More_eggs virus (Removal Instructions) - Free Guide
More_eggs virus Removal Guide
What is More_eggs virus?
More_eggs virus is a backdoor Trojan that is utilized by Cobalt Group and other criminal gangs to attack corporations and regular users

More_eggs virus is a backdoor written in JavaScript programming language. Also known as Terra Loader and SpicyOmelette, the malware allows malicious actors to perform various tasks on the host machine, including executing shell commands, downloading or deleting files/payloads, executing code, transferring information, etc. In other words, thanks to More_eggs malware, the attackers can control the machine over an HTTPS-based C2 protocol and, although the functionality of the commands is limited, it is enough to initiate the download of more sophisticated payload.
More_eggs backdoor is used to target all versions of Windows machines, and several variants of it have been released, including version 2.0 and 4.4. The malware has been prevalent for at least a couple of years (first described by Trend Micro specialists in August 2017),[1], and has been actively distributed with the help of malicious spam email attachments or hyperlinks that reach out financial organizations or regular PC users. More_eggs malware has been one of the main assets of financially-motivated Cobalt Group[2] and FIN6 cybercriminal gangs, which are also believed to be involved in a highly-evasive PureLocker ransomware and open-source software Cobalt Strike delivery campaign.
More_eggs backdoor is sold on the Dark Web as Malware-as-a-Service, i.e., anyone can buy and use the payload as long as the developers receive a predetermined percentage of the profits obtained from malware attacks. Thus, there is a high chance that there are multiple other malicious actors that distribute the More_eggs virus.
| Name | More_eggs |
|---|---|
| Type | Backdoor Trojan |
| Also known as | Terra Loader and SpicyOmelette |
| Associated crybercriminal gangs | Cobalt Group, FIN6 |
| Delivery method | Malicious actors mostly deliver the malicious payload of the backdoor in a sophisticated and multi-stage malicious email campaign |
| Risks | Trojan Backdoors are especially dangerous as they can be used for a variety of malicious activities, including the delivery of secondary payloads, data tracking, retrieving commands from cybercriminals, and much more. Consequently, users might suffer from money loss, identity theft, loss of personal data, etc. |
| Symptoms | Trojans are programmed to remain on the system without being detected – they rarely emit any symptoms and usually remain hidden on the infected systems as long as possible |
| Termination | In some cases, More_eggs trojan might self-delete. Nevertheless, it is known that bad actors load the host machine with other payloads that can remain on the system for weeks or even months. Regardless of what type of infection you are dealing with, you should employ reputable anti-malware software to terminate all the malicious components from your system |
| Recovery | Malware might cause significant damage to system files, which might prompt the need to reinstall the operating system due to crashes or other malfunctions. To avoid that and repair various system files affected by malware, we suggest using PC repair software FortectIntego |
More_eggs virus might be a high threat to any computer user, as a backdoor is designed to remain on the system undetected for as long as possible. During its operation, it can send the attackers the required information, such as the installed anti-malware program, IP address, computer name, OS versions, and other data. Due to this, More_eggs removal might be fairly hard, although most up-to-date security programs should be able to take care of its elimination in the Safe Mode environment.
Delivery process of More_eggs backdoor trojan
In 2018, More_eggs was closely analyzed by Talos Intelligence experts, that described the malspam campaigns as “highly sophisticated and evasive”:[3]
Simple campaigns typically use a single technique and often embed the final executable payload into the exploit document. However, more complex campaigns require meticulous planning on the part of the attacker and include more sophisticated techniques to hide the presence of the malicious code, evade operating system protection mechanisms and eventually deliver the final payload, likely to be present only in the memory of the infected computer and not as a file on the disk.
Several different More_eggs malware delivery campaigns were observed in the past, although most of the time, a fake (but legitimately-created) Linkedin account is made by the attackers. Using this account, the attacker delivers an email to a particular user of the targeted organization – it contains a subject line “Hi [Name], please add me to your professional network.”[4]
More_eggs actors pretend to offer users a new job in a similar position with allegedly much better prospects.[5] In some cases, the emails are embedded with a Google Drive link, which, once clicked, displays a message “Online preview is not available” and prompts users to click on another link, that is actually malicious. The URL, once clicked, automatically downloads a WSF file inside a ZIP archive. Once executed, it would initiate the More_eggs virus infection process.
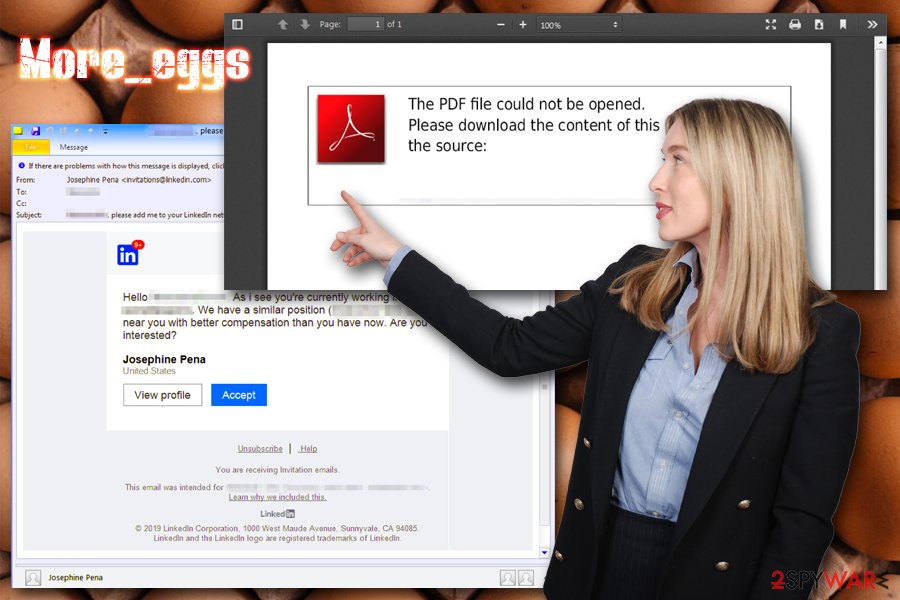
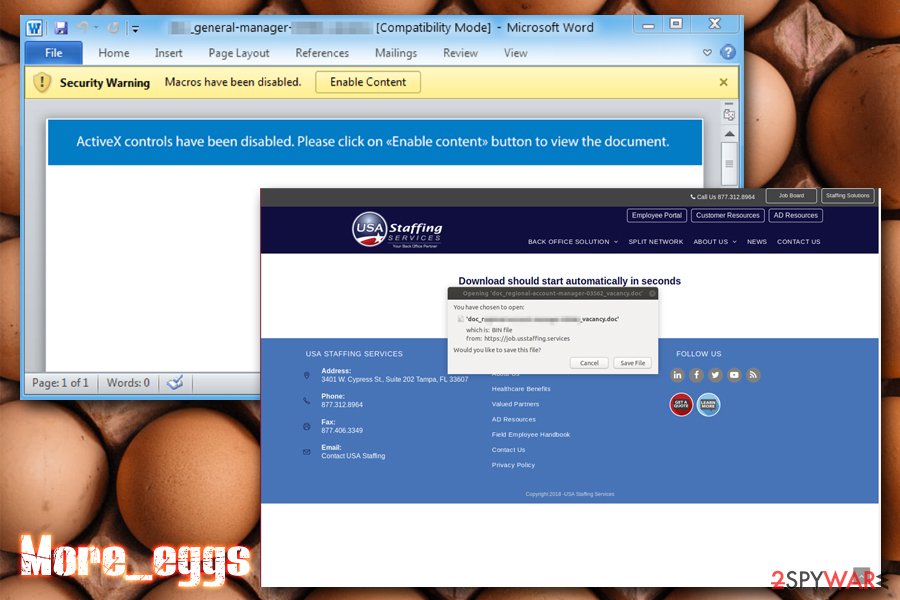
Other times, attackers opted to direct potential victims to sites that use stolen branding, which makes the campaign much more believable. Users were prompted to download the alleged job description inside an MS Word file, which, once opened, would not display anything until the “Enable Content” button is pressed – Macros enabled.
The mentioned documents are often used to abuse software vulnerabilities, including:
- CVE-2017-0199;
- CVE-2017-8570;
- CVE-2017-8759;
- CVE-2017-11882;
- CVE-2018-0802;
- CVE-2018-8174.
More_eggs malware performs multiple actions after infiltration
Upon infiltration, the More_eggs virus establishes a connection between a compromised machine and the attacker's Command and Control server. After that, it uses WMI and PowerShell commands to move laterally and escalate privileges on the impacted system. This method is often known as “living off the land”[6] by security experts and is often associated with fileless attacks – malware resides in the system's memory instead of the hard drive, complicating AV detection. Nevertheless, most of the up-to-date security applications should be capable of detecting post-infection activities and remove More_eggs without much trouble.
More_eggs Trojan also allows the attackers to download secondary payload, such as Mimikatz post-exploitation tool. It will enable them to extract sensitive information from the host machine and access various systems with the help of harvested credentials, resulting in privilege escalation and further movement within the IT infrastructure.
Process injection is not the only sophisticated ability of More_eggs virus, however. Several malware components, along with communications between the host machine and the malicious server, are encrypted by such encryption algorithms like RC4. Additionally, the backdoor modifies Windows registry files, sends out HTTP GET requests, writes information on text files (that are later deleted), and much more. These actions are performed with the help of the following commands:
- d&exec – Download and execute an executable (.exe or .dll).
- more_eggs – Delete the current More_eggs and replace it.
- Gtfo – Uninstall activity.
- more_onion – Execute a script.
- via_c – Run a command using “cmd.exe/C”.
Ways to prevent being deceived by sophisticated malspam campaigns
Phishing emails or websites have been around for many years now and were often poorly executed. In most of the cases, users can find suspicious indicators due to poor grammar, spelling mistakes, bad formatting, and other symptoms. However, cybercriminal gangs are sophisticated individuals, and they take time and effort to craft phishing emails that are identical to original ones. Besides, they also leverage multi-stage infection mechanisms that are not as obvious for many computer users.
Therefore, it is vital to recognize phishing emails before they manage to inflict major damage to computer systems and connected networks. Regardless of how well worded the email is, you can always check the sender's address – it is often a good indicator that it is illegitimate (nevertheless, beware of emails spoofing). Additionally, you should NEVER enable content by turning on the Macro function unless you have been expecting a document with such a feature.
Additionally, because some of the malware campaigns have been actively using software vulnerabilities to proliferate the malicious payload, it is vital to patch all the operating systems on time (along with all the installed software, e.g., Drupal). Finally, make sure your computer is equipped with a sophisticated anti-malware solution.
Delete More_eggs backgood with all its components from your system
Due to highly evasive infection mechanisms (fileless infection), detecting and preventing More_eggs virus becomes an almost impossible task for most modern security solutions. Nevertheless, by employing powerful anti-malware software, you should be able to remove More_eggs virus with all its components. The best way to do that is by accessing Safe Mode with Networking, as explained below – it would temporarily disable the main functions of the malware.
While More_eggs removal might not be necessary in every case (the malware can delete itself under particular circumstances), the termination of other components introduced by the Trojan is mandatory. In other words, just because the main payload is deleted after the infection, it does not mean that there is nothing else to eliminate.
Once More_eggs backdoor removal is complete, you should also employ PC repair software FortectIntego as it should be able to fix the damage done to the system and restore it to the pre-infection condition without having to reinstall the OS.
Getting rid of More_eggs virus. Follow these steps
Manual removal using Safe Mode
Accessing Safe Mode with networking will help you to stop the main functions of More_eggs malware:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from More_eggs and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting backdoors
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Lenart Bermejo, Ronnie Giagone, Rubio Wu, and Fyodor Yarochkin . Backdoor-carrying Emails Set Sights on Russian-speaking Businesses. Trend Micro. Security intelligence Blog.
- ^ Cobalt Group. Mitre. Knowledge base.
- ^ Multiple Cobalt Personality Disorder. Cisco Talos. Security research blog.
- ^ Fake Jobs: Campaigns Delivering More_eggs Backdoor via Fake Job Offers. Proofpoint. Threat Insight team report.
- ^ Ole Villadsen. More_eggs, Anyone? Threat Actor ITG08 Strikes Again. IBM. Security Intelligence threat research.
- ^ Mark Goudie. Going Beyond Malware: The Rise of “Living off the Land” Attacks. Crowdstrike. Security blog.














