Myday ransomware (virus) - Decryption Methods Included
Myday virus Removal Guide
What is Myday ransomware?
Myday ransomware – a perilous computer infection that restricts access to your files
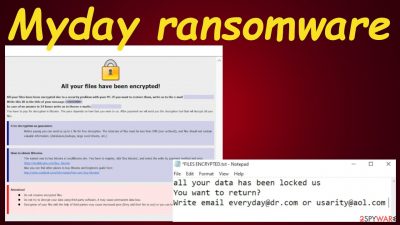
Myday ransomware is spread through file-sharing platforms and phishing emails.[1] When it enters a Windows computer, it immediately scans for personal files (documents, pictures, videos, etc.) and initiates the encryption procedure, which locks all of them by using complex military-grade coding algorithms.
During this process, the personal data is renamed by appending .[everyday@dr.com].myday extension to all original filenames. It's rendered useless as you won't be able to access any of it. Cybercriminals do that so they could extort cryptocurrency from you.
In the FILES ENCRYPTED.txt ransom note, which can be found on the desktop and in affected folders after the encryption, the assailants state their demands and instructions. They try to scare you into thinking that no one can help you to restore your files apart from them.
In some cases, that might be true. But by paying an undisclosed amount of money in Bitcoins to the cyber crooks, you'd be motivating them to attacks more innocent people and expand their dirty empire. Therefore, the only reasonable thing to do is to remove Myday virus from your infected computer.
This article will show you how that's done with illustrated guidelines. We've also added detailed instructions on finding the right decryption software and repairing corrupted system files and folders. But first, we'll let you know how this virus belonging to the Dharma ransomware family operates and reveal other peculiarities.
| name | Myday ransomware |
|---|---|
| Type | File-locker, cryptovirus |
| Family | Dharma |
| Infection symptoms | Inability to open personal files as they seem to be renamed; can't launch security software; strange text file with demands appears on the desktop |
| Appended file marker | All non-system data is appended with .[everyday@dr.com].myday extension |
| Ransom note | FILES ENCRYPTED.txt |
| Distribution | Phishing emails, file-sharing platforms, fake Flash Player updates |
| Elimination | Perform a full system scan with our recommended software to safely and quickly remove the ransomware and any other malicious entries |
| System health | Repair virus damage by performing system diagnostics with the time-tested FortectIntego optimization software |
Within the ransom note, the developers of Myday virus try to convince you that there's are no other options to regain access to your data apart from succumbing to their demands. They provide an email address (everyday@dr.com) to establish contact and offer to send them one encrypted file for free decryption.
That should persuade you that the necessary decryption software actually exists. The ransom amount isn't specified, but the assailants claim that it will increase if the victim doesn't reach out to them immediately. Then they provide instructions on how to obtains Bitcoins and falsely claim that third-party data recovery software could result in permanent data loss.
As we've stated before, paying the criminals is never the answer. Instead of the promised decryption software, you might receive additional malware. Or the ransomware authors could disappear, leaving you with encrypted files and a lighter wallet. Therefore, you need to remove the infection and use alternative data recovery methods.
The ransom note that you shouldn't believe a word that is written in it:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail everyday@dr.com
Write this ID in the title of your message
In case of no answer in 24 hours write us to theese e-mails: everyday@dr.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Remove Myday file virus in Safe Mode with Networking and repair corrupted system settings
Once a file-locking parasite is done with encrypting your precious data, the only thing that matters is how you respond to the incident. Since you're reading this part of the article, we're delighted that you decided to remove the ransomware and chose us to accompany you on this unpleasant journey.
Before proceeding to the removal, copy all encrypted files to a removable storage device. A USB thumb drive or an SSD will suffice. Normally, we'd say that now you have to download the Malwarebytes security software and perform a full system scan with it to remove Myday virus. But not this time.
Since this file-locker belongs to the notorious Dharma family, it might prevent you from visiting any security-related websites and from downloading and installing any anti-malware software. So you will need to do all that after rebooting your Windows computer in Safe Mode with Networking.
If you have no idea how to do that or need a reminder, these illustrated instructions will help you access the said mode on Windows 10/8 computers:
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
If Myday file virus infected your device running on Windows Vista/7/XP, use these instructions to access the Safe Mode with Networking feature:
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
After successfully rebooting your device in Safe Mode with Networking, you can proceed with the ransomware removal. As stated earlier, you will need a reliable anti-malware tool for that. Either the abovementioned tool or SpyHunter 5Combo Cleaner will do the trick perfectly as their virus detection engines are phenomenal.
All you have to do is download and install your preferred security software, update its virus definitions with the latest signatures, and perform a full system scan. Either of the recommended programs will automatically detect all malicious files and entries and suggest eliminating them. Please stick with the recommendations to fully remove Myday.
These days cybercrime is on the rise, and a trustworthy anti-malware tool is your frontline defense against various computer infections that are lurking on the internet and waiting for insufficiently protected devices to come around. Please make a habit of frequently updating your chosen security tool and perform full system scans at least a couple of times per week.
Once the removal is finished, you need to take care of the overall health of your device, as the ransomware infection might have done severe damage to its essential system files and settings. These damages might result in BSoDs,[2] freezing, severe lag, or even complete system failure.
Manual repairs are not recommended even for highly experienced IT specialists, as modifying the wrong entry might have disastrous outcomes. Therefore, system diagnostics software should be used. Many users and IT experts[3] from around the world recommend using the FortectIntego PC repair software, as its patented technology refreshes the system files, fixes all system-related irregularities, and even deletes all tracking cookies.
It has a free trial, so you have nothing to lose by giving it a go:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Once you successfully remove Myday ransomware and repair the damage that it has caused to your computer's system, you can restore your data from backups. If you didn't keep any, proceed to the next chapter, where we provide possible data recovery options.
Using alternative means to recover data
We're glad you decided not to succumb to the demands of the criminals and removed their vile creation. After cleaning up your device with proper system diagnostics software, it's time to try and recover your data. Please be advised that since this file-locking parasite is a brand new strain of ransomware, there is no dedicated decryption software yet.
But when the good guys receive samples of the article's culprit, they'll start working on it. For now, we can suggest using alternative .[everyday@dr.com].myday file recovery options. There's no guarantee that this method will work, but it doesn't hurt to try it out:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
If this third-party software was unable to recover .[everyday@dr.com].myday files, don't lose hope. Some companies are dedicating their time and money to help ransomware victims decrypt their files without losing a dime and put an end to this nightmare. Check out these free decryptors. Maybe some of them will help you:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
If none of them did, you have to arm yourself with patience. In our 20 years in this business, we've learned that the necessary decryption software is developed sooner or later. Therefore keep the copies of your encrypted files in the offline storage device and check back with us from time to time to check if the decryptor is finally available.
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ How To Recognize and Avoid Phishing Scams. Ftc. Federal trade commission, consumer information.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. Howtogeek. Online technology magazine.
- ^ Virusai. Virusai. Spyware news and security.










