented from visiting security-related websites and forums where they could find valuable information on the malware removal process and data recovery tips.
Even though the main goal of Mew767 ransomware is to lock up all the files that are found on the computer system and urge a ransom for them, this cyber threat can also be programmed to open backdoors for other malicious infections. A lot of ransomware viruses are known for their ability to install hazardous payload into computer systems. Here is a high risk of getting infected by a dangerous virtual parasite such as a Trojan horse.
Mew767 ransomware removal is the main task that you should complete ASAP while dealing with this cyber threat. Prevent the ransomware virus from installing other malicious infections into the Windows computer system by using reliable software to eliminate it. Make sure that you employ an expert-tested piece of software that is able to find and eliminate the virus. Also, if you have discovered any damage on your Windows machine, try repairing it with FortectIntego.
When you remove Mew767 ransomware, it is time to think about some data recovery alternatives. We do not recommend paying the demanded ransom price to the cybercriminals as there is a high risk of getting scammed. Rather than risking to lose a big amount of money and being left with nothing, you should get rid of the malware properly and try some data restoring techniques that our cybersecurity experts have provided at the end of this article.
The most popular places where you can discover ransomware
Cybersecurity experts from LosVirus.es[3] state that ransomware viruses are mostly distributed through email spam campaigns and the malicious attachments that come attached to the email messages. Most of the time, cybercriminals force users to believe that an official organization or business company is contacting them and providing important information in the email message and the attached file/document. However, this is just a trick used to convince potential victims into opening the clipped attachment.
A piece of advice would be to manage all of your emails with big care as you cannot know where malicious attempts might be hiding. What you should do is always identify the sender, make sure that the email message is not coming from some type of questionable email address. Then, check the entire message text for possible grammar mistakes and note that responsible companies would not send their emails full of mistakes. Last but not least, do not open any attachments without scanning them with antivirus software first.
Additionally, ransomware infections can get delivered through hacked software that is provided on websites such as The Pirate Bay. Avoid downloading software, movies, and other products from such questionable sources as they are high at risk of malware infections. Also, ransom-demanding parasites can get distributed through hacked RDPs such as the TCP port 3389. This often happens if the user fails to secure the RDP with a strong and reliable password. Other ransomware spreading places include:
- Malvertising.[4] The malicious payload can get easily spread through malware-laden advertisements that pop out on unprotected websites.
- Hyperlinks. There are also many infectious hyperlinks online that can relate in the installation of ransomware.
- Fake updates. False flash player or JavaScript updates often pretend to be regular upgrades that the user is encouraged to download immediately. However, do not agree with any updates without checking them officially first.
Advanced removal guidelines for Mew767 ransomware
If you have been dealing with this ransom-demanding parasite recently, you should not postpone its elimination process as things might only get worse. Mew767 ransomware removal is necessary if you want to avoid the risk of receiving other malicious infections. Also, note that if you do not get rid of the malware first, you will not be able to recover your data properly. For the elimination, employ only reliable antimalware tools.
When you remove Mew767 ransomware, it is time to find possibly-damaged objects on your Windows computer system by using tools such as SpyHunter 5Combo Cleaner or Malwarebytes. If this type of software discovers any corrupted components, you can try repairing them with FortectIntego. Afterward, you can continue with the data recovery process. We have provided some alternative tools at the end of this article that might be helpful while trying to recover at least some of the locked files.
Getting rid of Mew767 virus. Follow these steps
Manual removal using Safe Mode
To get rid of various malicious processes that are preventing you from terminating the ransomware virus, you should apply Safe Mode with Networking to your Windows PC:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Mew767 using System Restore
To properly deactivate the malware and bring your computer settings back to normal, complete the following steps to enable System Restore on your device:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Mew767. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mew767 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.File recovery is not an easy step when we are talking about documents that have been compromised by a ransomware virus. However, there is never the need to rush and pay the demanded ransom price as there is a high risk of getting scammed and receiving nothing for the money. Regarding this fact, our security experts decided to provide you with some data recovery alternatives that can turn out to be really helpful. Check the software below.
If your files are encrypted by Mew767, you can use several methods to restore them:
Employing Data Recovery Pro might be the right step toward file restoring.
If the ransomware virus has encrypted your files and documents and you do not know how to reverse them, you should try using this piece of software.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mew767 ransomware;
- Restore them.
Windows Previous Versions feature can help you with data recovery.
If you have been searching for a tool that would help you with file recovery, this particular software might be the one. However, make sure that you have launched System Restore in the past.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use Shadow Explorer and recover some files.
If the ransomware virus did not permanently damage or delete the Shadow Volume Copies of your files, try using this software for file restoring, otherwise, it might not operate properly.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Cybersecurity experts are still working on the official decryption key.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mew767 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Malware Hunter Team. About Mew767 ransomware. Twitter. Malware Hunter Team.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ NOTICIAS SOBRE SEGURIDAD Y VIRUS. LosVirus. Security and spyware news.
- ^ What is malvertising?. Malwarebytes Labs. Blog.





















