NFT Tab browser hijacker (Free Instructions) - Chrome, Firefox, IE, Edge
NFT Tab browser hijacker Removal Guide
What is NFT Tab browser hijacker?
NFT Tab is a browser-hijacking application that displays ads instead of being useful in any way

NFTs have been one of the largest trends in the tech world in recent years. They penetrated various industries, including clothing, vehicles, and gaming, and despite the shortcomings and major scandals, the Non-Fungible Token remains interesting to many in the sight of profit. The trend did not go past the browser hijacker creators, as apps like NFT Tab surfaced very recently. It is meant to help users find all-thinks NFTs easier.
A browser hijacker is an application that takes over the browser, such as Google Chrome, Mozilla Firefox, MS Edge, or another compatible browser. Once installed, it would set the homepage and the new tab address to srchingveno.com, redirecting all searches to Bing or another provider (depending on the user's location).
NFT Tab would also filter results in a different way and insert promotional links and ads during searches. As a result, users would be exposed to numerous ads that otherwise wouldn't be there, in addition to altered results. Another undesirable trait of the hijacker is data tracking – cookies help the app gather information about users passively, putting their privacy at risk. If you have this extension on your browser, we recommend you remove it for a better browsing experience.
| Name | NFT Tab |
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundles, ads, redirects |
| Symptoms | Homepage and new tab address hijacked by the extension; homepage and new tab set to srchingveno.com; promotional links are displayed as top search results; intrusive ads on various visited websites |
| Risks | Encounters with potentially unsafe ads. Also, since PUPs are distributed via software bundles, there is a chance of other infections |
| Removal | You can eliminate the browser hijacker by adjusting your browser's settings. Scanning your system with SpyHunter 5Combo Cleaner security software will confirm that there is no adware or malware running in the background |
| Other tips | After removing all potentially unwanted applications, we recommend you employ the FortectIntego utility to clean your web browsers and repair any damaged system files |
How browser hijackers spread
A browser hijacker's popularity and use, in the view of its developers, heavily rely on how the software is promoted and spread. The NFT Tab browser hijacker is unfortunately not an exception to the fraudulent distribution practices that are common among potentially unwanted programs.[1]
The majority of people prefer to download free software from third-party websites, which is where most malicious or unwanted apps come from. Without reading the instructions, people commonly skip past installation steps and clickthrough stages, allowing optional components to enter. This practice is often referred to as software bundling.
In order to avoid this, you must always keep a close eye on the installation process of any new applications you download from unofficial sources. . When given a chance, select Advanced/Custom options and uncheck all of the pre-ticked checkboxes. You should also pay attention to components such as fine-print text or misplaced buttons.
However, you should always avoid using software cracks and other sites that offer pirated software because you might end up infected with ransomware[2] or other dangerous malware.
Reasons to avoid browser-hijacking apps
Browser hijackers are not intrinsically dangerous; they seldom ever link you to malicious or exploit-kit-filled websites.[3] However, when it comes to distribution and functioning, there is frequently quite a bit of deceit because the creators' main goal is to monetize the numerous ads forced into every available space, not to please users.
A browser hijacker's primary characteristic is an unauthorized change to the browser's settings (although, if you are using a modern web browser such as Chrome, you are likely to be warned about these changes). This allows the app to incorporate adverts and refer users to alternative providers they are linked with while disguising the search results as genuine. These promotional links could display inaccurate or misleading information, triggering the installation of even more potentially dangerous applications.
Additionally, browser hijackers frequently pose as being very useful and frequently choose a theme to appeal to a particular audience. Evidently, NFT Tab is trying to be appealing to those interested in NFTs, while EmailCheckToday pretends to help users reach their email faster. All of these functions are bogus, and users are instead presented with links to websites associated with the name. Beyond regular search functions, hijackers barely provide anything else, producing ads, tracking user data, and impacting the experience negatively.
Remove NFT Tab easily
The most common type of potentially unwanted apps is browser extensions and NFT Tab spreads as such. It is simple to build and update the extension and has enough capability to deliver adverts to users who have it installed. Therefore, in order to remove the browser hijacker, you need to access browser settings and perform the following steps:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Internet Explorer
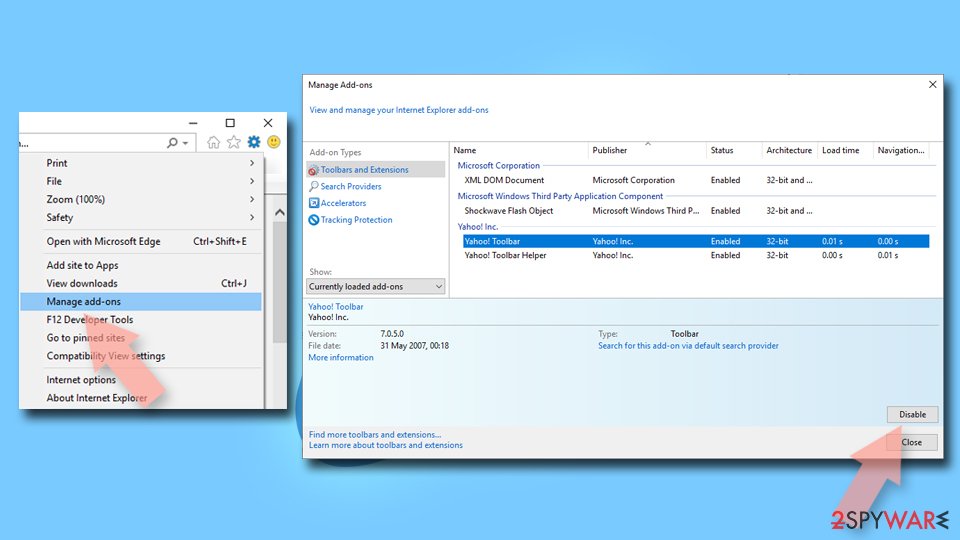
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
As was already said, browser hijackers are known for their data collection methods, which are done in order to share information with other parties for further financial gain. The program creators install a number of trackers on users' computers in order to accomplish this goal; these trackers continue to function even when the extension is deleted. As a result, you should ensure that cookies and other web data are removed from your system. You may do this automatically using FortectIntego or manually by following the steps below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Internet Explorer
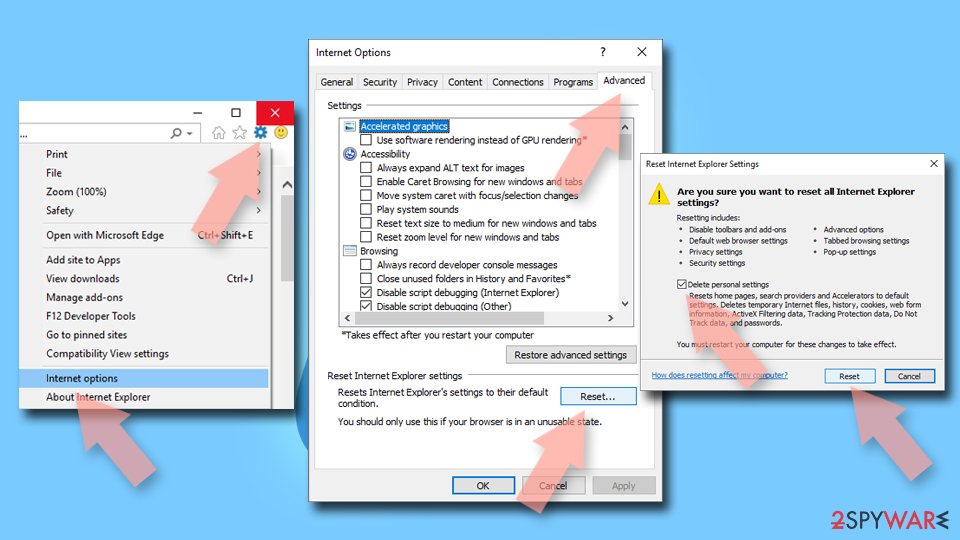
- Click on the Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
![Reset Internet Explorer Reset Internet Explorer]()
How to prevent from getting browser hijacker
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. How-to Geek. Site that explains technology.
- ^ Ransomware. Imperva. Application and data protection.
- ^ Exploit kit. Wikipedia. The free encyclopedia.