Mount Locker ransomware (Virus Removal Guide) - Decryption Methods Included
Mount Locker virus Removal Guide
What is Mount Locker ransomware?
Mount Locker ransomware – a malicious infection that encrypts all files and tries to demand money from its victim
Mount Locker ransomware is a newly detected threat that locks all files in the device and is designed to demand money to be paid for the return.[1] Once a malicious program manages to perform its doings on a targeted device, it will block your access to stored files on the computer and enforce you to contact cybercriminals and pay a specified ransom fee to get those data decrypted. The infection primarily targets business entities trying to get a huge amount of money from them.
Moreover, the cybercriminals behind the Mount Locker virus are using a whole range of sly tactics and a series of transmitters that often appear harmless and intriguing and can confuse even cybersecurity experts. Such a threat is a really serious problem and can cause a lot of damage to the victim because it can prevent access to very valuable digital information in the infected device.
Mount Locker virus mostly gets installed on a device through email attachments received from hackers. Cybercriminals disguise the email and attachment with hidden malicious codes and create the email letter in such a manner that it all seems received from the organization with a good reputation. But once such attachments are opened, the ransomware codes secretly start to run in the background and scans the system to find some required settings, details of stored files inside, active security programs on the device, and etc. After that, the malware starts the encryption[2] process for all stored files on the computer and appends files with a random extension like .ReadManual.C77BFF8C that got used with analyzed samples.
| Name | Mount Locker ransomware |
| Type | File locking virus, cryptovirus, malware |
| Distribution | This malware comes from infected email attachments, torrent websites, pirated software, game cheats, cracks |
| Issues | This virus is using an encryption algorithm to lock all personal files on the infected device. The victim can't open any encrypted file and gets encouraged to pay the ransom for such an opportunity |
| File extension | Each of the files gets random extension (f. e. .C77BFF8C). These files are encrypted and cannot be opened or used without decryption |
| Ransom note | A file named RecoveryManual.html is dropped for victims to inform people about virus behavior and possible steps to this problem. Hackers state that the only solution is to pay the ransom |
| File recovery | Data recovery might be impossible if you don't have backups. However, in some cases, official decryption tools or third-party programs recovery software can be useful |
| Malware removal | Remove Mount Locker ransomware by scanning your device with a powerful anti-malware application. |
| System fix | Ransomware or other threats sometimes can cause serious damage to the OS. In some cases, you will even need to reinstall it. To avoid that, we recommend fixing the virus damage with FortectIntego repair software |
If your device is infected, it is important to get rid of the Mount Locker virus before you try to do anything else to fix the damage. If you don't do that, the virus may keep encrypting new files that you create or data that you managed to recover from encryption. Also, it may prevent you from using your device normally.
Hackers are using a strong encryption algorithm, and the decryption key typically is different for all users. Therefore, only criminals behind the Mount Locker ransomware have the right decryption key/software. Unfortunately, if you don't have backups, it may be impossible to recover your files. But it is still not recommended to pay criminals.
Moreover, your backup sources or other devices will be unsafe too if they are connected to the infected computer. The virus may encrypt them, and you won't be able to use these devices to restore your information. It is clear that losing the backup access to your personal data can lead to a serious loss because the Mount Locker virus encrypts personal videos, images, documents, projects, audio recordings, and all other essential files.
If you want to prevent installed infection from encrypting more files, you should uninstall the virus. Although already encrypted files will remain encrypted even after Mount Locker ransomware removal, your new files will be safe and untouched by this threat.
After the Mount Locker virus termination, you may recover your data from backups. If you have them, you will avoid data loss. This is why it is recommended to always have your files backed up. You should store data on a remote server or unplugged storage device in the future.
Also, we recommend fixing any possible Mount Locker virus damage to your computer's OS with PC repair software like FortectIntego. In the future, you should be really careful with emails you are opening and websites you are visiting and use reliable anti-malware software.
Paying the criminals is not the option to recover encrypted files
The Mount Locker ransomware virus encrypts a wide variety of digital files. It is important to understand that encryption is usually not reversible unless a special decryption key is applied. Hackers always give victims a ransom note to inform about the ransomware and decryption method.
Sadly, the ransom note tells you only one possible step to take your files back. Mount Locker virus creators state that the only solution is to pay money. But security experts[3] say that it is unwise to give money for the criminals because most likely they won't decrypt files even after the ransom money is in their pocket.
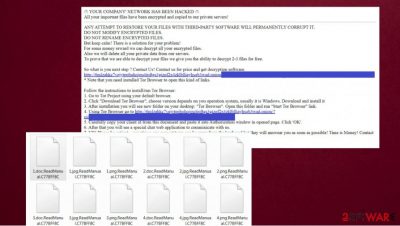
If you are curious about how a ransom note named as “RecoveryManual.html” looks, there is the example (the URL can be different):
Your ClientId:
–/!\ YOUR COMPANY' NETWORK HAS BEEN HACKED /!\
All your important files have been encrypted and copied to our private servers!
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE WILL PERMANENTLY CORRUPT IT.
DO NOT MODIFY ENCRYPTED FILES.
DO NOT RENAME ENCRYPTED FILES.
But keep calm! There is a solution for your problem!
For some money reward we can decrypt all your encrypted files.
Also we will delete all your private data from our servers.
To prove that we are able to decrypt your files we give you the ability to decrypt 2-3 files for free.So what is you next step ? Contact Us! Contact us for price and get decryption software.
hxxp://6mlzahkc7vejytppbqhqjou4ipftgs3gizof2x4zklblliayhsqb3wad.onion/?cid= a7fb00164f192687eda014cd1bde83252ad9ac2fdc89a26b1294b11918d6fe33
* Note that you need installed Tor Browser to open this kind of links.Follow the instructions to install/run Tor Browser:
1. Go to Tor Project using your default browser.
2. Click “Download Tor Browser”, choose version depends on you operation system, usually it is Windows. Download and install it
3. After installation you will see new folder on your desktop: “Tor Browser”. Open this folder and run “Start Tor Browser” link.
4. Using Tor Browser go to hxxp://6mlzahkc7vejytppbqhqjou4ipftgs3gizof2x4zklblliayhsqb3wad.onion/?cid= a7fb00164f192687eda014cd1bde83252ad9ac2fdc89a26b1294b11918d6fe33
5. Carefully copy your client id from this document and paste it into Authorization window in opened page. Click 'OK'.
6. After that you will see a special chat web application to comminicate with us.
7. NB! Please be patient – sometimes our support team can be away from the keyboard but they will answear you as soon as possible! Time is Money! Contact us as soon as possible.
We won't store you decryption key forever!
Typically, all ransom notes are similar. Criminals try to scare their victims by putting tight deadlines, asking for money, and promising that they send a secret decryption key as long as the victims do everything according to the plan. Mount Locker virus creators shouldn't be trusted, remember that.
Malicious actors even give the website that can be used to upload a few files for free test decryption. This way cybercriminals try to persuade the victim that all files can be decrypted if they pay the required amount of money. MountLocker ransomware is not decryptable, so you should either wait for the official tool release or rely on other methods.
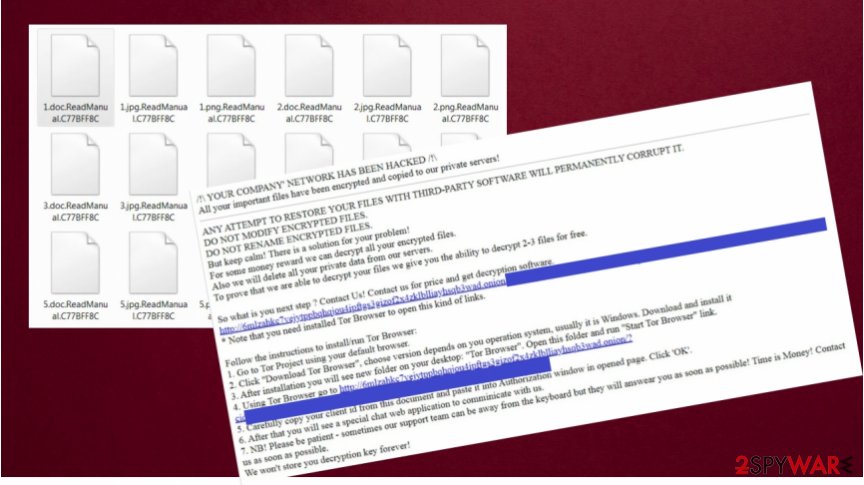
In reality, there is no guarantee that even if you satisfy all requirements the decryption code will be granted to you. Hackers can always disappear without sending anything in exchange or even ask for more money. That's why the best decision is to remove the Mount locker ransomware from the device and look for possible alternatives instead of doing everything that anonymous blackmailers want you to do.
And if you are still wondering how Mount Locker ransomware did infect your computer, it is important to remember that typically malware gets installed through untrustworthy software or file download sources, trojans, email spam campaigns, unofficial, fake software updating tools, and software “cracking tools.
If you want to avoid any damage to your computer, you should stop installing unofficial software. You must be especially cautious with emails you get because malicious files can be downloaded by the attached file or downloaded via a given website link.
Removing Mount Locker ransomware from your device is important before you can rely on file-recovery options
Ransomware can be a really serious problem. As we already recommended, you should make a copy of all your files and use a different place to store them. If you have backups, get rid of the Mount Locker ransomware virus as soon as possible.
This step won't give your encrypted files back, but it protects new files. If you don't want to remove the virus manually, we recommend running a scant with reliable anti-malware software such as SpyHunter 5Combo Cleaner or Malwarebytes. Only after the Mount Locker ransomware removal, you may try to recover your data from backups.
Moreover, ransomware or other threats sometimes can cause serious damage to your device OS. In some cases, you will even need to reinstall it. To avoid such inconvenient things to happen, we recommend fixing the MountLocker virus damage with FortectIntego repair software.
After you remove Mount Locker ransomware, you may try to recover your data. We recommend using the free decryption tool, third-party recovery solutions, or attempting to check whether the automatic Windows backups were not deleted. Unfortunately, if none of the methods below help, there is no other way to recover encrypted files at the present time. Nevertheless, keep in mind that paying cybercriminals is always risky, and they don't decrypt files in most cases too.
Getting rid of Mount Locker virus. Follow these steps
Manual removal using Safe Mode
To delete Mount Locker ransomware with Safe Mode, you need to perform this procedure on your device.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Mount Locker using System Restore
Sometimes, System Restore can be useful when you are trying to eliminate ransomware.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Mount Locker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mount Locker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Mount Locker, you can use several methods to restore them:
Data Recovery Pro method may be useful when dealing with ransomware.
Sometimes Data Recovery Pro is useful to restore few encrypted files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mount Locker ransomware;
- Restore them.
You can use the built-in Previous Version Feature in Windows.
It is possible to recover files one-by-one if you had System Restore point prepared before the ransomware attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Recover your files with ShadowExplorer
If the Mount Locker file virus failed to delete Shadow Volume copies, it is possible to recover data by using ShadowExplorer.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
MountLocker ransomware is not decryptable
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mount Locker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ What is Ransomware?. Trend Micro. Security researchers.
- ^ Encryption. Wikipedia. The Free Encyclopedia.
- ^ Odstranit Virus. Odstranit Virus. Security and Virus News.





















