Mmrac ransomware (virus) - Free Guide
Mmrac virus Removal Guide
What is Mmrac ransomware?
Mmrac ransomware is a malicious program that encrypts all personal files on your system
Mmrac is a ransomware-type virus that was first spotted attacking Windows computers in January 2022. Just like any other malware of this kind, it gains access to a Windows computer by using some type of phishing or social engineering (usually infected emails), although insufficient security measures such as weak RDP[1] passwords, installed vulnerable software, lack of effective anti-malware software, can also be the main culprits of the infection.
As soon as it manages to enter the system, it does not immediately begin data encryption, as it needs to make several changes for that to happen successfully – removal of Shadow Copies, registry modification, establishing of malicious process, to name a few. After compromising Windows, Mmrac ransomware begins to look for files to encrypt, as its main goal is not to destroy system files but rather prevent users from accessing their documents, pictures, videos, etc.
Suchlike files are then rendered inaccessible, and they receive a .Mmrac extension. They are also stripped of their original icons, so it is very easy to notice that something is not right. Upon trying to open an encrypted file, victims would be shown an error, regardless of which program they would try to open them with. Data encryption and infection processes usually last mere seconds, so interrupting them is almost impossible.
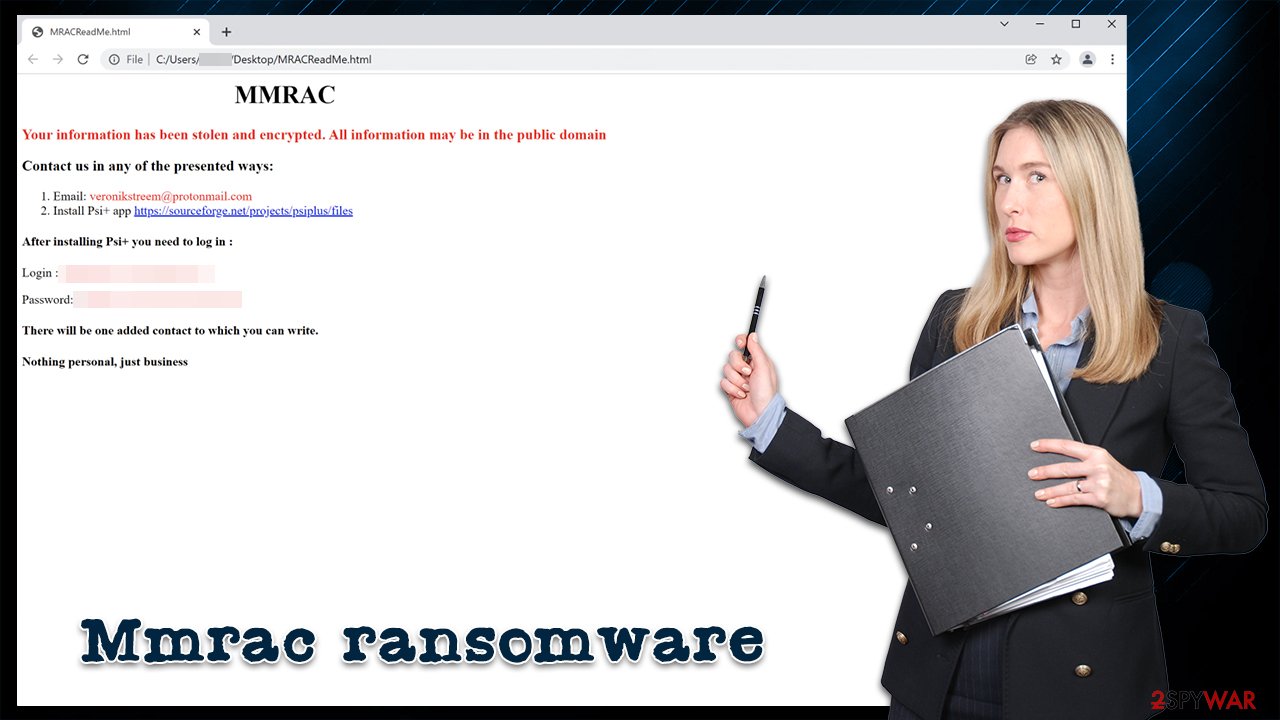
Once the data is locked, the virus then generates a ransom note titled MRACReadMe.html and places it on the desktop and other locations. Essentially, it is the main communication method between the attackers and users, as it holds the contact details and other important information within. In this case, crooks are asking their victims to either send them an email via veronikstreem@protonmail.com or contact them via XMPP client Psi+, for which they are given login details.
| Name | Mmrac virus |
|---|---|
| File extension | .mmrac is appended to each of the non-system files |
| Ransom note | MRACReadMe.html |
| Contact | veronikstreem@protonmail.com and Psi+ app |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files which might result in crashes, errors, and other stability issues. This can mean that Windows reinstallation might be necessary. Alternatively, FortectIntego PC repair can fix any of such damage automatically by replacing system corruption |
Ransom note analysis
Ransomware has a relatively long history under its belt and has been evolving for years now. What initially was a screenlocker is now something that manages to snatch people's files from them – which could be extremely valuable – and hold them behind a ransom request. These are always paid in Bitcoin or another cryptocurrency for anonymity purposes, and the size of these ransom payments varies greatly.
When it comes to the Mmrac files virus, it seems like the attackers took the most recent trend of firstly copying personal files before encrypting them. This action can be particularly damaging to companies and businesses, as companies' secret files could be leaked to competitors and other unauthorized parties. This is also one of the reasons why ransomware attacks are also considered data breaches – personal information of employees or customers can also be stolen. Malware can also affect the security of the breached systems, servers, and networks and make them more vulnerable to other attacks.
According to the ransom note, there is “nothing personal” about the attack, and it is all about money extortion:
MMRAC
Your information has been stolen and encrypted. All information may be in the public domain
Contact us in any of the presented ways:
Email: veronikstreem@protonmail.com
Install Psi+ app https://sourceforge.net/projects/psiplus/filesAfter installing Psi+ you need to log in :
Login :
Password:There will be one added contact to which you can write.
Nothing personal, just business
While cooperating with the cybercriminals might seem like a good idea initially (they might not ask a lot for decryption in some cases), it is actually the worst idea to follow. They might never provide you with a decryptor after you send them money. In fact, they might not even have a working one or send you an infected file instead. The act of paying a ransom also reinforces the idea that the illegal business works as intended and only encourages crooks to create more malware and infect more people.
Removal and file recovery
Ransomware victims are often puzzled on how to proceed after being infected, as they usually never had to deal with it before. It is true that certain procedures are to be followed in order to minimize the damage caused by the malware, and we are here to help you to follow the procedure correctly.
The first step that is absolutely vital for the correct Mmrac virus removal process is to disconnect the computer from the internet and the network if it was connected to it. Ransomware operators can send the commands for the virus to perform additional actions or even upload additional modules or payloads.
If your computer is not connected to a network, you can simply remove the ethernet cable or disconnect yourself from WiFi via the taskbar. Alternatively, you could simply perform the following actions to disconnect all the machines at once:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once your system is disconnected from the device, you can then perform a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security software to eliminate the infection. It is true that ransomware can often self-destruct after performing its job of data encryption, although it might not always be the case. Likewise, ransomware is often propagated along with other computer infections (mostly data-stealing Trojans), which can cause additional damage to personal safety and computer security.
The final step is to attempt to recover the locked data. There are a lot of misconceptions among users about how the encryption works and what the files actually become once they get affected by ransomware. Some people believe that they can restore their files as soon as they scan their computer with anti-malware or that their files are permanently corrupted as soon as they get encrypted – none of these are true.
The truth is that encryption algorithm such as AES or RSA,[2] (or a combination of those) if applied correctly, is extremely secure and can't be broken even by the most sophisticated supercomputers. That being said, it does not mean that the data affected is corrupted – it simply needs a unique key, which is held on the attacker's servers.
This is why the best mitigation technique is to make secure backups for personal files. Unfortunately, many users are unprepared for the attack and rarely have working backups ready. In this case, there are few chances of restoring the encrypted Mmrac files successfully unless a decryptor is created by security researchers. Nonetheless, you could try using recovery software which could be successful in restoring at least some of the lost data:
Note: before you proceed with this step, please make copies of the original encrypted files to ensure they don't get corrupted.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Mmrac ransomware Mmrac ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors,[3] which allows the keys to be released by the public – this is usually done by reputable security vendors. Here are a few links you might find useful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Additional tips
After you have removed malware from your system and attempted to recover your files, there are a few other things you could do. First of all, you should report the incident to the authorities.
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors.
Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial. Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you come from. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

Finally, you should take care of your system integrity. Once malware compromises a Windows computer, it might damage some system files, and anti-malware is incapable of replacing or repairing them. As a result, ransomware victims might later experience all sorts of inconveniences related to computer performance – crashes, errors, lag, and similar issues are common. While reinstalling the system would fix these problems, it is not always the optimal solution.
Instead, we recommend performing a full system scan with powerful PC repair software that could fix damaged system components automatically and also clean the junk files for better performance.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Remote Desktop Protocol. Wikipedia. The free encyclopedia.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Global software company.
- ^ Europol takes down VPNLab, a service used by ransomware gangs. The Record. Daily breaking news.











