Obfuscated ransomware (Removal Guide) - updated Feb 2019
Obfuscated virus Removal Guide
What is Obfuscated ransomware?
Obfuscated ransomware – a decryptable cryptovirus which is also known as BigBobRoss
| Name | Obfuscated ransomware |
|---|---|
| Type | Cryptovirus |
| Also known as | BigBobRoss |
| Danger LEVEL | High. This virus locks all found files, gladly, they can be recovered |
| Ransom note | Read Me.txt |
| Contact email | bigbobross@protonmail.com |
| Main executable | bedoneupx.exe |
| File extension | .obfuscated, .[id=] |
| Distribution method | Spam email attachments |
| Elimination | Use FortectIntego for Obfuscated ransomware removal, then recover your files by contacting Michael Gillespie. |
Obfuscated ransomware virus can also be called BigBobRoss ransomware due to the contact email left in the ransom note — bigbobross@protonmail.com. There are also a few different payload versions discovered in the wild, but the danger behind the cyber threat remains the same. The most dangerous thing about the ransomware is the file encryption that affects the original code of your photos, audio files, documents, and even archives.
Unfortunately, when your files get the .obfuscated extension, you cannot open or use them. Keep in made, that Obfuscated ransomware can lock a big variety of data, including audio, video, image, text document, archive, virtual drive, template files. We recommend cleaning the system thoroughly and then focusing on the data recovery using backups because it is the safest way.
Obfuscated ransomware developers cannot be trusted because these people only care about your money and there is little to none possibility that encrypted files can be recovered.[2] Use a reputable anti-malware tool like FortectIntego, eliminate all threats including this cryptovirus and avoid the risk of getting scammed by the crooks.
For further information, Obfuscated ransomware developers also urge paying the ransom price in Bitcoins. They provide the users which a site where such cryptocurrency can be obtained. It is known that cybercriminals who demand ransom always ask for some type of cryptocurrency (Bitcoin mostly) in order to stay safe and untrackable.
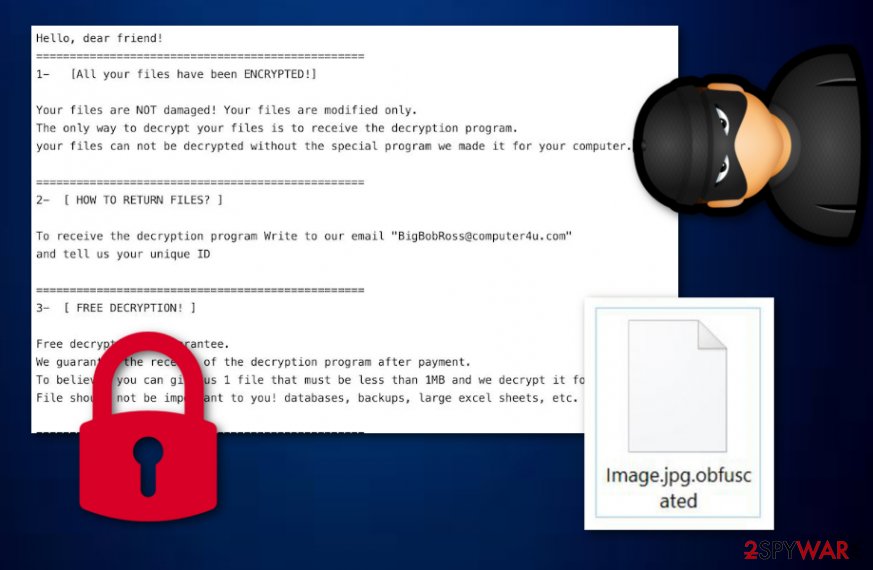
When Obfuscated ransomware is done encrypting your files the ransom note Read Me.txt is displayed on the screen and has the following message:
Hello, dear friend!
=================================================
1- [All your files have been ENCRYPTED!]Your files are NOT damaged! Your files are modified only.
The only way to decrypt your files is to receive the decryption program.
your files can not be decrypted without the special program we made it for your computer.=================================================
2- [ HOW TO RETURN FILES? ]To receive the decryption program Write to our email “BigBobRoss@computer4u.com”
and tell us your unique ID=================================================
3- [ FREE DECRYPTION! ]Free decryption as guarantee.
We guarantee the receipt of the decryption program after payment.
To believe, you can give us 1 file that must be less than 1MB and we decrypt it for free.
File should not be important to you! databases, backups, large excel sheets, etc.=================================================
4- [ Instruction ]the easiest way to buy bitcoins is LocalBitcoins site. you have to register, click “buy bitcoins”
and select the seller by payment method and price.https://localbitcoins.com/buy_bitcoins
=================================================
CAUTION!
please do not change the name of files or file extension if your files are important to you!
Your unique ID :
Additionally to the first encryption function, Obfuscated ransomware can alter various parts of the system and change various settings:
- modify Windows Registry Keys;
- disable security programs;
- delete shadow volume copies;[3]
- add files to system folders;
- run malicious processes in the Task Manager section.[4]
Since victims of Obfuscated ransomware have contributed to the analysis, there are a few versions of the same ransomware that can easily distribute around the world. However, the solution for most of the cryptovirus is the same – anti-malware tools and a full system scan. Expert-tested software is necessary for this process as the user himself/herself might cause even more damage while trying to delete the notorious infection on his/her own.
You need to remove Obfuscated ransomware using professional tools so that every related file can be deleted from the system entirely. Also, remember that the name of a threat may differ depending on the antivirus program you are using. You should follow the suggested steps of your anti-malware tool.
We want to remind you that Obfuscated ransomware is a ransom-demanding virus and its developers cannot be trusted. Even though the crooks offer 1 file for free decryption to prove that the decryption key is real, there still is no need of contacting them. First of all, you risk being left with no money. Second, cybersecurity experts have already released a decryption tool for .obfuscated files.
Researchers[5] note that Obfuscated ransomware can be detected as:
- TR/Encoder.cjfbq;
- TR/Crypt.XPACK.Gen;
- Trojan.Ransom.Filecoder;
- Trojan.Heur.RP.7mqaaiAmoeki;
- Win32:Malware-gen;
- TR/FileCoder.iirhw;
- Gen:Trojan.Heur.RP.7mqaaiAmoeki (B);
- etc.
Make sure to check if the system is malware-free after the automatic Obfuscated ransomware removal. You can do so by scanning the device again or with an alternative antivirus tool. This way you can be sure that data backups can be used to restore encrypted files. If you have no backups and still want to recover locked data, check our tips below the article.

Email attachments help infect the system with malware
There are many other variants of ransomware-type threats that get on the network using Word, Excel or PDF documents attached to the email spam. This is a common technique used by malware developers and distributors. When the email poses as a legitimate notification from companies like PayPal, FedEx or Amazon people tend to open them without consideration.
However, when the email is opened, and the attached file downloaded, malicious script is automatically launched on the device. The payload might also inject the system via the direct link on the PDF file or the email itself. You can avoid the infiltration if you pay more attention to the content of your email box. You should delete suspicious emails or the ones you were not expecting to get in the first place.
Continuously, ransomware infections are commonly distributed thru unprotected networks such as Torrents and The Pirate Bay. While downloading certain applications, movies, and TV series from these websites, you take risks of infecting your computer system with malware. We suggest staying away from third-party sources and downloading content only from primary distributors.
Get rid of the Obfuscated ransomware virus during a thorough system clean
The main tip we can give you when dealing with Obfuscated ransomware virus is to employ professional programs designed to terminate threats like this. Reputable anti-malware gives you the advantage because it can indicate possible risks and remove them from the computer once and for all. Eliminating the cyber threat on your own, you risk causing more damage to your system.
Remove Obfuscated virus using FortectIntego or SpyHunter 5Combo Cleaner and scanning the system entirely. This should take less than 15 minutes, and your device is safe to use again. Remember, wait until the process is finished and do not forget to refresh your entire computer system after the elimination just to ensure that the cyber threat has been taken care of properly.
Note that you need to perform Obfuscated ransomware removal before any data recovery attempts so that your computer is clear and safe. If you plug in the external device with your file backups on the infected system, ransomware encrypts your data once again. So, make sure that you accomplish your goals as required.
Getting rid of Obfuscated virus. Follow these steps
Manual removal using Safe Mode
To disable Obfuscated ransomware, reboot the system to the Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Obfuscated using System Restore
System Restore feature may help when you want to get rid of ransomware faster:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Obfuscated. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Obfuscated from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Obfuscated, you can use several methods to restore them:
Data Recovery Pro is a good alternative when you have no backups
You can use Data Recovery Pro for accidentally deleted files too
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Obfuscated ransomware;
- Restore them.
Windows Previous Versions feature helps when Obfuscated ransomware encrypts your important data
Windows Previous Versions can only be helpful when System Restore is enabled
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use ShadowExplorer for the file recovery
If the ransomware virus left Shadow Volume Copies untouched, you could recover data using ShadowExplorer
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Obfuscated ransomware decryptor is available
If you got infected with this ransomware virus, don't be scared because it seems that it is decryptable. For that, contact virus researcher Michael Gillespie.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Obfuscated and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Bedoneupx.exe analysis. VirusTotal. Online malware scanner.
- ^ Tarcisio Marinho. Ransomware encryption techniques. Medium. A place to read and write big ideas and important stories.
- ^ Shadow Copy. Wikipedia. The free encyclopedia.
- ^ Tim Fisher. Task Manager. Lifewire.com. Independent news site.
- ^ LosVirus. LosVirus. Spyware related news.





















